Credential stuffing is a type of cyberattack that uses credentials obtained from previous breaches to take over existing accounts on other web or mobile applications. This is a type of brute force attack that relies on the fact that many people use the same usernames and passwords on multiple sites. For a more in-depth description of credential stuffing and its impacts, refer to our piece on how credential stuffing works (/content/f5-labs-v2/en/archive-pages/education/what-is-credential-stuffing-.html). This article looks deeper into the anatomy of a credential stuffing attack and examines the tools of the trade.
Credential stuffing attacks include the following key steps:
An attacker obtains leaked credentials (i.e., a username and password pair) from prior cyberattacks.
The attacker uses a software tool to automate the testing of stuffing these credentials against various websites and mobile applications.
If a credential set is successfully authenticated, then it is flagged as a valid account.
The attacker can now take over the account and extract any value, including personally identifiable information, credit card information, and stored value (such as loyalty points), as well as access email, make fraudulent purchases, and resell the account.
Only a small percentage of the credentials tested are valid, typically between 0.1 and 2 percent. Because of the enormous number of credentials tested (typically in the hundreds of thousands to millions), this becomes a significant problem for the website owner.
This article focuses on step 2 of this process: how the attacker configures and tests their software tools to “stuff” the credentials. The second part of this article will go into step 4, launching the attack and overcoming the victim’s defenses.
Obtaining Credentials for Stuffing
One only has to search for “combolist for sale” on the public Internet to uncover the ecosystem built on buying and selling breached credentials. Beneath the surface, on the dark web, is a thriving market as well, including combolists-as-a-service, where bad actors use a subscription model to continuously provide freshly stolen credentials.
The price of credentials varies from free to tens of dollars, based on freshness, seller reputation, and competitive pressure. The F5 Labs 2021 Credential Stuffing Report goes into detail on the causes and magnitude of these spilled credentials.
Credential Stuffing Attack Tools
Several tools are available to orchestrate the credential stuffing once the attacker obtains the combolists, proxies, and potentially the CAPTCHA solving service. One such tool is OpenBullet, which is open source and easily available for download on the Internet. Attackers can use OpenBullet to create attack scripts, or they can purchase prebuilt scripts on the dark web. The following subsections describe how to create a basic attack script using OpenBullet’s intuitive visual editor.
Loading the Combolist
In this step, we browse to the list of credentials, or combolist, we will use in the attack. A combolist is simply a list of usernames and passwords separated by a character, such as a colon. For example:
- Testuser1:testpasseword1
- Testuser2:testpasseword2
- Testuser3:testpasseword3
Figure 1 shows how shows how to load the credential pair combolist into the OpenBullet configuration.
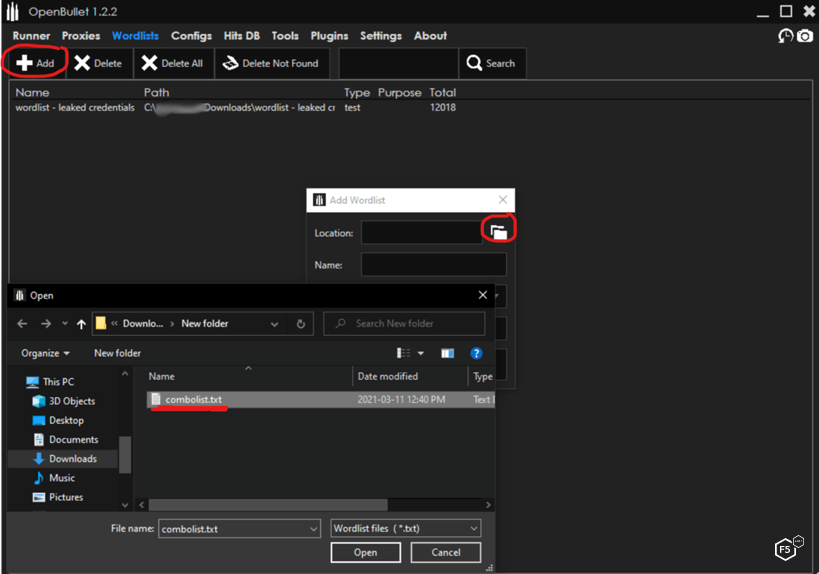
Figure 1. OpenBullet credential stuffing tool loading credential combolists.
