Mirai is an IoT botnet (or thingbot) that F5 has discussed since 2016. It infamously took down large sections of the Internet in late 2016 and has remained active ever since. Its source code was released online in September 2016, allowing unskilled attackers to create a malicious botnet with relative ease. Mirai continues to target IoT devices using the same tactics as before to attack and harness the collective power of millions of unprotected devices to launch DDoS attacks. It does not usually spread through traditional phishing attempts but acts as a self-propagating worm that searches for and attacks vulnerable servers. Although small changes have been made to this malware, malicious actors now appear to have taken advantage of public interest in the coronavirus (COVID-19) by naming their latest variant file covid. This sample, which is detailed below, is publicly available.
This name change continues a trend in which malware or malicious tactics, techniques, and procedures (TTPs) are renamed or “reskinned” but leave the core functionality basically the same. For this reason, it’s just as important now as it was before the pandemic for enterprises and individuals to remain vigilant in protecting their systems.
About the COVID Variant
After F5 researchers detected this new Mirai variant, it appears that the authors did not remake the malware or create new exploits. This sample was spotted with two different hashes that multiple antivirus engines detected and identified. Both samples are named covid and have different file extensions. For a table of the indicators of compromise (IoCs) for this sample, see the COVID-19 Fails to Slow Down Hackers section of this article.
Threat monitoring tools noted that the IP address hosting this malware is a Hostwinds domain. It is currently still active and the Whois information is hidden. Those seeking to perform additional analysis can use the following path to find the sample:
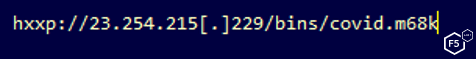
Figure 1. Screenshot showing the path to the Mirai sample
As with other Mirai samples, this variant’s inner content is XOR-encoded. We found that it uses 0x54, the same encoding key as many other Mirai samples. This led us to assume that, even though this is a fresh sample in the wild, it is not unique—it may have been named covid only because that’s trending right now.
Target List
In this sample, we found a range of targets that we’ve seen before. One is TeamSpeak, a voice communications app that gamers commonly use (see Figure 2). The other target is a Huawei router module (see Figure 3). These targets appear to be consistent with previous Mirai targets we’ve written about; TeamSpeak has been a target since our October 2018 Hunt for IoT article.
The following figure shows the targeting information from the TeamSpeak sample:
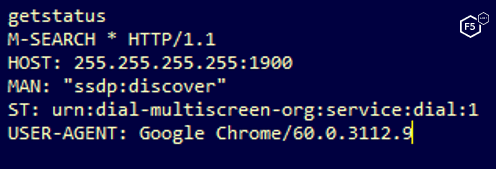
Figure 2. TeamSpeak target information from the Mirai sample
The following figure shows the targeting information from the Huawei router sample:
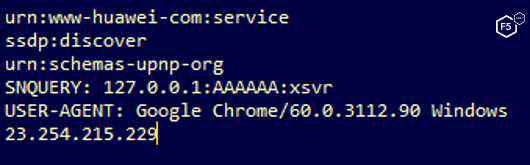
Figure 3. Huawei router target information from the Mirai sample
Neither of these targets is unique and both have long been Mirai and Bashlite targets.1 Mirai focuses on both TeamSpeak and Huawei because these systems have historically had vulnerabilities associated with default passwords. TeamSpeak is a choice target because its responses are larger than the requests made to it and can be used to conduct a volumetric amplification DDoS attack.
Signature Attacker Elements
Since the original Mirai source code was leaked in 2016, attackers have become creative with command-and-control (C&C) host names. In the covid sample, the attacker did little to obfuscate the code. It was evident during our static analysis that the malware was not packed, and our researchers could clearly see the malware’s strings (see Figure 4). These strings included a reference to TeamSpeak, Huawei, the UPnP protocol, specific user agents, and C&C hosts.
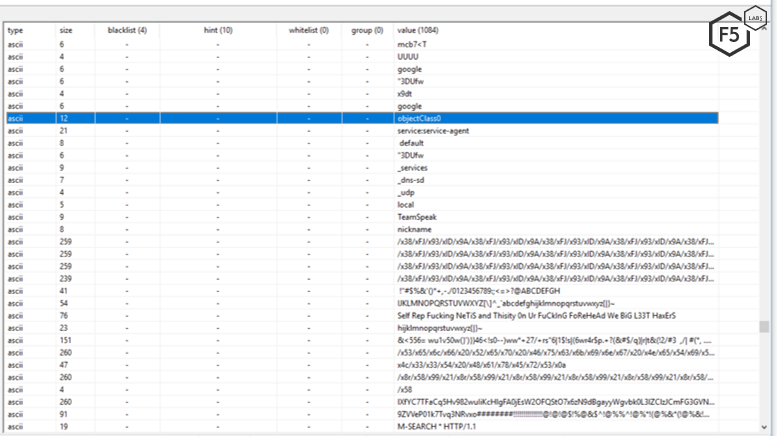
Figure 4. Capture of strings in PeStudio from the malware
Along with strings that tell us something about the malware, these attackers characteristically left offensive messages for any researcher investigating the sample (see Figure 5).

Figure 5. Offensive string that attackers left for researchers to find
COVID-19 Fails to Slow Down Hackers
While COVID-19 appeared to affect state-backed hacking in February, and other groups promised not to attack health care infrastructure, Mirai and other cybercriminal malware don’t seem to be slowing down, with files explicitly named after the virus.2 This implies that malware authors continue to work despite the global pandemic. Along with these Mirai files, researchers noticed other malware families attempting to take advantage of the virus by renaming or adding features that reference COVID-19 (see Table 1). At this time, analyses have been conducted on all of these samples.
| Malware | Indicator of Compromise |
| Trickbot and Emotet using COVID relation as part of malware file description4 | f2e44c889350ce062e414d5719e30a4c |
| Ginp banking Trojan uses COVID virus finder themed and fake app5 | MD5 not published yet |
| Mirai variant named COVID | cf203ca2c8d8411b7c7cfb1baf0f51c2 e879a608ef48e755b749ec9e34b38e3e |
| HawkEye keylogger using COVID for profit6 | c9c0180eba2a712f1aba1303b90cbf12 c1117451ce13b68715931abc437b10cd |
Table 1. Indicators of compromise for various malware families
Conclusion
While this Mirai variant doesn’t seem to use new exploits or techniques, it’s important to note when malware morphs to try and take advantage of a trend or current event. Mirai continues to be an active threat to IoT devices, and F5 researchers will stay apprised of current and changing tactics the malware uses. Continue the conversation with us on social media.
Security Controls
Enterprises and individuals should consider implementing the following security controls, depending on their specific circumstances (for a longer list of IoT hardening suggestions, see the conclusion of Hunt for IoT volume 4):
Recommendations
- Disable remote management, restrict access to a management network, or place devices behind a firewall.
- At a minimum, use network address translation (NAT) if devices are used at a residence.
- Change the vendor default credentials and disable the default admin account if you can.
- Update devices with the latest firmware as it is released.
- Use an intrusion detection system to catch known malware.
- Review and adjust access controls as necessary.
- Notify customers of malware detected on their systems during login, so they can take steps to clean their systems.
- Implement a patch management system in order to keep systems current on patches.
- Provide security awareness training to employees and customers.


