This ancient bot, also known as the “Mambo” bot (due to an old vulnerability in the Mambo CMS it tried to exploit) has been around for a very long time, and many variations of it have been seen. However, from our observations, it is still being actively used in recent exploitations.
After successfully exploiting an existing vulnerability on an unpatched webserver, a malicious Perl-based script is executed and turns the webserver into a member of a botnet. The names of the variables and functions in the code reveal that the bot author is likely a Portuguese speaker. Examples are words such as “servidor” (server), “conectar” (connect) and “pacotes” (packets).
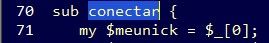
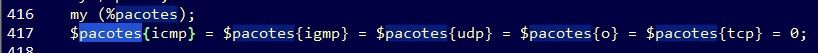
Figure 1: Samples of Portuguese script
Like every “good” bot, perlb0t supports several functionalities, such as port scanning, using Google search to find other vulnerable servers (also known as “Google Dorking”), running shell commands on the server and more. However, it seems that the main business model of this bot is a DDoS service.
The bot supports HTTP and TCP floods, by sending “GET” requests or just opening (3-way handshake) and closing TCP connections respectively.
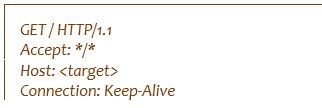
Figure 2: Straightforward “GET” attack
But the most interesting DDoS functionality in this bot is the “UDP flood”, as its author calls it. At first glance it seems like the author is trying to create specific floods (ICMP, UDP, IGMP, TCP), however when further analyzing, this functionality is no more than just sending malformed packets of different protocols. Let’s look at this one…
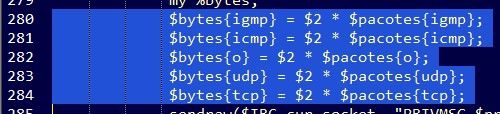
Figure 3: UDP flood functionality
The C&C (Command&Control) instructs its bots to perform a “UDP flood” with 3 parameters:
Target (IP/Domain)
Packet size (in Kbytes)
Duration (in seconds)
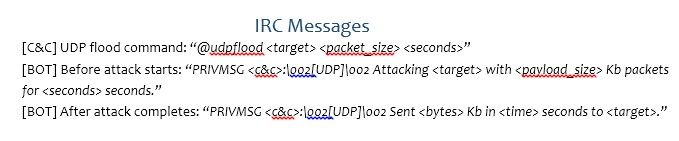
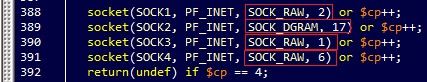
Figure 4: Using raw and datagram sockets
As we see from the source code, the bot uses raw sockets for the three types of packets, with different protocol numbers as the third argument, and one datagram socket for simple UDP. Using a raw socket enables the attacker to control more fields in the packet itself, however the bot writer needs to manually construct all the protocol headers.
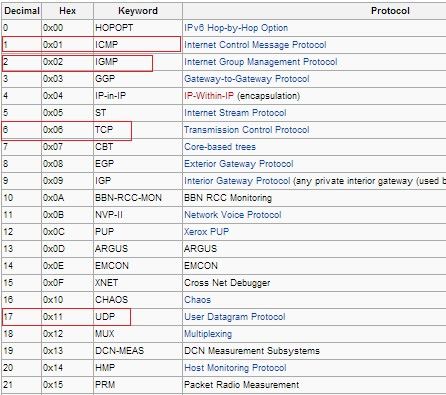
Figure 5: Table of supported IP protocols
By looking at the table of supported IP protocols, we see that the bot creates raw packets of IGMP, ICMP and TCP protocols. Those packets are just being marked with those protocol numbers, however other fields and headers are not actually set. The packet is filled with “A” characters according to the size specified by the C&C command, making the packet a malformed one.
However, even more interesting is the distinction the bot writer makes between the above protocols and other protocols the writer uses afterward. After sending malformed IGMP, UDP, ICMP and TCP packets, the bot will send 252 additional malformed packets of all other protocols (running from 3 to 255 protocol numbers, skipping previously sent protocols).
