
Introduction
Welcome to F5 Labs’ third annual report on phishing and fraud. Once again, we’re bringing you data from our partner Webroot® as well as the F5 Security Operations Center.
Phishing continues to be a major source of profit for cyber-criminals, and a big hassle for cyber-defenders. In the F5 Labs 2019 Application Protection Report (/content/f5-labs-v2/en/labs/application-protection.html), F5 Labs found that phishing was responsible for 21% of breaches, the second largest cause of breach reported by U.S. companies. The number one reported breach cause (absent other details) was unauthorized access to email. Because phishing can commonly grant unauthorized access to email, it’s likely phishing is also the cause of some of these breaches. So there you have it: one of the most prevalent ways attackers are breaching data is via phishing.
Anyone who’s been reading our reports over the years should not be surprised by this, since phishing has been bouncing into the top spot every time we look at breach causes. Speaking of breach causes, the 2019 Application Protection Report showed that the finance, health, education, non-profit, and accounting sectors were significantly more likely to be compromised through phishing or illicit email access than any other means.
Why so much phishing? The reason is simple: it’s easy and it works. Attackers don’t have to worry about hacking through a firewall, finding a zero-day exploit, deciphering encryption, or rappelling down an elevator shaft with a set of lockpicks in their teeth. The hardest part is coming up with a good trick email pitch to get people to click on, and a fake site to land on.
The Extant State of Phishing Attacks
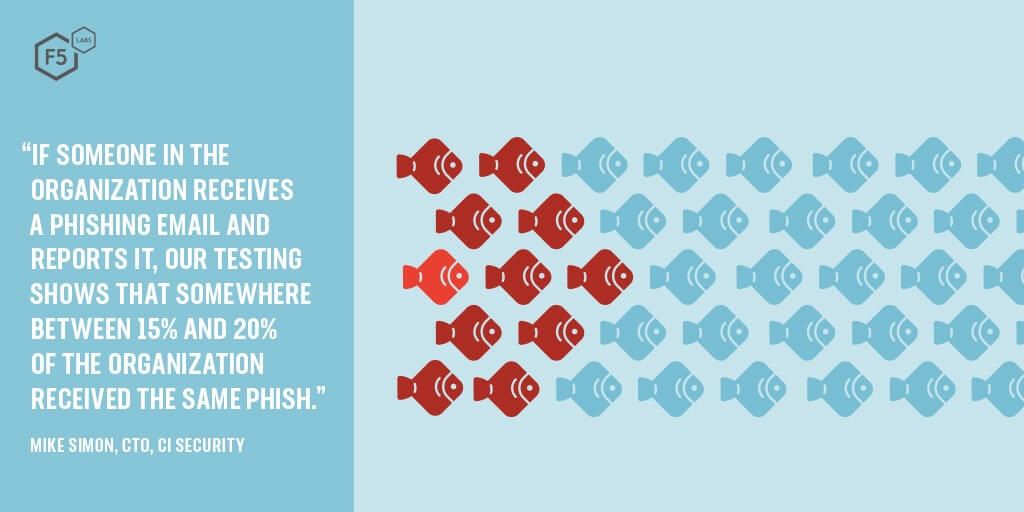
It’s 2019 and we’re still dealing with phishing, which stretches back 25 or more years. Mike Simon, CTO of managed detection and response firm CI Security, sees a lot of security incidents. We asked him what he thought of the current state of phishing attacks.
