Introduction - Hunt or Turkey Shoot?
We are continuing our “Hunt for IoT,” although we’re tempted to say it’s becoming more of a turkey shoot than a hunt as IoT security incidents are becoming so prevalent. This research rounds out our third year of looking at the attacker’s hunt for vulnerable IoT devices, and their continual expansion of IoT targeting. We have expanded our research beyond just tracking telnet attacks to now tracking attacks against more than 150 ports used by IoT devices. Because this sixth volume in our research series is significantly larger than previous ones, we are releasing our latest research efforts as a series of articles. In future articles, we’ll introduce you to more than two dozen new Internet of Things botnets (thingbots) that have been discovered since our last report; the attacks building these thingbots; and the networks the attacks are launched from.
This first article explores the effects of compromised IoT devices on individuals, organizations, and the society itself. News headlines are already chock full of notices of breached computers and platforms. The effect of compromise amplifies once you consider that there are literally billions of IoT devices out there. You read that right: billions. In our Hunt for IoT Report Volume 4, we referenced analyst projections (see Figure 20) that estimated we were somewhere in the 8 billion deployed range with a total eventual market of 1 trillion. And these estimates assume we haven’t hit 1% market adoption. We’re still in the early adopter phase and yet we are already seeing devastating attacks from IoT botnets. Some that have been developed are capable of taking down the Internet.
According to DBS Bank, which looked at data from IoT research institutions, we will reach 100% market adoption over the next 10 years. 2019 is the tipping point1 between early adoption and the early majority, where sales and deployment of IoT devices take off at an exponential rate.
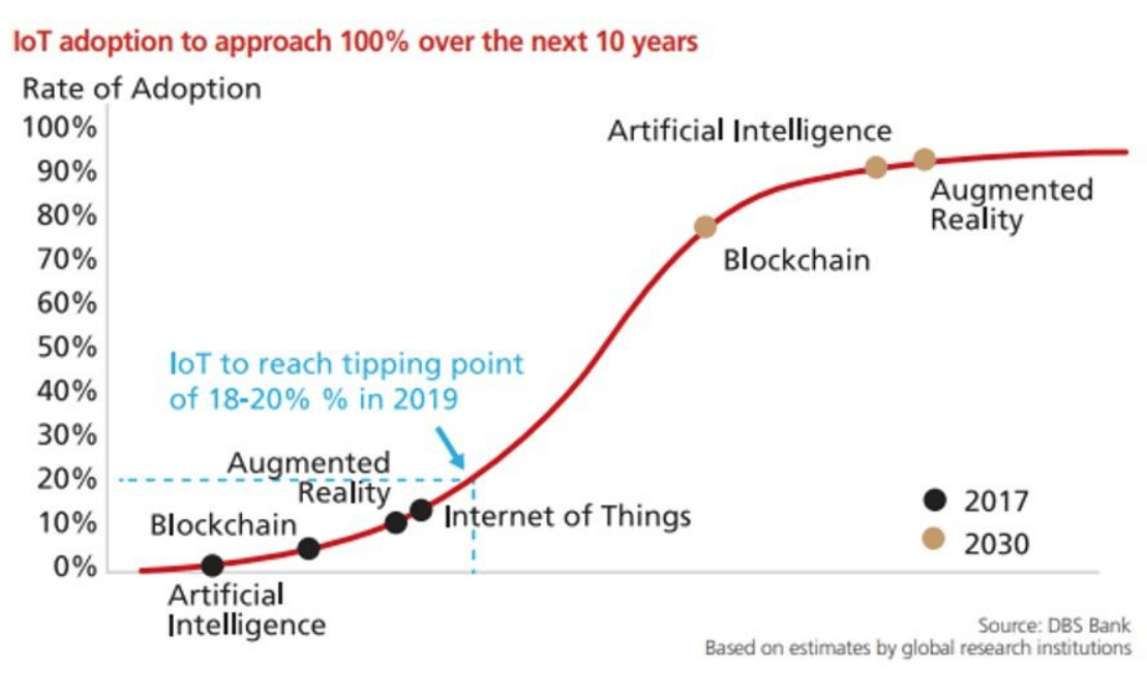
Figure 1: DBS Bank image depicting path to 100% IoT market adoption
What is the Problem with IoT Security?
Security guru Dan Geer notes that the cybersecurity industry came of age with the introduction of Windows 95 and its built-in TCP/IP stack. Suddenly every home computer was on the Internet in a world “where every sociopath is your next-door neighbor.”2 These home computers were poorly administered by amateurs. At that point, malware and cybercrime became the Internet's fastest growing enterprise. Today, we are repeating that mistake with a global pandemic of compromised IoT devices. Specifically, the hockey stick growth maps of cyber-mayhem look unnervingly, similar to what we experienced 24 years ago with PCs.