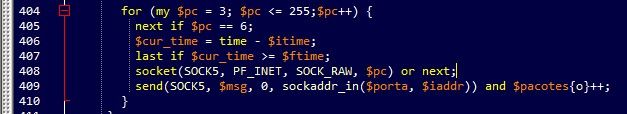
Figure 6: One loop in the attack
The above screenshot displays a single loop in the attack, while each loop uses a different source port sequentially (running from 1 to 65000). Note the inaccuracy; the bot writer must have meant to run over all the 65k ports, which is 65,536.
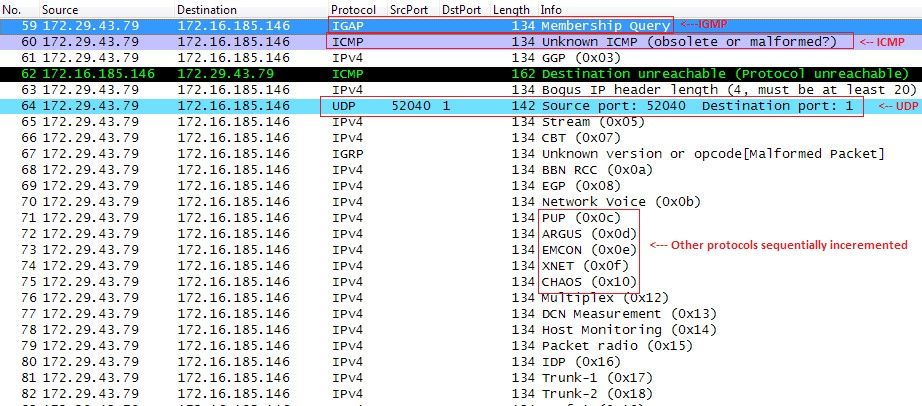
Figure 7: Sample bot traffic
As we see from the bot’s traffic, a sequence of malformed packets is sent (the only well-formed is UDP), while the protocol number is sequentially incremented. (In the screenshot, this is shown as: 0xc, 0xd, 0xe, 0xf, 0x10…) It is important to note, that creating raw sockets needs administrative privileges, so if the infected webserver does not run as the root user, the attack will be a simple UDP flood.
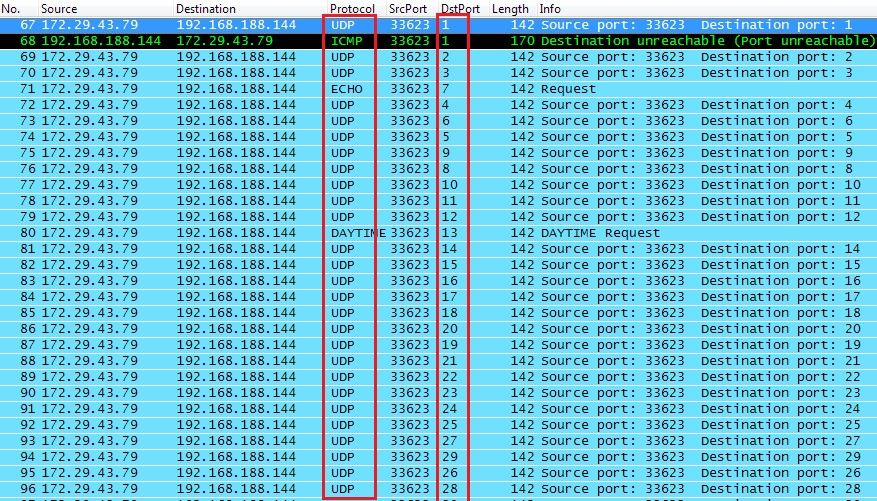
Figure 8: UDP flood
Note the destination port sequence.
To sum up, a lot of attackers are lazy. They will do the minimum required to make their money suggesting DDoS services. As we learn from this example, an ancient bot first detected back around 2005 is still in the wild. Having the same basic structure, with edited nuances and sometimes functionality, it still spreads by exploiting recently discovered web vulnerabilities, making your web server part of a botnet.


