
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
------------------------------------------------------------------------------------------
Welcome back to the Sensor Intelligence Series, our recurring monthly summary of vulnerability intelligence based on distributed passive sensor data. This time, we added a section discussing the overall level of scan traffic month to month, to give a better sense of how the ups and downs of the various CVEs we track compare to overall variations in traffic volume.
So, without any further ado, let’s dig into the changes we saw in October for the CVEs we track, so the people in the USA at least can get back to eating their Thanksgiving leftovers.
October Vulnerabilities by the Numbers
Figure 1 shows the traffic for the top 10 CVEs in October. CVE-2020-8958, a Guangzhou router command injection vulnerability, has been our top seen CVE for much of the past year, returning to the top in August and September 2023, and just this month being displaced from the premier spot by CVE 2017-9841, an RCE vulnerability PHPUnit. CVE-2017-9841 has been a top contender in the past but has been falling in the last several months. In third is CVE-2022-24847, an RCE in the open-source GeoServer software which we’ve seen towards the top position before. Overall traffic in the CVEs we track dropped again as it did in September, with the notable exception of CVE 2017-9841, which rebounded significantly from its general downward trend after it previously peaked in July.
Table 1 shows traffic for October, change in traffic from September, CVSS v3.x score, and EPSS scores for 70 CVEs. Our list of CVEs with confirmed attack or scanning traffic currently stands at 82, but 11 vulnerabilities saw no traffic in either September or October and so don’t make this table.
| CVE Number | October Traffic | Change from September | CVSS v3.x Score | EPSS Score |
| CVE-2017-9841 | 2776 | 1475 | 9.8 | 0.97477 |
| CVE-2020-8958 | 2773 | -1415 | 7.2 | 0.76447 |
| CVE-2022-24847 | 2367 | -134 | 7.2 | 0.00067 |
| CVE-2022-22947 | 2216 | 550 | 10 | 0.97481 |
| CVE-2022-42475 | 1219 | -189 | 9.8 | 0.38721 |
| CVE-2022-41040/CVE-2021-34473 | 1199 | -211 | 9.8 | 0.97344 |
| CVE-2021-40539 | 855 | 431 | 9.8 | 0.97402 |
| CVE-2021-28481 | 752 | -60 | 9.8 | 0.0405 |
| CVE-2021-26855 | 535 | 32 | 9.8 | 0.97494 |
| 2018 JAWS Web Server Vuln | 428 | 14 | NA | #N/A |
| CVE-2020-0618 | 396 | -21 | 8.8 | 0.97449 |
| CVE-2014-2321 | 280 | 258 | NA | 0.96364 |
| Citrix XML Buffer Overflow | 238 | -13 | NA | #N/A |
| CVE-2014-2908 | 237 | -19 | NA | 0.00594 |
| CVE-2017-18368 | 166 | -540 | 9.8 | 0.97501 |
| CVE-2019-18935 | 160 | -34 | 9.8 | 0.94355 |
| CVE-2021-44228 | 146 | 5 | 10 | 0.97453 |
| CVE-2020-25213 | 120 | 35 | 9.8 | 0.97352 |
