
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
Introduction
For May’s vulnerability analysis, we examine the top ten CVEs most targeted, highlighting notable shifts and ongoing trends in exploitation activity. Additionally, we provide analysis of a year's worth of targeted CVE traffic through the lens of primary Common Weakness Enumerations (CWEs) and the OWASP Top Ten categories.
Top CVEs for May 2025
In May, the CVE-2017-9841 PHPUnit RCE holds steady as the most targeted vulnerability with over 54,000 instances (see Table 1). CVE-2020-8958 Guangzhou RCE saw a significant jump in targeting. CVE-2020-8958 AvertX Enumeration saw a jump in targeting also, although in keeping with its recent fluctuation. CVE-2024-3721 TBK DVR Injection also saw a proportionally large increase in targeting, re-entering the top 10 in May although still below levels of targeting of fall of 2024. CVE-2024-3721 was the only top 10 CVE to see any significant change to EPSS, jumping a full 0.2. We speculate that the EPSS jump is in related to leading indicators from Mirai activity recently reported on by Kaspersky.1 We saw no changes in Known Exploited Vulnerabilities (KEV) in the top ten CVEs for May.
| CVE RANK | CVE ID | CVE NAME | MAY TRAFFIC | CVSS | EPSS | KEV |
| 1 (--) | CVE-2017-9841 | PHPUnit eval-stdin.php RCE | 54633 (-3986) | 9.8 | 0.94406 (--) | Y |
| 2 (up 2) | CVE-2020-8958 | Guangzhou ONU Command Injection RCE | 5157 (+2859) | 7.2 | 0.86759 (+0.0129) | N |
| 3 (up 5) | CVE-2020-11625 | AvertX Camera Username Enumeration | 3237 (+1662) | 5.3 | 0.00309 (+0.0011) | N |
| 4 (up 6) | CVE-2023-1389 | TP-Link Archer AX21 Command Injection RCE | 3112 (+1778) | 8.8 | 0.94022 (-0.0013) | Y |
| 5 (down 3) | CVE-2019-9082 | ThinkPHP PHP Injection RCE | 2766 (-229) | 8.8 | 0.94141 (-0.0001) | Y |
| 6 (down 3) | CVE-2022-24847 | GeoServer JNDI Lookup RCE | 2367 (+35) | 7.2 | 0.00154 (+0.0002) | N |
| 7 (down 2) | CVE-2022-42475 | FortiOS FortiProxy SSL-VPN Heap Overflow RCE | 2166 (-33) | 9.8 | 0.93065 (+0.0003) | Y |
| 8 (down 2) | CVE-2024-4577 | Apache PHP-CGI Argument Injection RCE | 1909 (-228) | 9.8 | 0.94376 (--) | Y |
| 9 (down 2) | CVE-2022-22947 | Spring Cloud Gateway Actuator Code Injection RCE | 1610 (-211) | 10 | 0.94474 (--) | Y |
| 10 (up 1) | CVE-2024-3721 | TBK DVR OS Command Injection | 1532 (+565) | 6.3 | 0.50993 (+0.2231) | N |
Table 1: Top 10 CVEs for May 2025. CVSS scores are v3.1. All data is as of 2025-05-31.
Common Weakness Enumerations (CWEs) Analysis
F5 Labs analyzed the last twelve months of CVE traffic through the lens of CWEs. We present an F5 Labs Top CWEs ranking as well as an F5 Labs OWASP Top Ten CWEs breakdown.
