
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
Introduction
While the CVEs we track each month showed very little variation, leading to a somewhat boring month for analysis, we pivoted and dove deeply into just one scanner, and found some amusing characteristics that make identifying this scanner very easy. First, however, let’s take a quick look at the trending CVEs from last month’s traffic.
Trending CVEs for August 2025
CVE-2017-9841, a PHPUnit Remote Code Execution vulnerability, continues to dominate exploitation attempts. This vulnerability allows attackers to execute arbitrary PHP code, and organizations should ensure their PHP environments are updated to mitigate risks.
CVE-2023-1389, a TP-Link Archer AX21 Command Injection vulnerability, remains a concern for home and small business networks. Users should follow TP-Link's patching guidelines and consider replacing compromised devices.
CVE-2019-9082, a ThinkPHP PHP Injection vulnerability, has seen increased activity. Organizations using ThinkPHP should validate input and update to secure versions.
CVE-2024-4577, an Apache PHP-CGI Argument Injection vulnerability, is gaining traction. Administrators should disable vulnerable configurations and apply patches.
CVE-2022-24847, a GeoServer JNDI Lookup vulnerability, remains active. GeoServer users should update to the latest versions and restrict external JNDI lookups.
Looking at an Inadvertent Disclosure Scanner
Having recently done some cluster analysis of our most recent data we thought it might be informative to dive deeply into just one set of activities ostensibly from the same actor. In this case we're going to look at traffic that's very easily identifiable, coming as it does from a single IP address (78.153.140.203) and sharing a common list of over 12,000 User-Agent strings in rotation, and a distinct set of targeted URLs. We'll look at its behavior over time, from when it started, to the changes in the URLs it tries to find and look a little bit into the source of the traffic as well.
IP Analysis
While a broader analysis shows this actor is likely using a dozen or more IPs to conduct their scans, mostly from the same netblock, for simplicity’s sake we're just going to look at the one with the most traffic sent.
The IP address 78.153.140.203 is in a netblock controlled by AS202306, "HOSTGLOBAL.PLUS LTD", an ISP provider based out of the United Kingdom. It is certainly known as a malicious IP as well with 12 out of 95 security vendors marking it as malicious on VirusTotal1 and AbuseIPDB2 reporting it as 100% malicious. Unsurprisingly most of the reports listed at AbuseIPDB were for scanning and specifically scanning targeting "/.env" files.
First Appearance and Prevalence
We first recorded traffic from this IP on January 10th, 2025 UTC although we've seen traffic from this netblock since November of 2023. Its appearance was continuous from that date until April 10th, 2025, when it suddenly disappeared from our logs. It reappeared on July 11th, 2025 and has been active since then.
URLs Scanned
This IP is very focused on finding exposed environment files. This is most likely because it is not uncommon for developers to place highly sensitive information, including database credentials, access tokens, passwords and even ssh private keys into such files. This IP does not content itself with scanning just for the most obvious path but instead scans for 130 unique URLs.
80.23% of the scans are for variations on '/.env', and 11.45% were for variations on 'phpinfo.php'. The remaining 8.32% were a mix of various other requests which also targeted the sort of accidental information or credential disclosure as the most prevalent categories.
The table below demonstrates this clearly, with most URLs targeting various ‘.env” paths.
| URL | n |
|---|---|
| /.env | 1782 |
| /api/.env | 1006 |
| /backend/.env | 942 |
| /admin/.env | 904 |
| /.env.example | 857 |
| /app_dev.php/_profiler/phpinfo | 824 |
| /?phpinfo=-1 | 804 |
| /config/.env | 464 |
| /media/.env | 421 |
| /server/.env | 384 |
Table 1: Counts of unique URLs, showing /.env and similar being the most prevalent.
Changes in URLs Being Scanned
A quick analysis shows that the URLs being scanned has changed over time. Not perhaps substantively but it interesting to observe what this action ostensibly thought was working or worth targeting.
The total URLs as well as counts for those added and removed each month are in the table below.
| 2025 month | URLs Added | URLs Removed | Total |
|---|---|---|---|
| 1 | 33 | 0 | 33 |
| 2 | 55 | 0 | 88 |
| 3 | 0 | 46 | 42 |
| 4 | 0 | 0 | 42 |
| 5 | 0 | 42 | 0 |
| 6 | 0 | 0 | 0 |
| 7 | 42 | 27 | 57 |
| 8 | 10 | 0 | 67 |
Table 2: A table showing URLs added and removed by month in 2025. This shows a large increase in URL diversity in February, and large drop in March, of 2025.