| CVE-2018-13379 | 119 | 2 | 9.8 | 0.97336 |
| CVE-2021-26086 | 117 | -3 | 5.3 | 0.54993 |
| CVE-2017-1000226 | 104 | -2 | 5.3 | 0.00127 |
| CVE-2022-40684 | 84 | 22 | 9.8 | 0.95286 |
| CVE-2018-10561 | 59 | 3 | 9.8 | 0.97317 |
| CVE-2020-17496 | 40 | 7 | 9.8 | 0.97451 |
| CVE-2021-3129 | 40 | -6 | 9.8 | 0.97509 |
| NETGEAR-MOZI | 31 | -27 | NA | #N/A |
| CVE-2019-9082 | 23 | -32 | 8.8 | 0.97467 |
| CVE-2020-3452 | 20 | 4 | 7.5 | 0.97541 |
| CVE-2019-12725 | 8 | -2 | 9.8 | 0.96271 |
| CVE-2018-20062 | 7 | 1 | 9.8 | 0.96823 |
| CVE-2022-22965 | 7 | -21 | 9.8 | 0.97469 |
| CVE-2020-9757 | 6 | 4 | 9.8 | 0.96999 |
| CVE-2018-7600 | 4 | -3 | 9.8 | 0.97555 |
| CVE-2020-25078 | 4 | -438 | 7.5 | 0.96829 |
| CVE-2021-22986/CVE-2022-1388 | 4 | -46 | 9.8 | 0.9745 |
| CVE-2018-17246 | 3 | -1 | 9.8 | 0.96913 |
| CVE-2021-21985 | 3 | 0 | 9.8 | 0.9737 |
| CVE-2017-0929 | 2 | 2 | 7.5 | 0.03588 |
| CVE-2017-11511 | 2 | 2 | 7.5 | 0.3318 |
| CVE-2018-1000600 | 2 | 1 | 8.8 | 0.95579 |
| CVE-2018-7700 | 2 | 2 | 8.8 | 0.73235 |
| CVE-2020-17505 | 2 | 0 | 8.8 | 0.96839 |
| CVE-2020-17506 | 2 | -1 | 9.8 | 0.95885 |
| CVE-2020-25506 | 2 | -4 | 9.8 | 0.97424 |
| CVE-2020-28188 | 2 | -1 | 9.8 | 0.9724 |
| CVE-2020-7961 | 2 | -4 | 9.8 | 0.97414 |
| CVE-2021-26084 | 2 | -27 | 9.8 | 0.97173 |
| CVE-2021-29203 | 2 | 0 | 9.8 | 0.95745 |
| CVE-2021-33564 | 2 | 0 | 9.8 | 0.07998 |
| CVE-2013-6397 | 1 | 1 | NA | 0.65834 |
| CVE-2017-11512 | 1 | 1 | 7.5 | 0.97175 |
| CVE-2019-2767 | 1 | 0 | 7.2 | 0.14972 |
| CVE-2019-8982 | 1 | -3 | 9.8 | 0.02146 |
| CVE-2020-13167 | 1 | -5 | 9.8 | 0.97419 |
| CVE-2020-15505 | 1 | -2 | 9.8 | 0.97504 |
| CVE-2020-7796 | 1 | -1 | 9.8 | 0.72496 |
| CVE-2021-20167 | 1 | 0 | 8 | 0.95282 |
| CVE-2021-21315 | 1 | 0 | 7.8 | 0.96899 |
| CVE-2021-32172 | 1 | -1 | 9.8 | 0.26193 |
| CVE-2021-33357 | 1 | 0 | 9.8 | 0.96598 |
| CVE-2021-3577 | 1 | -1 | 8.8 | 0.96855 |
| CVE-2008-6668 | 0 | -1 | NA | 0.00359 |
| CVE-2015-3897 | 0 | -2 | NA | 0.83225 |
| CVE-2017-17731 | 0 | -4 | 9.8 | 0.14043 |
| CVE-2021-25369 | 0 | -1 | 6.2 | 0.00118 |
| CVE-2021-27065 | 0 | -92 | 7.8 | 0.96908 |
| CVE-2021-41277 | 0 | -8 | 10 | 0.11624 |
| CVE-2022-1040 | 0 | -1 | 9.8 | 0.97072 |
| CVE-2022-35914 | 0 | -1 | 9.8 | 0.96807 |
| CVE-2023-25157 | 0 | -2 | 9.8 | 0.38863 |
Table 1. October traffic, change from September, CVSS and EPSS scores for 70 CVEs.
Targeting Trends
To better assess rapid changes in attack traffic, Figure 2 shows a bump plot, which plots both traffic volume and changes in rank. The 12 CVEs shown here represent the top five for each of the twelve months. Notable in this month’s plot, as previously mentioned, is the rise of CVE 2017-9841. While not anywhere near its former peak in July, it did see a sharp reversal from the general downward trend previously observed.