Mapping CVEs to CWEs
How CVEs map to CWEs, as well as how CWEs inter-relate, is somewhat involved and beyond the scope of this article. We spare you the details, suffice to say that we’ve simplified and cleaned up the mapping from CVE to a single primary CWE for each of the top 25 CVEs of the last twelve months (see Table 2). CWEs often have verbose names, so for brevity we’ll use shortened names for the rest of this article. CWE names are inherently specialized and can be quiet inaccessible, so we’ve included a contextualized refresher on each of them in the following section.
| CVE | CVE Name | Primary CWE | CWE Name | CWE Short Name |
| CVE-2017-9841 | PHPUnit eval-stdin.php RCE | CWE-94 | Improper Control of Generation of Code ('Code Injection') | Code Injection |
| CVE-2023-1389 | TP-Link Archer AX21 Command Injection RCE | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | Command Injection |
| CVE-2022-24847 | GeoServer JNDI Lookup RCE | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | Command Injection |
| CVE-2022-22947 | Spring Cloud Gateway Actuator Code Injection RCE | CWE-94 | Improper Control of Generation of Code ('Code Injection') | Code Injection |
| CVE-2020-8958 | Guangzhou ONU Command Injection RCE | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | Command Injection |
| CVE-2020-11625 | AvertX Camera Username Enumeration | CWE-203 | Observable Discrepancy | Observable Discrepancy |
| CVE-2022-42475 | FortiOS FortiProxy SSL-VPN Heap Overflow RCE | CWE-787 | Out-of-bounds Write | Out-of-bounds Write |
| CVE-2019-9082 | ThinkPHP PHP Injection RCE | CWE-94 | Improper Control of Generation of Code ('Code Injection') | Code Injection |
| CVE-2024-4577 | Apache PHP-CGI Argument Injection RCE | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | Command Injection |
| CVE-2024-3721 | TBK DVR OS Command Injection | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | Command Injection |
| CVE-2022-47945 | ThinkPHP Lang Parameter LFI RCE | CWE-22 | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') | Path Traversal |
| CVE-2018-0296 | Cisco ASA Web Interface Directory Traversal DoS | CWE-22 | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') | Path Traversal |
| CVE-2021-28481 | Microsoft Exchange Server RCE | CWE-94 | Improper Control of Generation of Code ('Code Injection') | Code Injection |
| CVE-2021-26855 | Microsoft Exchange Server RCE | CWE-918 | Server-Side Request Forgery (SSRF) | Server-Side Request Forgery (SSRF) |
| CVE-2020-0618 | Microsoft SQL Server Reporting Services RCE | CWE-502 | Deserialization of Untrusted Data | Deserialization of Untrusted Data |
| CVE-2018-10561 | Dasan GPON Authentication Bypass | CWE-284 | Improper Access Control | Improper Access Control |
| CVE-2024-3273 | D-Link NAS HTTP GET Command Injection | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | Command Injection |
| CVE-2015-2051 | D-Link DIR-645 HNAP Command Execution | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | Command Injection |
| CVE-2023-23752 | Joomla Webservice Endpoint Access Control | CWE-284 | Improper Access Control | Improper Access Control |
| CVE-2021-44228 | Log4Shell | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | Command Injection |
| CVE-2014-2908 | Siemens SIMATIC S7-1200 XSS | CWE-79 | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') | Cross-site Scripting |
| CVE-2021-26086 | Atlassian Jira Path Traversal | CWE-22 | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') | Path Traversal |
| CVE-2017-18368 | ZyXEL P660HN-T1A Remote Log Command Injection | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | Command Injection |
| CVE-2021-40539 | Zoho ADSelfService Plus REST API Auth Bypass RCE | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | Command Injection |
| CVE-2019-18935 | Telerik RadAsyncUpload .NET Deserialization RCE | CWE-502 | Deserialization of Untrusted Data | Deserialization of Untrusted Data |
Table 2: The top 25 CVEs by observed activity over a 12-month period, and their corresponding primary CWE mappings.
CWE Refresher
CWE numbering, much like CVE numbering, is a necessary evil. It is very beneficial to be able to unambiguously refer to CWEs, but then CWE identifiers alone carry no semantic meaning for the reader. Furthermore, readers will be forgiven for not being intimately familiar with the technical underpinnings of attacks involving each CWE. The following list is a reminder of the essential aspects of each CWE in the context of CVEs exploited over HTTP requests. For additional details, consult the mitre.org repository footnote links as many have robust diagrams and explanatory text to further contextualize each CWE.
