The digital world is marred by various kinds of fraud, including account takeovers, malware-initiated transactions, and exploitation of loopholes in legitimate transactions. Identity is the first line of defense against fraud, and it faces the full brunt of the assault with attempts like new account fraud, synthetic identity fraud, and account takeover fraud. F5 Labs has tracked various identity-related attacks and malware campaigns and found that the effectiveness of hacker tricks changes over time. This article takes a step back from analyzing hacker techniques and looks for answers to two key questions:
- What is fueling the growth in fraudulent transactions?
- Why, even with sophisticated security tools, do these attacks succeed?
Fraud’s Low Entry Barrier and High Payback
In the digital era, the thought of not being “connected” is unfathomable. To maintain continued online access, everyone uses credentials. Fraudsters are on the lookout for these credentials to help them circumvent security controls and commit fraud. They succeed by capitalizing on:
- The plethora of available breached credentials. The 2021 Credential Stuffing Report by F5 Labs and Shape Security exposed a profound lack of awareness about the threat of credential spills. Tracking the use of 900 million credentials spilled in Collection X across two banks, a retailer, and a food and beverage provider revealed that legitimate users continued to use 610 million of the compromised credentials. Fraudsters can easily acquire these credential sets and take over genuine accounts.
- Breached personally identifiable information (PII). Fraudsters quite frequently need to create look-alike accounts or synthetic identities or reset credentials for a genuine account. To facilitate these activities, they need access to genuine user data. Figure 1 shows how PII data for more than 300,000 customers of a hardware wallet shop was available for purchase through a dark web auction with a starting price of 2 Bitcoins.5
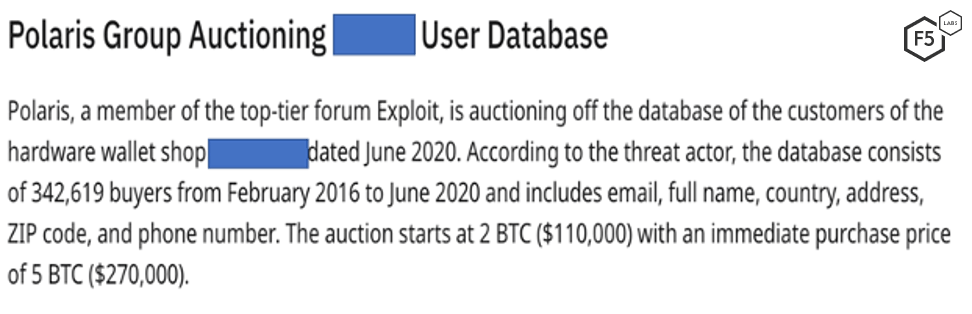
Figure 1. Reddit screen capture for an auction advertising a customer database on the dark web.
- Malware-infected machines. With the advancement in protection mechanisms like antiviruses, sandboxes and browser security, the use of infected machines to commit fraud seems to have slowed. A 2021 Kaspersky report shows that only 4 percent of fraudulent transactions in the financial sector were from malware-infected devices.1 However, this vector cannot be completely discounted, as malware researchers routinely find new and innovative ways of coding to avoid detection and mitigation, as shown in Figure 2.
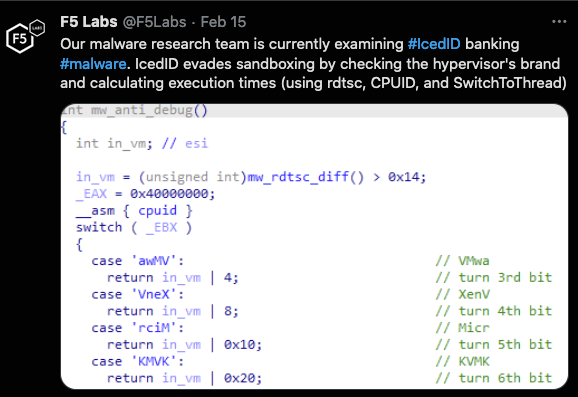
Figure 2. One innovative way of coding is this IcedID malware that includes evasion techniques for detecting sandboxes.
The above points, combined with factors like growth in web and mobile transactions, a steady pool of people who are willing to be money mules, and affordable availability of knowledge on tactics to commit fraud, are propelling the growth of players involved in fraudulent activities.2
Even Strong Defenses May Contain Weaknesses
One could argue that fraudsters’ tactics are not novel and that investing in specialized products with machine learning and artificial intelligence should solve the issue of fraud. But somehow fraudsters still manage to outsmart security defenses. In a recent discussion that F5 Labs had with the head of the fraud risk and compliance team at a major bank, a question was posed: Is your product capable of blocking the malicious transactions by itself?
