
The Sensor Intel Series is created in partnership with Efflux , who maintains a globally distributed network of sensors from which we derive attack telemetry.
------------------------------------------------------------------------------------------
Introduction
Welcome to the February 2024 installment of the Sensor Intelligence Series, our monthly summary of vulnerability intelligence based on distributed passive sensor data. This month’s attack data is, at least in the most seen attacks, much like recent months. We continued to tweak our approach to threat hunting this month and managed to find 27 new to us CVEs buried in low volume traffic.
New CVE Signatures
Some of these you may recognize, such as CVE-2018-7600 (AKA “Drupalgeddon 2”), which was a very major issue when it came out. That we still see scans for this vulnerability, albeit at very low levels, may surprise some readers. We assume that this is most likely due to off the shelf vulnerability scanner activity, which may include payloads for many older vulnerabilities. It is however interesting to note that while none of these CVEs showed very high levels of activity, they all had at least some.
Cross Site Scripting (XSS) CVEs
- CVE-2005-3129 (Squirrelmail)
- CVE-2009-1872 (Adobe Cold Fusion)
- CVE-2011-4926 (Adminize WordPress plugin)
- CVE-2014-4535 (Import Legacy Media Wordpress plugin)
- CVE-2016-1000149 (simpel-reserveren WordPress plugin)
- CVE-2020-17453 (WSO2 Management Console)
- CVE-2020-27982 (IceWarp)
- CVE-2020-9344 (Subversion ALM)
- CVE-2021-21801 (Advantech R-SeeNet)
- CVE-2021-38702 (Cyberoam NetGenie devices)
- CVE-2022-0653 (Profile Builder – User Profile & User Registration Forms WordPress plugin)
- CVE-2022-22954 (VMware Workspace ONE Access and Identity Manager)
Remote Code Execution (RCE) CVEs
- CVE-2018-7600 (Drupal)
- CVE-2010-0219 (Apache Axis)
- CVE-2012-1823 (PHP)
- CVE-2015-2051 (D-Link DIR-645 Wired Wireless Router)
- CVE-2015-8562 (Joomla!)
- CVE-2020-24949 (PHP-Fusion)
- CVE-2021-25003 (WPCargo Track and Trace WordPress plugin)
- CVE-2022-0885 (Member Hero WordPress plugin)
Directory Traversal CVEs
- CVE-2015-4074 (Helpdesk Pro plugin for Joomla!)
- CVE-2018-20463 (JSmol2WP WordPress plugin)
- CVE-2022-40734 (UniSharp laravel-filemanager)
Unauthorized Data Access CVEs
- CVE-2019-2588 (BI Publisher component of Oracle Fusion Middleware)
SQL Injection CVEs
- CVE-2020-22211 (74cms)
- CVE-2023-25651 (ZTE mobile internet products)
With all that out of the way, let’s get to the numbers.
February Vulnerabilities by the Numbers
Figure 1 shows February attack traffic for the top ten CVEs that we track. CVE-2020-11625 which jumped to the top of our list last month and has remained there this month. This vulnerability has shown some odd patterns, having the exact identical number of requests for November and December 2023, before jumping up 250% to nearly 5700 connections in January, and now falling off to 3732 connections this month. This is a vulnerability in few different web-enabled video security cameras from brand AvertX. In other words, this is yet another IoT vulnerability, supporting the ongoing trend of IoT scanning and exploitation in our passive sensors. CVE-2020-8958, a perennial top scorer, fell several places this month, and CVE-2017-9841, an old but critical vulnerability in PHPUnit, replaces it in the number two spot.
