In our recent 2021 Credential Stuffing Report, we talked about the prevalence of credential stuffing attacks and the bot technology that attackers use. In my past life as a law enforcement and intelligence officer, I was often surprised by the innovation and maturity of the "businesses" and services that cybercrime entrepreneurs develop. As head of the Shape Intelligence Center, I continue to watch our adversaries evolve, and I like to see for myself how common tools and services used against our customers operate, when I can. One key service that cybercriminals use is CAPTCHA bypass. This is what I found when I went to work for a CAPTCHA-solving click farm.
What are CAPTCHAs?
Before diving into the details, let’s take a moment to review what CAPTCHAs are and how they work. CAPTCHA is a backronym for Completely Automated Public Turing test to tell Computers and Humans Apart. CAPTCHAs were first implemented in the late 1990s1 as a rudimentary reverse Turing test to help websites filter out growing volumes of problematic bot traffic. CAPTCHAs come in many forms including those shown in Figures 1 and 2.

Figure 1. An example of a traditional CAPTCHA.
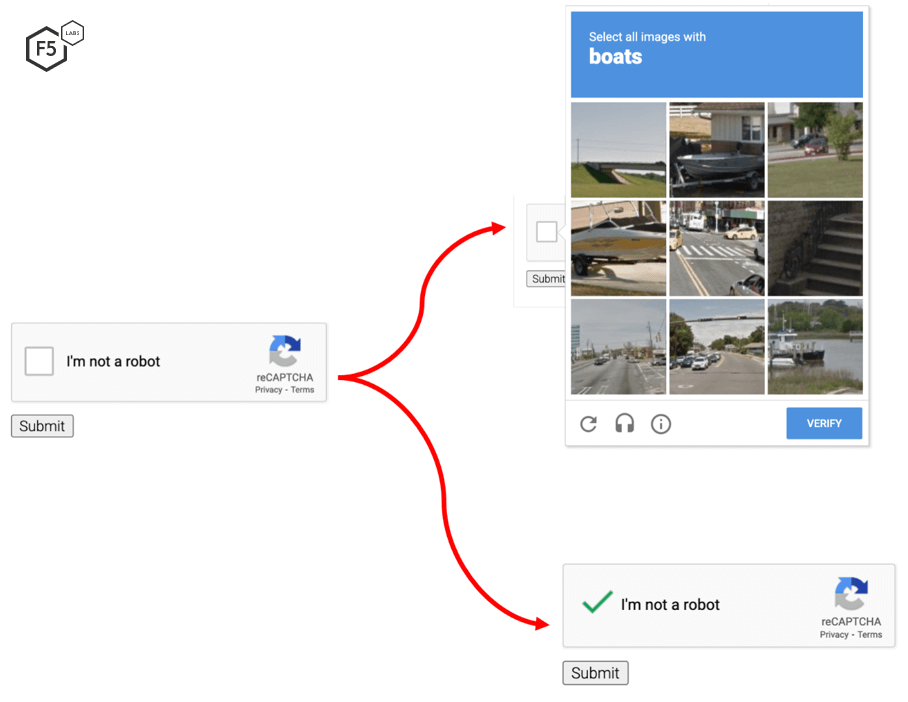
Figure 2. A reCAPTCHA presents an “I’m not a robot” checkbox to the user. A challenge like the one on the upper right is triggered if Google reCAPTCHA thinks the user might be a bot.
CAPTCHA Solvers
CAPTCHAs provided a good defense against automated attacks when they were first introduced nearly two decades ago, presenting an obstacle that the early generations of bots couldn’t easily overcome. However, as bots evolved and started solving CAPTCHAs, the CAPTCHAs started to get even more complex and difficult for humans to solve, such as the CAPTCHA shown in Figure 3.
