Cyber security has evolved in ways we never could have imagined. We have more specialized and powerful tools and services today than ever before, security budgets are slowly inching upward, and there are even glimmers of support from management. Yet, with the pace of technological change, the growing “professionalization” of cyber crime, and ever growing compliance requirements, it’s understandable why we often feel like we’re fighting a losing battle.
The good news is, it isn’t a losing battle. In this report, we talk through the essentials things we must all be doing to keep our heads above water in the current flood. Things like focusing beyond the perimeter but also protecting the applications and identities, encrypting everywhere, preparing responses to common threat scenarios like DDoS and credential breaches. But, then what? We all know the flood is going to get much worse—and soon. So, how do we get ahead of the curve so we can act instead of react?
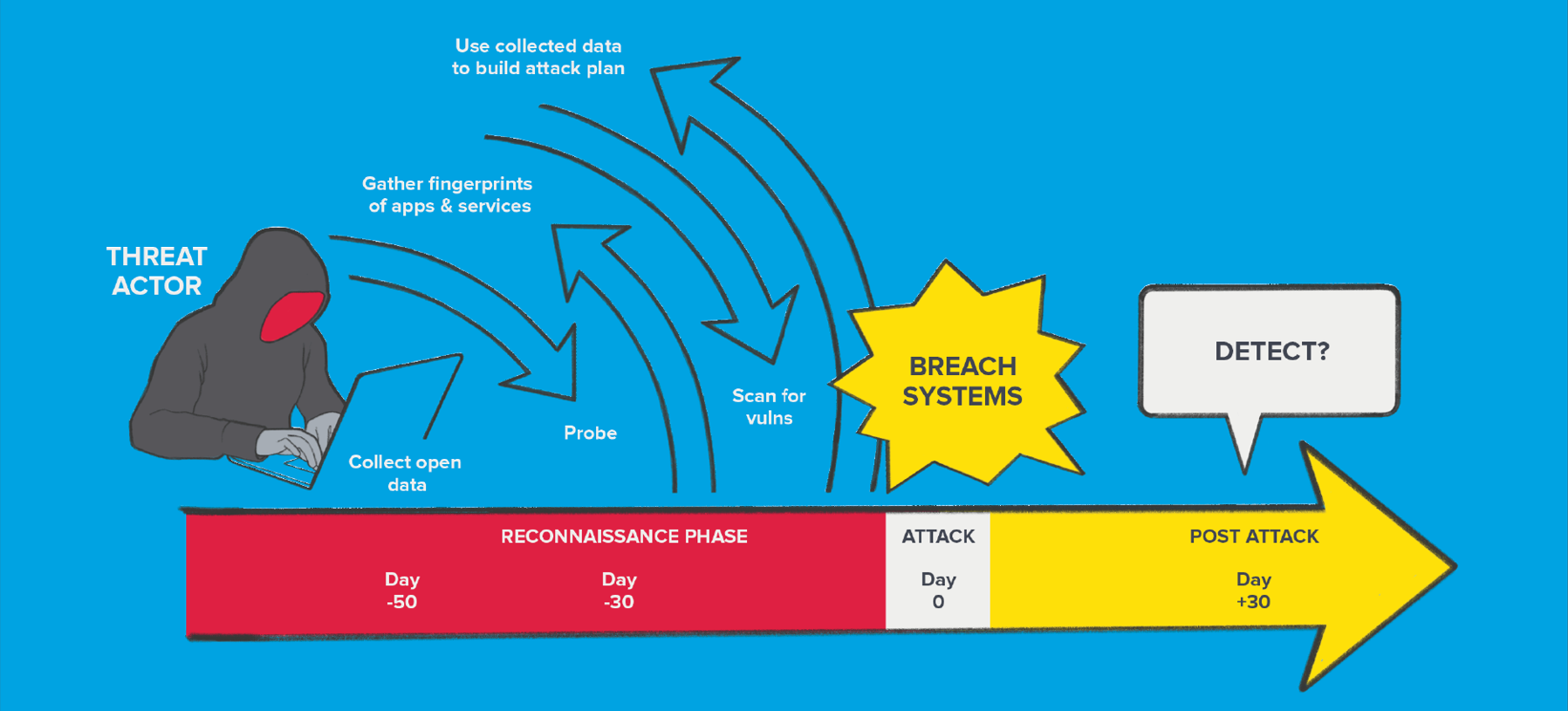
Threat Intelligence gives advanced insight into a hacker's recon phase—the value is before an attack.
Threat Intelligence gives advanced insight into a hacker's recon phase—the value is before an attack.
That’s where threat intelligence comes in. We delve into what threat intelligence really is (hint: it’s not just raw data feeds), the various types, and the growing importance of “human” threat intelligence that is actionable, relevant, and timely. We look at why only threat intelligence offers us a way to see an attack coming and prepare for it. Finally, we explain how the F5 Labs team of senior cyber security professionals will help you get there.
To see the full version of this report, click "Download" below.


