As advanced persistent threats (APTs) dominate the malware landscape, signature-based detection no longer provides adequate security for this fast-evolving threat environment. Signature-based detection relies on vendors providing signature updates to their platforms. Unfortunately, many of today’s threats are targeted to infiltrate a specific organization, used once, and then repackaged and modified to evade detection.
In contrast to limited intrusion detection and prevention solutions, advanced threat protection (ATP) systems trap and execute suspicious objects before they cross the wire, ensuring inspected traffic does not pose a danger to the endpoint. ATP systems can also stop a threat that has never been seen before, such as a zero-day attack.
Since ATP systems are so effective at stopping malware, more of these systems are being deployed to protect an increasing share of ingress and egress traffic. However, increased deployment of ATP systems has uncovered three areas where they can be further strengthened by use of complementary technologies that increase their effectiveness: SSL/TLS assistance, high availability, and traffic steering. This paper looks at how F5 and FireEye solutions work together to deliver enhanced performance and improved results across these three areas.
A number of trends are driving the need for improved SSL/TLS inspection, including growing usage of SSL/TLS, increased complexity (such as longer key lengths) across cryptographic protocols, and a trend on the part of the “bad guys” to encrypt malicious payloads so they cannot be detected. These trends place an ever-increasing burden on existing ATP systems and were a driving factor behind the development of F5® SSL Orchestrator™, a solution that provides high-performance decryption and re-encryption of inbound and outbound SSL/TLS traffic, dynamic service chaining, and policy-based traffic steering for intelligent management of encrypted traffic flows across the entire security chain—thus freeing ATP systems to focus exclusively on detecting malicious objects.
F5 SSL Orchestrator brings increased flexibility to your threat detection and mitigation systems and greatly improves your ability to scale without disruption. Like any solution, it is possible for ATP systems and their critical sensors to fail, and such a failure can easily end up blocking traffic. F5 SSL Orchestrator helps ensure that critical sites meet their availability and uptime targets even in the face of a sensor or device failure. F5 SSL Orchestrator intelligently balances traffic across multiple ATP systems to ensure a site remains available even when a sensor failure or overload takes place. Additionally, this configuration enables administrators to add or remove sensors without impacting overall site availability.
