
The Sensor Intel Series is created in partnership with Efflux , who maintains a globally distributed network of sensors from which we derive attack telemetry.
------------------------------------------------------------------------------------------
Welcome to the February 2023 installment of the Sensor Intelligence Series. This series offers web application vulnerability targeting intelligence. We produce this intelligence by analyzing scanning and exploit attempts logged by sensors run by our data partners, Efflux. As always, our analysis is limited to traffic on ports 80 and 443.
CVE-2020-8958, an IoT vulnerability in several Guangzhou/VSOL routers, has been the top-targeted vulnerability we track for six of the last seven months, and it retains its top spot in February as well. However, its traffic declined 47% compared with January, making its recent volume closer to what we observed in November. Perhaps this spells the beginning of its decline, although as you’ll see below in Figure 2, we’ve seen CVEs in general and this one in particular seem to fall off of a cliff, only to rebound the following month.
Also notable this month is the dramatic growth in CVE-2020-25078, which is also an IoT vulnerability but this time in several IP cameras. On the one hand the volume of traffic scanning for this vulnerability was not remarkable, with ~3600 connections in February, but only 200 connections were attempted in January, which means traffic increased roughly 18-fold in one month. Let’s see what else changed to put this growth in context.
February Vulnerabilities by the Numbers
Figure 1 shows the top ten vulnerabilities and their traffic for February. Below CVE-2020-25078 we see several CVEs that have been near the top throughout 2022, such as CVE-2017-9641 and the CVE-less 2018 JAWS digital video recorder vulnerability.1
However, also notable is CVE-2020-0688, a remote code execution (RCE) vulnerability in Microsoft Exchange Server. This is obviously not a new vulnerability, but we only recently identified it in our logs, despite its presence throughout this project.
| CVE-2020-25078 A remote administrator password disclosure vulnerability in several D-Link IP Cameras: DCS-2530L (before 1.06.01), DCS-2670L (before 2.03), DCS-P703, and DCS-46xx/47xx/48xx Series. NVD |
| CVE-2020-0688 A remote code execution vulnerability in Microsoft Exchange Server resulting from a memory corruption flaw. NVD |
Table 1 shows traffic volumes for all vulnerabilities that we track. In addition to CVE-2020-0688, which we mentioned earlier, we also added CVE-2014-8379, a file upload vulnerability that had not previously shown up in our logs.
| CVE Number | Count | Change |
| CVE-2020-8958 | 7606 | -6600 |
| CVE-2020-25078 | 3590 | 3388 |
| CVE-2017-9841 | 1983 | -96 |
| 2018 JAWS Web Server Vuln | 1688 | -1609 |
| CVE-2022-22947 | 1482 | -376 |
| CVE-2020-0688 | 1447 | -150 |
| CVE-2022-41040/CVE-2021-34473 | 1270 | -516 |
| CVE-2018-10561 | 935 | 33 |
| CVE-2018-13379 | 530 | 75 |
| CVE-2021-3129 | 487 | -71 |
| CVE-2019-9082 | 442 | -149 |
| CVE-2021-28481 | 384 | -105 |
| CVE-2021-26086 | 348 | 141 |
| CVE-2021-40539 | 320 | -138 |
| CVE-2017-1000226 | 311 | 122 |
| NETGEAR-MOZI | 294 | -37 |
| CVE-2014-2908 | 284 | -36 |
| CVE-2017-18368 | 279 | -146 |
| Citrix XML Buffer Overflow | 274 | -53 |
| CVE-2019-18935 | 243 | -234 |
| CVE-2020-15505 | 219 | -14 |
| CVE-2022-40684 | 201 | 88 |
| CVE-2013-6397 | 188 | -69 |
| CVE-2019-12725 | 181 | 150 |
| CVE-2021-26855 | 129 | 71 |
| CVE-2007-3010 | 113 | 76 |
| CVE-2021-44228 | 106 | -51 |
| CVE-2014-8379 | 80 | NA |
| CVE-2021-26084 | 66 | 24 |
| CVE-2019-9670 | 63 | -3 |
| CVE-2021-22986 | 52 | 2 |
| CVE-2021-41277 | 27 | 24 |
| CVE-2021-21985 | 22 | -38 |
| CVE-2022-1388 | 20 | 13 |
| CVE-2020-9757 | 17 | 3 |
| CVE-2022-22965 | 13 | -20 |
| CVE-2020-3452 | 11 | -25 |
| CVE-2020-25506 | 10 | -2 |
| CVE-2021-33564 | 8 | -2 |
| CVE-2020-13167 | 6 | 4 |
| CVE-2020-17506 | 5 | 2 |
| CVE-2021-25369 | 5 | 2 |
| CVE-2015-3897 | 4 | 0 |
| CVE-2018-7600 | 4 | -1 |
| CVE-2020-17505 | 4 | 2 |
| CVE-2021-20167 | 4 | 1 |
| CVE-2021-29203 | 4 | -6 |
| CVE-2021-33357 | 4 | 0 |
| CVE-2018-17246 | 3 | -1 |
| CVE-2018-7700 | 3 | 1 |
| CVE-2019-8982 | 3 | 0 |
| CVE-2021-3577 | 3 | 2 |
| CVE-2022-1040 | 3 | -1 |
| CVE-2008-6668 | 2 | 0 |
| CVE-2017-0929 | 2 | 0 |
| CVE-2018-1000600 | 2 | 1 |
| CVE-2020-28188 | 2 | 1 |
| CVE-2020-7796 | 2 | -2 |
| CVE-2021-21315 | 2 | 1 |
| CVE-2021-32172 | NA | NA |
Table 1. CVE targeting volumes for February, along with change from January. We added two new CVEs to our list of signatures this month: CVE-2020-0688 and CVE-2014-8379.
