Winter 2020 Update: the 2019 Application Protection Report was written over the course of 2019 and based on data from the 2018 calendar year. At the end of 2019, in preparation for continuing our research in 2020, we collected and examined public breach notifications from 2019. These new data validated our findings from the previous year, and in some cases indicated that trends we identified are accelerating. While we will unpack all of the signs in our forthcoming 2020 research series, we have included our latest findings, particularly with respect to data breaches, in a 2nd Edition of the 2019 APR Executive Summary. We hope this fresh intel is useful to you while we read the signs and work on the 2020 report!

This is the 2019 Application Protection Research Series in its most distilled form. We’ve taken the information and conclusions contained in the episodes, boiled them down to their essences, and tied them together to form a single, brief overview of the 2018 application threat landscape. One of the goals of the Application Protection Research Series is to place all threats and trends within the same big picture and over the same timeframe, to help practitioners incorporate new information into their current work. This perspective has the added advantage of allowing us to see links between trends that might seem disparate on the surface, like the popularity of PHP injection and the growth of APIs, and to begin to address the underlying phenomena driving those trends.
Viewed in this way, our research illuminates some interesting aspects of the current state of security. In 2018, to the extent that new attack techniques and approaches emerged, it was largely in response to changes in how organizations design, create, and manage applications. The context that makes old attack techniques like injection and phishing newly relevant is the pattern of decentralization and disintegration that applications have been experiencing over the last few years. While this trend offers business advantages for organizations, it also transfers known risks into relatively less well-known or well-understood forms that the industry will take time to process.
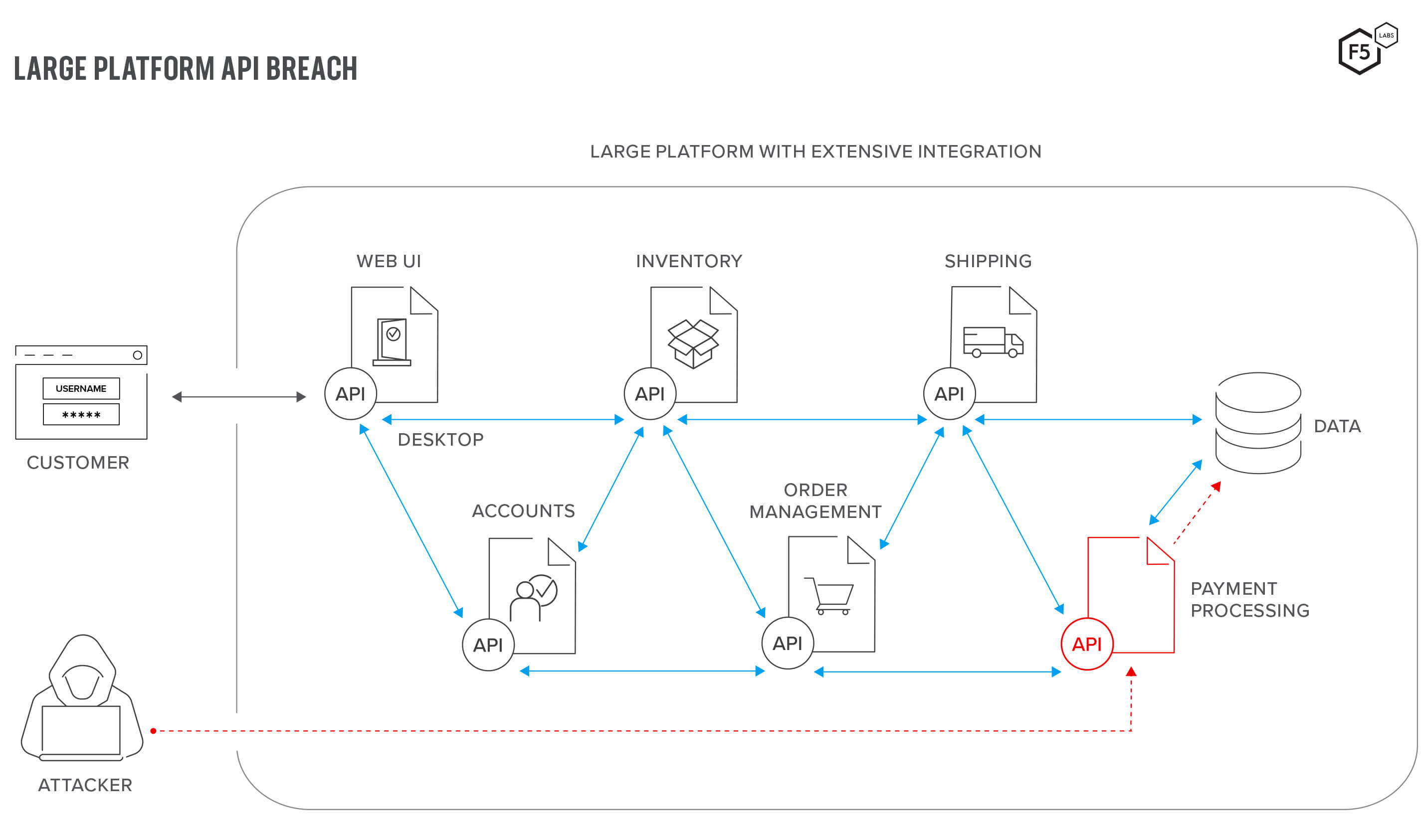
In other words, attackers have not needed to come up with new tricks. They were able to wait until application owners changed things, usually in the direction of greater complexity and abstraction, and then exploit the resulting visibility challenges using slightly modified versions of attacks that are already well-known and understood. This is why formjacking, API hacking and phishing have the prevalence that they do today.
