Securing your Borderless Business
You might have heard any number of folks here at F5 quip, “Identity is the new firewall.” That might sound, well, soundbitey but there’s a whole lot wrapped up in that simple statement. A whole lot of security and the changing way we address today’s digital disruptions.
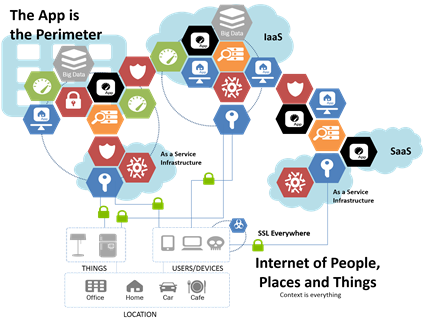
Whether it’s cloud or threats moving steadily up the application stack, or it’s the dissolution of monolithic apps into APIs and microservices, the reality is that these disruptions are having a ripple effect outward. The effect has shaken the ground on which data centers are built and are causing not unexpected changes in data center architectures. These changes are being driven heavily right now by the emergence of a borderless business. A business that relies on applications, many of which are are deployed over there (SaaS) and a few over there (IaaS) and some still down here (in the data center).
The changes are a result of recognizing that a borderless business cannot be effectively secured by traditional architectures centered on a firewall as the strategic point of control into the business.
It doesn’t work that way anymore because the perimeter being secured is no longer the data center. The perimeter is now that application, and that application, and that other application. Traditional IP-based firewalls are ineffective not only because of their limited understanding of applications but by their tethered nature. Traditional IP-based firewalls, still a necessity in the data center, are largely ineffective in highly volatile network environments like cloud because the address space of applications it is supposed to protect are often rapidly changing. The introduction of containers, too, has increased the problem of volatility in network-based access control to applications because of their (often much) shorter life-spans. With lifetimes measured in minutes rather than days or weeks (or months), the strain placed on traditional IP-based firewalls is incredibly high.
Identity-based access control to applications, on the other hand, is concerned about matching users and apps, not IP addresses, and provides a better way to control access to applications based on context rather than configuration. That means rather than narrowing in on IP addresses, user requests for access can be evaluated based on client, location, device, time of day, network speed and application in addition to IP address, if you really want to look at it. That access provides a better means of determining who (or what) should (or should not) have access to a given application. And it’s much easier to provide that service for applications no matter their deployed location. An identity-based access control service can travel with an application from the data center, to the cloud, and back again if necessary, because its control is based on understanding the client and the application and applying policies in real-time irrespective of the network that carries those requests and responses.
An identity-based access control option also means providing parity across disparate environments. While relying on traditional IP-based firewalling to control access to applications means using one system in the data center and another in the cloud, the same identity-based access control service can be deployed in both environments, meaning consistent based policies that provide better compliance with corporate policies as well as less operational overhead in terms of management and auditing. That parity is something we see continuing to be in demand for those operating in a hybrid (multi-cloud) environment. In our State of Application Delivery 2016 nearly half (48%) of respondents cited policy and audit parity with on-premises as an important security factor for cloud adoption.

Additionally, the rise in security breaches caused by stolen or easily discovered credentials indicates it’s past time to move beyond basic, password-based authentication and into a more intelligent means of allowing or denying access. PWC, in its latest global security survey, noted that 91% of respondents use “advanced authentication.” Citing tokens and two-factor authentication methods, they note that advanced authentication provides significant benefits in terms of not only customer confidence, but in corporate confidence as well.
Context-based access control provides similar measures by providing multiple “factors” on which to evaluate requests. Two-factor authentication can be implemented by such solutions, but organizations can also develop authentication measures that rely on contextual clues automatically provided for an even more seamless application experience. One could argue that in the era of “things” acting as clients, a more automatic “many factor” based authentication policy is required, as most “things” don’t own mobile phones of their own and owners might not appreciate being involved in the frequent transactions required for things to synchronize and “phone home”.
Regardless of what your organizations’ determination on authentication and access control might be, it’s almost certainly true that it will not rely solely (if at all) on IP-based firewalls. Because IP-based firewalls rely on the notion that a well-defined corporate border exists. And in today’s cloudy, mobile, and almost ephemeral world of application infrastructure, that border no longer exists.
