Wherever there is Internet, there are businesses looking to take advantage of the twenty-first century gold rush: data collection. Cybercrime is no exception. Attackers focus on breaching applications to collect data on Internet users and then monetize that data in darknetAn encrypted network that runs on the Internet, enables users to remain anonymous, and requires special software to access it. Tor and Freenet are examples of darknets.markets. The dark webInternet content that exists on darknets and is not accessible via search engines. Special software is required to access it.economy is growing, and its users have a specific penchant for dealing in digital identities and credentials. Every year billions of credentials are spilled powering credential stuffing and stocking the shelves of darknet markets selling stolen data. Shape Security and F5 Labs are tracking credential spills for our 2021 Credential Stuffing Report (due out in January 2021). To date in 2020, a period plagued with the COVID-19 pandemic driving increased remote access and decreased visibility, we have tracked over 1.5 billion exposed credentials in breaches.
To protect the anonymity of users, darknet markets only transact in cryptocurrency. Research by Chainanalysis1 shows that bitcoin transactions grew from $250 million in 2012 to $872 million in 2018. They estimate bitcoin transactions for 2019 reached $1 billion. Some darknet markets have generated huge amounts of sales, for example Silk Road 2.0 generated more than $9.5 million in bitcoin prior to its shutdown in 2014.2 According to Juniper Research, it is estimated that all online fraud losses will reach $48 billion by 2023.3
With the growing sophistication of defense mechanisms, cyber attackers are interested in more than simple username and password pairs to various online sites and services. In late 2018, a new darknet marketplace, Genesis Store, emerged offering a unique product: the option to generate unique or random device fingerprints. Hackers can purchase stolen device fingerprints through the purchase of bots controlling infected machines on Genesis. Device fingerprints include information about a user’s account, including passwords and usernames, but also detailed identifiers such as browser cookies, IP addresses, user-agent strings, and other operating system details. Many anti-fraud solutions still consider device fingerprints to be a unique identifier, so mimicking this to bypass anti-fraud solutions is very attractive to attackers.