Leaving the top ten, Table 1 shows the traffic volume for the top 19 vulnerabilities that we’re tracking, along with change from the previous month, CVSS score, and EPSS score. In terms of high-traffic CVEs, the percent change is usually instructive. We did this in part because the table was getting so large as to not be very useful, as well as being somewhat confusing for a quick visual scan, as small changes in low traffic vulnerabilities would show very large percentage change.
| CVE Number | February Traffic | Change from January | Percent Change | CVSS v3.x | EPSS Score |
| CVE-2017-9841 | 2531 | 383 | 17.83% | 9.8 | 100.0% |
| CVE-2021-44228 | 463 | 234 | 102.18% | 10 | 100.0% |
| CVE-2021-3129 | 696 | 204 | 41.46% | 9.8 | 100.0% |
| CVE-2019-9082 | 232 | 198 | 582.35% | 8.8 | 99.9% |
| CVE-2022-22947 | 1858 | 158 | 9.29% | 10 | 100.0% |
| CVE-2021-28481 | 465 | 66 | 16.54% | 9.8 | 92.0% |
| CVE-2019-18935 | 178 | 1 | 0.56% | 9.8 | 98.9% |
| CVE-2017-1000226 | 175 | 0 | 0.00% | 5.3 | 33.5% |
| CVE-2021-26086 | 173 | -7 | -3.89% | 5.3 | 98.9% |
| CVE-2020-0618 | 387 | -30 | -7.19% | 8.8 | 99.9% |
| CVE-2021-26855 | 132 | -47 | -26.26% | 9.8 | 100.0% |
| Citrix XML Buffer Overflow | 240 | -73 | -23.32% | n/a | n/a |
| CVE-2014-2908 | 236 | -77 | -24.60% | n/a | n/a |
| CVE-2021-40539 | 176 | -95 | -35.06% | 9.8 | 100.0% |
| CVE-2022-42475 | 1134 | -106 | -8.555 | 9.8 | 97.2% |
| CVE-2022-24847 | 2260 | -262 | -10.39% | 7.2 | 39.7% |
| CVE-2022-41040/CVE-2021-34473 | 607 | -482 | -44.26% | 9.8 | n/a |
| CVE-2020-8958 | 1532 | -1562 | -50.485 | 7.2 | 98.1% |
| CVE-2020-11625 | 3732 | -1938 | -34.18% | 5.3 | 46.2% |
Table 1. CVE targeting volumes for February, along with change from January, percent change, CVSS v3 score, and EPSS score.
Targeting Trends
As Table 1 shows, there’s a lot of month to month variability in terms of targeting volume, so to visualize some of these changes, Figure 2 is a bump plot showing the change in traffic volume and position over the last twelve months. We see our current frontrunner, CVE-2020-11625, falling off in volume somewhat but still going strong. We also can observe the track of CVE-2020-8958 from its high last June, only to rebound in January back to second, and now fall down to fifth place.
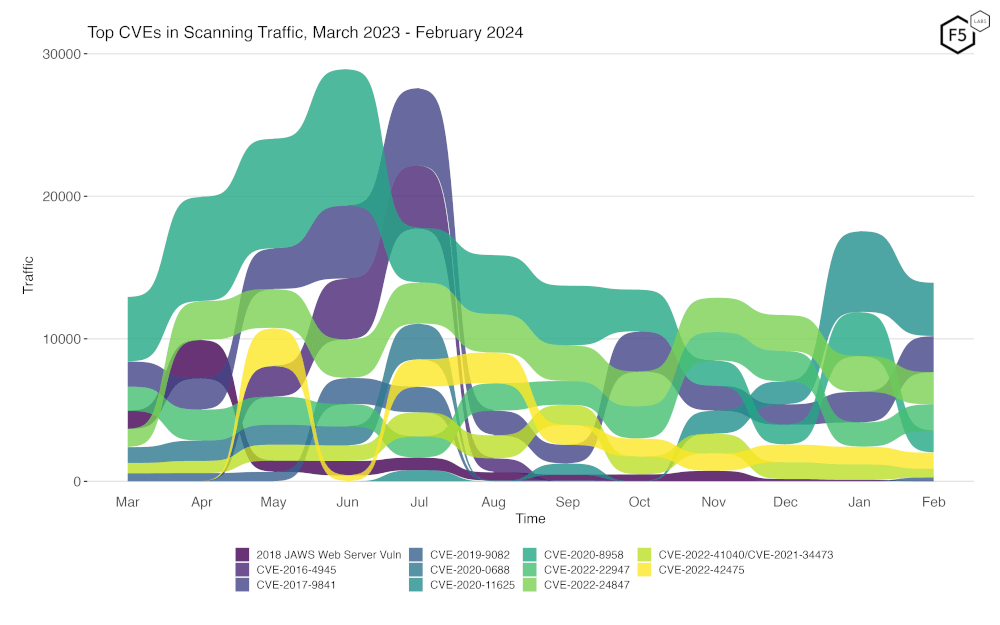
Figure 2. Evolution of vulnerability targeting in the last twelve months. Most CVEs we track here remained consistent, with the exception of CVE-2020-8958 and CVE-2017-9841.