On the surface, this seems like a normal question that any security-minded professional would ask, but the question definitely had a deeper meaning for organization fraud and compliance teams. As fraud is a complicated issue that cuts across various groups in an organization, including governance risk and compliance (GRC), network, security, and application teams. By the time the teams reach a consensus, fraudsters have met their objectives and have moved on to a different tactic or target.
Building on this understanding of organizational silos, the potential for gaming an ecommerce business’s security controls would look like the following:
- Run credential-stuffing campaign using leaked data from credential spills.
- Take over accounts and check for stored payment information and, if needed, add a stolen credit card for payment.
- Purchase expensive luxury items.
The fraudster wins the goods; the retailer loses in the form of inventory, chargebacks, and customer trust. Nike was hit with similar fraud.3
In this potential method, the fraudster would cross paths with the information security team and the fraud and risk team and would capitalize on the gap between the two organizational functions:
- The information security team would battle the fraudster’s bot by attempting to block credential-stuffing attacks and has valuable information on accounts being tested, the origin of the request etc.
- The fraud and risk team would get involved after a customer lodges a complaint, when the retailer is hit with a chargeback, or when monitoring system alerts.
By narrowing the barriers between these teams, the fraud and risk team could monitor the accounts and other identifiers flagged by the information security team. This would greatly reduce the likelihood of the fraudster’s success.
Building an Effective Antifraud Platform
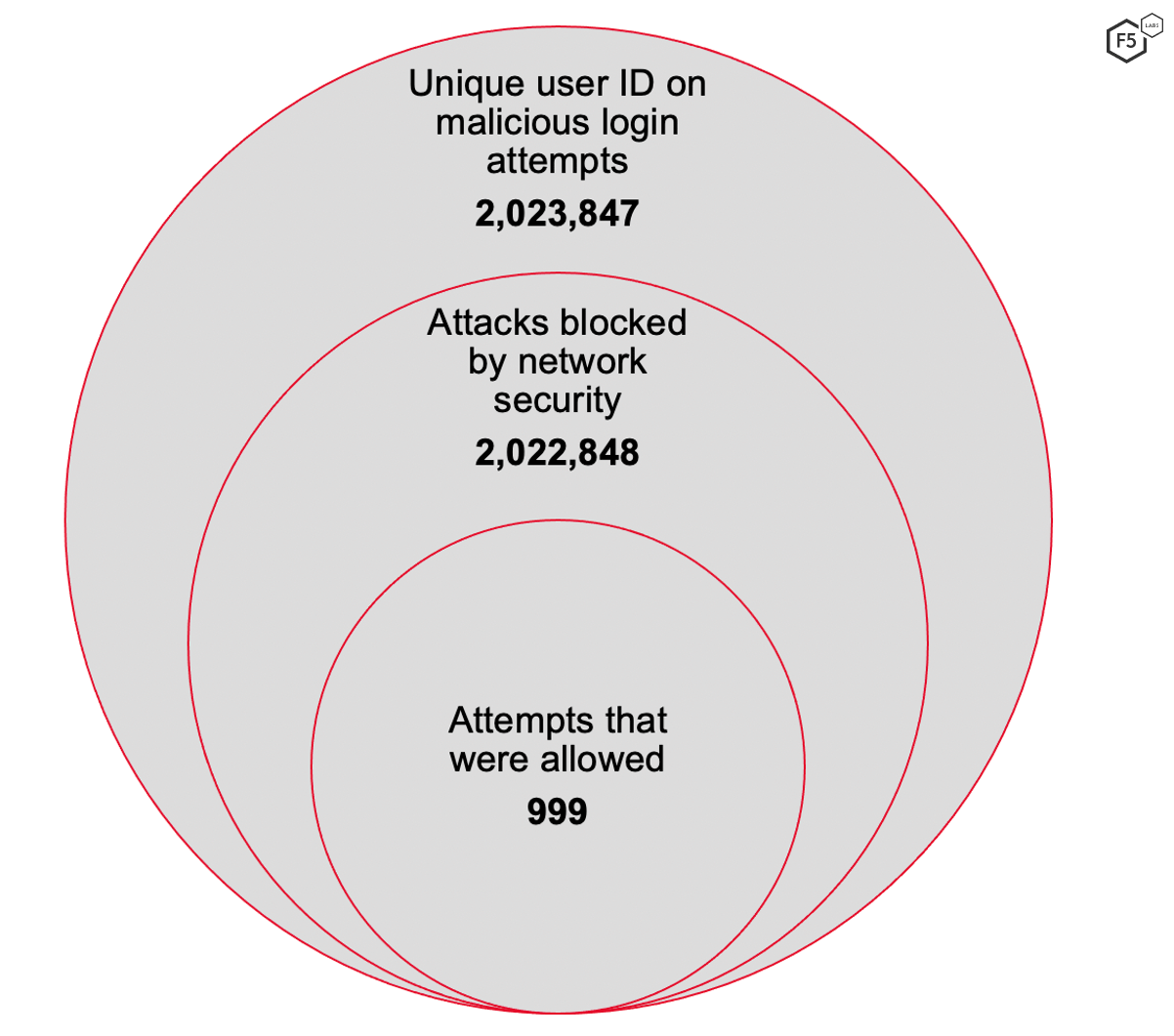
Figure 3. Analysis of threat traffic on a login page.
