
This is the full-spectrum, director’s cut version of the Application Protection Report, untrammeled by petty concerns like brevity or toner prices (for the shorter version, please see our Summary). This report pulls together the various threats, data sources, and patterns in the episodes into a unified line of inquiry that began in early 2019, picking up where the 2018 Application Protection Report left off, and concluded in early 2020 with updated data on 2019 breaches and architectural risk.
One of the goals of the Application Protection Research Series is to place security trends and patterns into a single long-term picture, to get away from news cycles and hype that only focus on new threats or vulnerabilities that may not even be applicable. This perspective also allows us to see linkages between the different subdomains and foci that make up the complex and porous field we call information security.
One of the underlying themes for the 2019 series has been that changes in the ways that we design, build, and deploy applications have been drivers for risk. From third-party services driving the rise of an injection attack known as formjacking, to a growing list of seemingly avoidable API breaches, to the prevalence of platforms running on languages with old and documented flaws, there has been a good deal of goalpost movement for defenders. The implication is that many of the people who are making decisions with significant ramifications for security—system owners, application architects, DevOps teams—are generally placing other priorities ahead of security. Based on the acceleration of trends in 2019 that we identified from 2018, it seems that this tension will characterize the next few years of the security arms race.
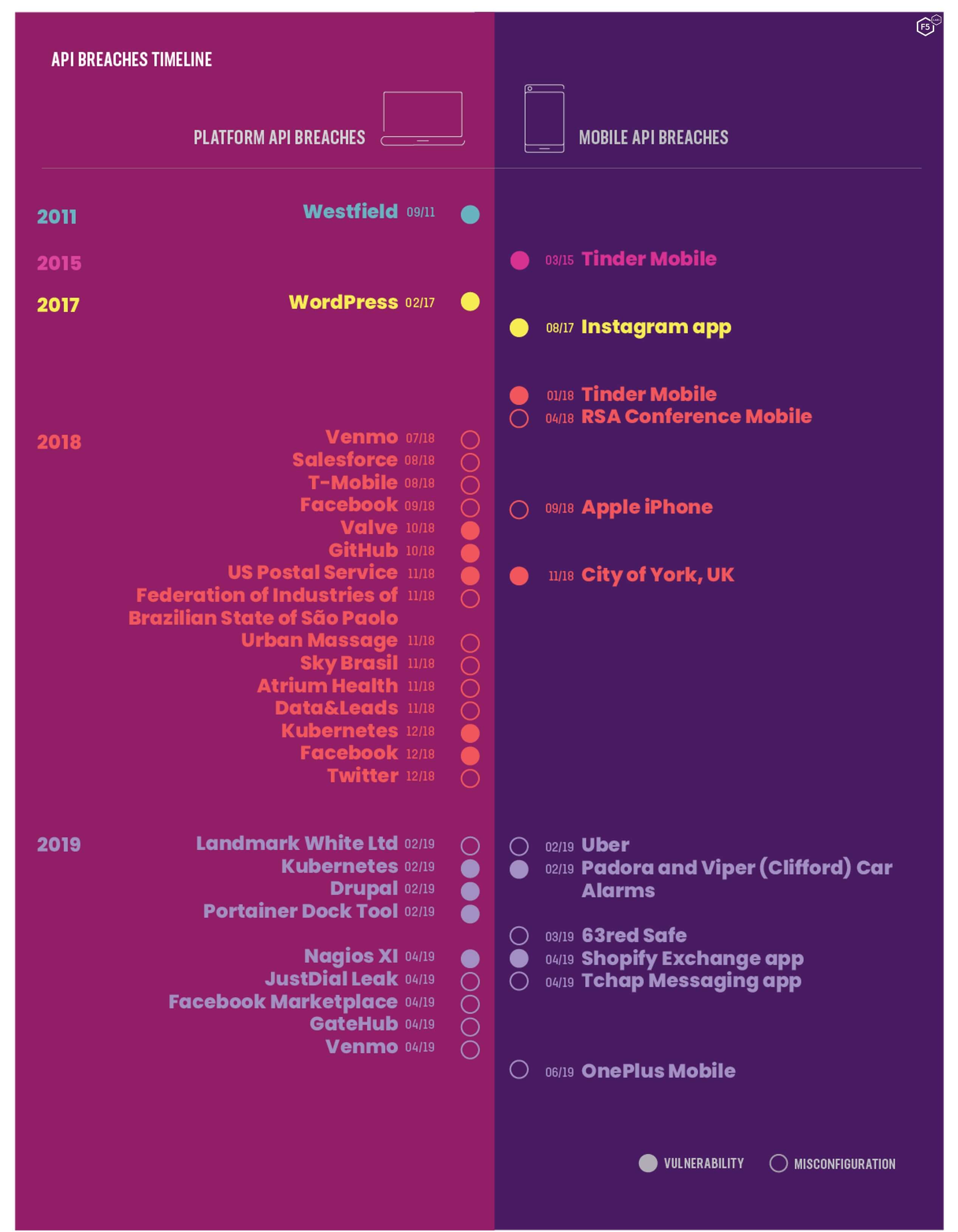
Figure 1. A timeline of API breaches showing platform type and simplified breach cause. This is part of the API section of the bigger report.
