Trickbot, the latest arrival to the banking malware scene and successor to the infamous Dyre botnet, is in constant flux, and its authors are continually adding new targets and functionality. F5 malware researchers have been monitoring Trickbot and have uncovered a new variant that substantially increases the number of German banks being targeted. Trickbot was previously focused on banks in Australia, the UK, and Canada, but only a very small number of banks in Germany, as shown in our November 7, 2016 article Little TrickBot Growing Up: New Campaign.
This latest variant, version “1000007” as shown in the base configuration below, targets banks belonging to one of Germany’s largest banking groups: Sparkassen-Finanzgruppe.
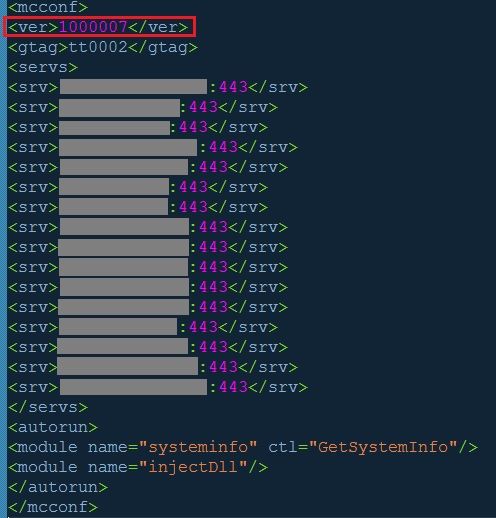
Figure 1: TrickBot Version 1000007
Figure 1: TrickBot Version 1000007
Figures 2 and 3 directly below show configuration snippets that identify some of the targeted banking domains:
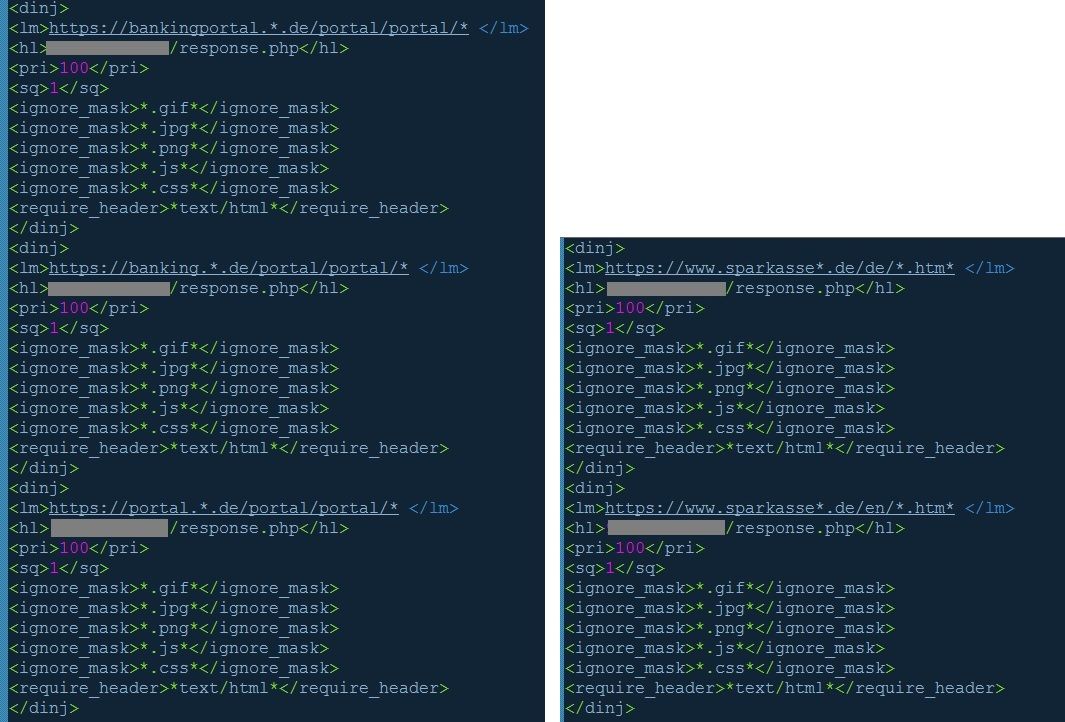
Figures 2 & 3: Banking targets in webinject configuration
Figures 2 & 3: Banking targets in webinject configuration
TrickBot version 1000007 targets the following German banks:
- Stadtsparkasse Hilchenbach
- Sparkasse Goettingen
- Kreissparkasse Traunstein-Trostberg
- Kreissparkasse Freudenstadt
- Kreissparkasse Boeblingen
- Landessparkasse zu Oldenburg
- OstseeSparkasse Rostock
- Sparkasse Kulmbach-Kronach
- Sparkasse Maerkisches Sauerland Hemer-Menden
The malware sample analyzed is referenced below with its corresponding Virus Total report. This particular sample only has a 25% detection ratio within the world’s top antivirus providers. Only time will tell if this newcomer will reach the epic scale of its predecessor, but if history is any lesson, TrickBot will surely continue to expand its target portfolio and abilities to commit fraud just as Dyre (/content/f5-labs/en/labs/articles/threat-intelligence/dyre-update-moving-to-edge-and-windows-10-with-anti-antivirus-22452.html) did in its heyday.
Sampled MD5: 43cfa53d6d327356f23bc73dc737bfcd
https://www.virustotal.com/en/file/36e474a46591f0543dbc49521f138d3aea2300b256bea0d27d5c95ae56b05a56/analysis/