Adding Proxies for Credential Stuffing
Attackers use proxies to distribute their login requests across multiple IP addresses, making it impossible to trace their source IP address or to selectively block them based on IP address. They also use proxies to select which countries and autonomous system numbers (ASNs) they appear to be coming from. Proxy service providers can supply proxies based on ASN type—data center, residential, or mobile—allowing the attacker to blend in with the expected traffic. Proxies are available starting from free to pay-as-you-go, or monthly or yearly subscriptions.
Now we add and test the proxies we will use to distribute the attack, as shown in Figure 2. This is just a matter of importing the proxy list obtained and having the tool check them against any website. All nonworking proxies can be deleted with the click of a button.
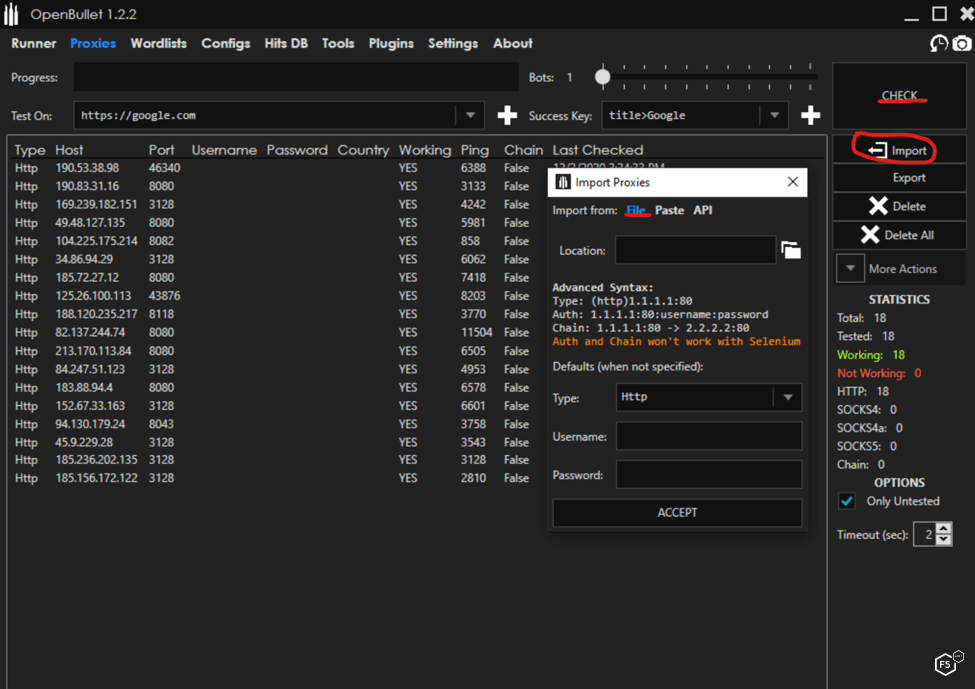
Figure 2. OpenBullet credential stuffing tool loading proxies.
Building a Credential Stuffing Attack Configuration
Building an attack configuration in OpenBullet consists of adding blocks to create a stack, which is a chain of blocks executed in order. For illustration, we will build a basic configuration. In Figure 3, we add a Request block, which will send a GET request for the login page. We can add in custom cookies and custom headers as needed.
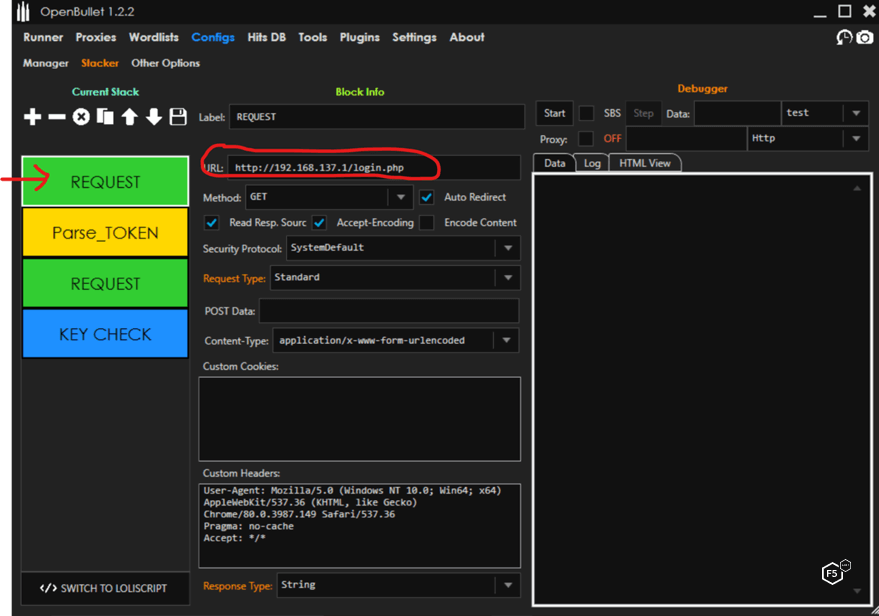
Figure 3. Configuring a request in OpenBullet.
