Extend Access Management through Azure Active Directory
F5 and Microsoft deliver an integrated solution that boosts productivity and reduces risk by centralizing access management.
The Importance of Centralized Access Control in an Increasingly Online World
To stay competitive, businesses are deploying more apps across multiple environments including the public and private cloud, SaaS and on premises—which can lead to complications. As demand increases and complexity grows, it’s critical to stay on top of deployments to ensure security and ease of use. F5 has the tools you need to reduce friction and address security threats.
Boost Productivity
F5 access solutions integrate with Microsoft Azure Active Directory (Azure AD) to provide a single pane-of-glass for access to critical applications that run your business.
Reduce Risk
Consolidate and streamline access management with flexible and adaptive policies that evaluate risk in real time.
Keep it Simple
Leverage an easy-to-use interface to onboard apps and define Azure AD Conditional Access policies through a guided configuration engine.
Seamless Integration for Centralized Control
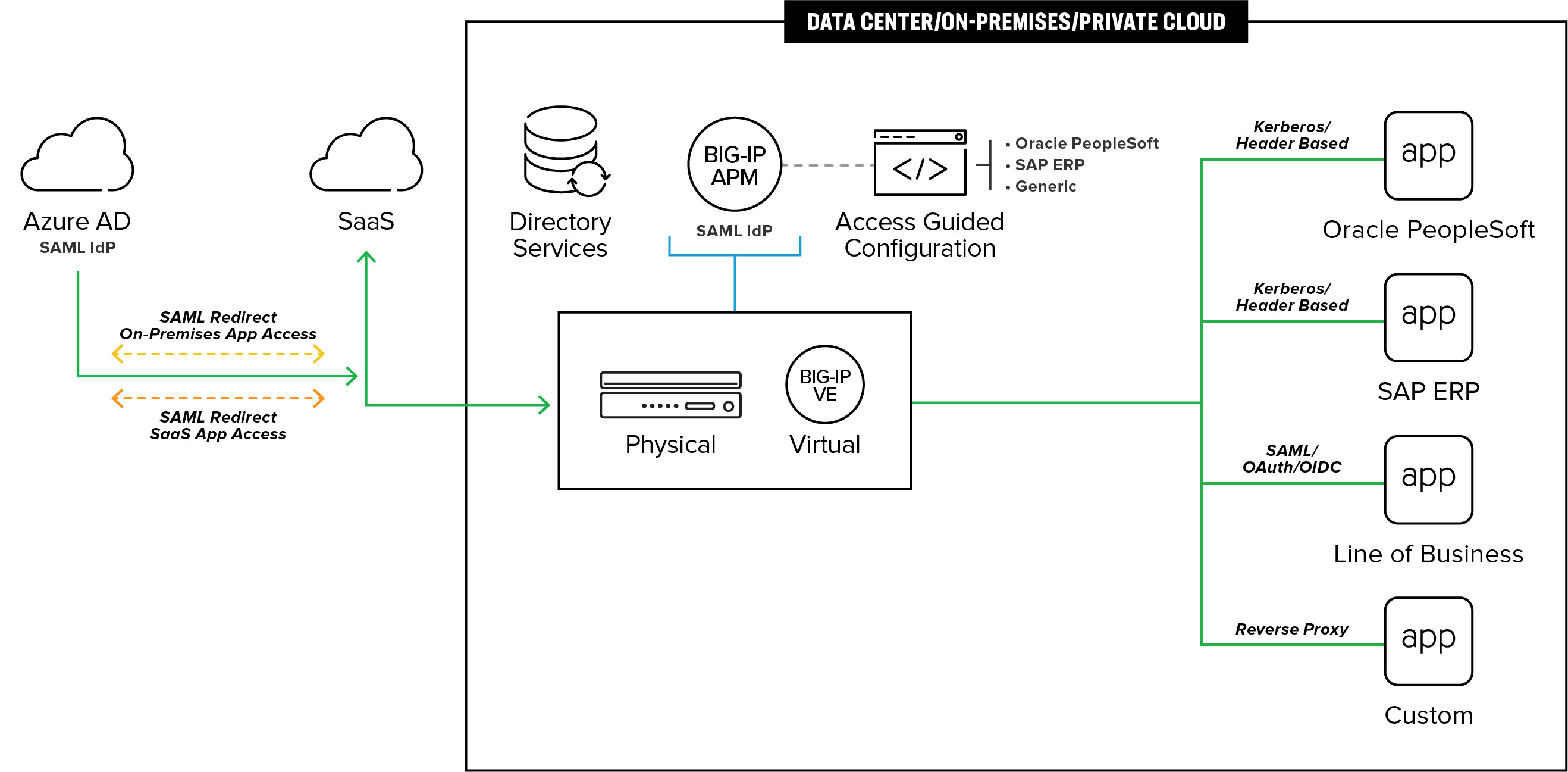
Security management made easier
F5 BIG-IP Access Policy Manager (BIG-IP APM) seamlessly integrates with Microsoft Azure Active Directory (Azure AD) to provide users with a single pane of glass for accessing all applications, while consolidating management of access-related security policies.
How F5 Helps
-
Seamless Access to All Applications
Enhance productivity by giving users easy access to all necessary apps
With the F5 and Microsoft Azure AD integrated solution, administrators can use the guided configuration to quickly deploy and manage access, reducing labor and costs. Abstracting authentication and authorization complexity while fully supporting AuthN and AuthZ reduces the burden of account access for users and the threat surface for attackers.
Resources
Featured
Applications can live anywhere, which means today’s users can work from anywhere. That’s great for user and corporate productivity. But how can organizations ensure quick, easy, and secure access to applications that can reside anywhere and be accessed from anywhere, at any time?
