To pull off successful phishing scams, at a minimum, attackers need information about your organization and your employees. We saw several ways they go about getting this information in parts 1, 2, and 3 of this blog series (How Phishers Bait Their Hooks… (/content/f5-labs/en/labs/articles/threat-intelligence/phishing-for-information-part-1-how-phishers-bait-their-hooks-with-information-you-volunteer.html), How Attackers Collect Data About Your Employees (/content/f5-labs/en/labs/articles/threat-intelligence/phishing-for-information-part-2-how-attackers-collect-data-about-your-employees.html), and How Attackers Gather Data About Your Organization (/content/f5-labs/en/labs/articles/threat-intelligence/phishing-for-information-part-3-how-attackers-gather-data-about-your-organization.html)). But one area organizations often overlook is the information that’s leaking out of their systems.
Improperly configured network systems and applications can leak internal configuration and infrastructure information. This can include information like server names, private network addresses, email addresses, and even usernames. Devices and software that have been known in the past to leak internal data onto the Internet include DNS servers (/content/f5-labs/en/labs/articles/threat-intelligence/dns-is-still-the-achilles-heel-of-the-internet-25613.html), self-signed certificates, email headers, web servers,1 web cookies, and web applications.2
Here is a simple example of how a sloppily configured web server can reveal the internal IP addressing scheme:
HTTP/1.0 200 OK
Date: Mon May 22 15:31:46 PDT 2017
Server: Macrohard-YYZ/6.0
Connection: Keep-Alive
Content-Type: text/html
X-Powered-By: BTQ.NET
Accept-Range: bytes
Last-Modified: Sat, May 20 04:14:01 PDT 2017
Content-Length: 1433
Connection-Location: http://192.168.0.10/index.htm
Attackers can also comb through web application source code to look for developer names, internal code words, and even references to supposedly hidden services.3 Almost all of these kinds of technical information leakages are rated very low impact and are usually deprioritized in remediation.
Application Platform Discovery
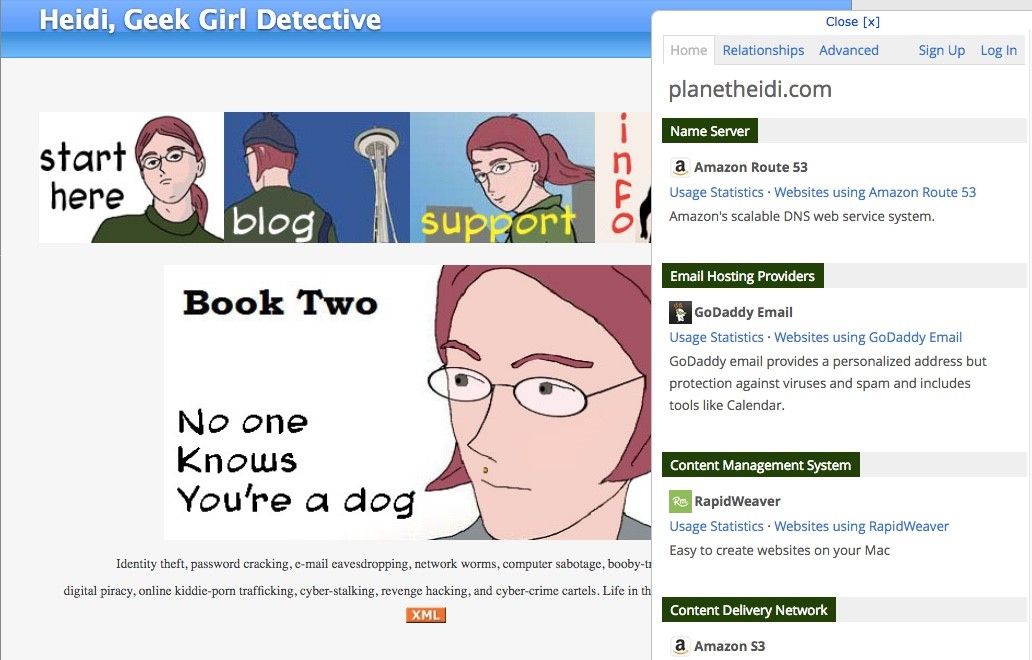
Applications are rarely built from scratch but are instead assembled from libraries and existing frameworks. All of these application components can contain vulnerabilities as well as clues to the development team and processes in an organization. There are numerous easy-to-use tools that can uncover what is being deployed. Here is the BuiltWith tool’s analysis of a site:
Email Headers
An excellent source of internal configuration information can be gleaned from email headers. Attackers can simply fire off a few email inquiries to folks at an organization and see what they can find. Here’s a typical email header using our example company, Boring Aeroplanes, from Part 1 of this series. Note both internal and external IP addresses are shown, along with server names:
Received: from edgeri.boringaeroplanes.com (host-12-154-167-196.boringaeroplanes.com. [312.154.167.296])
Received-SPF: pass (google.com: domain of charles.clutterbuck@boringaeroplanes.com
designates 312.154.167.296 as permitted sender) client-ip=312.154.167.296;
Received: from edgeri.boringaeroplanes.com (172.31.1.48) by
WEXCRIB00001059.corp.internal.boringaeroplanes.com (172.31.1.42) with Microsoft
SMTP Server id 14.3.301.0; Fri, 28 Apr 2017 10:40:36 -0400
Received: from WEXCRIB00001065.corp.internal.boringaeroplanes.com (70.338.297.31)
by WEXCRIB00001059.corp.internal.boringaeroplanes.com (172.31.1.42) with
Microsoft SMTP Server (TLS) id 14.3.301.0; Fri, 28 Apr 2017 10:39:23 -0400
Received: from WEXCRIB00001054.corp.internal.boringaeroplanes.com
([169.254.9.522]) by WEXCRIB00001065.corp.internal.boringaeroplanes.com
([70.338.297.31]) with mapi id 14.03.0301.000; Fri, 28 Apr 2017 10:39:31 -0400
From: "Clutterbuck, Chuck" <charles.clutterbuck@boringaeroplanes.com>
Subject: Inquiry
Thread-Topic: Inquiry
Thread-Index: AdLAKumC2+2KaqenReOr0muBBLJpfQ==
Date: Fri, 28 Apr 2017 14:39:30 +0000
Accept-Language: en-US
x-originating-ip: [10.16.15.170]
x-keywords4: SentInternet
x-cfgdisclaimer: Processed
MIME-Version: 1.0
Return-Path: charles.clutterbuck@boringaeroplanes.com
From this, attackers have a number of IP addresses, and they know what software the mail server is running and how email flows out of the organization.
In parts 1 through 4 of this blog series, we’ve seen how cyber attackers scavenge the Internet to build profiles for phishing and other kinds of social engineering attacks. In part 5, we look at what you can do to protect yourself from such scams.