Then we add a Parse block to extract the token from the GET response to send with our login POST, as shown in Figure 4. Depending on the website design, this step may or may not be necessary. We can extract the token by indicating what is on the left and right side of it in the response source code. We assign the extracted token to the variable token.
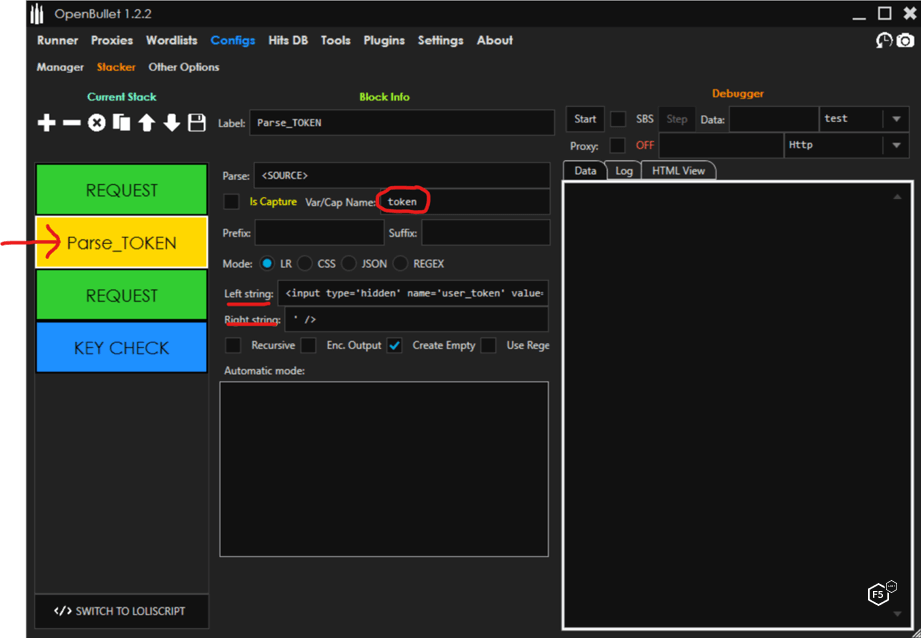
Figure 4. Configuring an OpenBullet parse token.
Now we can add a Request block to form and send the login POST. In the POST Data field, we build out our POST request. In this case:
“username=<USERNAME>&password=<PASSWORD>&Login=Login&user_token=<token>”
The tool will substitute <USERNAME> and <PASSWORD> for the values contained in the combolist and insert the token obtained in the Parse block. The full POST looks like this with the variables substituted for each request:
“http://192.168.137.1/setup.php?username=<USERNAME>&password=<PASSWORD>&Login=Login&user_token=<token>”
Figure 5 shows how this looks in OpenBullet.