These are the CWEs we’ll be referring to in the article, listed here in order of significance:
- CWE-94: Code Injection2 - An attacker crafts an HTTP request with malicious content that is directly evaluated or executed by the server resulting in Remote Code Execution.
- CWE-77: Command Injection4 - An attacker supplies input in an HTTP request that is unsafely concatenated into a system command resulting in Remote Code Execution.
- CWE-203: Observable Discrepancy5 - An attacker manipulates HTTP requests to trigger subtle differences in server responses (e.g. error messages, response timing, etc), inferring sensitive internal state or existence of resources.
- CWE-787: Out-of-bounds Write6 - An attacker sends crafted HTTP data (typically a field that is too long) that causes the application to write outside the bounds of a memory buffer, corrupting memory and potentially enabling Remote Code Execution.
- CWE-22: Path Traversal7 - An attacker includes directory traversal sequences (i.e. “../” and encoded variations such as “..%2F”) to access files outside the intended directory, commonly exposing, and sometimes modifying, sensitive files.
- CWE-918: Server-Side Request Forgery (SSRF)8 - An attacker submits a crafted URL in an HTTP request, causing the server to make HTTP requests that bypass firewall and request routing controls to interact with internal HTTP services.
- CWE-502: Deserialization of Untrusted Data9 - An attacker delivers malicious serialized objects in an HTTP payload, which, when deserialized by the server, result in logic manipulation or Remote Code Execution.
- CWE-284: Improper Access Control10 - An attacker sends HTTP requests that exploit missing or weak access control checks to access sensitive data or perform sensitive actions.
- CWE-79: Cross-site Scripting11 - An attacker injects malicious scripts into HTTP requests that are stored by the server and later executed in the victim’s browser, enabling session hijacking, credential theft, or arbitrary actions as the victim’s user.
F5 Labs Top CWEs
We have ranked CWEs by their total annual traffic (see Table 3). Furthermore, the individual CVEs and their annual traffic are listed for convenience of traceability. CWE-94 Code Injection ranks highest due to the outsized influence of CVE-2017-9841. CWE-77 Command Injection comes in second and represents the greatest diversity of CVEs in the F5 Labs Top CWEs. The numbers of CVEs as well as associated CVE traffic volume fall off from the third rank onwards, and yet contain a number of counterintuitive surprises we explore here.
Offensive practitioners would be forgiven for calling in to question the low rankings of CWE-22 Path Traversal, and CWE-284 Improper Access Control. The reason for this is obscured behind the fact that the CWEs here are ranked by the primary CWE we have mapped CVEs to. Regarding CWE-284, arguably many of the CVEs listed here were missing proper access control, but only as secondary CWE root causes. CWE-22 Path Traversal ranking lower, however, is best explained in terms of attacker motivation. While path traversal bugs are commonplace, they are rarely as impactful for attackers to exploit, which in turn means other more impactful exploits see significantly higher levels of attention and therefor correspondingly higher CWE traffic.
Blue teams might find the low ranking of CWE-203 Observable Discrepancy to be anomalous as techniques like user enumeration and default credential reuse are commonplace. Again, the primary motivation we see in evidence in F5 Labs CVE traffic is Remote Code Execution (RCE). So even when default credentials are leveraged as part of an exploit chain, we have still picked the more critical root cause to be the primary CWE attribution in this data set (e.g. with the post-auth CVE-2020-8958 Guangzhou ONU Command Injection RCE).