A visualization of this shows quite clearly that a rather large number were added in February then some removed in March, and staying consistent in April (perhaps they found the optimal settings).
The aforementioned outage for May and June comes next and then when the IP returns it comes in with more unique URLs than before and continues to rise.
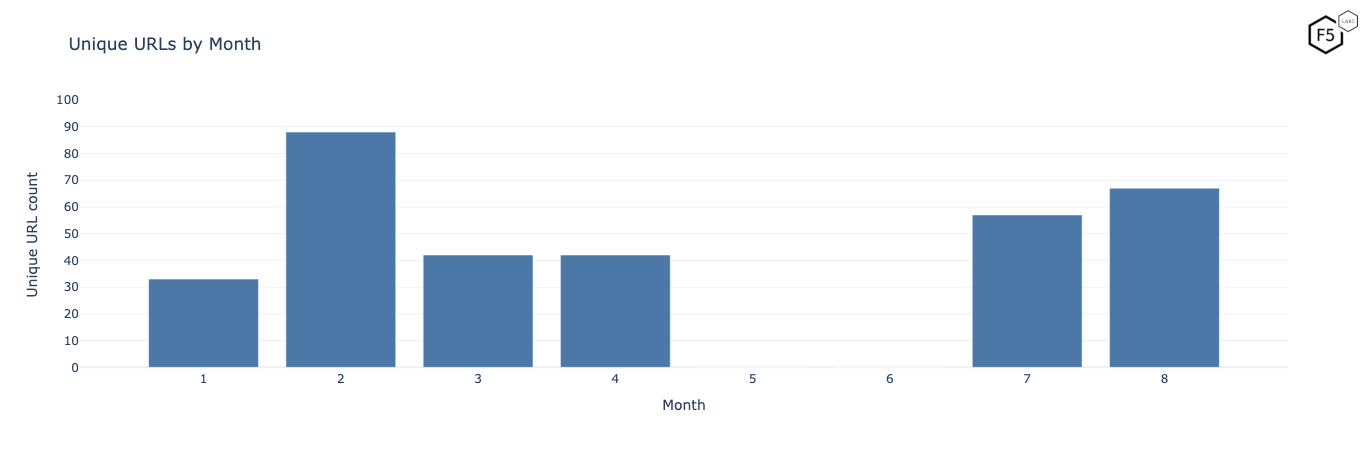
Figure 2: A bar chart of unique URLs by month, showing both increases and decreases as well as a 2 month outage.
The decrease between February and March removed 46 URLs, which we'll omit listing but were mostly capitalization variations on a pattern like "/DIRECTORY/.env" such as
'/Upload/.env' '/Public/.env' '/Misc/.env' '/Lib/.env'.
The following URLs were added between July and August 2025.
| URLs Added |
|---|
| '/exapi/.env' |
| '/.env.development' |
| '/.aws/credentials' |
| '/portal/.env' |
| '/public_html/.env' |
| '/pinfo.php' |
| '/client_secrets.json' |
| '/project/.env' |
| '/app/config/parameters.yml' |
| '/stag/.env' |
Table 3: URLs added between July and August 2025, with 10 listed URLs.
No URLs were removed.
Just one of the URLs removed in March ("/.aws/credentials") made it back into the set in August. The minimal amount of overlap is interesting. Clearly this actor has opinions on what does and doesn't work well for them, as well as perhaps realizing that in a lot of situations, most servers prefer lowercase paths, although they are not required.
Diversity of User-Agent Strings
One final quality of the traffic analyzed here is the immense diversity of User-Agent strings seen. Over 12,723 unique User-Agent strings are present, the vast majority of which are used exactly once. Given that this traffic was observed across a large number of sensors (44 over the course of the year), this would indicate that we are perhaps seeing only a small amount of a much larger corpus of User-Agent strings.
Most of the User-Agent strings were generally similar to actual browser User-Agents. The shortest were 30 characters long, using "Opera/9.12 (Windows NT 5.0; U)" and variations, and the longest was 278 characters, being an extremely long Mozilla string with a large number of other elements.
The first few characters of each User-Agent, up to the first “/” character, gives a good indication of the preferences of the scanner.
| Start | n |
|---|---|
| Mozilla | 11690 |
| Opera | 785 |
| Dalvik | 42 |
Table 4: Counts of the initial characters of observed User-Agent strings, showing Mozilla being by far the most frequent.
