Introduction
What Is a DNS Amplification Attack?
A Domain Name System (DNS) amplification attack is just one of many types of distributed denial-of-service (DDoS) attacks. As with all DDoS attacks, the goal of attackers is to keep users from accessing a networked system, service, website, application, or other resource by making it slow to respond or disabling it entirely.1 Most DDoS attacks are volumetric in that they bombard a victim’s network with more traffic than it can handle. Think of it like bumper-to-bumper, stand-still traffic on a six-lane freeway near a stadium when a concert or sporting event ends. Thousands of cars crowding the freeway all at once completely impair the normal flow of traffic.
A DNS amplification attack uses different techniques to accomplish the same end goal of denying service. Instead of thousands of cars flooding the freeway at one time, imagine six wide-load trucks traveling side by side along that same six-lane freeway. The flow of traffic is completely impaired—not by a sudden onslaught of thousands of cars but by several vehicles so large that normal traffic can’t flow through. So, while most DDoS attacks work by overwhelming a system with a huge quantity of average-sized packets, a DNS amplification attack uses larger packets to achieve the same result. No analogy is perfect, however, and there are a few more wrinkles to the DNS amplification story, so let’s look more closely at the details of this attack.
How Does a DNS Amplification Attack Work?
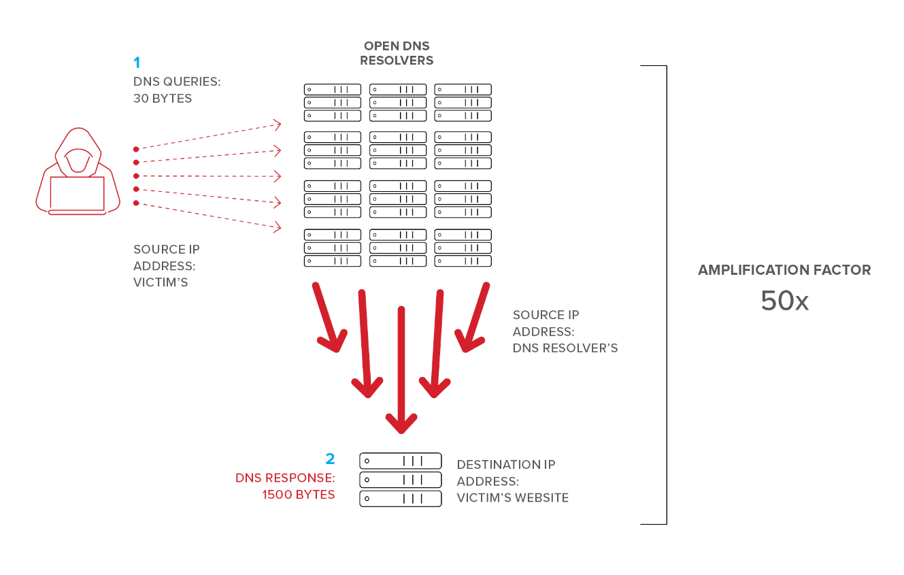
In a DNS amplification attack, malicious actors take advantage of the normal operation of the Domain Name System (DNS)—the “address book” of the Internet—using it as a weapon against a targeted victim’s website. The goal is to flood the website with fake DNS lookup requests that consume network bandwidth to the point that the site fails.
To understand how the attack works, let’s revisit at a high level how DNS works. When a user types www.example.com into their browser, DNS is the Internet service that accepts that request, finds the IP address assigned to that domain name, and sends it back to the browser so the client can connect to that website.
There’s a specific process for finding that address, beginning with the user’s device checking its local cache; if not found, then querying the assigned Internet Service Provider’s (ISP’s) DNS servers (resolvers); if not found, then proceeding through a hierarchy of DNS resolvers across the Internet until the IP address is found. Internally, a corporate network typically only resolves DNS requests for its own employees, but the Internet is full of “open,” publicly accessible DNS resolvers that will resolve DNS requests for anyone—including attackers. Using these open resolvers, attackers can send many fake requests without raising any red flags.
So, what’s next for attackers? Amplification. Remember, their goal is to turn relatively small DNS requests into huge responses. A typical DNS request (just a few lines of text) is very small—usually in the tens of bytes—and returns a response that’s only slightly larger. As shown in Figure 1, a genuine (non-malicious) DNS response might have an amplification factor of 1.5 or less.
To achieve their goal, attackers craft DNS requests in a way that substantially amplifies the size of the response. One way to do this is by requesting not just the IP address for a site like www.example.com, but information about the entire domain (for example, using DNS requests for the record type “ANY”), so the response might include details about subdomains, backup servers, mail servers, aliases, and more. Suddenly, a 10-byte DNS request could generate a response that’s 10, 20, even 50 times larger.

The Role of UDP in DNS Amplification Attacks
But, what’s still wrong with this picture? The DNS responses are being sent back to the attacker, not to the intended victim. This is where the User Datagram Protocol (UDP) lends attackers a helping hand.1
If you think about the trillions of DNS requests that are made every day across the Internet, DNS exchanges need to happen at lightning-fast speed. DNS relies on UDP for this. It’s fast because its primary job is to relay messages back and forth between sources and destinations; it doesn’t do other tasks like guaranteeing delivery or validating data. It’s also fast because it’s a connectionless protocol, meaning it doesn’t keep track of “conversations,” so it has no way of knowing if the source IP address in a request is valid.
So, in their DNS requests, attackers forge (spoof) the source IP address to that of the victim’s. This strategy both hides the attacker’s identity and ensures that all responses from the DNS resolver will be sent to the victim’s system instead of the attacker's. In this way, the DNS resolvers are acting as reflectors, “returning” responses to a victim that never requested anything.
To use a different analogy, think about someone pranking a victim by posting a fake help wanted ad on multiple websites and listing the intended victim’s email address in the contact information. If the ad service doesn’t verify the requester’s information, the victim, who never placed the ad, will soon be inundated with unwanted email responses. An “amplified” version would ask interested parties not just to respond but to attach résumés, photos, job and character references, high school and college transcripts, background check information, and so on. The “response” emails would be enormous.