
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
-----------------------------------------------------------------------------
Introduction
Welcome to the October 2024 installment of the Sensor Intelligence Series, our monthly summary of vulnerability intelligence based on distributed passive sensor data.
Following on from our last month’s analysis, scanning of CVE-2017-9841 has fallen to barely a trickle.
CVE-2023-1389, an RCE vulnerability in TP-Link Archer AX21 consumer routers, which has been consistently towards the top of our ranking, continues for a third month to be the most scanned for CVE that we track, although it too has fallen off somewhat.
BotPoke Scanner Switches IP Addresses
The last few months we have been tracking a pattern of scanning which was strongly associated with a specific IPv4 address, 141.98.11.114, which we noted was exhibiting signs of being the BotPoke scanner.
While last month it fell off slightly, this month it simply disappeared from our logs entirely.
This does not mean that the scanning isn’t happening. In fact, what has happened is that the scanning activity associated with the BotPoke scanner has moved from a Lithuanian address to one in Hong Kong, specifically 154.213.184.3. This IP continues the tradition of being our most seen IP, and accounts for 31.5% of all the traffic we observed this month.
Other than changing IPs, this scanner continued to do exactly what it did last month and targeted the same URIs and many of the same regions where our sensors reside.
October Vulnerabilities by the Numbers
Figure 1 shows October attack traffic for the top ten CVEs that we track. CVE-2023-1389 is dominating this visualization, with much more traffic than any of the other top 10. The massive increase in scanning for this vulnerability throws off the proportionality of this view, however. See further down for an easier to understand view using a logarithmic scale in Figure 3.
Targeting Trends
Figure 2 is a bump plot showing the change in traffic volume and position over the last twelve months. We can see quite clearly the still heavy scanning for CVE-2023-1389, as well as the continued decline in scanning for CVE-2017-9841, and we can just make out CVE-2020-11625 rising to second place, albeit with a relatively small amount of traffic.
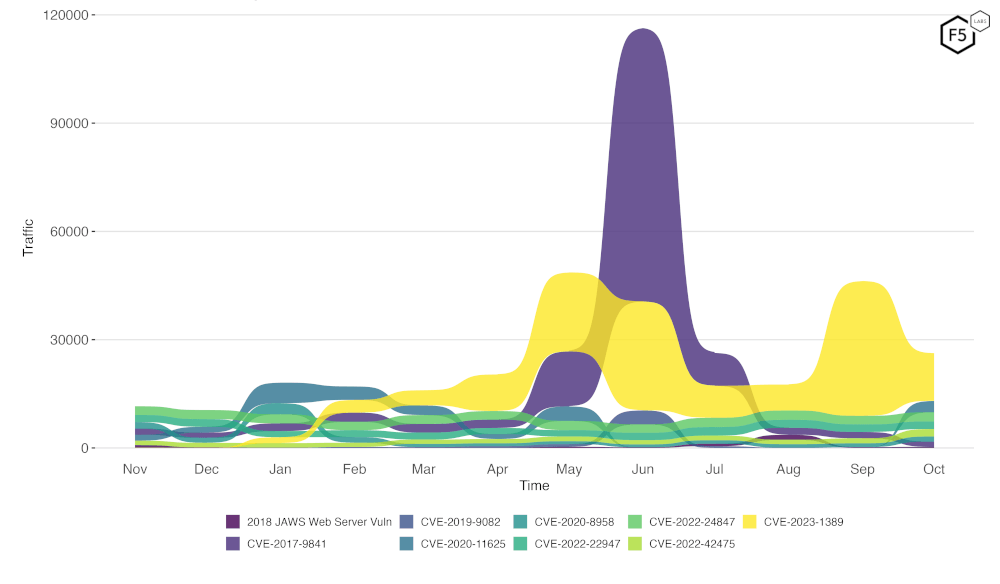
Figure 2: Evolution of vulnerability targeting in the last twelve months. Note the continued falloff in scanning for CVE-2017-9814, and the slight increase in scanning for CVE-2020-11625.