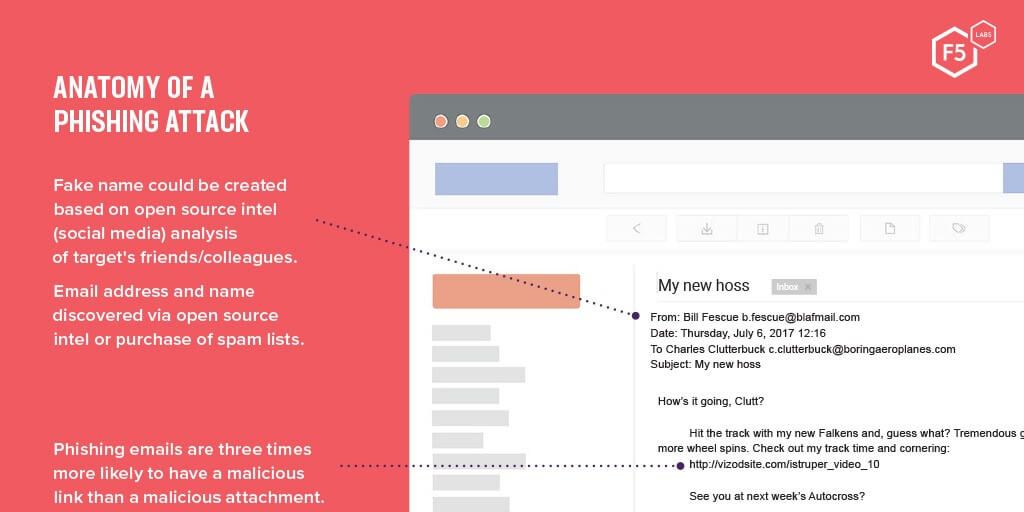
Anatomy of a Phishing Attack in 2019
There’s plenty of phish in the sea… er, Internet, so let’s debone an aggregate phishing attack and take a look. Webroot® gave us a detailed snapshot of phishing data for the month of July 2019, which we sliced and tweezed apart to show you what’s going on in phishing.
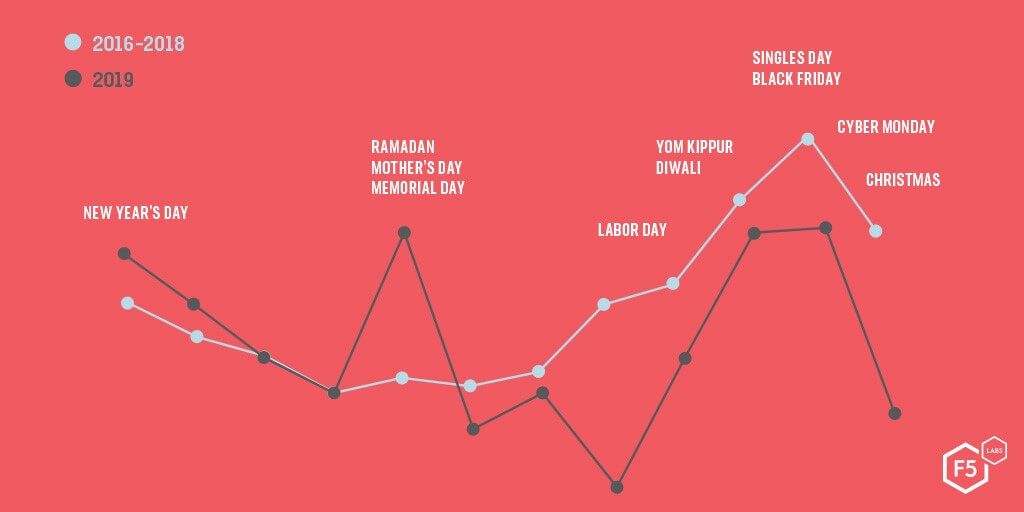
Phishing Trends
Does phishing have a season? Last year, we looked at three years worth of phishing attack data collected from the F5 SOC and discovered a 50% increase in phishing attacks during the “holiday” season (roughly October through January). This was expected behavior because it’s easier to trick people into opening up package delivery notifications or receipt emails during the height of holiday shopping.
However, the past year of phishing hasn’t shown the same pattern. The rise of social media makes personal data freely available to attackers anytime, so they don’t have to wait for the end-of-year holiday shopping season to trick unsuspecting shoppers. As a result, we expect phishing to become a more balanced year-round sport. Looking at phishing trends in 2019, there is a spike in attacks in springtime, followed by another spike in the months leading up to end-of-year holidays and purchasing events, likely attributed to large cybercrime campaigns.
Responding to Phishing
Every organization is on the receiving end of phishing attacks, whether they’re discovered or not. Given the success rate of phishing and its status as the top root cause of breaches, every organization needs a phishing response. Such a strategy must include security awareness training, and the following technical security controls:
- Deploy multifactor authentication (MFA)
- Clearly label all email from external sources to prevent spoofing
- Use antivirus (AV) software
- Have a web filtering solution
- Inspect encrypted traffic for malware
- Make it easy for users to report phishing
- If people are clicking on phishing email links, get visibility
Download the Full Report
We've gone more in depth in all of these topics in the full report, which is one click away through the button below. We won't even ask for your email address.