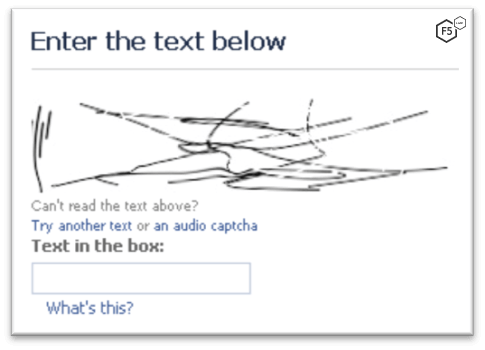
Figure 3. An actual but unsolvable CAPTCHA.
In 2013, Google researchers used Google’s deep convolutional neural network to solve the “hardest category of reCAPTCHA” and obtained 99.8% accuracy. Over the last 20 years, my success rate has hovered around 50-70% so now I become increasingly annoyed every time I encounter any form of CAPTCHA. Today, we’re at a point where bots solve CAPTCHAs more quickly and easily than most humans. The bots are not, however, using deep convolutional neural networks as Google did. They’re using third-party CAPTCHA solving services and applications instead, a few of which are highlighted in Figure 4.

Figure 4. A simple Google search turns up dozens of CAPTCHA solver services and apps.
While the variety of alternative ways to bypass CAPTCHA faster and more efficiently has grown in recent years, the original human click farm solution remains most accessible and popular. Aside from those who develop and run these services in the background, a human CAPTCHA solving service basically revolves around the human workers solving CAPTCHAs and the “customers” who purchase their output to keep their automation running on CAPTCHA-protected sites. To see firsthand how both sides of this business work, I signed up as both a solver and a customer with the Russian CAPTCHA solving company, 2Captcha.
