In 2018 we published our first Application Protection Report, which summarized trends and attack patterns for 2017 across multiple disciplines of information security and offered a big picture strategy for controlling application risk. We created that report in order to provide three things that we felt the security industry needs: a specific focus on application security, a sweeping scope, and a longer timeframe of analysis. In a world of breaking threat bulletins, mainstream sensationalism about hacking, and increasing specialization in information security, we wanted to tie things together to deliver the intelligence that we always wished we’d had when defending our own networks.
As valuable as we feel that report is, we recognized that neither our datasets nor our adversaries are considerate enough to follow nice round timeframes like calendar years. As a result, we are shifting our approach and releasing shorter reports about specific issues on an ongoing basis. The Application Protection Report is now becoming the Application Protection Research Series, and we will continue to focus on the big picture that we provided in our first report, but with greater granularity and timeliness.
Before we go any further, we need to recap why this series is specifically about application security. There’s so much to worry about in information security – why devote so much attention to applications? In short, we focus on applications because that’s what our adversaries do. Applications are the new battlefield of information security. To understand why this is, we need to back up a bit to understand how things have changed.
Ah Geez, A History Lesson?
In the first 30-odd years of the Internet, going back to the ARPANET days, people primarily used it as a medium of information transmission. It allowed users to quickly move locally processed information to geographically disparate locations for further local processing or consumption by other humans. Local storage was also the norm. The information that was chosen for transmission was, for the most part, a small subset of already meaningful data that had been curated and processed into human insight. There were some outliers, organizations and people who had foreseen (or stumbled upon) the model that we all eventually grew into, but for the most part, the information traveling across the Internet remained a small subset of the wider store of human information.
However, over the following 20 years, up to the present, the Internet has gradually grown into a place that contains a greater and greater percentage of all human information, and is a platform not merely for transmission of rich information, but also for storage and processing of data at any level of abstraction. One of the outcomes of this is that the gap between software, which processed and stored information, and networks, which transmitted and displayed information, often in static HTML files that we called websites, has collapsed. Pretty much all software is either hosted online or needs an Internet connection to run, and users need Internet connections to add the context and value that turns data into information anyway. All applications are internetworked, and all networks terminate in applications.
The result is that, in 2019, applications are the focal point of contemporary operations for business, and increasingly, for non-profits and the public sector as well. Webmail, social media, search engines, online banking, travel booking, databases, media streaming, eLearning, and the ubiquitous content management systems that have replaced static sites are all applications. As the meeting point of users and networks, applications are the defining value proposition for most businesses, and the gateway in all forms to that which attackers value most: data.
In short, we focus on applications because they have quietly but inexorably taken center stage as the defining component of the Internet. This might sound obvious, but the security industry isn’t (/content/f5-labs-v2/en/labs/articles/cisotociso/4-areas-where-infosec-facts-and-fiction-clash--mind-the-gap-pt--.html) really keeping (/content/f5-labs-v2/en/labs/articles/cisotociso/4-areas-where-infosec-facts-and-fiction-clash--mind-the-gap-pt-2.html) up with the trends (/content/f5-labs-v2/en/labs/articles/cisotociso/4-areas-where-infosec-facts-and-fiction-clash--mind-the-gap-pt-3.html).1 Attackers, on the other hand, are on top of it. As you’ll see in our research series, the only things that attackers focused on more in 2019 than web applications were the users connecting to those applications–and then only as a first step to gain access to data.
