
Download the full report now!
Executive Summary
Privacy today isn’t just about staying away from prying eyes. The very act of communicating across the Internet with open, non-confidential protocols invites exposure to code injections, ad injections, and overall risk injection.
A recent example involved spyware that was developed by FinFisher and only sold to nation-states. Middleware systems inside the Türk Telekom IPS hijacked unencrypted web sessions, then redirected the sessions to websites that installed the spyware. It appears this was a targeted attack on five provinces in Turkey and specific locations in Syria. Similar middleware systems were also used inside of Telecom Egypt to, again, hijack unencrypted web sessions. This time the motive was financial: the redirects sent unsuspecting users to revenue-generating ad farms and crypto-mining malware downloads.*
This is why cryptographic protocols like Transport Layer Security (TLS) exist—to help prevent adversaries from eavesdropping and tampering with data. TLS provides a way for endpoints to be authenticated and communicate confidentially over the Internet. Encrypting Internet connections with TLS would have stopped these redirect attacks. But like all security protocols, it must be constantly tested, proved, and improved if we have any hope of staying ahead of adversaries.
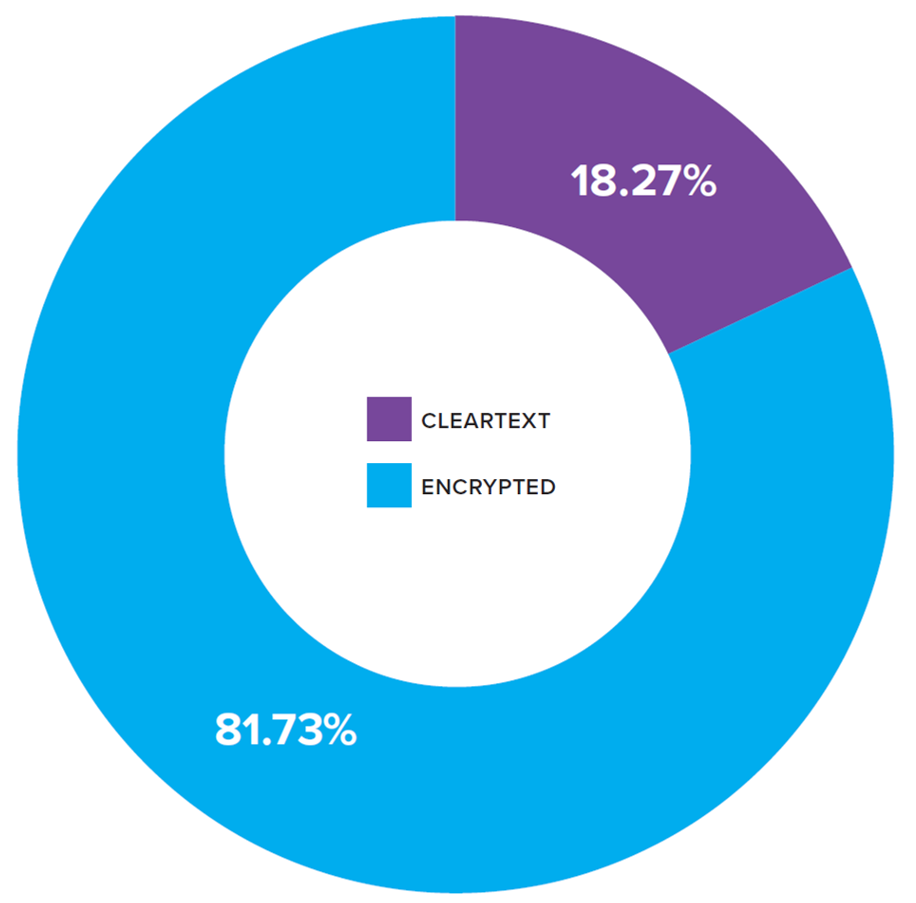
Encrypted HTTP Page Loads (source: telemetry.mozilla.org)
F5 has been diligently monitoring the “cryptographic health” of the Internet since 2014. In 2016, we began reporting on the state of TLS in the F5 Labs 2016 TLS Telemetry Report. With the benefit of nearly four years of data, we’ve seen some positive signs of progress and some lingering areas of concern. In this, our second report in the series, we share our key findings for 2017, based on a sampling of more than 20 million SSL/TLS hosts worldwide:
- TLS’s predecessor, SSL 3.0—which is now prohibited from use by the Internet Engineering Task Force (IETF)—is taking its time disappearing entirely from the Internet. 11.2% of Internet hosts still support it.
- The transition from TLS 1.1 to TLS 1.2 has been steady, with 27% more hosts making the move in 2017. Currently, 89% of hosts are using TLS 1.2.
- IETF’s progress on TLS 1.3 has been slow for many reasons, not the least of which is debate about whether TLS 1.2 is really “broken” enough to require fixing.
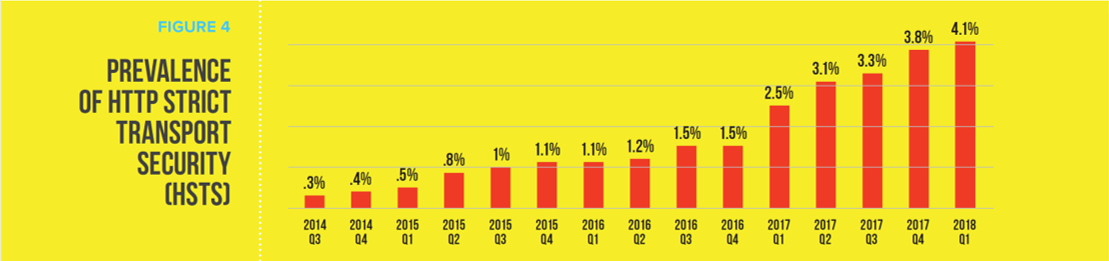
- The HTTP Strict Transport Security (HSTS) header, important because it instructs the browser to always use a secure connection, is finally seeing some forward motion, even though numbers are still very low. Since the summer of 2014, HSTS usage has grown from a mere .33% to just over 4% in Q1 of 2018.
- Forward secrecy, a cryptographic technique designed to prevent adversaries in the future from decrypting captured, encrypted sessions from today, is steadily being adopted. Now, 88% of hosts prefer forward secrecy, up from about 30% in 2014.
- Self-signed certificates (those not signed by a trusted Certificate Authority) dropped from 15.2% in the first quarter of 2017 to 11.6% in Q1 of 2018. At the same time, free certifications from Let’s Encrypt jumped so sharply in 2017 that it is now the second most popular Certificate Authority website.
Security teams can use these findings to evaluate their security posture and make improvements where needed. We’ve also included recommendations around the use of HTTPS for every website as well as the use of HTTP Strict Transport Security (HSTS); the use of Online Certificate Status Protocol (OCSP) stapling to ensure the validity of digital certificates; the need to patch to protect devices from ROBOT attacks; and the recommended use of Qualys SSL Labs to test your website’s cryptographic security posture.
To see the full version of this report, including recommendations, click “Download” below.