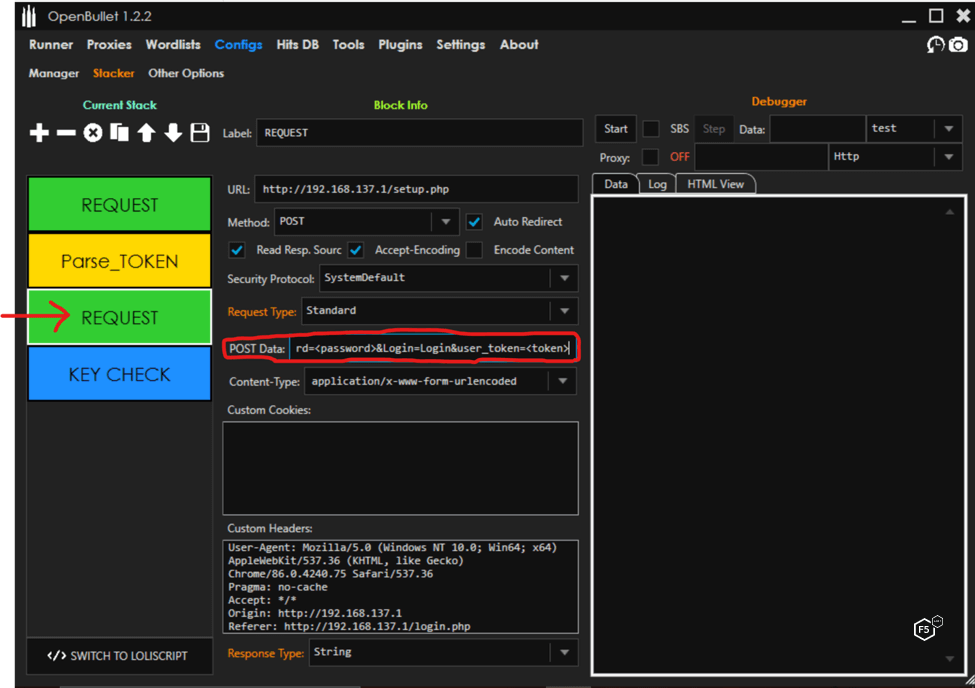
Figure 5. Configuring an OpenBullet parse token, part 2.
Now we can add a Key Check block to look for any element on the page that will denote a success or failure, as show in Figure 6. The tool keeps track of successes and can capture other information in its database, such as point balance or any other interesting field.
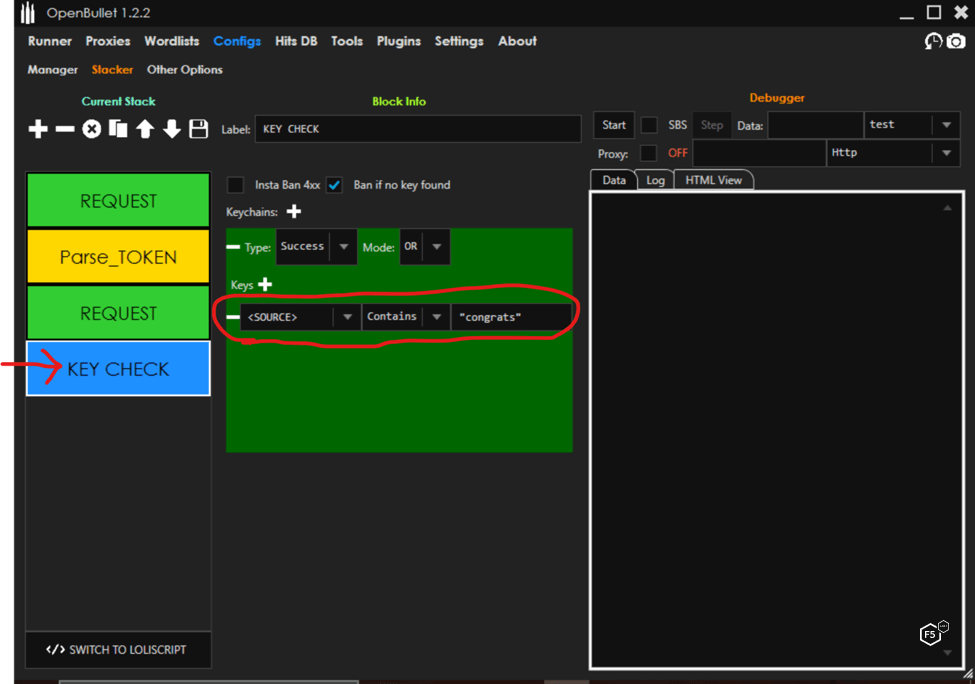
Figure 6. Configuring a Key Check block in OpenBullet.
All Ready for Credential Stuffing
Now that we are done configuring, we are ready to try this on a victim website, which is a matter of launching the attack in the tool’s Runner section. Part 2 of this article will look at how attackers run the tool and manage CAPTCHA evasion. Stay tuned!


