F5 Labs recently published a report called Lessons Learned from a Decade of Data Breaches. The purpose of our research was to figure out how attackers are breaching businesses and determine the attack paths—from the initial attack through to the root cause of the breach. The 433 cases we looked at were limited to breaches where there was a known attack type, root cause, data type and count of records breached, or cost of the breach. Not all of the cases included every one of these elements, but there was enough compelling data in total to conclude that 86% of the breach cases started with an application or identity attack.

The report totaled breach records by type, the results of which were sobering:
- 11.8 billion records were compromised in just 337 cases
- 10.3 billion usernames, passwords, and email accounts were breached, which is equivalent to 1.36 records per person on the planet, or 32 records per US citizen
- 280 million social security numbers (SSNs) were breached, which is equal to 86.5% of the US population
The startling counts of breached records in the report start to make sense when you consider that over half of the world’s population today is online. Society functions in an online world now where applications are the new storefronts of businesses and in a lot of cases, applications are the business.
Applications are also the gateway to data—both corporate and customer data—which has immense value to attackers, whether their motive is cybercrime, hacktivism, espionage, or warfare. The concern over the safety of applications and data is borne out in a separate report by F5 and Ponemon, The Evolving Role of CISOs and their Importance to the Business (/content/f5-labs/en/labs/articles/cisotociso/cisos-striving-toward-proactive-security-strategies.html) in which respondents were asked to rank the top threats to their security ecosystem. On a scale of 1 (minimal impact) to 10 (significant impact), respondents ranked both “insecure applications” and “data exfiltration” at 8.2.
Attacking Applications Directly
One-way attackers can get to data is by exploiting applications directly. In fact, applications were the initial target of attack in the majority of breaches at 53%. Those attacks exploited the systems by targeting web application vulnerabilities with primarily injection attacks against various types of forum software at the application services layer and SQL injection attacks.
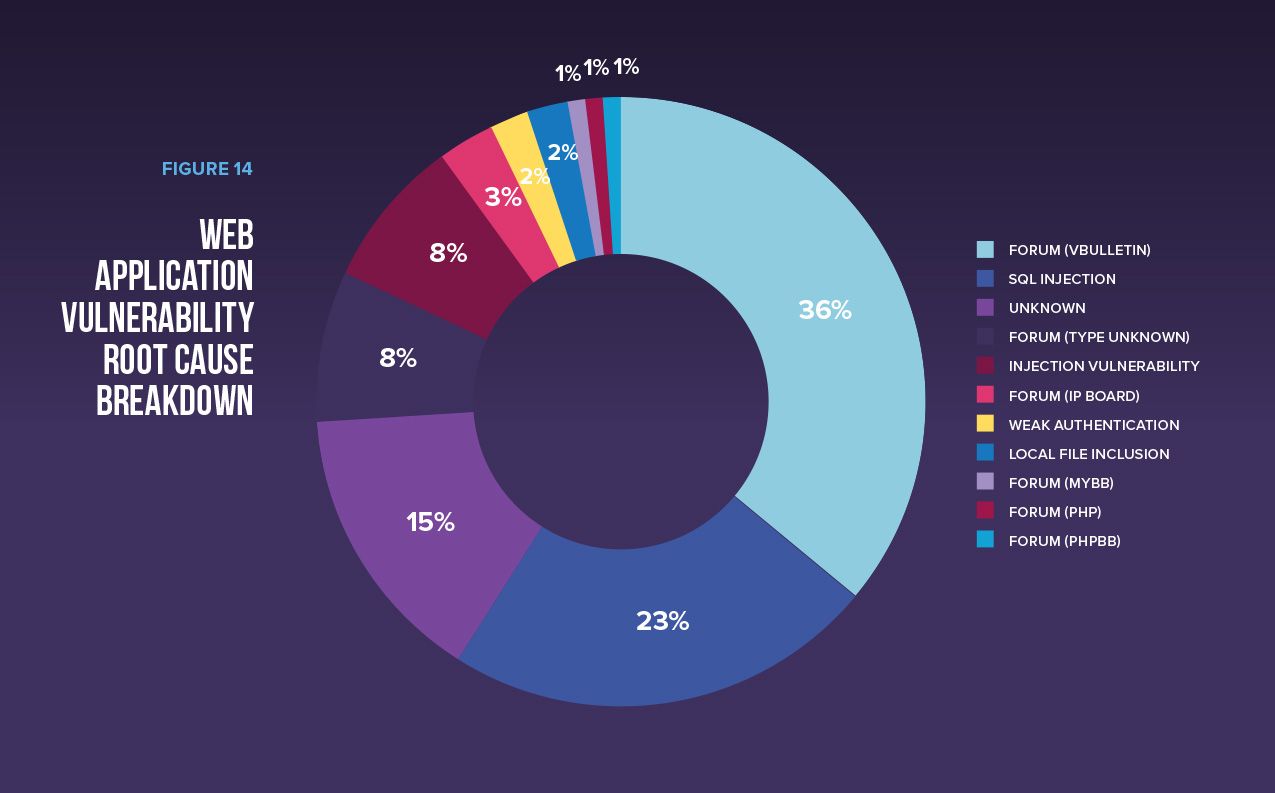
Web Application Vulnerability Root Cause Breakdown
The obvious takeaway here is that these two most commonly breached application vulnerabilities represent low hanging fruit for attackers.