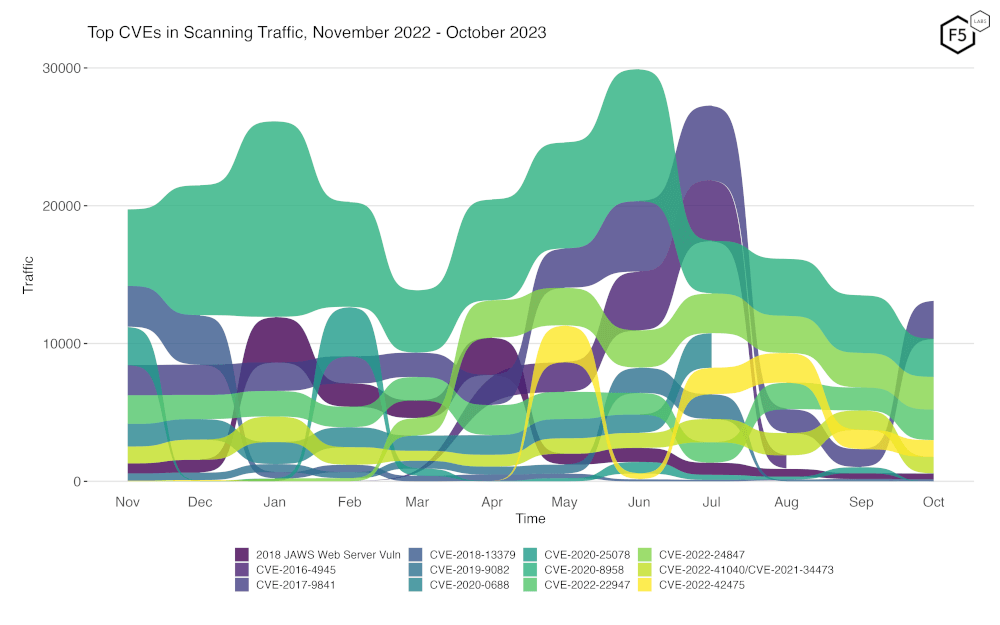
Figure 2. Evolution of vulnerability targeting trends over previous twelve months. Note the sharp rise in traffic for CVE-2017-9841.
Overall Scanning Traffic Changes
Lest the downward trend shown in Figure 2 makes it seem like overall scanning traffic may be abating, it’s important to note that the volume of scanning we observed has remained relatively constant, at least over the last three months, increasing by approximately 5.1% from August to September, then falling approximately 5.8% from September to October.
The full details of the changes in scanning traffic over the last 12 months are shown in the following table.
| Month | % Change from Previous Month |
| November 2022 | 15.3% |
| December 2022 | 1.2% |
| January 2023 | 5.6% |
| February 2023 | -15.5% |
| March 2023 | -22.4% |
| April 2023 | 37.3% |
| May 2023 | -0.9% |
| June 2023 | -0.3% |
| July 2023 | 20.1% |
| August 2023 | -27.9% |
| September 2023 | 5.1% |
| October 2023 | -5.8% |
Table 2: Percentage change of overall scanning traffic from November 2022 to October 2023
Long Term Trends
Because Figure 2 only shows high-traffic CVEs, Figure 3 shows traffic for all 82 CVEs we have tracked. In this view, most of our tracked CVEs can be seen to be holding at a relatively steady rate, with a few showing marked declines from relatively high rates seen in previous months, such as CVE-2013-6397, a directory traversal vulnerability in Apache Solr before version 4.6, and CVE-2021-26084, a critical Remote Code Execution vulnerability in Confluence Server and Data Center in several versions before 7.4.11, 7.11.6, and 7.12.5.