The Mechanics of Using Solvers
So how does this process actually work? The steps below outline how an automated attack can leverage this human labor when required. In most cases, a diligent attacker will conduct reconnaissance on a target site ahead of time, during which CAPTCHA would be identified as a requirement. Once an account is created and set up (in this case, with 2Captcha), the general process is illustrated in Figure 5.
An attacker using a bot connects to a website that presents a CAPTCHA challenge.
The bot captures an image of the CAPTCHA and sends it to 2Captcha via 2Captcha’s API.
2Captcha sends the image to one or more humans to solve.
2Captcha sends the solved CAPTCHA back to the bot via the API.
The bot submits the correctly solved CAPTCHA to the website.
The website incorrectly categorizes the bot as human and allows it to proceed.
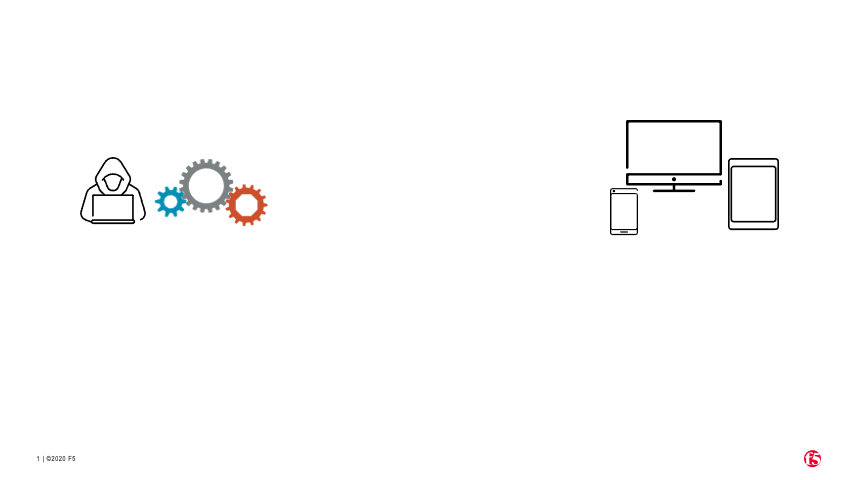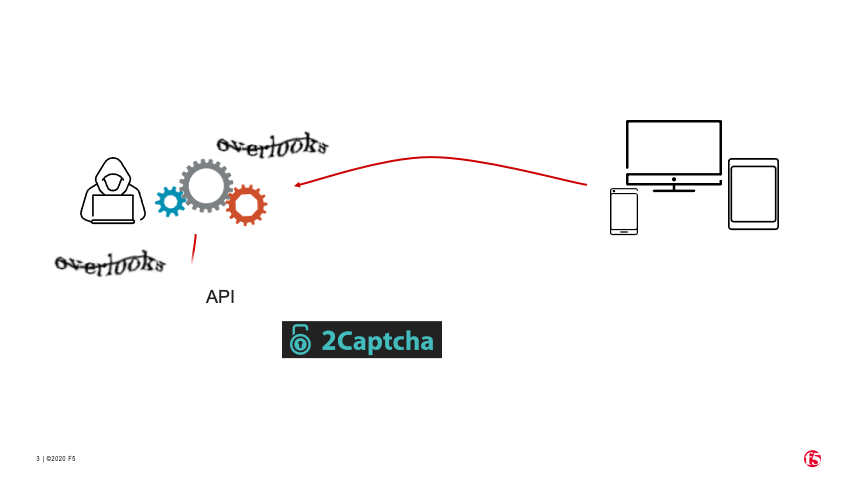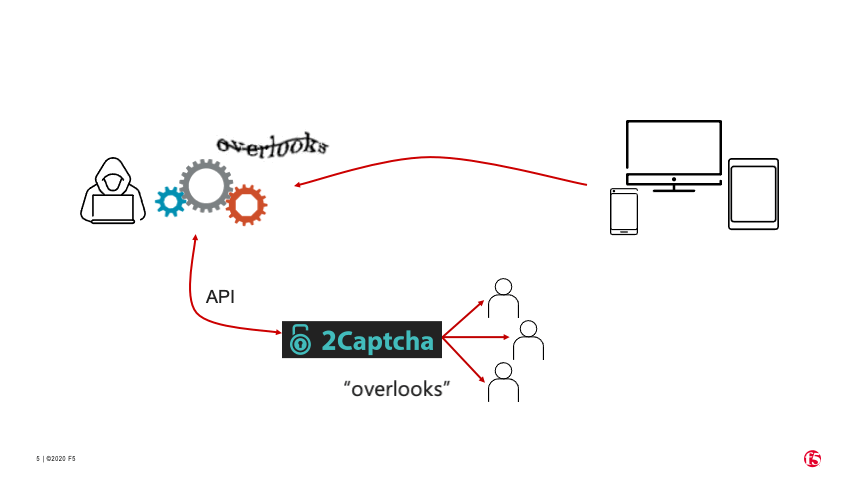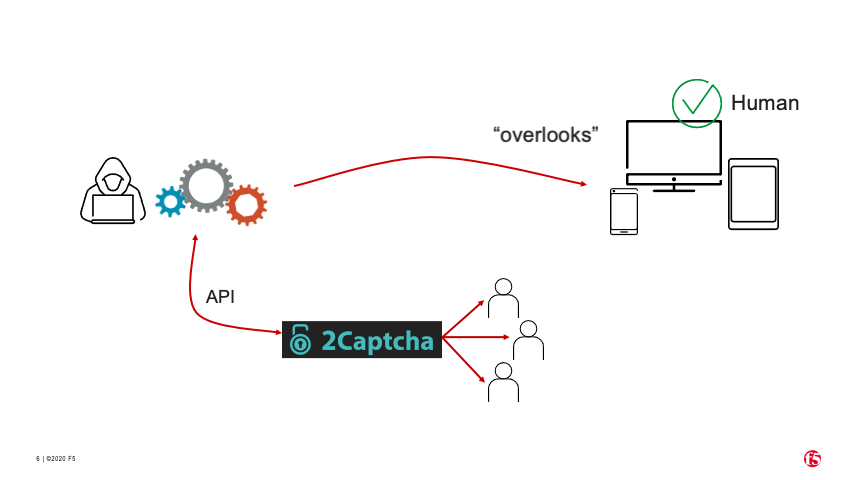
Figure 5. How CAPTCHA solver services use human labor to solve traditional CAPTCHAs.
