
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
Introduction
Welcome to this month's installment of the Sensor Intel Series, our monthly summary of vulnerability intelligence based on distributed passive sensor data, looking at data from December of 2024.
Top 10 Scanned Review
CVE-2023-1389, an RCE vulnerability in TP-Link Archer AX21 consumer routers, which has been consistently towards the top of our ranking, continues for a fifth month to be the most scanned for CVE that we track. This is especially interesting as TP-Link devices are under scrutiny by the US Government, which we’ll talk about more in a second.
CVE-2022-24847, a remote code execution vulnerability in the GeoServer software comes in second this month, unsurprisingly as this one has been showing up in the top 4 for the last 12 months (the window of our analysis), and for much longer in 2023 as well.
CVE-2022-22947, a Spring Cloud Gateway code injection vulnerability, which has also appeared consistently in our top 10 for at least 12 months is in third place.
CVE-2020-11625, in fourth place this month, is not an RCE or command injection, but rather a vulnerability in a webcam manufactured by AvertX, which allows an attacker to determine valid usernames for the device. It’s CVSS v3 score is a mere 5.3, which points out that sometimes attackers are just trying to find devices to use, not devices to run code on.
CVE-2022-42475 is a heap buffer overflow in FortiOS and FortiProxy SSL-VPN products. It too has been consistent in our results for at least 12 months.
The rest are similar in that we have seen them many times and for many months, except for one CVE which we recently started tracking – CVE-2024-12856, an authenticated command injection vulnerability in Four-Faith consumer router models. Given that the affected firmware version also has default credentials, this essentially turns this vulnerability into a remote and unauthenticated command injection vulnerability. The NVD publish date is 12/27/2024, and we first saw this vulnerability show up on November 8th. 2024. which implies that this vulnerability was known before the CVE was published.
TP Link and the US Government
We thought we should briefly mention that CVE-2023-1389, our top scanned for CVE for the last five months, which first appears in our logs in July of 2022, and which has been in our top 10 since January of 2024, is a vulnerability in a TP-Link home router. TP-Link has recently attracted the attention of the US government, which is considering taking action to prohibit the sale of TP-Link devices in the United States of America. However, the possible action doesn’t seem related to this vulnerability, per se, but seems to be more around the widespread use of these routers in the USA and the ties of the company to China, and concerns about espionage or nation-state hacking activity.
BotPoke and Top Talkers
We’ve continued to track a pattern of scanning associated with the BotPoke scanner that first appeared in August. We also noted that in October, the IP address associated with the scanning had changed, from one in Lithuania to one from Hong Kong, and in November that it had switched to one based out of the Netherlands.
This month, the Netherlands address continued to be used, and once again this IP address is our top talker, with 9% of our total traffic originating from this single IP.
The next two most active source IPs were, as last month, part of a cluster of IPs that are scanning for similar URIs, mostly related to PHP and credential related information exposures.
December Vulnerabilities by the Numbers
Figure 1 shows December traffic for the top ten CVEs that we track. CVE-2023-1389 is dominating this visualization, with much more traffic than any of the other top 10. The massive amount of scanning for this vulnerability throws off the proportionality of this view, however. See further down for an easier to understand view using a logarithmic scale in Figure 3.
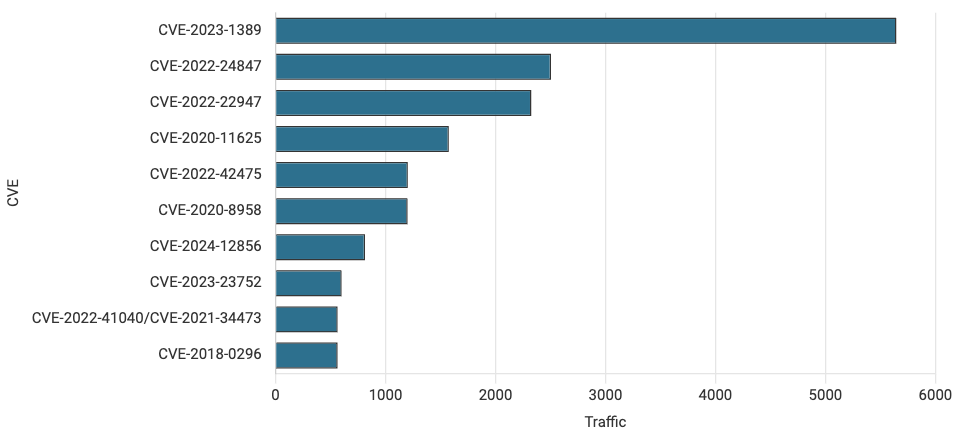
Figure 1. Top ten vulnerabilities by traffic volume in December 2024. CVE-2023-1389 continues to dominate all other CVEs we track in terms of volume for now five months in a row.
Targeting Trends
Figure 2 is a bump plot showing the change in traffic volume and position over the last twelve months. We can see quite clearly the still heavy scanning for CVE-2023-1389, albeit slowly decreasing. We can also observe a falloff in scanning for CVE-2020-8958, after last month’s increase.