Another theme of the last few years of application security research has been the prominence and great success of access-tier attacks. By this we mean attacks that focus on the intersection between human users and information systems. These attacks can focus on humans, like phishing or other social engineering, or on machines, like credential stuffing and brute force. It can be tempting to look at phishing success rates and conclude that our battle is unwinnable. Instead, we take this as evidence that technical controls are working, and that more straightforward paths to our data have become impassable. It also indicates that there will always be some aspects of the security problem that don’t fit well into the traditional body of security knowledge, and people—squishy, unpredictable, occasionally lovable—will always be the most prominent of these.
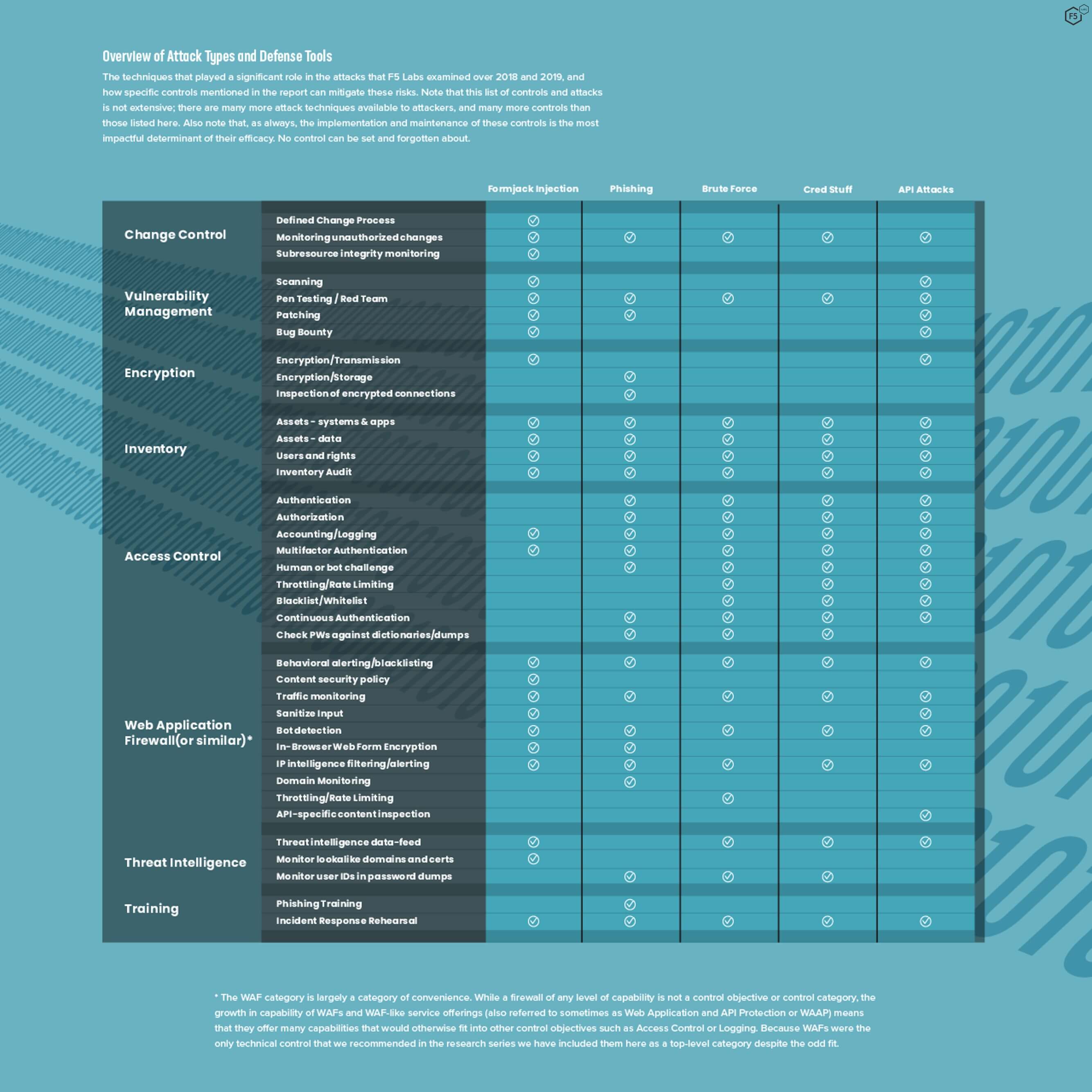
Figure 2. The control matrix from the report, showing some of the risks that we've identified and which control categories can help mitigate risk.
The matrix above, which is also included at the conclusion of the report, shows how different types of controls can help mitigate the specific vectors we’ve identified in this research. At the end of each section, we go into greater detail about how to actually prevent or mitigate some of the attacks we’ve documented here. After all, a report called Application Protection wouldn’t be any use if it didn’t help protect any applications. As you read the report and consider our findings, recommendations, and predictions for the future, we ask three things:
Think on how our work resonates with your own experience in your own systems
Consider what questions and follow-up research this report provokes for you
Share those thoughts and questions with us for future work
Our line of work demands communication and collaboration, and F5 Labs’ sole mission is to put useful information in the hands of defenders—tell us how we can help!