This challenge of organizational silos hampering the fraud prevention team’s effectiveness has not gone unnoticed. A survey of financial fraud professionals shows organizations are beginning to combine information security and fraud systems.4 Today’s tools need to wield the power of machine learning and artificial intelligence, but the insights on threat collected by one team must not be restricted within organizational silos. Instead, a collaborative platform should bring information security professionals along with the fraud and GRC teams. The intelligence-sharing platform can help isolate anomalies and mitigate attacks.
Analysis of a year of threat data from a large food and beverage organization revealed that network security controls for defending against bots on the login page were 99.95 percent effective, as shown in Figure 3.
For the same time frame, an analysis of all attempted fraud yielded 1,681 malicious user sessions. Cross-referencing the session owners with the 999 (.05%) user identities that the network security allowed resulted in an overlap of 1,232 sessions, as shown in Figure 4. This illustrates that cybercriminals are capitalizing on the gaps between the fraud and network teams’ solutions.
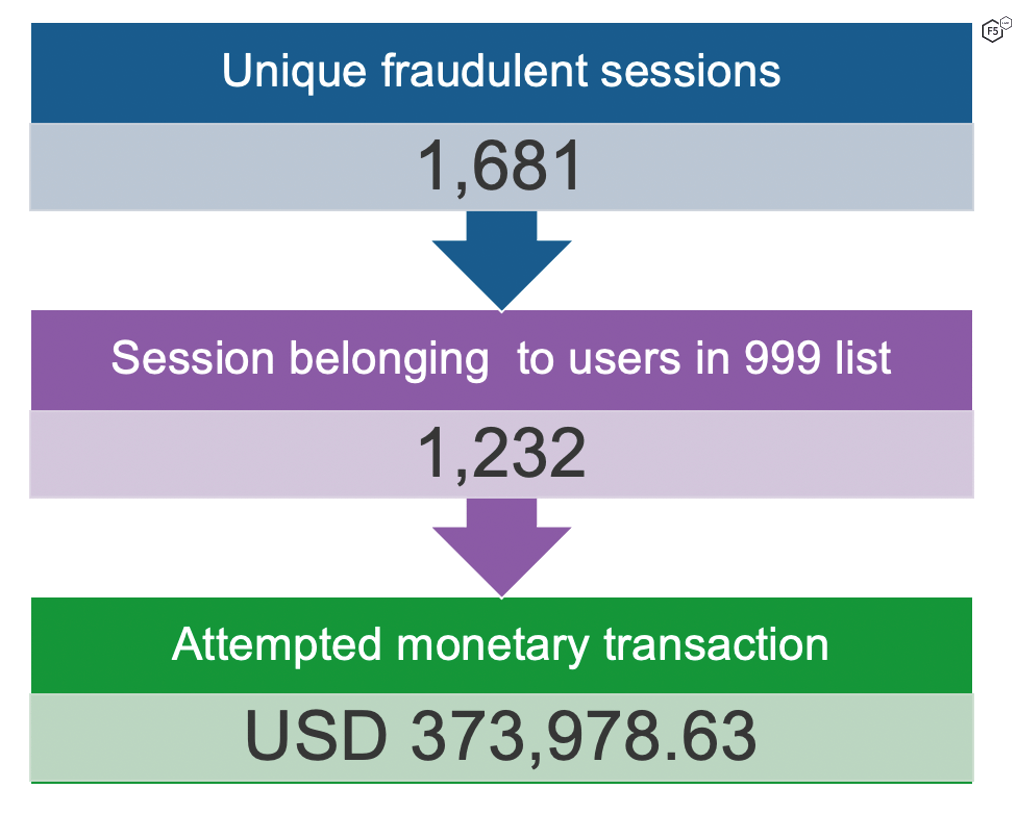
Figure 4. Cross-referencing fraudulent session with threat attempts on a login page.
The analysis also signifies that a collaborative approach would boost the effectiveness of fighting fraud. This collaboration can be built using a platform approach in which all security teams, including network, application, identity, and fraud, can share intelligence, improve visibility and coordinate mitigations. A common data dictionary would help teams evaluate the threats analyzed and reduce the response time.
It is important to understand that hackers don’t play by organizational rules. Their single motive is to monetize fraud, and unless fixed, these organizational gaps present a lucrative target.
Recommendations
- Build a platform that can converge network, application, identity, and fraud security intelligence and improve threat response time.
- Build a common data dictionary across teams to ensure consistent analysis.