Genesis Marketplace at a Glance
The Genesis Marketplace, available both on the dark web and the public internet provides an avenue for attackers to buy digital fingerprints. As shown in Figure 1, the site features a wiki, a news page, a rolling ticker of how many bots are available for sale, and a ticketing system.

Figure 1. Genesis marketplace menu showing wiki, bots, and news
Wiki Pages for Help
The wiki, as shown in Figure 2, includes a how-to guide with animated gifs teaching people how to use the platform.
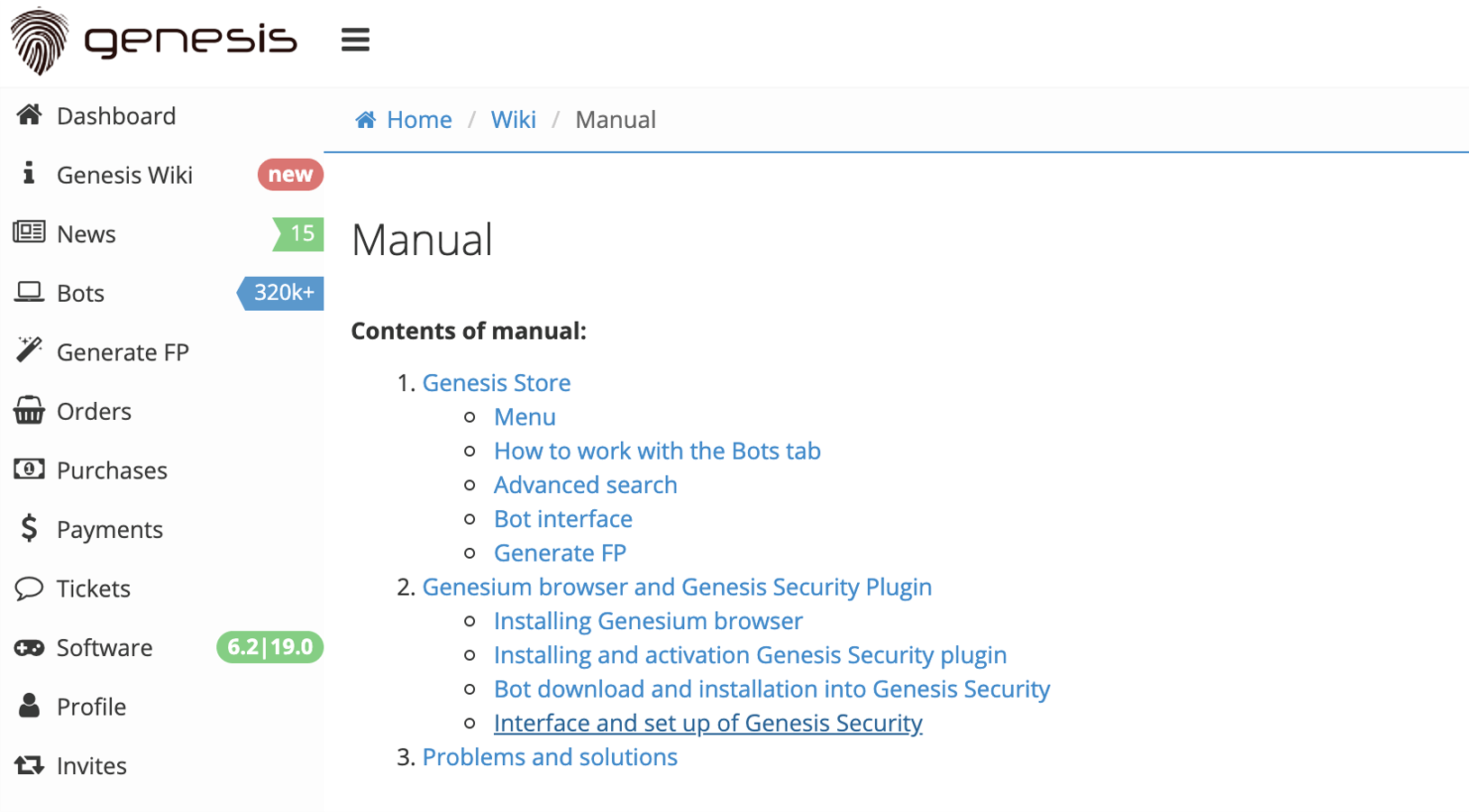
Figure 2. Genesis Marketplace Wiki has a Table of Contents
The Genesis Marketplace user experience is professional, much like what one would expect to see on any ecommerce site. The search feature, as shown in Figure 3, lets a user search for specific brands, credentials from a particular website, or specific data types like a credit card.
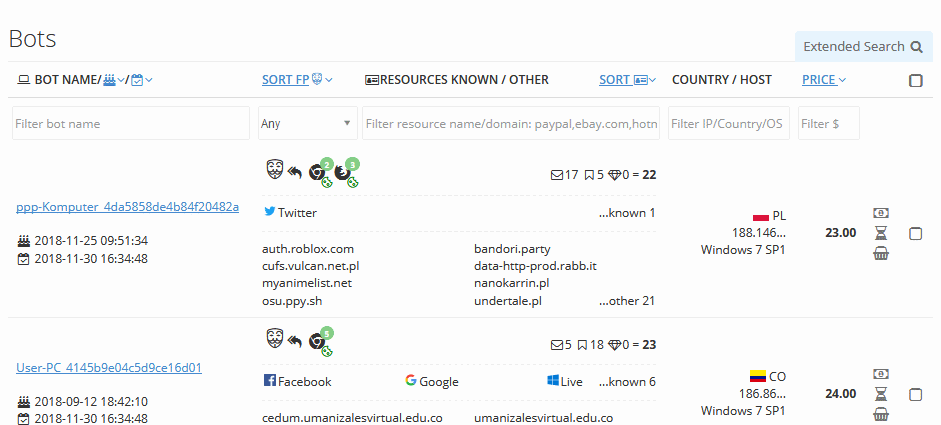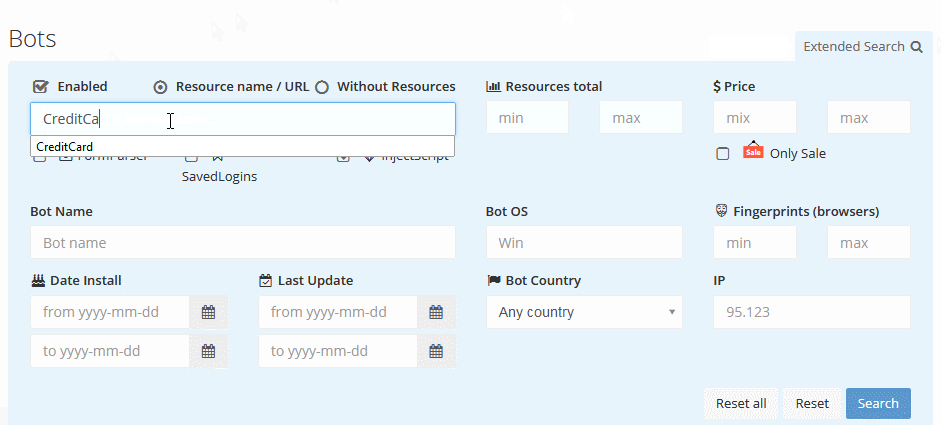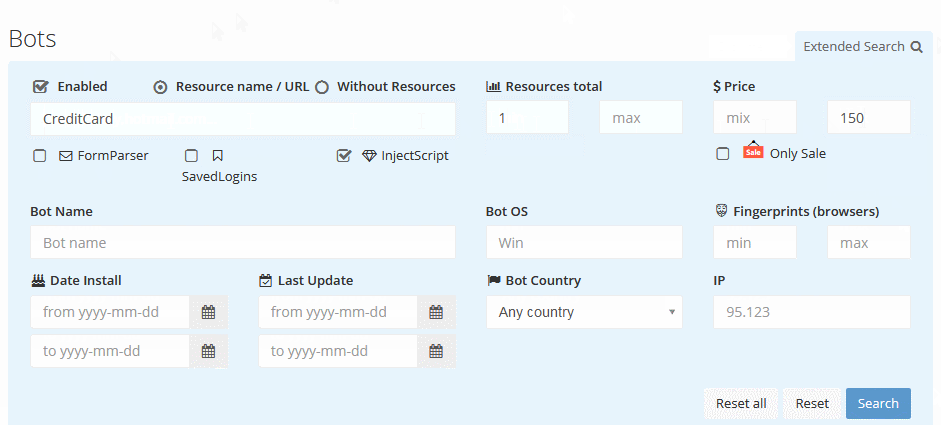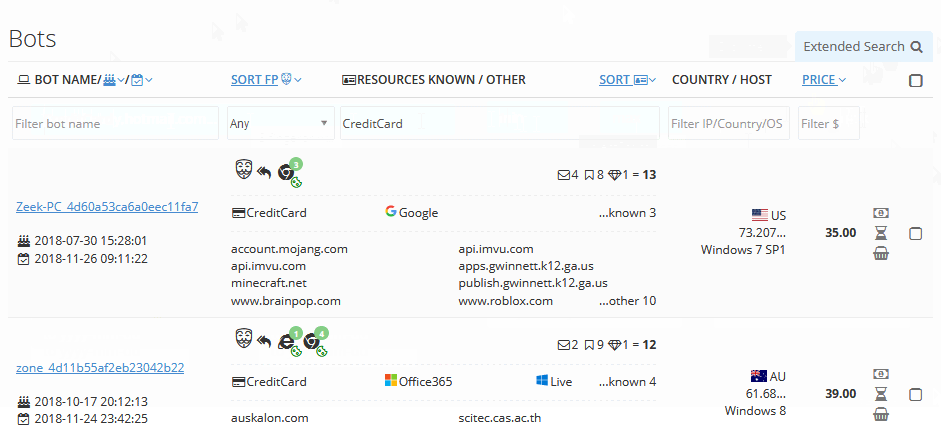
Figure 3. Genesis Marketplace brand search guide (Source: Genesis Help page)
News and Updates Section
The News section provides blog-like updates on new site features, shown in Figure 4.
