Samba.org, which distributes Samba open-source software that provides Windows file sharing access to non-Windows machines, just disclosed a critical remote code execution vulnerability1 that has existed for 7 years. That number was jaw dropping last month when Intel’s AMT vulnerability was released, but between this latest vulnerability and WannaCry, the security industry may be getting numb to shocking discoveries.
Need-to-Know Facts
- This vulnerability is the Linux version of WannaCry, appropriately named SambaCry. A malicious Samba client that has write access to a Samba share could use this flaw to execute arbitrary code typically as root.
- The flaw allows a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it with the privileges of smbd (typically root).
- This flaw affects all versions of Samba from 3.5.0 onwards, except for the most recent releases of Samba 4.6.4, 4.5.10 and 4.4.14.
- There's no DoublePulsar back door piece to this just yet, but working exploit code for Metasploit4 was released publicly over 24 hours ago, so expect it to be weaponized quickly.
How Bad Is It, Really?
Samba is an open source network application that provides the same functionality as Microsoft Server Message Block (SMB). SMBv1 was the target of the EternalBlue exploit, which runs on Microsoft systems. However, Samba is not the same application. Because Samba is added to Unix systems for file share compatibility to Microsoft systems, it is often not running out of the box. Granted, it's on nearly every Linux distribution, but not everyone uses it. Samba is also used on many network appliances and devices, as these devices often use Linux as their internal operating system. Therefore, Linux systems and many network appliances are potentially vulnerable.
The vulnerability requires the following conditions:
- smbd must be running on a port accessible to the attacker (tcp/445)
- the "nt pipe support" setting must be enabled (on by default) in smb.conf
- the attacker must have access to a writeable share
Notably, the attacker does not have to have authenticated access if they can write to the writable share anonymously.
In order to exploit the vulnerability, the attacker would upload a shared object file to the writeable share and issue a simple command to cause smbd to execute the shared object.
This will cause the smbd process to execute the code contained in the target.so file with its level of privilege, which is usually root. The Metasploit exploit module allows the attacker to choose the payload. An attacker who is in a position to leverage this vulnerability will have full access to the entire system with root level privileges.
Threat Scope
A shodan.io query of "port:445 !os:windows" shows approximately one million non-Windows hosts that have tcp/445 open to the Internet, more than half of which exist in the United Arab Emirates (36%) and the U.S. (16%).
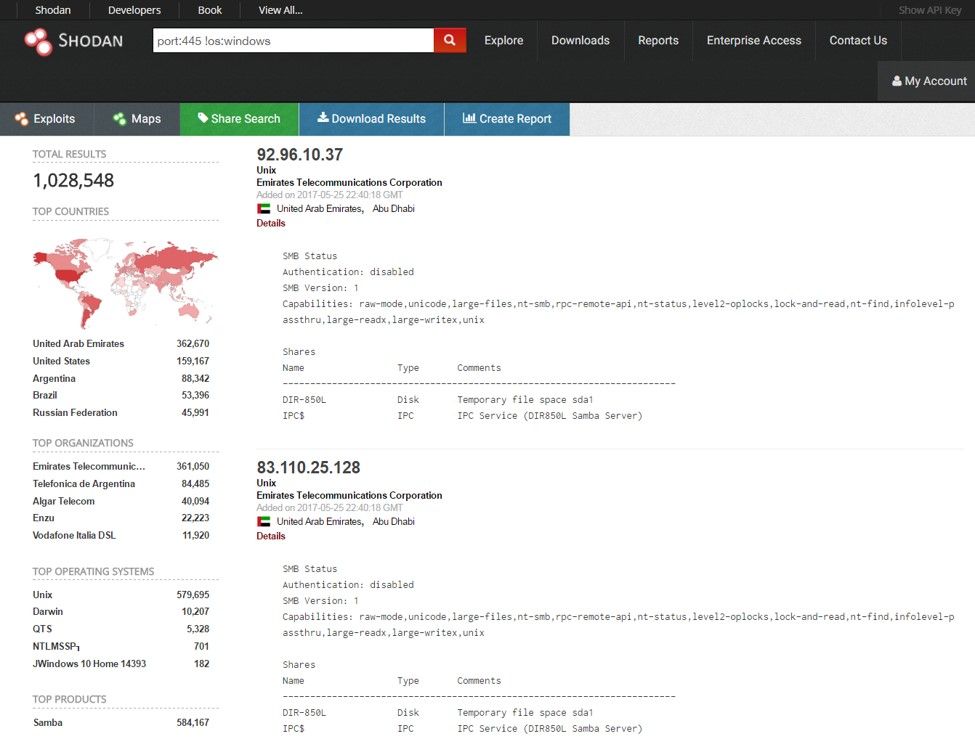
Figure 1: Shodan search reveals devices with port 445 open to the Internet
While many of these may be running patched versions, have SELinux protections, or otherwise don't match the necessary criteria for running the exploit, the possible attack surface for this vulnerability is large.
Because exploit code is available, and the exploit itself is reasonably simple, the likelihood that this might be integrated into various malware and ransomware toolkits is very high. There is also the possibility that this will be used in a worm-like fashion, such as we saw with WannaCry just two weeks ago.
It’s also worth noting that we’re heading into a holiday weekend for the U.S., which is a prime “strike when everyone’s out” time for attackers.
Threat Mitigation Actions
Network + Remote Code Execution + Root = Drop What You’re Doing and Patch. Snarky-ness aside, there are several standard fixes and mitigations to consider:
- samba.org has released patched versions of their software, including ones for older, unsupported releases. Upgrading to one of these versions and restarting smbd fixes the issue.
- Adding the line "nt pipe support = no" to the smb.conf file and restarting smbd will also stop attackers from being able to exploit this vulnerability, but this can disable some expected functionality for Windows clients of the vulnerable Samba server.
- System-level protections include SELinux. On Redhat, Linux SELinux is enabled by default and the default policy prevents loading of modules from outside of samba's module directories. This blocks the exploit. However, many systems administrators turn off SELinux since it can interfere with the operation of third-party software. It is important to check the status of SELinux with the “getenforce” command.
- Disk areas meant to be shared as writeable shares via Samba, if they are partitions, can be mounted on the Linux server with the "noexec" flag, which also prevents the exploit from working.
- Firewalls can be used to block access from untrusted networks to port tcp/445.
More Information
- If you are an F5 customer, please refer to the following support article for information on F5 product vulnerabilities (not vulnerable), and mitigation solutions: https://support.f5.com/csp/article/K13551136
- Official details from the creators of Samba: https://www.samba.org/samba/security/CVE-2017-7494.html