The rest are a huge mixture of strings, most approximating lesser known mobile browser agents.
Notably the User-Agents include many akin to "More Firefox 1.0 user agents strings -->>" which would indicate that this scanner is using a pre-determined list of User-Agents, perhaps scraped from somewhere, leading to link text being included in the output. This is a great hook to hang our analysis hat on. By leveraging this very odd User-Agent we can easily now identify the other IP addresses this scanner has used. For August 2025, there were 5 total, each in the same netblock as the IP analyzed here, specifically “78.153.140.{151,177,179,203,223}”
Why We Looked at this Data
This scanner has several identifiable characteristics; a prevalence of a relatively small, and now relatively static set of information disclosure URLs, a massive corpus of User-Agent strings, and the consistent use of one IP address across many months, although as we said at the beginning, this is likely just one IP that is used by the actual actor, who seems to favor the use of one particular UK based ISP. Some of the User-Agent strings are immediately identifiable, given that they appear to be artifacts from whatever list the actor uses to generate the massive corpus.
This sort of analysis may seem somewhat useless – certainly, this sort of scanning is far better defended against by simply prohibiting access to the sorts of paths that this scanner is attempting to find, along with ensuring that developers have good secrets discipline. Nevertheless, we feel it serves as an interesting example of how, when one dives deeply into a set of data, one will usually find some characteristic, some small flaw, that will enable more accurate detection and labeling.
We now turn our attention to the usual roundup of CVE metrics from August 2025.
Top CVEs for August
In August, CVE-2017-9841 saw over 47,000 exploitation attempts, maintaining its dominance (as shown in Table 1). CVE-2023-1389 dropped significantly in activity, while CVE-2019-9082 and CVE-2024-4577 showed upward trends. CVE-2022-24847 rounds out the top five with stable activity levels. Other CVEs in the top 10 include CVE-2022-42475, CVE-2022-22947, and CVE-2020-8958, each showing varying levels of activity. Movement among the top 10 was minimal, with minor position changes seen.
| # | CVE ID | CVE NAME | AUGUST Traffic | CVSS | EPSS | KEV |
|---|---|---|---|---|---|---|
| 1– | CVE-2017-9841 | PHPUnit eval-stdin.php RCE | 47297 (+3830) | 9.8 | 0.94406 – | Y |
| 2– | CVE-2023-1389 | TP-Link Archer AX21 Command Injection RCE | 5127 (-3633) | 8.8 | 0.93961 (-0.0006) | Y |
| 3↑ | CVE-2019-9082 | ThinkPHP PHP Injection RCE | 2446 (+243) | 8.8 | 0.94139 (-0.0001) | Y |
| 4↑ | CVE-2024-4577 | Apache PHP-CGI Argument Injection RCE | 2376 (+987) | 9.8 | 0.94365 (-0.0002) | Y |
| 5↓ | CVE-2022-24847 | GeoServer JNDI Lookup RCE | 2283 (-85) | 7.2 | 0.00191 (+0.0001) | N |
| 6↓ | CVE-2022-42475 | FortiOS FortiProxy SSL-VPN Heap Overflow RCE | 2229 (-60) | 9.8 | 0.94003 – | Y |
| 7↓ | CVE-2022-22947 | Spring Cloud Gateway Actuator Code Injection RCE | 2110 (-63) | 10.0 | 0.94461 (-0.0001) | Y |
| 8↓ | CVE-2020-8958 | Guangzhou ONU Command Injection RCE | 2055 (+92) | 7.2 | 0.8591 (+0.0041) | N |
| 9↓ | CVE-2025-31324 | SAP NetWeaver Metadata Uploader Unauthenticated Upload | 1642 (-233) | 9.8 | 0.30208 (-0.3357) | Y |
| 10– | CVE-2022-47945 | ThinkPHP Lang Parameter LFI RCE | 1191 (+120) | 9.8 | 0.89687 (+0.0115) | N |
Table 5: Top 10 CVEs for August 2025. CVSS Scores are v3.1. All data is as of 9/1/2025.
Long-Term Targeting Trends
The following plot shows CVE-2017-9841 remains the most exploited vulnerability this month, showing a significant increase in activity compared to July but also continuing its dominance of the overall CVE observations we make. CVE-2023-1389 experienced a small drop in exploitation attempts, continuing in second place. CVE-2019-9082 and CVE-2024-4577 both saw increased activity, climbing to third and fourth positions respectively. CVE-2022-24847 maintained its presence in the top five, albeit with a slight decrease in activity, and falling from third most commonly seen to the fifth position.