The final ranking surprise we anticipate readers may have is for the relative high ranking of CWE-787 Out-of-bounds Write. There are two parts to the explanation here. The first half of the explanation is statistical: with such a small sample size of CVEs and many fine grained CWE categorizations it becomes unsurprising to arrive at CWEs with only a single associated CVE. The second half of the explanation is due to the high level of visibility and impact of exploitation of SSL-VPN devices. We suspect that these two factors coincided in this case to elevate CWE-787 Out-of-bounds Write surprisingly high in the rankings.
| Primary CWE | CWE Short Name | CWE Total Annual Traffic | CVE Annual Traffic | CVE | CVE Name |
| CWE-94 | Code Injection | 375343 | 325529 | CVE-2017-9841 | PHPUnit eval-stdin.php RCE |
| 27193 | CVE-2022-22947 | Spring Cloud Gateway Actuator Code Injection RCE | |||
| 16262 | CVE-2019-9082 | ThinkPHP PHP Injection RCE | |||
| 6359 | CVE-2021-28481 | Microsoft Exchange Server RCE | |||
| CWE-77 | Command Injection | 242034 | 154687 | CVE-2023-1389 | TP-Link Archer AX21 Command Injection RCE |
| 32036 | CVE-2022-24847 | GeoServer JNDI Lookup RCE | |||
| 21613 | CVE-2020-8958 | Guangzhou ONU Command Injection RCE | |||
| 11757 | CVE-2024-4577 | Apache PHP-CGI Argument Injection RCE | |||
| 9049 | CVE-2024-3721 | TBK DVR OS Command Injection | |||
| 4167 | CVE-2024-3273 | D-Link NAS HTTP GET Command Injection | |||
| 3355 | CVE-2015-2051 | D-Link DIR-645 HNAP Command Execution | |||
| 2269 | CVE-2021-44228 | Log4Shell | |||
| 1747 | CVE-2017-18368 | ZyXEL P660HN-T1A Remote Log Command Injection | |||
| 1354 | CVE-2021-40539 | Zoho ADSelfService Plus REST API Auth Bypass RCE | |||
| CWE-203 | Observable Discrepancy | 21444 | 21444 | CVE-2020-11625 | AvertX Camera Username Enumeration |
| CWE-787 | Out-of-bounds Write | 19613 | 19613 | CVE-2022-42475 | FortiOS FortiProxy SSL-VPN Heap Overflow RCE |
| CWE-22 | Path Traversal | 16076 | 7915 | CVE-2022-47945 | ThinkPHP Lang Parameter LFI RCE |
| 6396 | CVE-2018-0296 | Cisco ASA Web Interface Directory Traversal DoS | |||
| 1765 | CVE-2021-26086 | Atlassian Jira Path Traversal | |||
| CWE-284 | Improper Access Control | 7648 | 4684 | CVE-2018-10561 | Dasan GPON Authentication Bypass |
| 2964 | CVE-2023-23752 | Joomla Webservice Endpoint Access Control | |||
| CWE-502 | Deserialization of Untrusted Data | 6093 | 4862 | CVE-2020-0618 | Microsoft SQL Server Reporting Services RCE |
| 1231 | CVE-2019-18935 | Telerik RadAsyncUpload .NET Deserialization RCE | |||
| CWE-918 | Server-Side Request Forgery (SSRF) | 5296 | 5296 | CVE-2021-26855 | Microsoft Exchange Server RCE |
| CWE-79 | Cross-site Scripting | 2253 | 2253 | CVE-2014-2908 | Siemens SIMATIC S7-1200 XSS |
Table 3: F5 Labs Top CWEs for a 12-month period, with total annual traffic and associated CVEs.
F5 Labs OWASP Top Ten CWEs
We have totaled the traffic each OWASP Top Ten category received over the last twelve months (see Table 4). We have done this by following the mapping from CVE to primary CWE to OWASP category, and propagated the CVE traffic through to the resulting OWASP category. The resulting data shows a remarkably unbalanced alignment between OWASP Top Ten categories and observed CVE traffic. A03:2021 – Injection is the clear leader in observed CVE traffic. This makes a lot of intuitive sense as CVE exploitation inherently skews in favor of Remote Code Execution outcomes. Counter-intuitively A01:2021 - Broken Access Control is relatively underrepresented. Echoing our analysis from previously, arguably many of the CVEs listed here were missing proper access control, but only as secondary CWE root causes. F5 Labs attribution from CVE to OWASP category is dependent on our determination of the single primary CWE, which were often variations of injection CWEs.