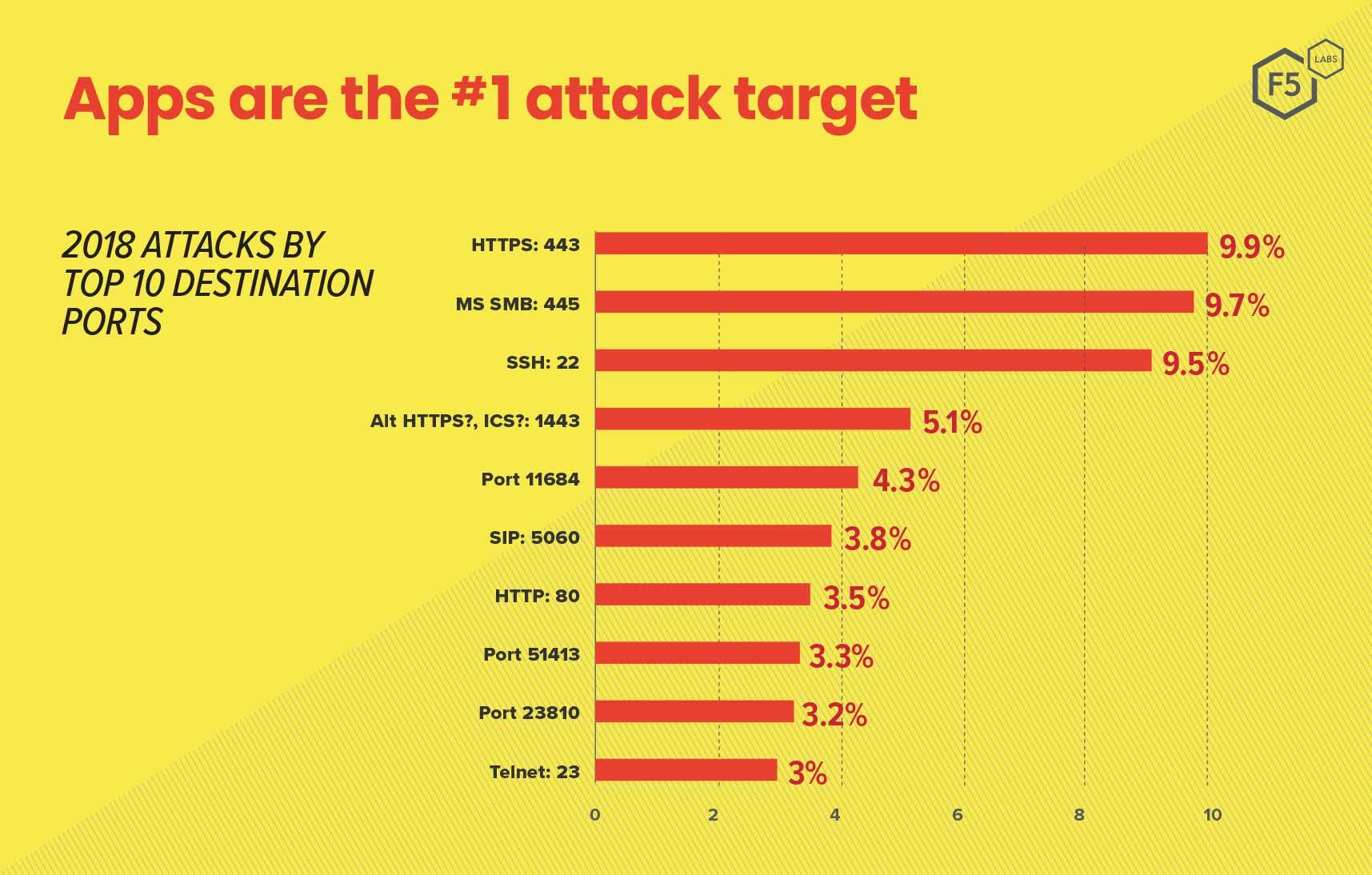
This chart shows the top ten target ports by honeypot traffic volume. While not every port shown here is used exclusively for application traffic, these data still demonstrate the degree to which known-malicious traffic focuses on a small number of ports that are associated with applications.
Modeling the New Attack Surface
At the heart of the Application Protection Research series is the aggregation and sharing of big-picture data. We believe that all information security needs to be risk-based. Everyone at F5 Labs has worked in organizations that did it otherwise, and we understand the realities at play in the industry, so we mean no rebuke. However, as an industry, we need to move beyond compliance, checklists, anecdotes, hunches, astrology, and tea leaves for building security programs. At the same time, information systems themselves are not exactly naturally forthcoming with information, organizations often don’t share unless they have to, and we don’t usually know what risks our individual orgs face until we’ve already been hacked. This is what makes threat intelligence the leading edge of risk-based security, and this is why we work the way we do.
As we were developing the 2018 report, we realized that we needed to reconceptualize how we think about applications and their attack surface. The result was a conceptual model that used layers (/content/f5-labs-v2/en/labs/articles/cisotociso/apps-are-like-onions--they-have-layers.html) to display the various transmission and processing functions necessary for an internetworked application to run. We mapped different attack techniques to the different application tiers (and we found, unsurprisingly, that it was a many:many mapping), and so developed a model of attack surfaces that is two-dimensional, containing breadth as well as depth, instead of just counting how many machines had a specific vulnerability.
The App Stack, as we call it, has become an integral part of how we understand threats and vulnerabilities, and now underpins all of our research, from tactical threat pieces to our strategic CISO-to-CISO series. You will see us refer to the App Stack in our episodes to help tie each piece of intelligence into a broader picture. The App Stack also helped us structure the questions and analyses that we used for each episode. For the most part, each episode is oriented toward a specific tier of the app stack, to answer how threats to that specific tier redound and reverberate across applications, organizations, and the user population.
The structure and content of our research is based on the broad and deep experience that our team brings to our work. However, in the end our success hinges on whether our audience is able to apply this intelligence to mitigate risk. If you have feedback, data to share, requests for topics, or thoughts about our approach, please let us know.