Targeting Trends
To better understand how February contrasts with previous months, Figure 2 shows a bump plot of targeting frequency. To avoid overplotting, this shows thirteen CVEs which together constitute the top five for each of the twelve months.
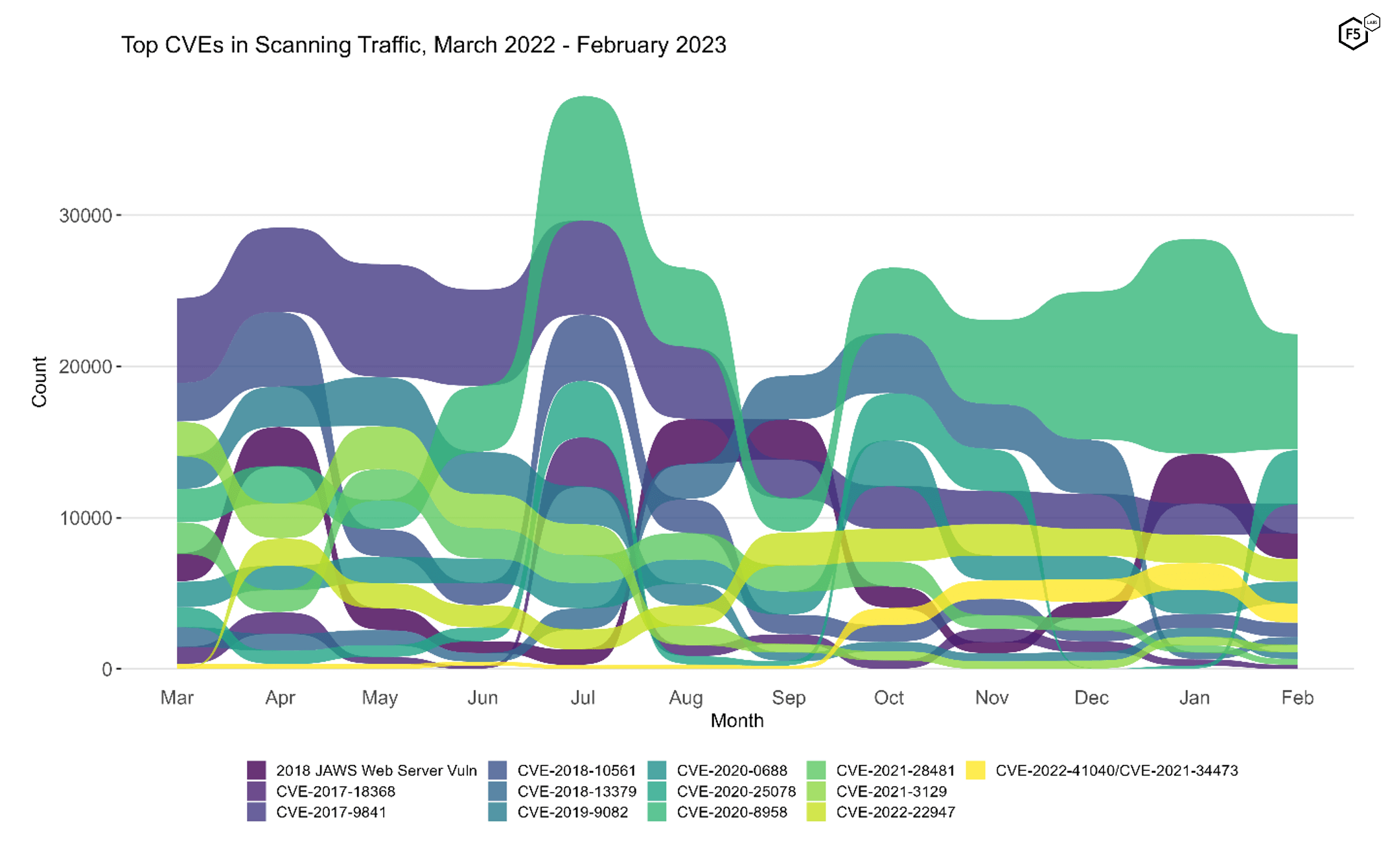
Figure 2. Evolution of vulnerability targeting in the last twelve months. Note the slight decline in 2020-8958 as well as the dramatic growth of 2020-25078.