F5 SSL Orchestrator, when combined with FireEye Network Security, offers flexible deployment options and scalability for optimal threat protection. When deployed on the wire between an intranet and the internet, F5 SSL Orchestrator creates a decrypt/clear-text zone between the client and web server, which acts as an aggregation visibility point for FireEye security devices to inspect traffic. With SSL/TLS management and visibility into both inbound and outbound SSL/TLS traffic and options for both inline and out-of-band deployments, APTs can be contained quickly and efficiently in real time. This enables administrators to quarantine or delete harmful data before it infiltrates the network.
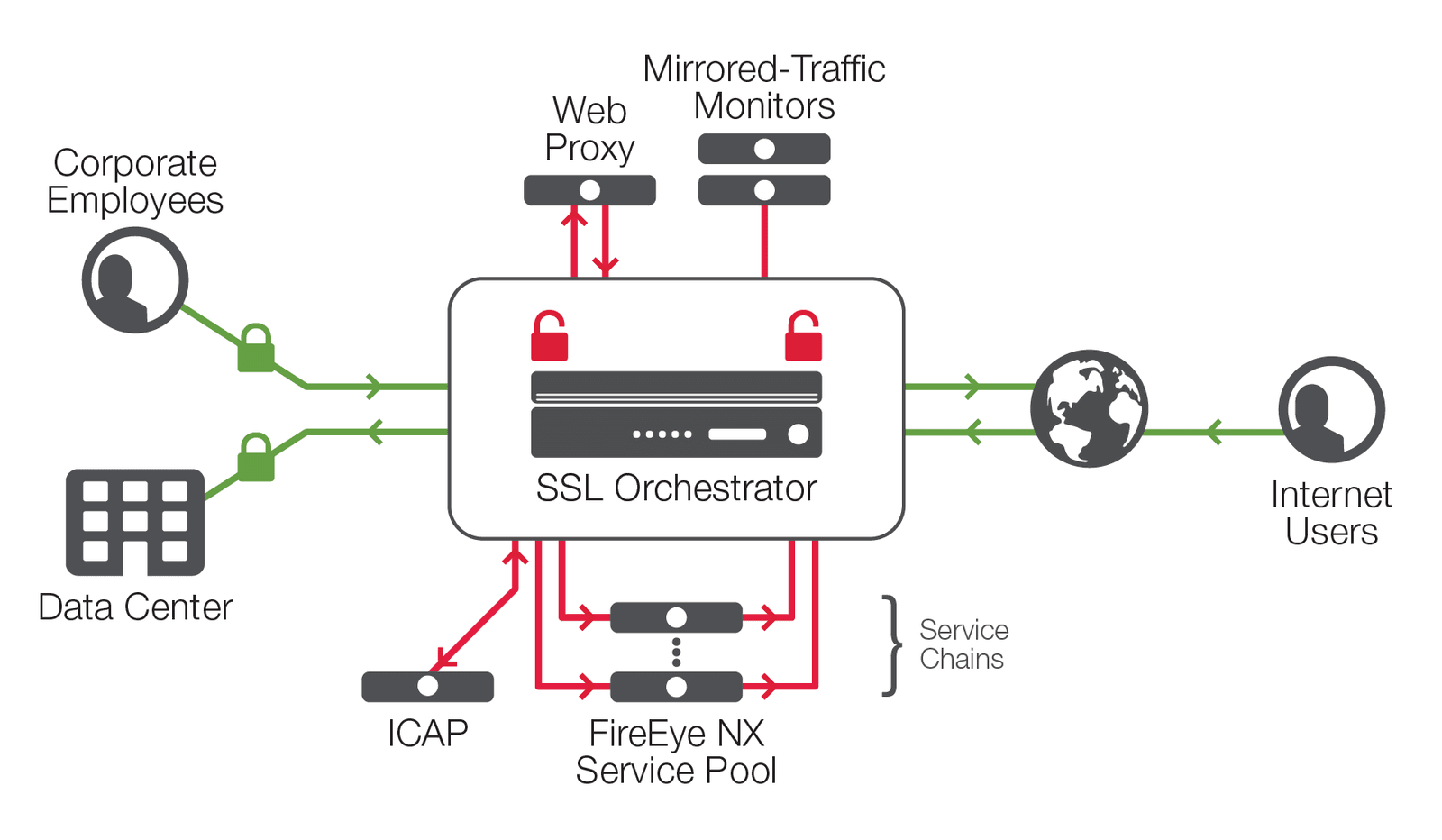
Figure 1 depicts the comprehensive F5 SSL Orchestration and FireEye solution, exploiting the full capabilities of the combined technologies to provide elastic scalability and service chaining.
F5 SSL Orchestrator deployed inline to the web traffic:
1. Decrypts SSL traffic for delivery to the FireEye Network Security pool.
2. Encrypts SSL traffic which passed through the FireEye Network Security device.
3. Performs load balancing on the FireEye pool, delivering optimal availability.
4. Enables a pool bypass when all the members are down.
5. Determines whether traffic should be decrypted or if it is able to bypass the FireEye pool without being decrypted, reducing load on devices.
This architecture enables the FireEye devices to operate most efficiently and at their fullest capabilities without compromising traffic throughput. Key management is centralized within F5 SSL Orchestrator, freeing the FireEye pool from having to perform any SSL functionality, while still providing it with full traffic visibility.
F5 SSL Orchestrator’s dynamic service chaining and policy-based traffic steering allow you to intelligently manage encrypted traffic flows across the entire security chain with optimal availability. Traffic steering allows for traffic determined not to need decryption (such as VDI) to bypass the ATP pool, thereby increasing the pool’s effective capacity. This configuration also enables a continuous traffic flow in the event of slowdown or failure of the FireEye sensors. In this way, the architecture protects traffic to the fullest—exposing threats and stopping attacks, while increasing efficiency and eliminating performance bottlenecks.
Today’s daunting security challenges require both advanced threat protection and the ability to ensure application availability. F5 and FireEye are working together to deliver solutions that offer the most effective technology, intelligence, and expertise in identifying and stopping malicious activity before it can occur. F5 and FireEye solutions enable you to find hidden threats with enhanced SSL visibility, ensure optimal security and performance through dynamic service chaining and policy-based traffic steering, deliver advanced threat protection with greater scalability, and improve operational efficiency with enhanced architecture.
To learn how F5 and FireEye can help your business succeed, visit f5.com/fireeye.
PUBLISHED DECEMBER 13, 2018