You can't protect what you can't find
Visibility is an often-cited challenge typically referring to the ability to inspect traffic, transactions, and errors that occur during an application's execution. But there's another, perhaps more critical, meaning to visibility at the business layer: a complete inventory of the corporate application portfolio.
In the first years of our State of Application Services (then called State of Application Delivery) research, we used to ask how many apps a respondent could shut down without anyone noticing.
Our intent was to discover just how many apps were really "critical" to the business, either for profit or productivity.
We don't ask anymore, because it turns out that most folks have absolutely no idea how many apps are in their portfolio let alone what percentage is critical.
Consider the answers to the question in 2017, in which 2104 respondents took to the time to give us a response.
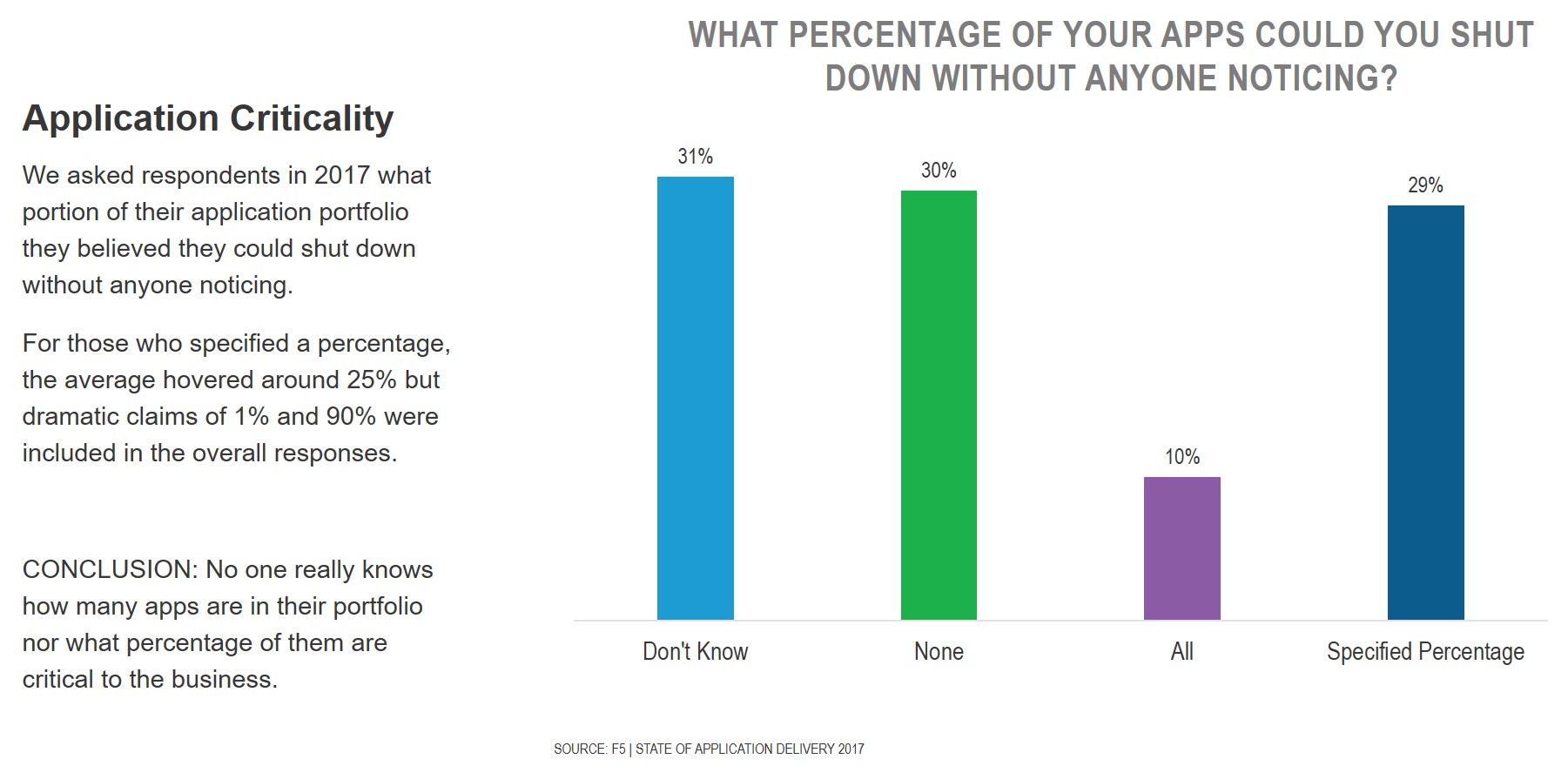
This exercise seems to validate the observation of our own Kara Sprague, who has noted that "0% of customers can report with confidence the number of applications in their portfolio."
To be fair to customers - and the market at large - a significant portion of businesses today are multi-generational. The CIO, who probably should have a good idea, likely didn't exist as a position until the late 1990s. And those who sit in the CIO chair today are likely not the same person who sat in it just a decade earlier. Cataloging and inventorying application portfolios was not something we even talked about until well after the turn of the century.
And let's not discount the impact of acquisitions and mergers on application portfolios. Even if you did know the exact number of apps in your portfolio, what about the companies you've acquired - or the one that acquired you?
The reality is that only in the last few years has the market come to recognize just how important - how critical - applications are to their respective businesses. They are the capital in which we invest today with the hopes and expectation it will pay off in the future.
Which means we really ought to protect them better, because they are under attack. Constantly.
That task is made more difficult by the ability to find them, in the first place.
But find them we must. Because while we may be protecting our most "critical" applications, we aren't protecting them all. But we should be.