Consumer-Grade Technology
To begin with, most IoT devices lack nearly all of the security features of a mature, robust, general-purpose home computer system. And that’s saying a lot, if you consider the “security features” of your average home computer. But IoT is even weaker. How weak? Well…
Most don’t have any automatic patching capability, much less a system to warn the operator of the need to patch. They use extremely poor authentication mechanisms—our IoT Security is dependent on a telnet password of 12345. They usually don’t have forensic capability and, in many cases, not even logging functions. If they do, logging is lightweight or easily compromised by an attacker. Manufacturers rarely provide “secure” modes of operation or hardening procedures to lock down features. In fact, most IoT devices rarely offer any precautions to their users about placing these devices on the Internet or that any dangers exist at all.3
The Monoculture Problem
Nearly all IoT operating systems are derived from Linux, because of its portability, speed, and open, free license. A decade ago, Linux malware was very rare. With the growth of IoT and Android, Linux malware is rivaling Windows malware in prevalence. And like the old worries about Windows, we have a serious “monoculture” problem. In agriculture, a monoculture refers to a single species of crop or livestock that is vulnerable to a single disease that could wipe out the entire population in a single pandemic. In 2003, security pundit Bruce Schneier noted, “The basic problem with a monoculture is that it's all vulnerable to the same attack.”4 A single IoT exploit or malware/thingbot is a weapon that can be used to attack thousands, if not millions, of IoT devices with a click of the mouse.
Lack of Security Tools
Since we just talked about the power and prevalence of IoT malware, we should mention that, if an attack were to strike, you don’t have much recourse except to reflash the software (assuming it’s possible and you can figure out how) or throw the device away. The anti-virus market for Linux-based systems, much less IoT devices, is not nearly as mature or sophisticated as the Windows market. Of course, anti-virus is highly unlikely to be installable on an IoT device. Because of the size and limited capability of these devices, there are no on-box security tools available for IoT devices. Those that are available mostly work off box, on the network to which the IoT device is connected, which provides significantly less visibility and control over the device itself.
Abundance of Long-lived, Unpatched Vulnerabilities
The average lifespan of a refrigerator is 17 years.5 Can you imagine how quickly a 17-year old operating system would be hacked when connected on the open Internet? IoT devices may or may not have more vulnerabilities than any other nascent platform. But as we said, these devices are rarely patched and poorly managed, but also ubiquitous and numerous.
Let’s look closer at the lifespan of an IoT vulnerability.
| Step | Parties involved | What Happens | Magnitude | If not? |
|---|---|---|---|---|
| Blissful Ignorance Zone | ||||
| 1. Discovering the IoT vulnerabilities | Researchers and attackers | Who finds these holes? Those incentivized to do so: security researchers and the attackers. | Likely a large number of disclosed and undisclosed vulnerabilities | Vulnerability remains undiscovered |
| 2. Disclosing the IoT vulnerabilities | Researchers and attackers | Attackers will not tell anyone about the holes they’re exploiting. Responsible security researchers will only tell the IoT manufacturers. | A subset of the previous | The vulnerability remains known only to the attacker community |
| Danger zone – Zero-day territory | ||||
| 3. Accepting the Vulnerability | IoT manufacturers and security researchers | Tell the manufacturer about the vuln… but, can you find the right company? does company still exist? Will they listen to vuln reports? | A subset of the previous | The vulnerability is published as a zero-day in a free-for-all hacking extravaganza |
| 4. Publishing the IoT Vulnerabilities | IoT manufacturers and security researchers | Does IoT manufacturer even consider this a vuln? Are they willing to disclose? | A subset of the previous | The vulnerability remains hidden or released as a zero-day |
| Extreme Danger Zone – Vulnerability known | ||||
| 5. Creating the patches for the IoT vulnerabilities | IoT manufacturers | Is IoT manufacturer willing and able to create patch? | A subset of the previous | The vulnerability remains unpatched but now becomes widely known amongst attackers |
| 6. Awareness of the patch | IoT manufacturers and IoT owners | Does IoT manufacturer have a mechanism to notify owner? Are the IoT listening? | A subset of the previous | The vulnerability remains unpatched but now becomes widely known amongst attackers |
| 7. Applying the patches to the IoT vulnerabilities | IoT owners | Is IoT owner capable of applying the patch correctly? Even at best, many organizations can only patch 1 in 10 holes | A subset of the previous | The vulnerability remains unpatched but now becomes widely known amongst attackers |
Figure 2: IoT vulnerability lifespan
Impacts of IoT
We broke down the payloads and impact of the thingbots we’re tracking at F5 Labs. When an IoT device is absorbed into the thingbot, here’s the disruption they cause:
| Impact | Prevalence | Effects |
|---|---|---|
| Used as a DDoS attacker against someone else | Very common. Over half (58.6%) of the known thingbots are used for this. | Theft of bandwidth, Possible denylisting of IP address |
| Crypto-currency mining | Common. 15.5 % of the known thingbots are used for this. | Theft of compute resources on device |
| Proxy spying, man-in-the-Middle attacks on traffic passing through a device | Uncommon. 8.6% of the known thingbots are used for this. | Exposure of privacy, personal data, credential theft, fraud |
| Surveillance from embedded sensors (camera, audio, other) | Uncommon. 5% of the known thingbots are used for this. | Exposure of personal data, fraud |
| DNS redirect, proxy for hijack | Rare. About 3% of the known thingbots are used for this. | Click fraud, possible denylisting of IP address |
| Hijack for botnet Command & Control | Rare. About 2% of the known thingbots are used for this. | Theft of bandwidth, possible denylisting of IP address |
| Credential stuffing | Rare. About 2% of the known thingbots are used for this. | Theft of bandwidth, possible denylisting of IP address |
| PDOS / Bricking | Rare - About 2% of the known thingbots are used for this. | Permanent failure of IoT device itself, loss of data |
Figure 3: Impact of thingbots
IoT: Dangerous Even When Used as Directed
Even when not subverted by a thingbot, IoT technology is a privacy travesty. Data and administrative communication channels are often unencrypted. IoT devices are often designed to capture and record real world data with things like cameras, microphones, and sensors. They’re ultraportable and designed to automatically attach themselves to wireless, seek out the Internet, and broadcast their presence.