Forum software is a favorite target for attackers because they consume user content that if not sanitized properly could be a crafty little malicious script that injects a PHP backdoor. Forum makers (as well as CMS providers that have similar issues with their software) consistently publish critical remote code execution vulnerabilities. In turn, attackers automate their recon scans to look for the specific forum software for which they have written an exploit. If you are running a forum software with an unpatched critical remote code execution vulnerability, the chances are high that you have already been exploited.
SQL injection, a critical vulnerability that enables an attacker to inject SQL queries and execute administrative operations on the backend database, shouldn’t require explanation because it’s been around for decades. It’s a complete and utter InfoSec fail for this to be a top attack root cause. These vulnerabilities are extremely easy for anyone (an attacker, or the company’s security team) to find—and for attackers to exploit.
Security professionals should expect these types of vulnerabilities to be targets of attack and plan their vulnerability management accordingly.
Getting to Your Data through User Identity Attacks
When the development and security teams have done a good job securing an application, it’s much easier for attackers to get to the data through users who have access to the application and the data within it.
In the cases we researched, identities were the initial attack target in 33% of the breaches. Most of these attacks were attributed to phishing; it turns out tricking a user into giving up their credentials is remarkably easy, despite the industry’s security awareness training efforts. Thanks to social media and consumers’ eagerness to share every aspect of their personal lives (see data collected from various public forms (/content/f5-labs/en/labs/articles/threat-intelligence/phishing-the-secret-of-its-success-and-what-you-can-do-to-stop-it.html)), phishing attacks will remain highly effective for the foreseeable future.
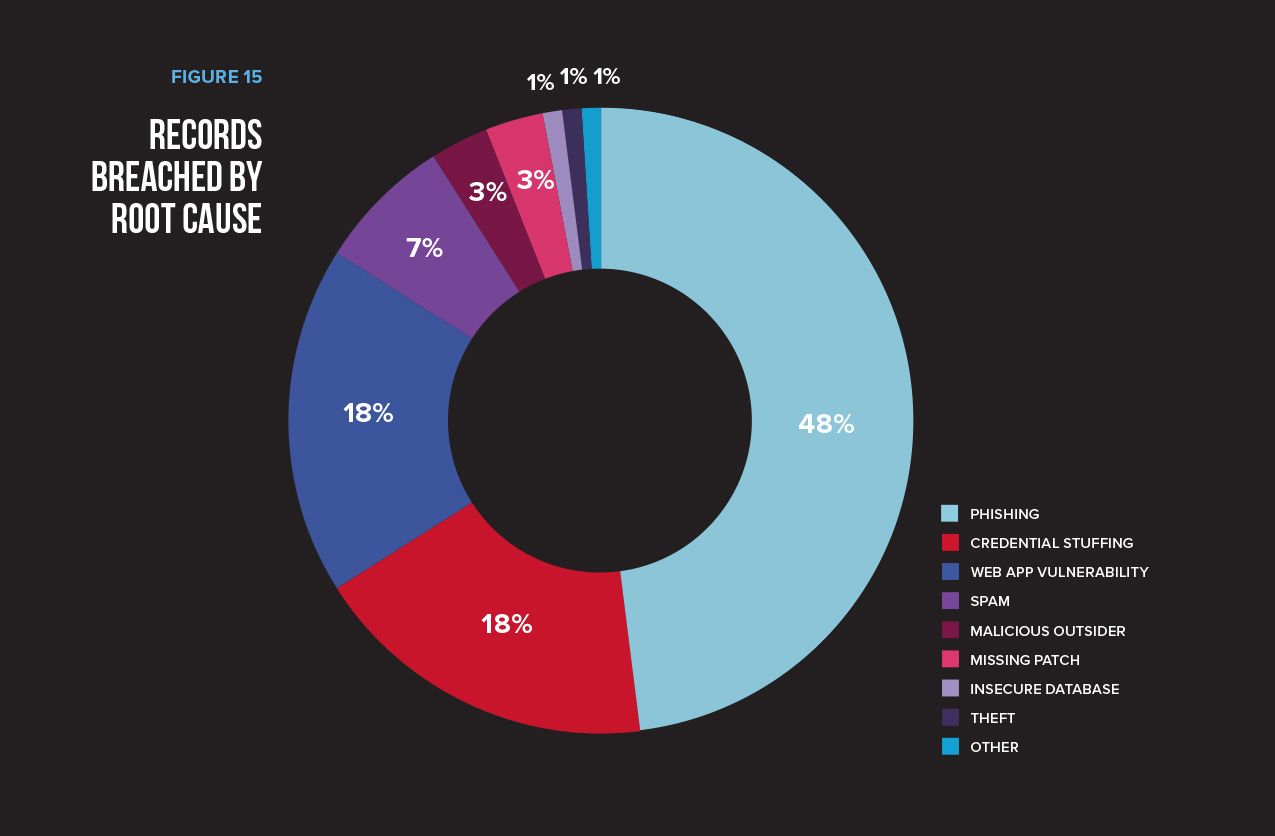
Records Breached by Root Cause
Unfortunately, phishing has no boundaries. From executives, to receptionists, to system administrators, these attacks are successful. Our breach trends report points out that even the NSA targets system administrators through phishing attacks. It also states that more data is collected by attackers through phishing attacks than any other attack type. From the attacker standpoint, that’s a measure of success, and one that reassures that phishing won’t stop anytime soon.
Protecting the Two Most Common Attack Vectors
Security teams are constantly struggling to keep up with compliance requirements, securing new business initiatives, and vulnerability management, not to mention operating their security controls. Feeling like you are on the wrong end of a firehose is common in the InfoSec world. So, leverage the research available to you and appropriately prioritize your security initiatives. If 86% of breaches start with identities and applications, then managing application vulnerabilities and limiting