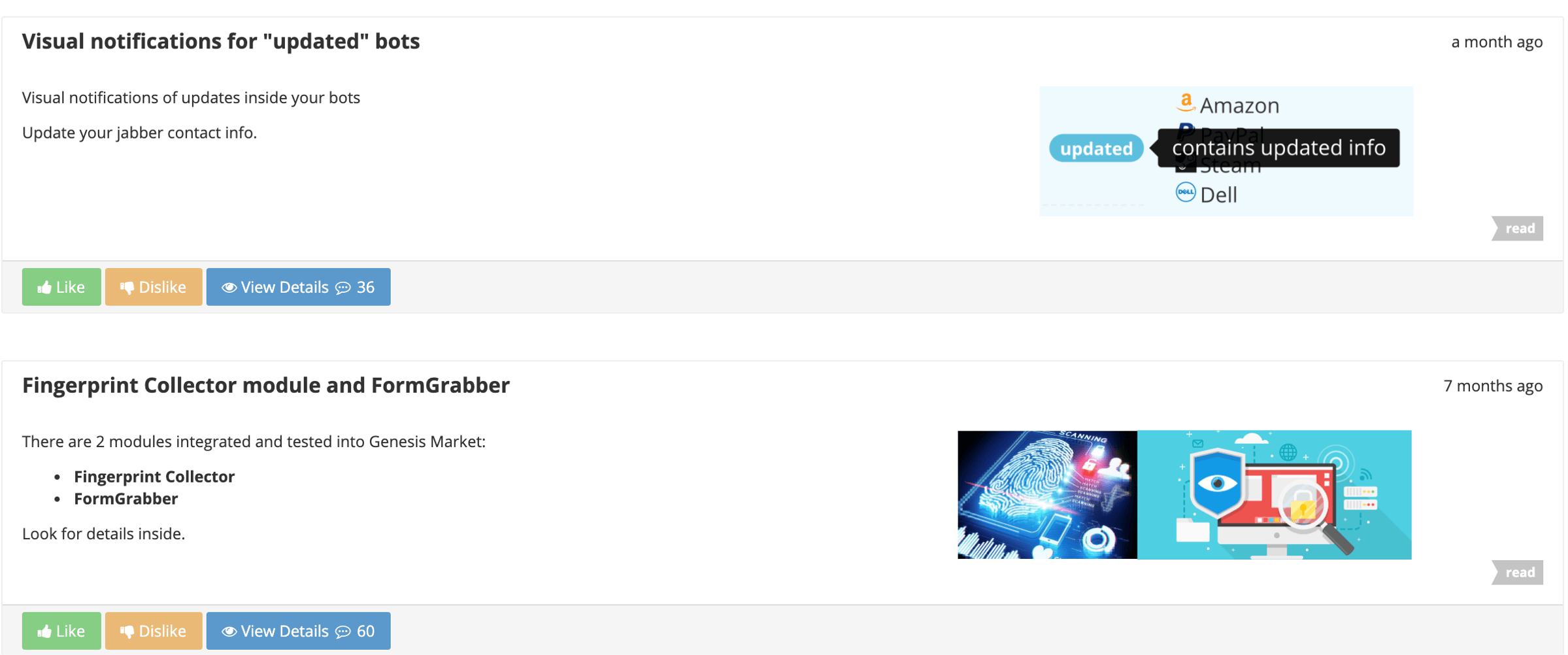
Figure 4. Genesis Marketplace new feature release section
The site also keeps customers that have purchased bots updated with the blue “Updated” tags, as shown in Figure 5. This feature acts as a real-time notifier to the illicit customer who purchased the bot. It highlights new data available in their purchased bots, such as new cookies by browser, new credit cards, or new accounts to specific websites.