Many OWASP categories have no attributed CVE traffic. The primary explanation we have here is due to the lens through which OWASP Top Ten, necessarily, views security. The OWASP Top Ten serves to educate software engineers and support their defending security teams. Therefor the OWASP categorization reflects the holistic security needs of developing software, which does not necessarily correlate with CVEs that see mass exploitation. For example, OWASP Top Ten categories will be very valuable for framing contextualized penetration tests, but much less relevant at explaining the intersection between exploitation outcomes and availability of vulnerable devices and software. Concretely, A02:2021 - Cryptographic Failures would show up in an assumed breach penetration test with a finding such as “Passwords unencrypted in database backups”, whereas such a deployment-specific vulnerability is unlikely to show up in mass exploitation of a published CVE.
Of final note for the F5 Labs OWASP Top Ten CWEs, we list two CVEs that have no corresponding OWASP category. With CVE-2020-11625, CWE-203 Observable Discrepancy did not fit cleanly into any OWASP category. With CVE-2022-42475, buffer overflow bugs have not featured in the OWASP Top Ten since the early days in 2004 (as A5 Buffer Overflow3).
| OWASP Category | OWASP Category Total Annual Requests | CWE | CWE Short Name | CWE Total Annual Requests | CVE Annual Requests | CVE | CVE Name |
| A01:2021 - Broken Access Control | 23724 | CWE-22 | Path Traversal | 16076 | 7915 | CVE-2022-47945 | ThinkPHP Lang Parameter LFI RCE |
| 6396 | CVE-2018-0296 | Cisco ASA Web Interface Directory Traversal DoS | |||||
| 1765 | CVE-2021-26086 | Atlassian Jira Path Traversal | |||||
| CWE-284 | Improper Access Control | 7648 | 4684 | CVE-2018-10561 | Dasan GPON Authentication Bypass | ||
| 2964 | CVE-2023-23752 | Joomla Webservice Endpoint Access Control | |||||