the impact of exploited identities should be high on your priority list. It’s encouraging to see that many organizations are at least moving in the right direction by steadily increasing their investment in application protection. The CISOs we surveyed (/content/f5-labs/en/labs/articles/cisotociso/cisos-striving-toward-proactive-security-strategies.html) said they were spending 12% on app protection two years ago. That has increased to 17% today and is expected to rise to 29% two years from now.
You can “86” most of your cyber attackers by doing the following:
Deploy a web application firewall (WAF). Do this immediately if you don’t already have one. You don’t need money to do this—and you don’t have to apply blocking rules (before you know what you are doing) that might take down your application. There are decent, free WAFs (in software form) that you can deploy in listen-only mode. Once you’ve logged and monitored enough of your web application’s traffic, you can begin defining a blocking policy that won’t take down your app but will protect you from attacks that are likely to exploit it. The added bonus is that if your app is actively being exploited, the post data in your WAF logs will tell you exactly how.
Note that WAFs are not easy to manage. They require technical skillsets in both web application vulnerabilities and secure development (in the language your application is written in), and someone who knows how the application works. It’s rare for one person to have all these skills, so it takes a team to operate a WAF effectively. Freeware solutions provide a good way to get your feet wet but can quickly become cumbersome. If you can afford it, you can save time (and ultimately money) if you buy an enterprise solution that is easier to manage “out of the box” and provides more effective, centralized management. Another option is to not manage a WAF in house at all but rather outsource the service to a team of experts who do this 24x7x365.
Your users will fall victim to phishing attacks, so deploy multifactor authentication (MFA) for all users and all applications. That way, when users are tricked into giving up their credentials, a remote attacker cannot log into your system without having the second authentication factor. Deploying MFA to all applications takes time, perhaps years, so prioritize applications that are externally accessible. Leveraging an MFA solution that integrates seamlessly with an identity federation solution can help streamline the deployment (assuming you have all your apps integrated with that solution) and will be less frustrating for your users. Identity federation solutions also reduce password fatigue and the massive problem we have now with the one-to-many relationship passwords have with applications. When the Yahoo and Sony compromised databases were compared (also in the breach trends report), 59% of the credentials were found to be the same.
For a more comprehensive list of recommendations, see the full F5 Labs’ Lessons Learned from a Decade of Data Breaches (/content/f5-labs/en/labs/articles/threat-intelligence/lessons-learned-from-a-decade-of-data-breaches-29035.html) report.