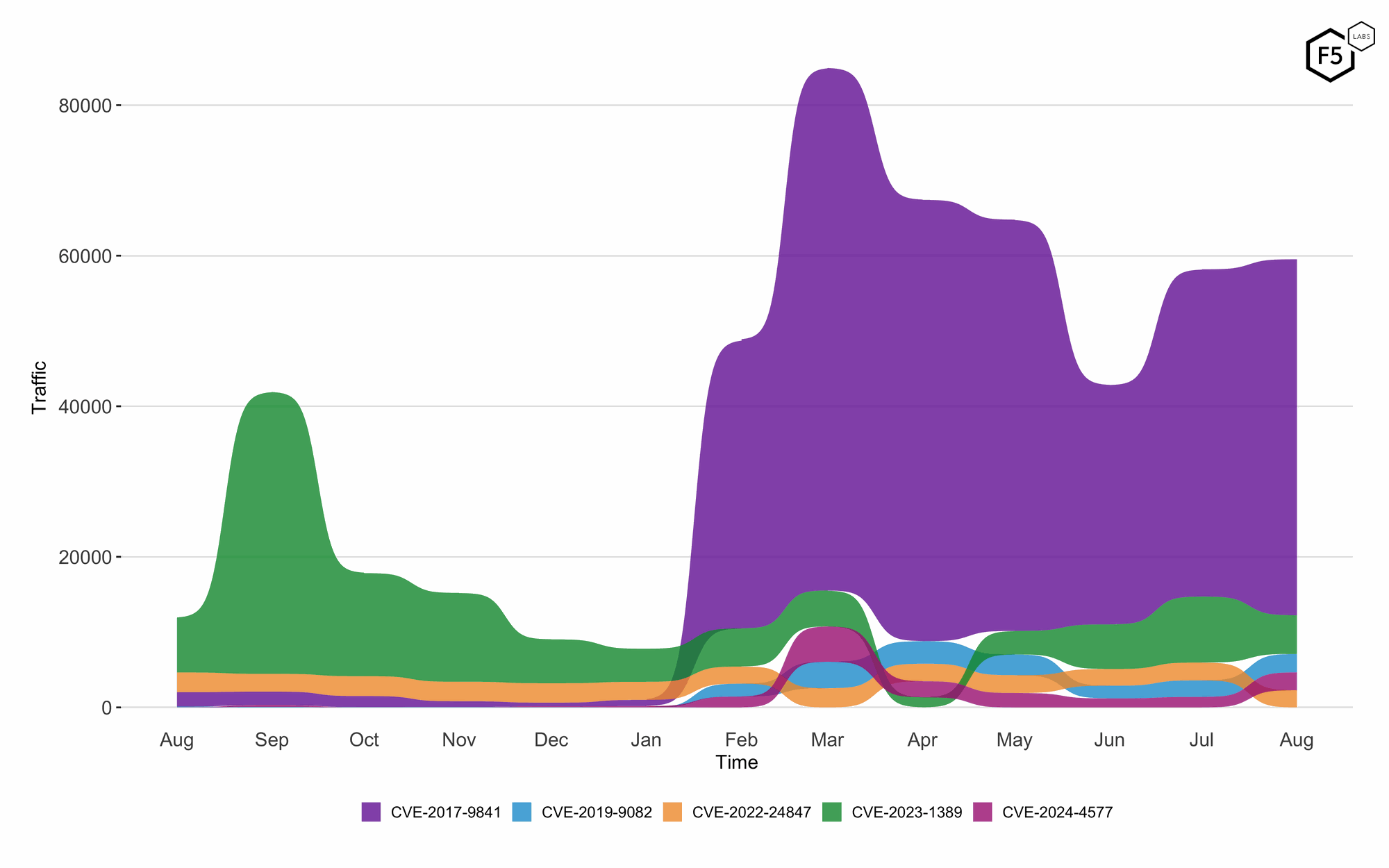
Figure 3: Twelve-month bump plot of the top 5 CVEs. Note the continued dominance of CVE-2017-9841.
Long-Term Trends
No specific CVEs were highlighted for long-term trends this month, so Figure 4 provides a general overview of activity across various vulnerabilities. CVE-2017-9841 continues to dominate the landscape with sustained high activity levels, while other CVEs show moderate fluctuations.