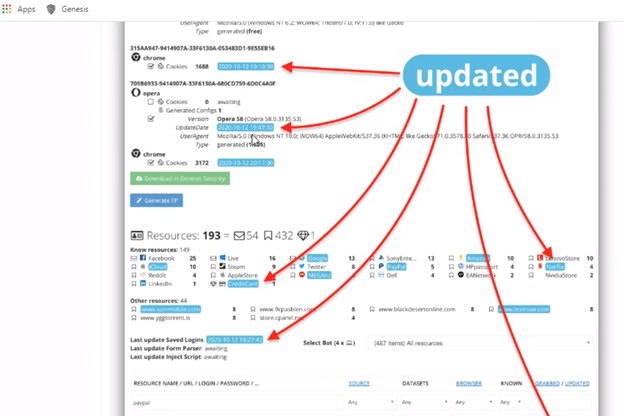
Figure 5. Genesis marketplace showing updates on purchased bots
Help Desk and Ticketing System
The Genesis Marketplace also has a full featured help desk with a ticketing system. The Tickets feature works like a normal tech support portal where the marketplace operators are prompt in their replies, and answers are provided in perfect English.
Bot Supply and Trade Economics
On October 20, 2020, the Genesis Digital Fingerprint Marketplace showed 323,000 bots available for sale, as depicted in Figure 6.
Figure 6. Bot count available on Genesis marketplace October of 2020: 323,000
Around October of 2019, there were 127,000 bots for sale, as shown in Figure 7. In just one year, the inventory of bots in Genesis has shown a 153% growth.
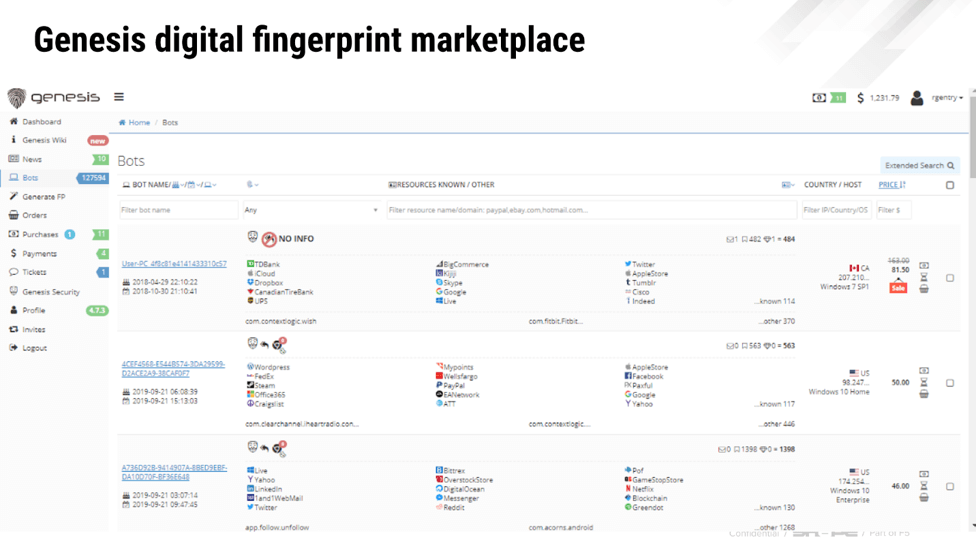
Figure 7. Bots available for sale Genesis marketplace around October of 2019: 127,000
Much like a legitimate ecommerce website, operations are automated, and inventory is updated frequently. Figure 8 is a screen capture was taken on October 20, 2020 at 1:15 UTC. The date and time in the screen capture are roughly 5 hours earlier at 19:58:52 UTC on October 19, 2020.

Figure 8: Genesis bot data updated in real time
Genesis Marketplace Prices Vary by Country and Associated Accounts
Bots are available on Genesis Marketplace for many countries in all regions of the world including United States, Canada, Singapore, France, United Kingdom, and Australia. Each bot has a multitude of accounts associated with a compromised host. Figure 9, captured on 16 October 2020, shows prices ranging from $0.70 (for a bot in Great Britain) to the most expensive at $176.00 (from Zambia).