IoT devices, even when not subverted by botnets, are powerful instruments of surveillance, control, and manipulation. Like any technology, they magnify the power of their operator and help them achieve their goals. The question is: are the controller’s goals helpful or malevolent? Sometimes it’s all a matter of perspective. The same government claiming to be protecting citizens using technology (such as surveillance cameras) may also be accused of oppressing citizens with the same technology. For the purposes of our conversation, it is the power of the IoT devices that we will examine. Power that bears examination, both in the light of legitimate usage but especially problematic when leveraged for cybercrime or cyberwarfare (/content/f5-labs-v2/en/labs/articles/threat-intelligence/ready-or-not--cyberwarfare-is-here.html).
IoT Can Be Used to Exert Ubiquitous Surveillance
Scanners and cameras such as IP cameras, automatic license plate readers (ALPRs),6 International Mobile Subscriber Identity (IMSI) catchers to collect cellular communication, biometric scanners are widely deployed across the world on government vehicles, traffic lights, public and private buildings, airports, campuses, stadiums, freeway ramps, bridges, and in our residences. All this data is collected for various commercial uses and supposedly to enhance public safety.7 But even if we assume no nefarious intent, what happens to these systems and data if they are compromised or subverted? Guess what? We’re already there with the leakage of tens of thousands of license plate images.8
Control Can Be Achieved Through Shutting Down Fleet Vehicles
Vulnerable GPS tracking systems9 and cellular gateways that are commonly used by emergency service vehicles. If compromised, they could potentially grind cities to a halt. Vulnerabilities in these cellular gateways gave the Mirai botnet the ability to launch DDoS attacks from police cars. Those same vulnerabilities allowed F5 researchers to identify a policeman’s home in less than 6 minutes from basic pattern recognition of leaked GPS coordinates. Remote access to emergency services could be devastating in the hands of an adversarial nation-state or terrorist organization.
Beyond GPS systems and cellular gateways in vehicles, most cars with power steering have a computer inside them called a Controller Area Network (CAN bus). The ability to remotely exploit cars through this system has been widely publicized for many years.10
Control Can Be Achieved Through Shutting Down Electricity
The electrical systems of smart buildings and entire municipalities are increasingly under the control of IoT devices.11 Russia has launched cyberattacks against power stations in Kiev, Ukraine, twice knocking out power to the city. The MADIoT attack12 provides an avenue for blowing power grids by synchronously switching on and off high wattage IoT devices connected to them.13
Figure 4: Usenix image depicting MADIoT attack (source:
The Abuse of IoT for Strategic Psychological Operations (PSYOPs)
Through mass surveillance systems and other IoT devices (smart TVs, VoIP systems, small office/home office (SOHO) routers, personal assistants, cars, wearables, etc.) that can grant access to a target of interest if hacked, data can be collected at mass scale and used in information warfare much like Russia’s meddling in the 2016 US Presidential election, which was fueled, in part, by their access to millions of SOHO routers in the US.14 Right now, millions of residential systems that use cameras to collect video including security cameras, baby monitors, and smart doorbells, are vulnerable to remote hijacking because of a point-to-point software they use called iLnkP2P.15
Conclusion
These are stories of current technological capabilities and how they are being used in questionable ways. And the chance of them being exploited and used in malicious attacks to the peril of human life is high. Globally, we are treating IoT devices as if they are low risk. Low likelihood of being exploited and, a low impact if the device is exploited. Yet reality is quite the opposite.
The next articles in the Hunt for IoT Volume 6 research series focuses on the IoT botnet discoveries made since our last report (/content/f5-labs-v2/en/labs/articles/threat-intelligence/the-hunt-for-iot--multi-purpose-attack-thingbots-threaten-intern.html) in October 2018. We’re tracking how they’re created, how easy they are to build and, perhaps most concerning of all, the profiles of the threat actors behind these bots.


