In part 1 of this blog series (/content/f5-labs/en/labs/articles/threat-intelligence/phishing-for-information-part-1-how-phishers-bait-their-hooks-with-information-you-volunteer.html), we saw an everyday example of how easily a competent corporate executive (or any other employee, for that matter) can be drawn into a phishing scam through social engineering. In this installment, we see how some of the seemingly innocent actions we take (information we post) on the Internet make the job of a phisher simple—like taking candy from a baby.
Since spear phishers go after a specific organization, they need to know who works there before they can begin their targeting. A lot of people tag themselves on various social media sites as an employee of a particular company. LinkedIn is a site that provides lots of details on where people work. Quora is another site where tech people congregate:
Through these sites, it’s not hard for phishers to gather up a list of names of employees at a specific organization.
Social Media and Personal Information
Despite the security team’s best efforts to prevent it, employees will share and spread information about themselves all over the Internet. Social media companies expend tremendous effort to encourage people to join and post information about themselves. Some valuable bits of information that attackers can use are:
- Work history
- Education information (college and high school attended)
- Family and relationship information
- Comments on links
- Dates of important life events
- Places visited
- Favorite sites, movies, TV shows, books, quotes, etc.
- Photographs
Profiling
All these pieces of information provide powerful leverage points for attackers, but they also provide a lot of valuable indirect information. As our phishing example in part 1 (/content/f5-labs/en/labs/articles/threat-intelligence/phishing-for-information-part-1-how-phishers-bait-their-hooks-with-information-you-volunteer.html) points out, attackers can observe the writing style of the people they want to impersonate. Beyond that, they can also create detailed psychological profiles of victims. There are a number of tools and techniques available to do things like:
- Analyze sentiment to determine people’s opinions and political leanings1
- Analyze posting times to determine when people are awake (and asleep) and what their home time zones are2
- Determine an individual’s personality type, which can inform manipulation techniques3
- Analyze relationships and friendship ties4
With sites like Facebook that host nearly 2 billion users,5 it’s very easy to craft a Google search for someone with “[name] [location] site:facebook.com” to find their page.
Many social media users are part of interest groups, which can provide useful leverage points for a phisher.
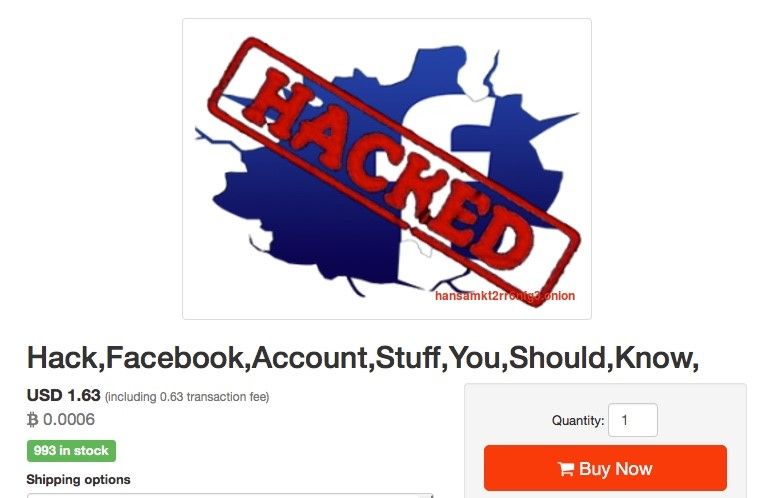
Even when someone sets their social media profile to “private,” it’s still not too difficult for an attacker to break in and get what they want. Here is a hacking service being advertised on a Darknet for just that purpose:
People Search Engines
In addition to social media sites, there are numerous “people search” sites like Pipl, Spokeo, and ZabaSearch. Many of these sites pull together profiles based on dozens of resources. Sometimes they’re not very helpful, like this example for me, because I’m a paranoid security guy:
However, different sites can dig up some interesting data, like this example:
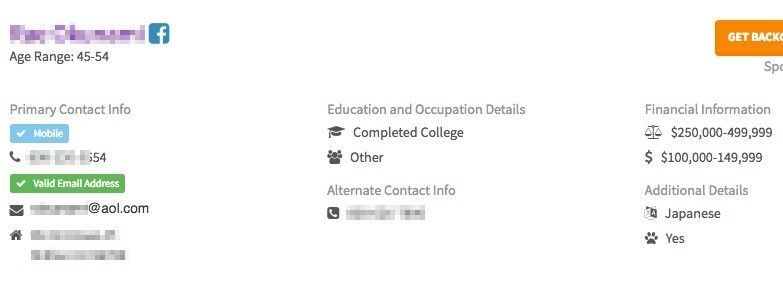
Note how this site provides Facebook information, email address, annual income, education, phone number, age range, and even racial profiling. Here’s some typical information you can get from these kinds of sites:
- Home address
- Mobile phone number
- Home (landline) phone number
- Age
- Salary range
- Spouse and family
- Email address, which leads to possible usernames
- Middle name
- Maiden name
Most employees don’t think about things like this—because most employees don’t think like bad guys. It doesn’t occur to them how much personal and work-related information they are freely volunteering on various websites—or how easy they make it for phishers to pull information together into some pretty comprehensive professional dossiers. The lesson here is think before you volunteer information about yourself and your work, and limit the number of websites where you do this. In Part 3 of this series, we look at how attackers (phishers) gather up information about your organization.