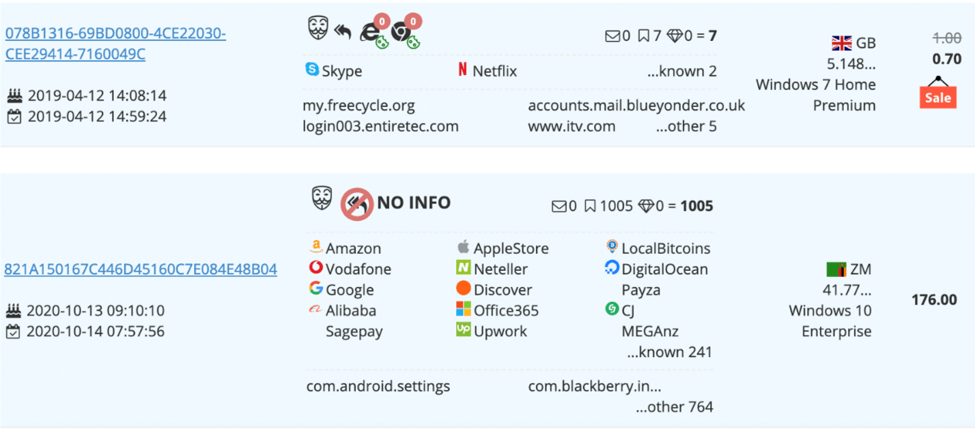
Figure 9: Genesis marketplace prices vary based on region and associated accounts
Genesis Marketplace Showcase for Premium Branded Accounts
Everything from cloud and hosting company accounts, to email platforms, social media, and financial institutions are available for sale in the Genesis Marketplace. The search functionality makes it easier for cybercriminals to target premium brands. They can purchase bots with accounts associated with their target and mimic a device that has been associated with prior transactions. Figure 10 shows a simple search for Amazon that yielded 52,000 results—nearly 16% of the 327,000 available bots.
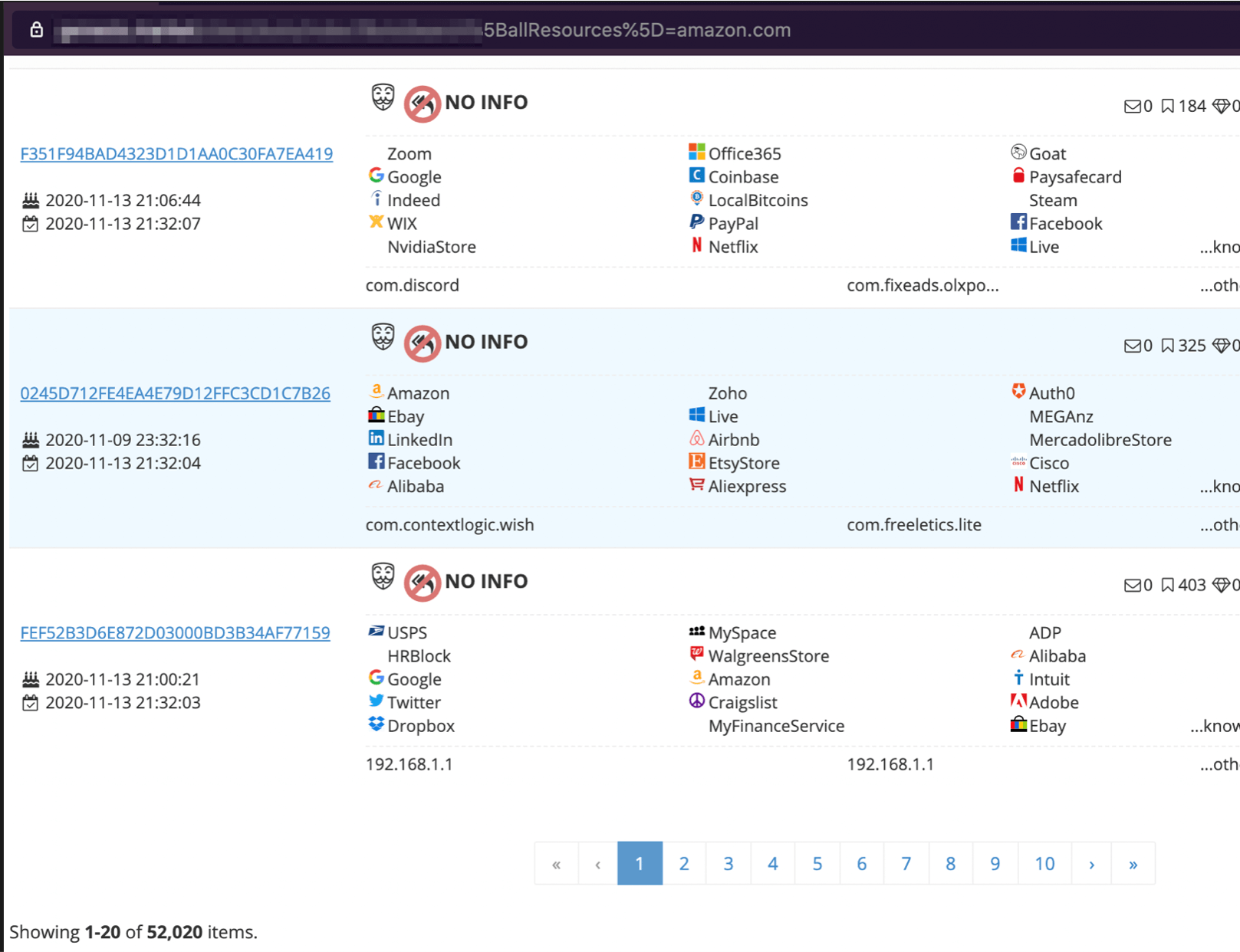
Figure 10: Genesis marketplace search for amazon.com yields 52K hits
Genesis Marketplace Provides Plugins for Easy Impersonation
Once a customer purchases a bot, Genesis Marketplace also makes it easy for them to use those stolen profiles. It offers a unique browser plugin (.crx file), downloadable from the website, which can install a stolen profile. Afterward, attackers merely need to access the eservice from the victim’s location. This can be done by using a proxy server or VPN service procured on the web, thereby bypassing simple anti-bot and anti-fraud defenses and appearing as a legitimate user.
Conclusion
With increased sophistication of anti-fraud systems, marketplaces like Genesis will see a boom. Genesis is currently a by-invitation marketplace, and the user experience on the platform is quite smooth. With a significant growth in the number of bots, as well as the range of accounts that a hackers can target, the popularity of Genesis is bound to grow. It is imperative for cyber defense teams to understand the looming threat of stolen fingerprints.
Recommended Security Controls