| A02:2021 - Cryptographic Failures | 0 | N/A | N/A | N/A | N/A | N/A | N/A |
| A03:2021 - Injection | 619630 | CWE-94 | Code Injection | 375343 | 325529 | CVE-2017-9841 | PHPUnit eval-stdin.php RCE |
| 27193 | CVE-2022-22947 | Spring Cloud Gateway Actuator Code Injection RCE | |||||
| 16262 | CVE-2019-9082 | ThinkPHP PHP Injection RCE | |||||
| 6359 | CVE-2021-28481 | Microsoft Exchange Server RCE | |||||
| CWE-77 | Command Injection | 242034 | 154687 | CVE-2023-1389 | TP-Link Archer AX21 Command Injection RCE | ||
| 32036 | CVE-2022-24847 | GeoServer JNDI Lookup RCE | |||||
| 21613 | CVE-2020-8958 | Guangzhou ONU Command Injection RCE | |||||
| 11757 | CVE-2024-4577 | Apache PHP-CGI Argument Injection RCE | |||||
| 9049 | CVE-2024-3721 | TBK DVR OS Command Injection | |||||
| 4167 | CVE-2024-3273 | D-Link NAS HTTP GET Command Injection | |||||
| 3355 | CVE-2015-2051 | D-Link DIR-645 HNAP Command Execution | |||||
| 2269 | CVE-2021-44228 | Log4Shell | |||||
| 1747 | CVE-2017-18368 | ZyXEL P660HN-T1A Remote Log Command Injection | |||||
| 1354 | CVE-2021-40539 | Zoho ADSelfService Plus REST API Auth Bypass RCE | |||||
| CWE-79 | Cross-site Scripting | 2253 | 2253 | CVE-2014-2908 | Siemens SIMATIC S7-1200 XSS | ||
| A04:2021 - Insecure Design | 0 | N/A | N/A | N/A | N/A | N/A | N/A |
| A05:2021 - Security Misconfiguration | 0 | N/A | N/A | N/A | N/A | N/A | N/A |
| A06:2021 - Vulnerable and Outdated Components | 0 | N/A | N/A | N/A | N/A | N/A | N/A |
| A07:2021 - Identification and Authentication Failures | 0 | N/A | N/A | N/A | N/A | N/A | N/A |
| A08:2021 - Software and Data Integrity Failures | 6093 | CWE-502 | Deserialization of Untrusted Data | 6093 | 4862 | CVE-2020-0618 | Microsoft SQL Server Reporting Services RCE |
| 1231 | CVE-2019-18935 | Telerik RadAsyncUpload .NET Deserialization RCE | |||||
| A08:2021 - Software and Data Integrity Failures | 0 | N/A | N/A | N/A | N/A | N/A | N/A |