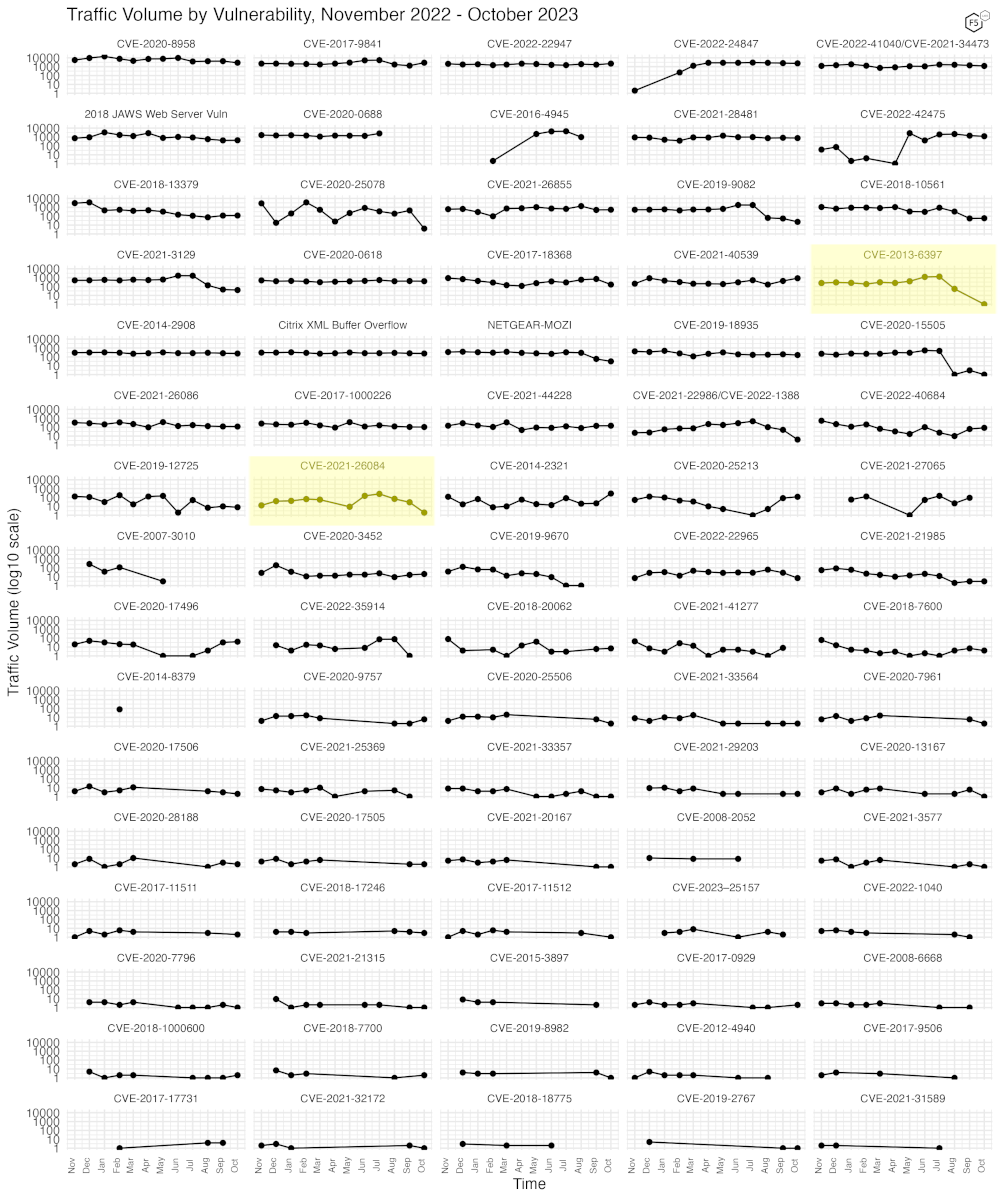
Figure 3. Traffic volume for the last twelve months for 82 tracked CVEs.
Conclusions
We must once again reiterate that our sensors are passive, and they do not respond to requests, nor do they pretend to be any specific platform or software stack. They are simply an open socket on port 80 and 443, with just enough of a webserver to be able to record the requests made to them and negotiate any required TLS connection. They do not have DNS names, although it’s certainly possible they may once have had them. Sometimes IP blocks are reassigned, and old DNS records remain that continue to point to them.
For those new to the Sensor Intelligence Series, we will conclude by repeating some old but valid observations. We see a continuing focus on IoT and router vulnerabilities, as well as easy, essentially one-request remote code execution vulnerabilities. These typically result in the installation of malware, crypto miners, and DDoS bots. See you in December!
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Inventory your exposed applications rigorously, to allow rapid response to emerging vulnerabilities that may be quickly weaponized by threat actors.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