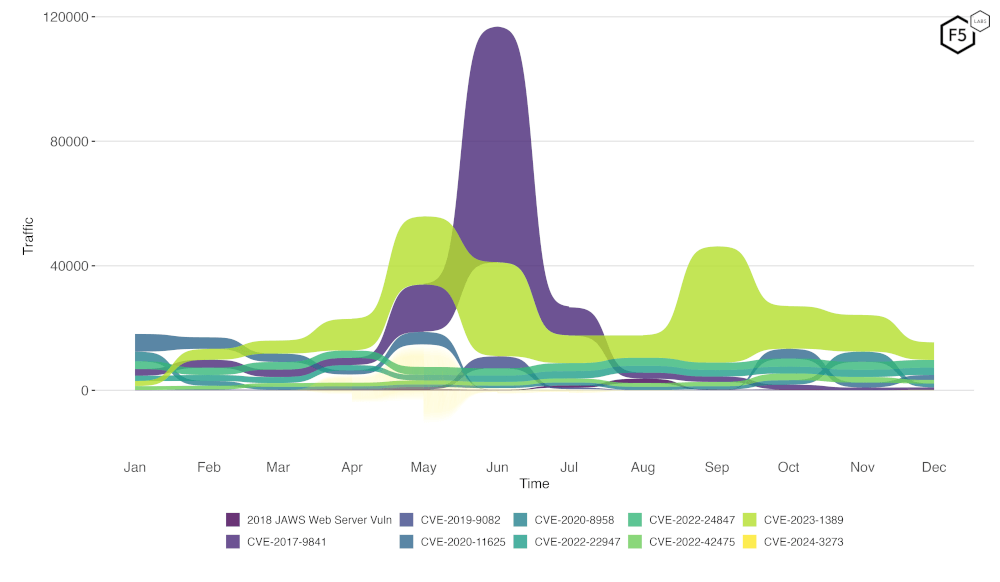
Figure 2, Evolution of vulnerability targeting in the last twelve months. Note the continued high level of scanning for CVE-2023-1389, and the decrease in scanning for CVE-2020-8958.
Long Term Trends
Figure 3 shows traffic for the top 20 CVEs by all-time traffic, followed by a monthly average of the remaining CVEs.
The sudden re-emergence of scanning for CVE-2020-11625 continues, at the right of the top row. On the leftmost cell of the second row, we can see the drop in scanning for CVE-2020-8958 after it’s sudden increase last month. CVE-2018-10561, which we noted had increased approximately ten-fold in the last 12 months has returned to previously observed levels.
Specifically of note is CVE-2023-23752, an unauthorized access bug in Joomla! 4.0.0 to 4.2.7 has exploded from last month going from single digits to nearly 1000 events. Looking into that a little we note that traffic identified as trying to exploit this vulnerability is coming from about 20 IPs, but mainly from just one – ‘66.63.187.168’, an IP currently owned by “Quadranet Enterprises, LLC”, a hosting provider based out of the USA.
In the lower left corner, you can see the average of all the other 138 CVEs we currently track and note that these show a similar level of scanning since last month.
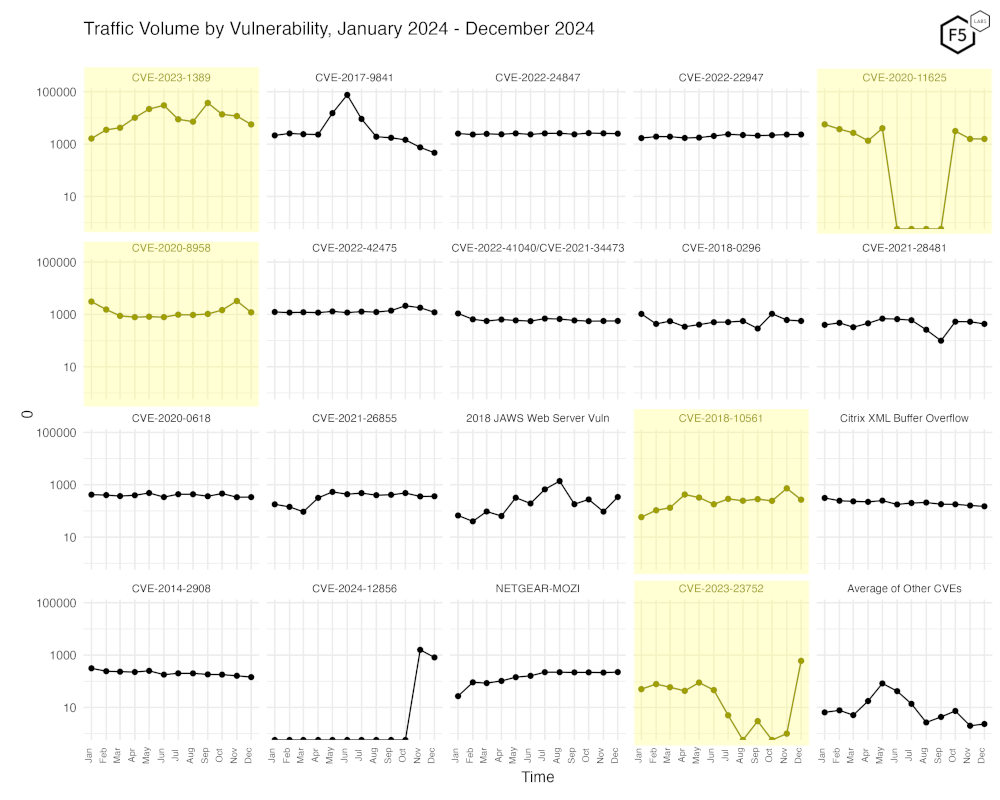
Figure 3. Traffic volume by vulnerability. This view accentuates the recent changes in CVE-2020-11625, CVE-2020-8958, CVE-2018-10561, and CVE-2023-23752.
Conclusions
We promised you an end of year roundup last month, and that will be coming out as a separate article in a little while. But after that, see you next month, where we’ll look at the first data we’ve seen in 2025!
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