| A09:2021 - Security Logging and Monitoring Failures | 0 | N/A | N/A | N/A | N/A | N/A | N/A |
| A10:2021 - Server-Side Request Forgery (SSRF) | 5296 | CWE-918 | Server-Side Request Forgery (SSRF) | 5296 | 5296 | CVE-2021-26855 | Microsoft Exchange Server RCE |
| N/A | N/A | CWE-203 | Observable Discrepancy | 21444 | 21444 | CVE-2020-11625 | AvertX Camera Username Enumeration |
| CWE-787 | Out-of-bounds Write | 19613 | 19613 | CVE-2022-42475 | FortiOS FortiProxy SSL-VPN Heap Overflow RCE |
Table 4: The OWASP Top Ten categories with their associated CWEs and observed CVEs in activity over the past 12-months.
Long Term Targeting Trends
CVE-2017-9841 (PHPUnit eval-stdin.php RCE) maintains high levels of targeting (see Figure 1). No other CVE in recent months comes close to CVE-2017-9841’s level of activity. CVE-2019-9082 (ThinkPHP PHP Injection RCE) maintained consistent levels of activity and in doing so was surpassed by growth in all the remaining CVEs in the top five for May: CVE-2020-8958 (Guangzhou ONU Command Injection RCE), CVE-2020-11625 (AvertX Camera Username Enumeration), and CVE-2023-1389 (TP-Link Archer AX21 Command Injection RCE).
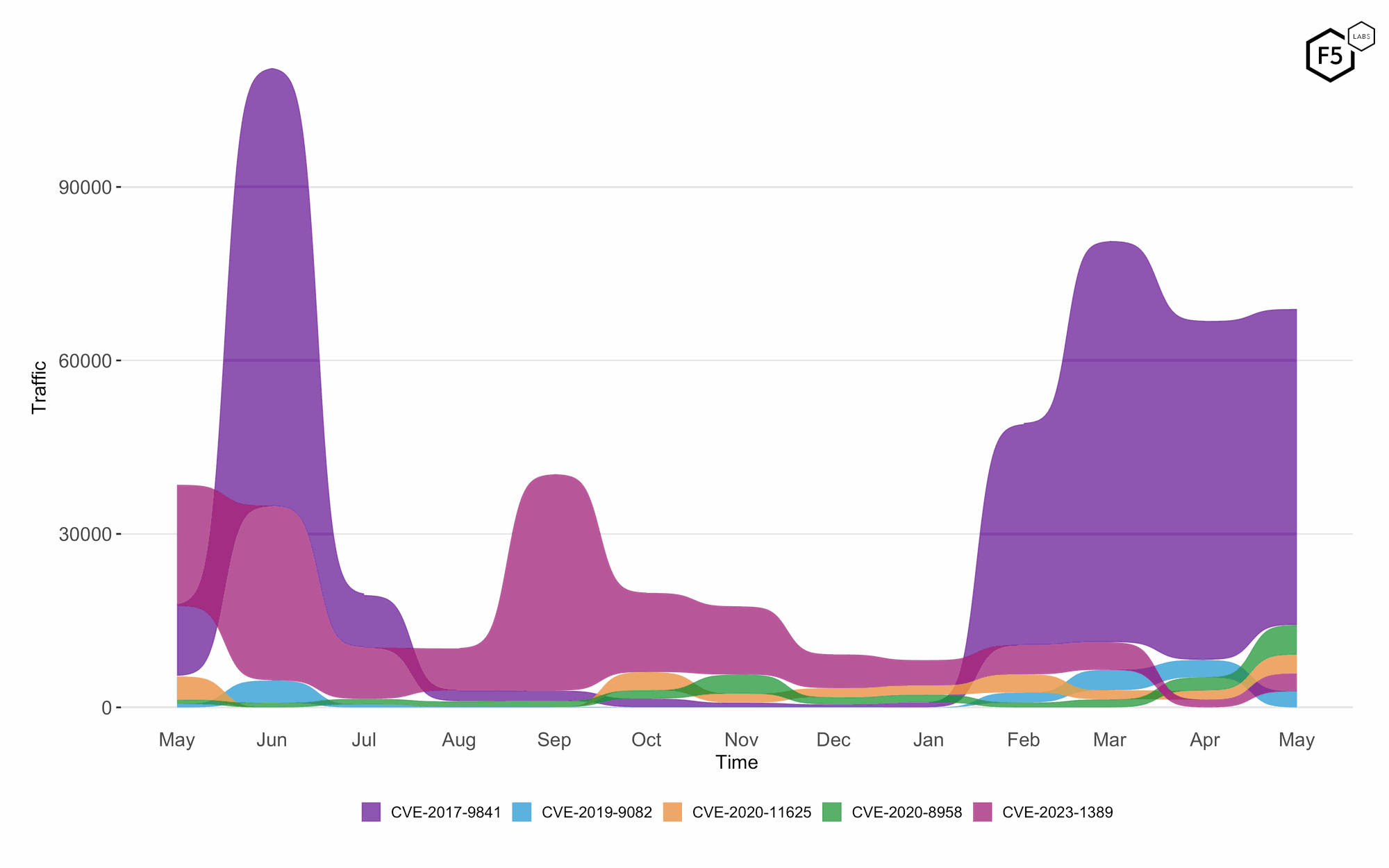
Figure 1: 12-month bump plot of the top 5 CVEs. CVE-2017-9841 maintains significantly higher activity than all other CVEs observed. CVE-2019-9082 activity stays constant.
Long Term Trends
CVE-2020-8958 (Guangzhou ONU Command Injection RCE, top right) is the most significant trend to watch in May, maintaining near exponential targeting growth levels on prior months for 3 months running now (see Figure 2 – readers are reminded that the y-axis scale is logarithmic). CVE-2023-1389 (TP-Link Archer AX21 Command Injection RCE, top left) has broken with its downward trend and may be seeing revived interest. CVE-2024-3721 (TBK DVR OS Command Injection, right) may be on the cusp of returning to prior peaks of targeting with almost a 60% increase in May.