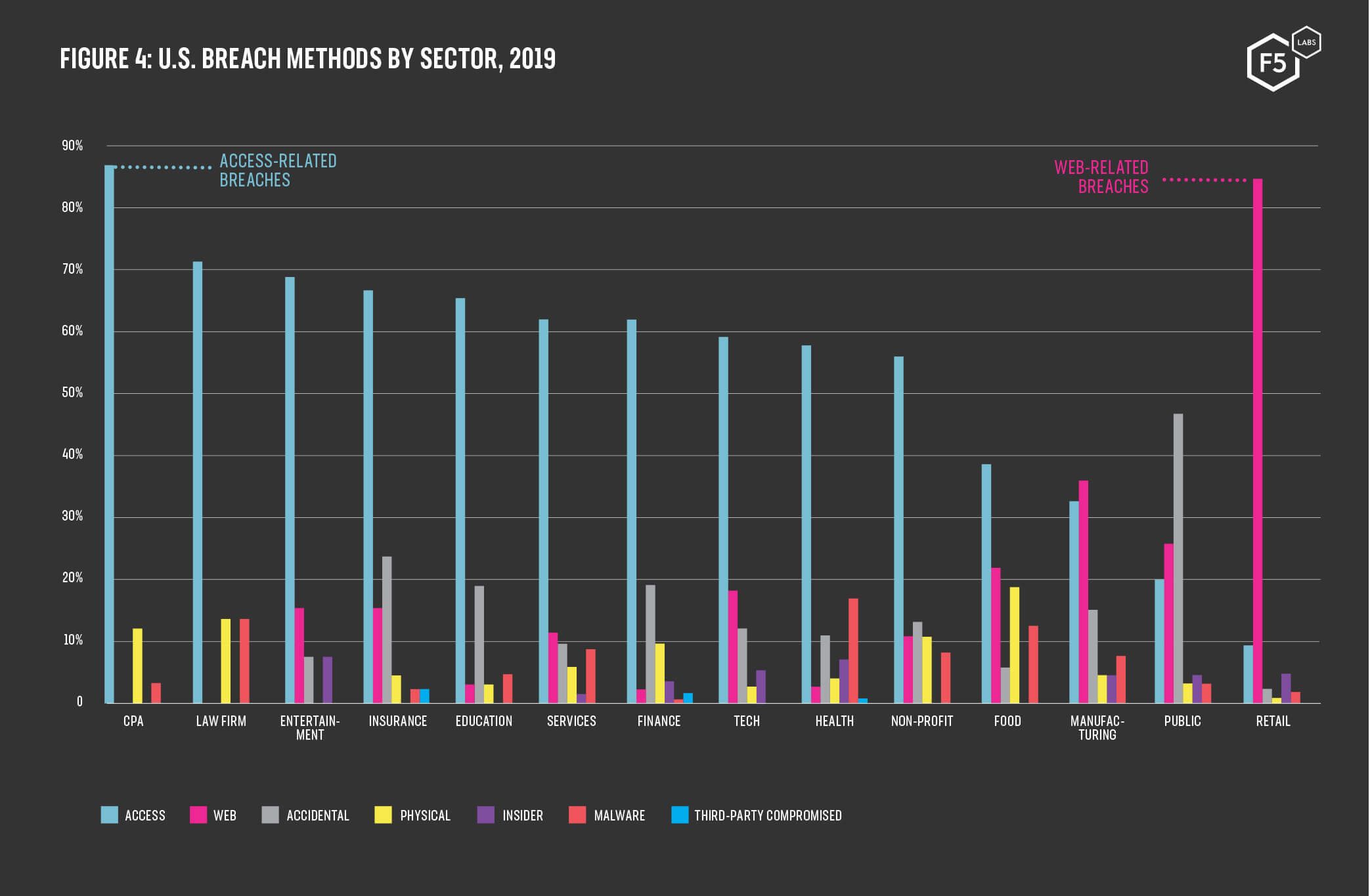
We also were able to draw correlations between an organization’s industry and the mode in which it is most likely to be successfully breached. This kind of analysis helps us move past anecdotes and marketing claims, and continue to build maturity in risk-based security programs. As applications are designed around new architectures and consumption models, the need for risk-based controls that deal with how a particular application actually works, as opposed to how someone thinks all applications work (or should work), will only become more important. We offer this threat intelligence in the hopes that it will assist local defenders in the particularities of their particular tasks.