Long Term Trends
Figure 3 shows traffic volume over the past year for all of the CVEs we track. Other than the growth of 2020-25078 discussed above, recent months have not seen dramatic changes in the more frequently-targeted CVEs near the top of the plot.
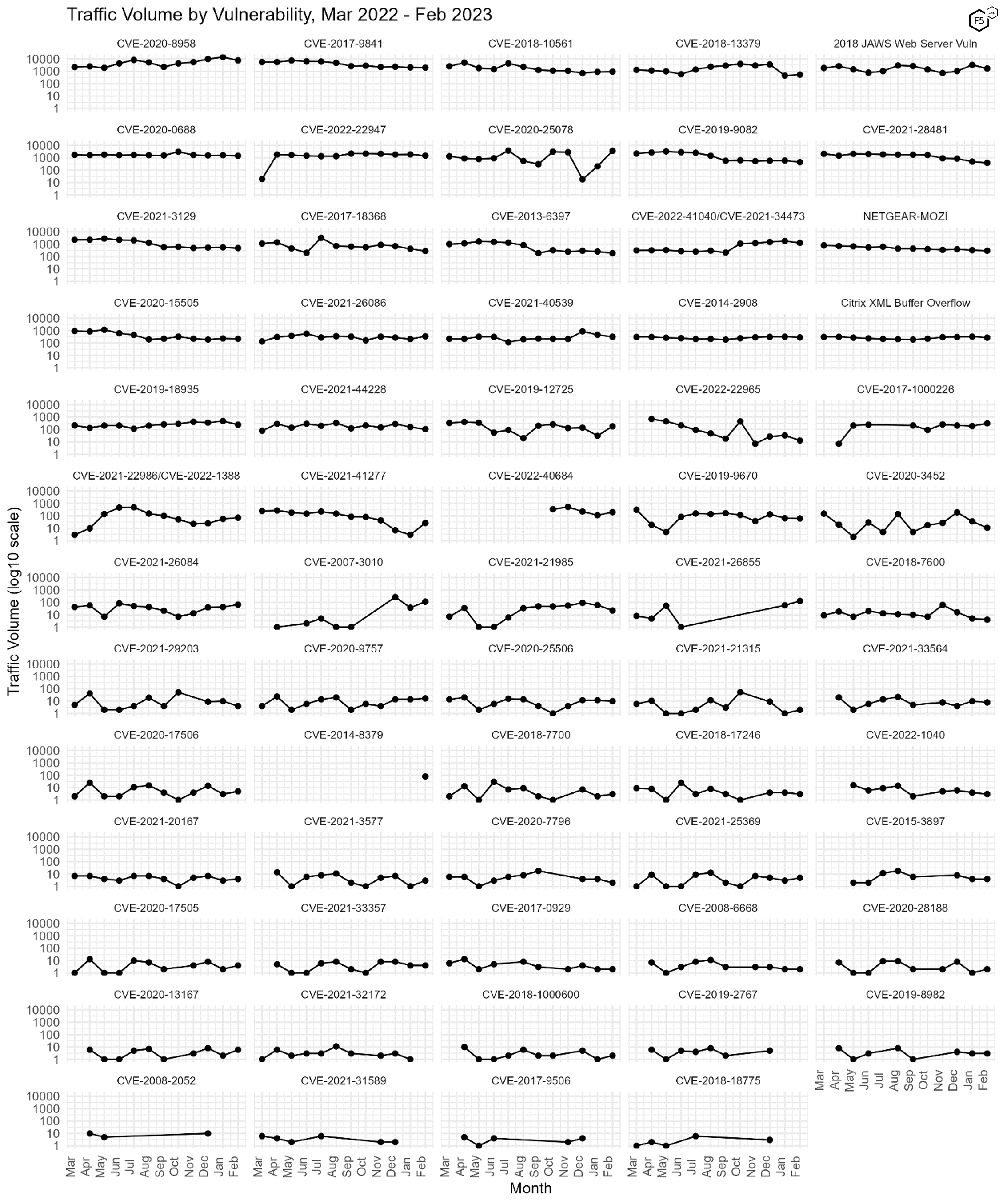
Figure 3. Traffic volume by vulnerability. The resurgence of 2020-25078 is visible here (2nd row, middle column). The log10 scale on the y-axis illustrates how dramatic the growth has been in 2023.
Conclusions
As we often have in the last few months, we can’t help but notice the prevalence of two kinds of vulnerabilities in our logs: RCEs and IoT vulns. The value RCEs offer to attackers is obvious. As for IoT vulnerabilities, it seems fitting that as one IoT vuln (CVE-2020-8958) finally stops growing in prevalence, another (CVE-2020-25078) shoots up in volume to “help out.” All this IoT attention adds to our suspicion that attacker infrastructure for DDoS attacks remains a high priority. For more on DDoS please see the 2023 DDoS Attack Trends, and we’ll see you in a month with more intel.
| CVE-2020-8379 A file upload vulnerability in the Creative Contact Form plugin for WordPress and Joomla. Attackers can upload a PHP file and then access it on the server at another endpoint. NVD |
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