Long Term Trends
Figure 3 shows traffic volume over the past year for the top 19 CVEs by volume of traffic, along with a monthly average of the remaining CVEs.
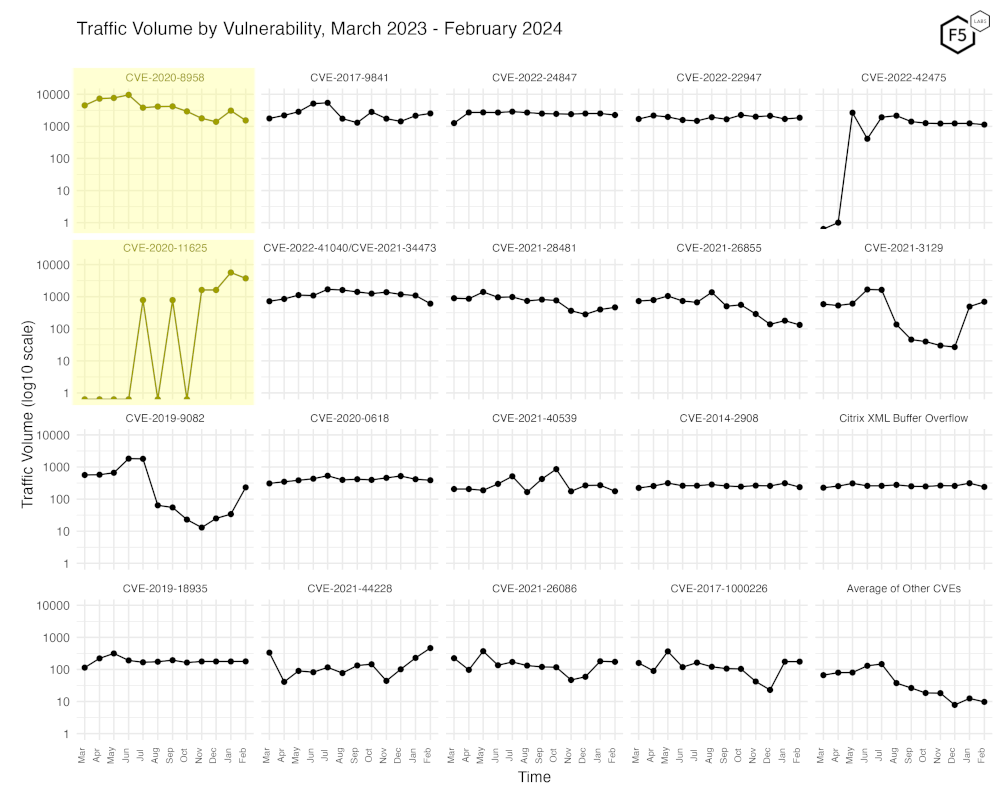
Figure 3. Traffic volume by vulnerability. Notable is the spiky variability and recent increase in scans for CVE-2020-11625.
While the obvious variability of CVE-2020-11625 is easy to spot here, it’s a little bit less easy to see the decline in traffic for CVE-2020-8958. But note that we’re using a logarithmic scale, and this will conceal relatively small changes. We use this because even within the top 19 of CVEs scanned for by traffic volume, there is a lot of range in the amount of traffic. CVE-2019-9082 is a good example, having been as low as 10 requests a few months ago, and now in the hundreds.
Conclusions
Under the hood, this month’s installment continues our push towards technical and procedural changes. We continue to add more CVEs, even if they are not high traffic ones. In part we do this to simply have a more precise output, but since the raw observations noted here also feed the EPSS vulnerability intelligence system, the more exhaustive we can be, the better the results.
Our recommendations remain much the same – keep an eye on your IoT devices, change default creds, patch not only your frontline apps but also your cameras, routers, and similar gear.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