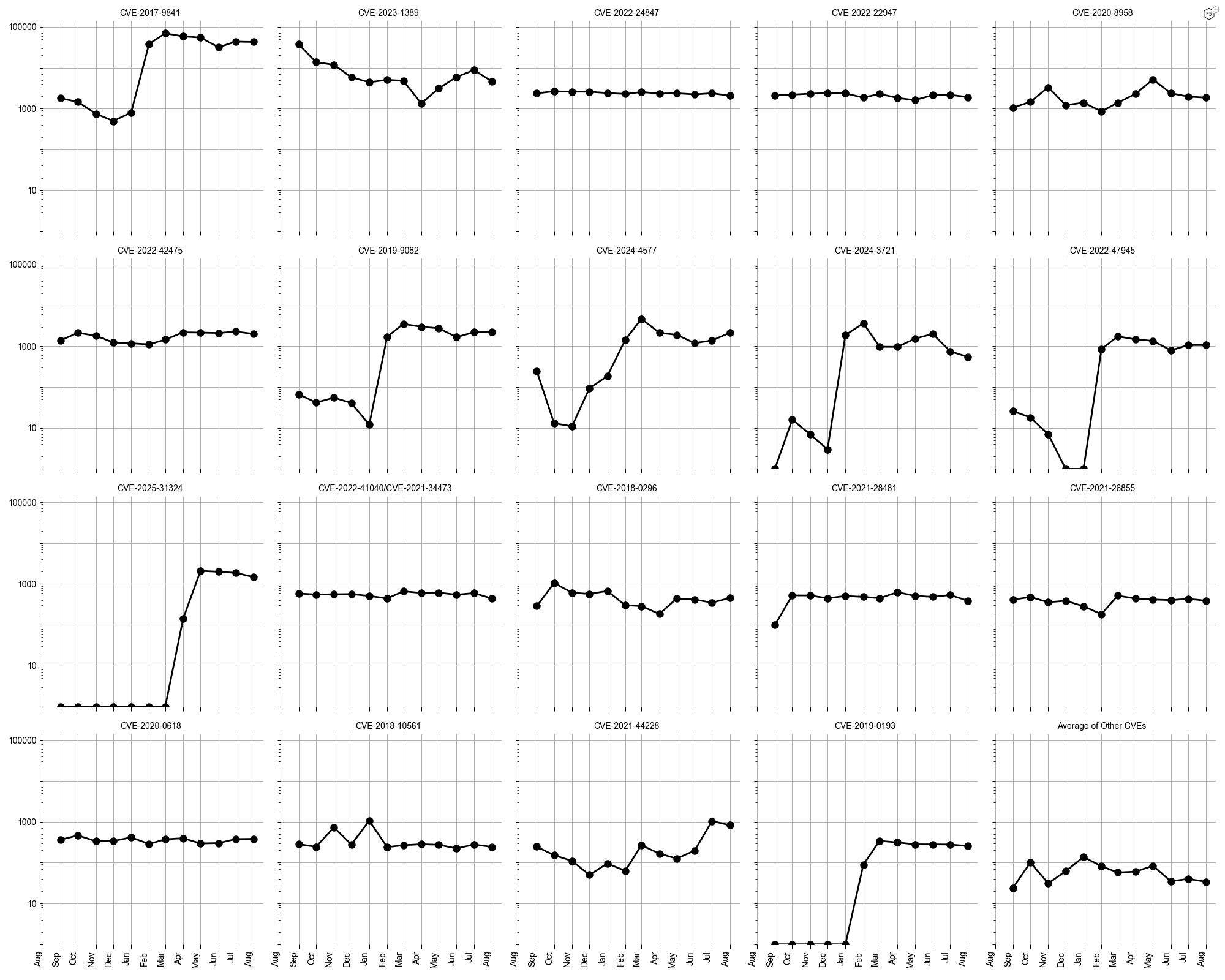
Figure 4: Evolution of vulnerability targeting in the last twelve months, shown using a logarithmic scale for ease of comparison.
Conclusion
The data from August highlights the persistent threat posed by vulnerabilities like CVE-2017-9841 and CVE-2023-1389. Organizations must prioritize patching and secure configurations to mitigate risks. Staying informed about trends and actively monitoring systems are key to maintaining cybersecurity resilience.
Further, if resources allow, an occasional deep analysis of a particular set of traffic that is of concern can often reveal very specific detections and provide even greater protection than generic signatures.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


