In complex IT environments including the public sector, it’s crucial to protect mission-critical applications against the evolving array of encrypted threats, including ransomware. To do so, many organizations often end up with a patchwork of multiple security solutions and network tools. However, this approach hampers AWS app performance, limits development speed and agility, and complicates management. With ever-present cyber threats, organizations like yours must avoid these obstacles to stay competitive and offer the latest digital apps and services via AWS.
Ransomware threats are rising—with a reported 73% increase in ransomware attacks in 2023 compared to 2022—and criminals are targeting companies of all sizes across every industry. The advances in phishing tactics, drive-by downloads, software vulnerability exploits, and other common attack vectors provide bad actors with a variety of avenues to gain access to your apps and network via encrypted payloads. When an IT team has assembled different security and network tools, they may struggle to properly detect and rapidly mitigate those encrypted ransomware attacks.
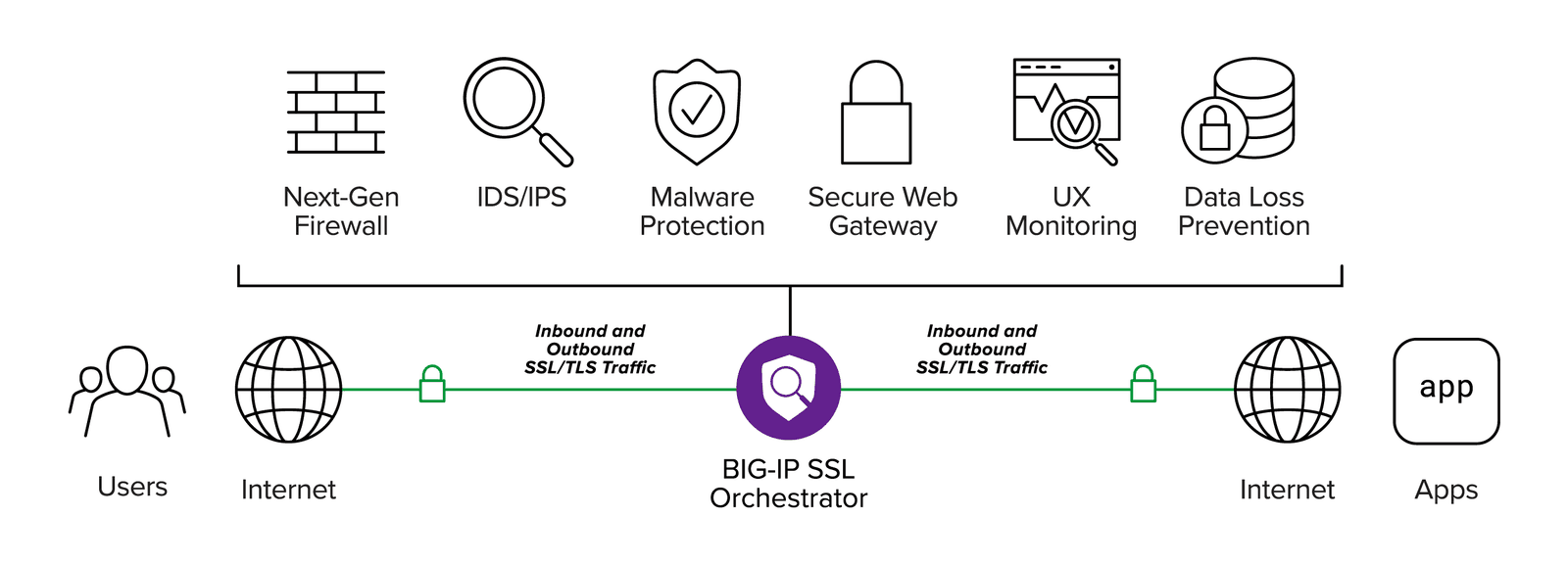
To ensure that all outbound and inbound traffic for AWS apps is protected from encrypted threats, businesses need a solution that strengthens and unifies a security approach. With F5® BIG-IP® SSL Orchestrator®, teams can gain visibility into encrypted SSL and TLS traffic and identify threats they might have missed. BIG-IP SSL Orchestrator gives your security professionals visibility into encrypted threats to safeguard AWS apps without slowing them down.
Combat ransomware effectively
BIG-IP SSL Orchestrator provides layer 3 through layer 7 protection by decrypting incoming encrypted traffic, enabling you to inspect your security stack to identify threats and re-encrypt it. BIG-IP SSL Orchestrator also makes it easy to monitor outgoing traffic to prevent malware from contacting external sites or exfiltrating data. This helps combat the double extortion method now common in ransomware—attackers steal and threaten to leak stolen data if they don’t get their initial ransom. Outbound traffic inspection also protects against phishing attacks, one of the most common ransomware vectors, by preventing the email recipient from connecting to the linked malicious site.
Manage traffic intelligently to boost performance
Delivering centralized control and policy-based steering, BIG-IP SSL Orchestrator enables you to offload encrypted traffic management for your AWS apps for greater efficiency and higher performance. Eliminate the performance degrading daisy-chaining of various security solutions by using BIG-IP SSL Orchestrator to create security based on the type of incoming traffic, ensuring optimal security against encrypted ransomware attacks. BIG-IP SSL Orchestrator adapts to changing network conditions and organizational needs, ensuring apps are always secure and available.
Enable greater agility
With a simple set of Terraform templates, administrators can combine BIG-IP SSL Orchestrator with AWS Gateway Load Balancer to gain visibility into SSL/TLS traffic flows across their AWS estate while applying robust threat detection against encrypted ransomware. Once configured, teams can inject high-performance ransomware protection into AWS. BIG-IP SSL Orchestrator is vendor-agnostic and optimized to integrate easily with the world’s leading security devices, including F5 security services, enabling leaders to maximize their security investments quickly and easily.
To learn more about how BIG-IP SSL Orchestrator can combat today’s and tomorrow’s encrypted attacks against your AWS environments, visit f5.com/aws.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