Illicit marketplaces like Genesis empower fraudsters to trick many security controls (https://www.f5.com/content/f5-labs-v2/en/archive-pages/education/what-are-security-controls). Therefore, a comprehensive and intelligent defense is required on both the user and enterprise fronts. Users need to understand threats to their digital identity (https://www.f5.com/content/f5-labs-v2/en/archive-pages/education/digital-identity-is-an-increasingly-popular-attack-vector-for-cybercriminals) and mechanisms to safeguard (https://www.f5.com/content/f5-labs-v2/en/archive-pages/education/how-to-guard-against-identity-theft-in-times-of-increasing-online-fraud) it. Enterprises need to have greater visibility to detect this evolving threat.
Recommendations
- Security Awareness Training. Organizations should frequently train employees on how to spot phishing attacks as phishing is the primary method of malware delivery. Attackers are quickly capitalizing on new trends, and users need to be extra vigilant watching for email, voicemails, and text messages that appear to be related to widely discussed topics in the media or popular culture
- Use anti-malware controls. All machines that surf the Internet (personal devices, company-issued laptops, mobile phones) should be have anti-malware software that is updated regularly. Watch for drive-by malware installed from risky adult and gaming sites as they are at high risk for contracting the malware that controls the systems in the bots Genesis sells.
- Inspect endpoints. Collect environmental and behavioral signals throughout the users’ journey and utilize artificial intelligence to identify malicious intent both from humans and bots
- Detect malicious intent. Integrate with solutions that monitor the tools, tactics, and procedures used by Genesis and can detect the usage of Genesis plugins and the stollen digital fingerprints.
- Augment authentication with intelligence. Integrate threat intelligence on stolen credentials to the authentication process and reject usage of compromised credentials.