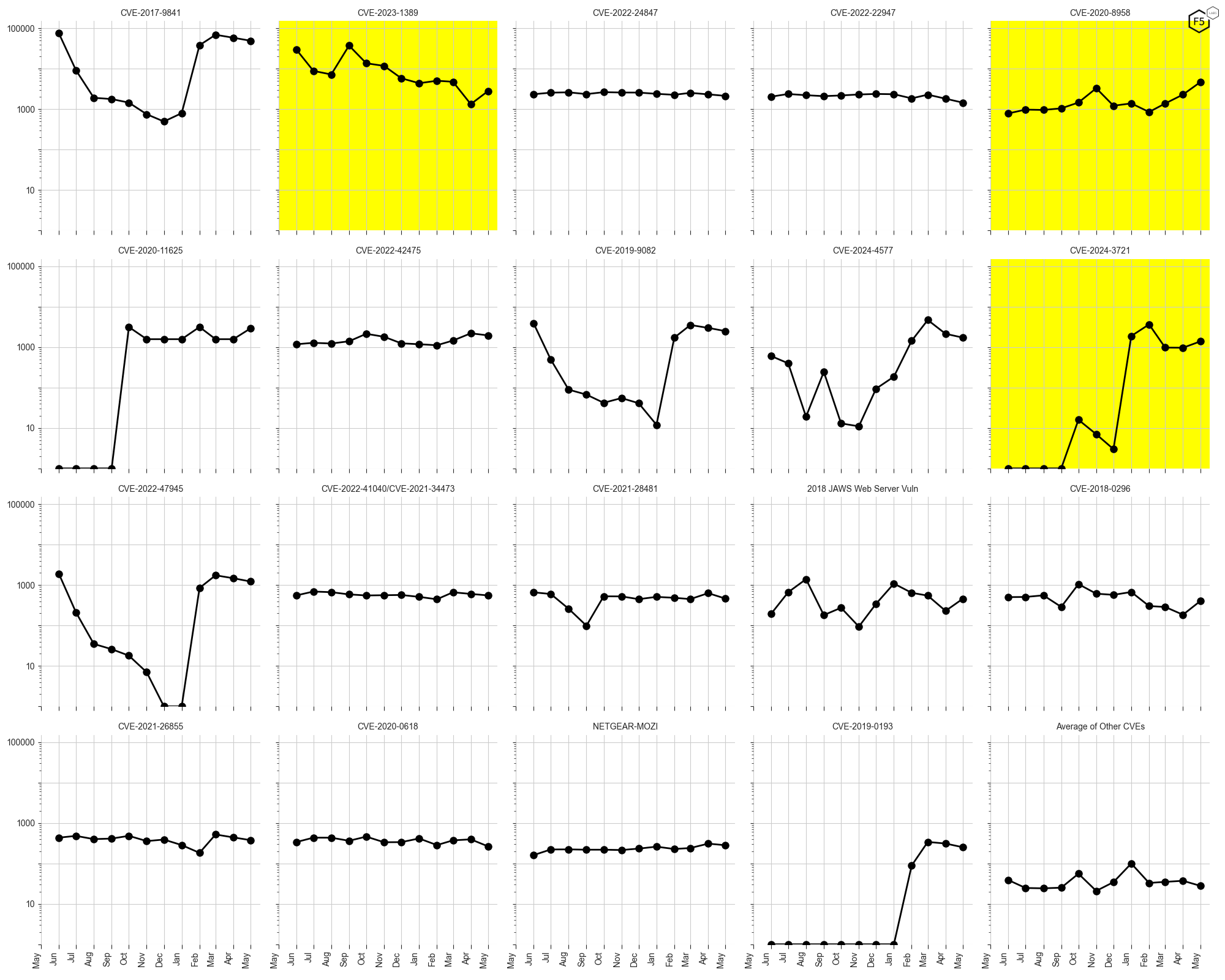
Figure 2: Evolution of vulnerability targeting in the last 12-months, shown using a logarithmic scale for ease of comparison. CVE-2020-8958 has established a steep upward trend. CVE-2023-1389 has broken its downward trend. CVE-2024-3721 may be establishing an upward trend.
Conclusion
Observed CVE targeting in May 2025 held consistent with recent trending, with a slight uptick in overall activity. We reported significant increases in activity CVE-2020-8958 (Guangzhou ONU Command Injection) and CVE-2024-3721 (TBK DVR OS Command Injection) and speculated that the latter is likely due to a Mirai variant. Analysis of twelve months of CVE targeting attributed to Common Weakness Enumeration (CWE) and OWASP Top Ten categories indicate a continued bias by attackers towards injection vulnerabilities leading to Remote Code Execution outcomes, specifically CWE-94 (Code Injection) and CWE-77 (Command Injection). There were some surprises to our CWE and OWASP Top Ten analysis which we addressed in their respective sections.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


