It is hardly surprising that identity theft is a significant source of frustration for, well, everyone.
Because we now live in a digital economy, identity theft can have a devastating impact on every aspect of your life as a consumer. Resulting damage to credit scores from unsatisfied repayment can prevent you from obtaining car loans, personal loans, renting a place to live, and, in some cases, from employment.
Business, of course, also pays the price for identity theft. Financial institutions are particularly vulnerable to these attacks because they are, after all, in the business of dealing with money. And money is a strong motivator.
Money is the primary motivation for 76% of cyber-attacks. The majority or 73% of these attacks and breaches were carried out by people outside the organization, including 50% by organized criminal groups and 12% by nation-state or state-affiliated actors.
-- 2018 Data Breach Investigations Report
Fraudulent accounts opened, used, and never repaid weigh down financial institutions' balance sheets. In 2018, new account fraud accounted for $3.4 billion in losses, up from $3 billion in 2017, according to Javelin Strategy. According to the FTC, the top type of identity theft in 2019 was credit card fraud via new accounts. Someone stole someone else's identity, and used it to open a line of credit.
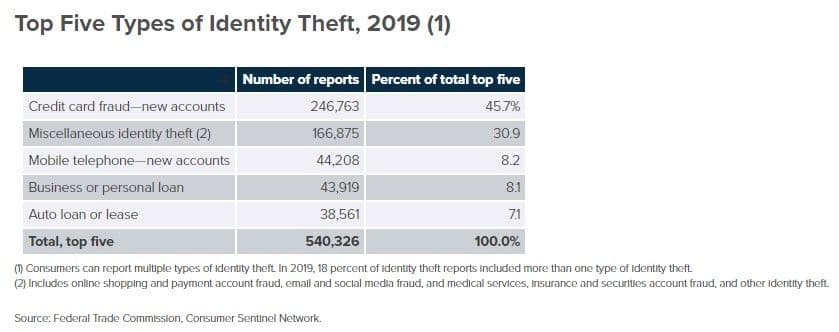
Nearly 250,000 attempts at credit card fraud in one year. That breaks down to one attempt every two minutes every day of the year.
This is not something we can stop by throwing people at the problem.
First, we don't have enough people skilled at recognizing fraud to conduct a manual review of every account opening. Even if we did, a human being can't accurately determine fraud from analysis of an application in under two minutes. Consider the last time you applied for any type of credit in person. It took far longer than two minutes.
Lastly, consumers are not willing to wait for manual review. They aren't. They will abandon any app and digital process that, in their opinion, takes too long to respond. The definition of "too long" varies but in general, it's not more than two minutes.
Digital account opening (DAO) is part of just about every business today but have been widely embraced by financial institutions due in part to the rise of FinTech. As a nearly pure digital process today, the best way to address the scale and speed of analysis required to prevent fraud is technology.
More Than Data
DAO is a digital workflow. That means it incorporates multiple interfaces (mobile, web, chatbots) as well as modern applications and almost certainly traditional backend systems. Tracking a single application through the complex interactions between applications and, potentially, across cloud properties is not a trivial task. And while the new, modern components of a digital account opening workflow may be instrumented to generate the right data, chances are traditional backend systems are not.
Even if we leverage the on average ten application services that process traffic and can emit the right data, we are left with the challenge of analyzing it in the context of the transaction. This requires having access to data generated from multiple systems and locations. Today, we have many sources of data. That data is not correlated across a workflow in part because it's reported to siloed systems with their own dashboards and alerting systems. Today, we don't have the contextual awareness of all the variables needed to accurately identify an attempt to fraudulently open an account. Moreover, many rely on outdated techniques that are readily evaded by attackers.
Traditional CAPTCHA techniques and rudimentary JavaScript-based inspection of client devices are not enough to detect, let alone prevent, exploitation of DAO and related digital experiences. Traditional IP-based defenses are not enough. I can spoof my IP, my user-agent, and mimic mouse movements. Using the power of modern computing, I can fool most CAPTCHA systems. Attackers today are far too experienced and sophisticated to let such simple techniques stand in the way of fraudulently opening a new account. They rapidly adapt to new techniques and quickly discover how to overcome them.
The technology we need must be just as capable of learning and adapting as attackers.
"Savvy risk and fraud management in 2020 will combine the benefits of machine learning, applied intelligence, and context-driven analytics, along with anomaly detection to create a manageable, multi-tiered approach."
-- Bottomline, State of Digital Account Opening & Onboarding
While this statement is a mouthful, it accurately represents the type of technology we need today to prevent fraud. We need AI-infused analytics capable of ingesting and analyzing vast quantities of data in minimal time. We need analytics capable of correlating data across the entire workflow to prevent fraud at the speed it occurs.
Detecting fraud today requires more than just data. It requires correlation of data, collected from as many points in the digital workflow as possible, and the ability to quickly analyze results.
That's what F5 intends to do: build a multi-purpose application analytics platform capable of providing business with the insights they need to scale, secure, and optimize digital workflows at speed.
About the Author

Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.