Long Term Trends
Figure 3 shows traffic for the top 20 CVEs by all-time traffic, followed by a monthly average of the remaining CVEs. Again, one can easily see the precipitous rise and fall of scanning for CVE-2017-9841, as well as the steady rise of scanning for CVE-2023-1389, and then a slight dip this month. At the top row all the way to the right, we can see CVE-2020-11625 rising in what appears a very dramatic fashion, but remember this is a logarithmic scale, so we’re really seeing a rise from single digits to 1000s.
In the lower left corner, you can see the average of all the other 110 CVEs we currently track and note that these have remained constant this month.
Also of note - CVE-2017-18368. Scanning for this CVE has been very jagged and this month is no different.
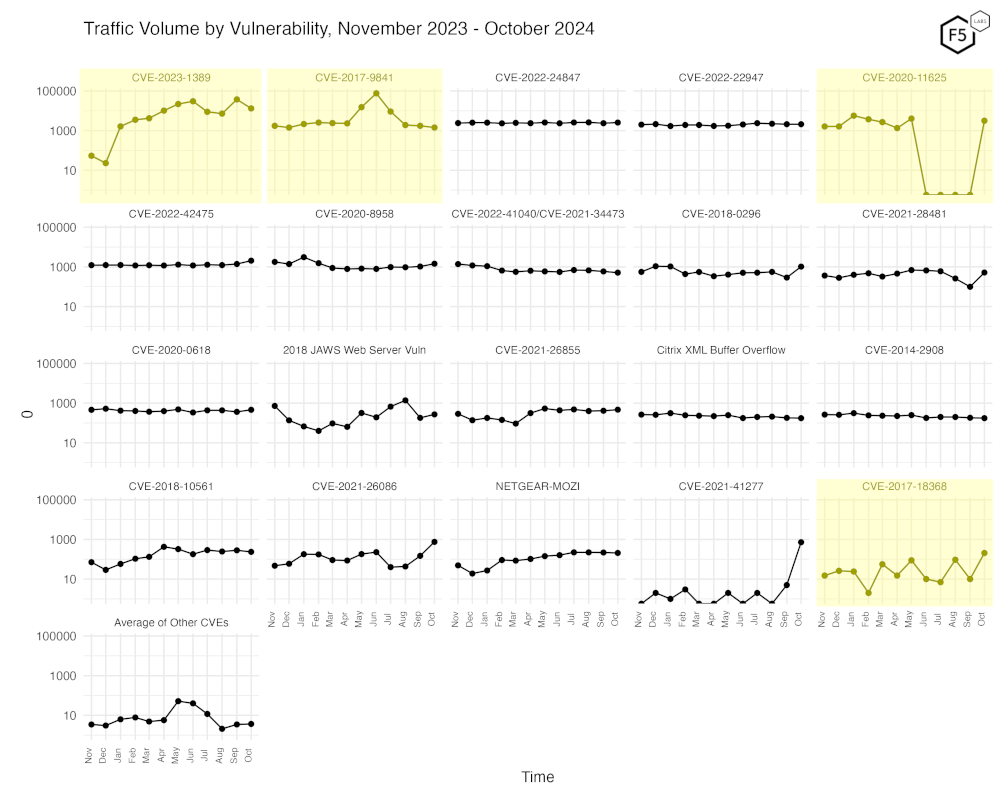
Figure 3. Traffic volume by vulnerability. This view accentuates the recent changes in both CVE-2023-1389 and CVE-2017-9841, well as the increase in scanning for CVE-2020-11625 and CVE-2017-18368.
Conclusions
The frequent changing of the infrastructure scanning agents use is to be expected. Sadly, many ISPs and providers around the world are all too happy to turn a blind eye to this sort of behavior, and while the BotPoke scanner is engaging in at least somewhat benign activity, many other scanners actively try to exploit vulnerabilities and can frequently do so without much action being taken. To be fair, C2 and malware distribution sites are frequently taken down – but we wonder how much more effective such efforts would be if internet access providers were to be more engaged at the beginning of the process.
And on that cheery note, see you next month!
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