For reCAPTCHAs that present an “I’m not a robot” checkbox on the target website (see animation in Figure 6), the process for circumventing the CAPTCHA is slightly different.
The bad actor’s bot uses 2Captcha’s API to instruct one of the human workers to visit the target website and manually check the “I’m not a robot” checkbox themselves to solve the CAPTCHA.
The human solver gets a token for the solved CAPTCHA (because they are human).
2Captcha passes the token to the bad actor’s bot via the API.
The bad actor’s bot submits the valid token to the target website.
The website incorrectly categorizes the bot as human and allows it to proceed.
All these steps can be done through a proxy, so the process is completely transparent to the website.
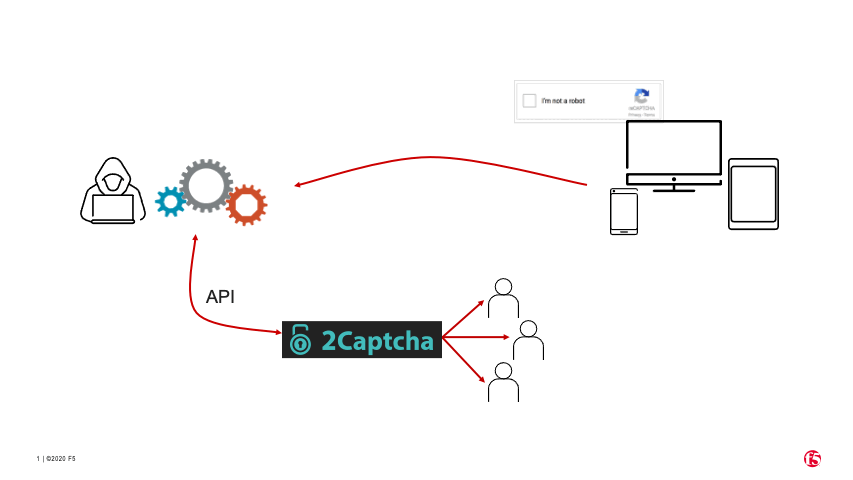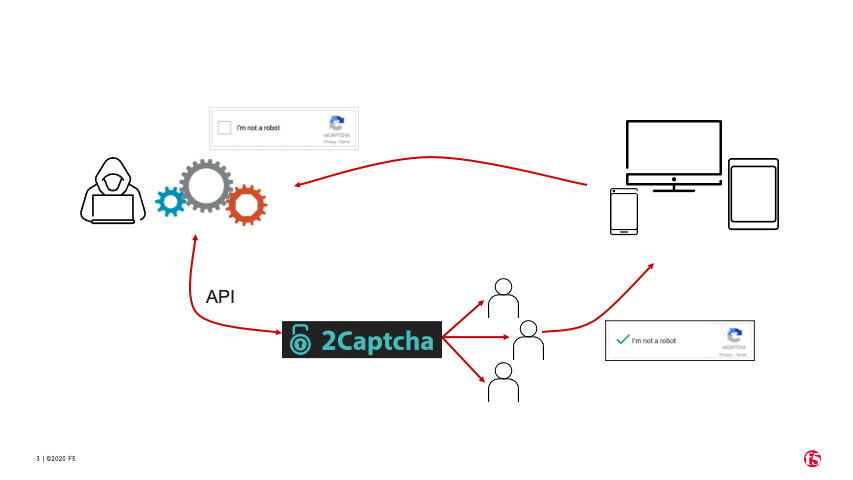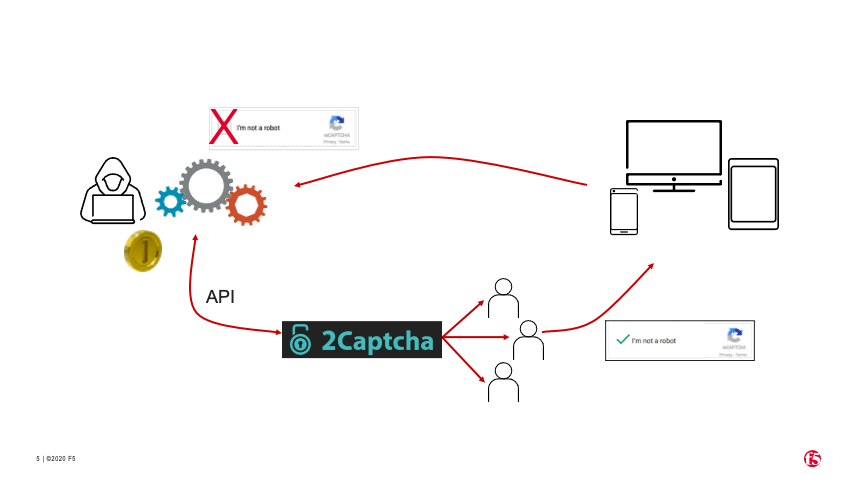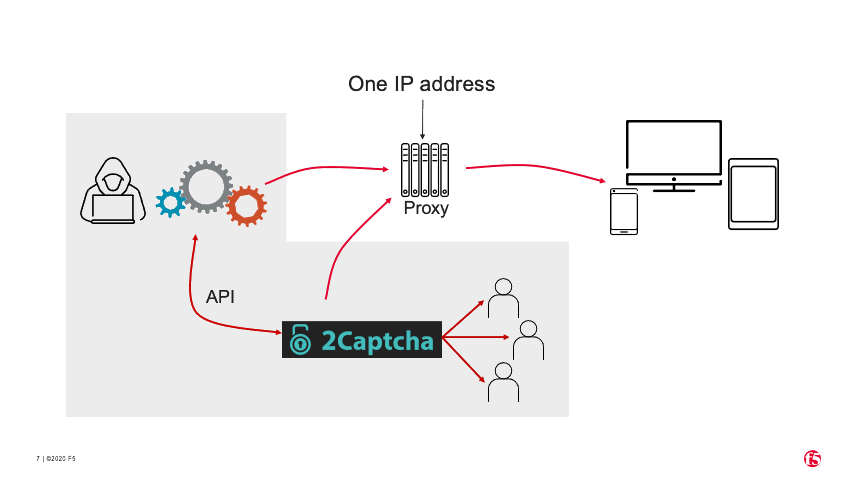
Figure 6. How CAPTCHA solver services use human labor to solve ReCAPTCHAs.
As Figures 5 and 6 illustrate, CAPTCHA solver services have made it possible for attackers to completely circumvent CAPTCHAs, including Google’s latest version called CAPTCHA Enterprise (not shown here).
The Business of Human CAPTCHA Solvers
In many respects, CAPTCHA solver services operate like any legitimate enterprise, and they are clearly in business to make a profit. While the fees they charge “customers” (attackers) might be considered reasonable, the business model is weighted heavily against CAPTCHA solvers. And with relatively low overhead, the profit margin is attractive.
Isn’t this illegal? Not really. Solving a CAPTCHA isn't the same as hacking a server or taking over an account. It may be a violation of a site's terms of service, and it may enable a criminal act (e.g., credential stuffing), but the user of the service is the perpetrator, while the service itself can claim ignorance of its customers’ intentions. Even so, many of these companies are located overseas; 2Captcha, for example, is hosted in Russia.
How Much Does the Service Cost?
2Captcha charges customers different rates depending on the type of solved CAPTCHAs they want to purchase. Traditional CAPTCHAs cost customers $0.75 per 1,000. In comparison, solved reCAPTCHAs cost customers $2.99 per 1,000—almost four times as much as traditional CAPTCHAs (see Figure 7).
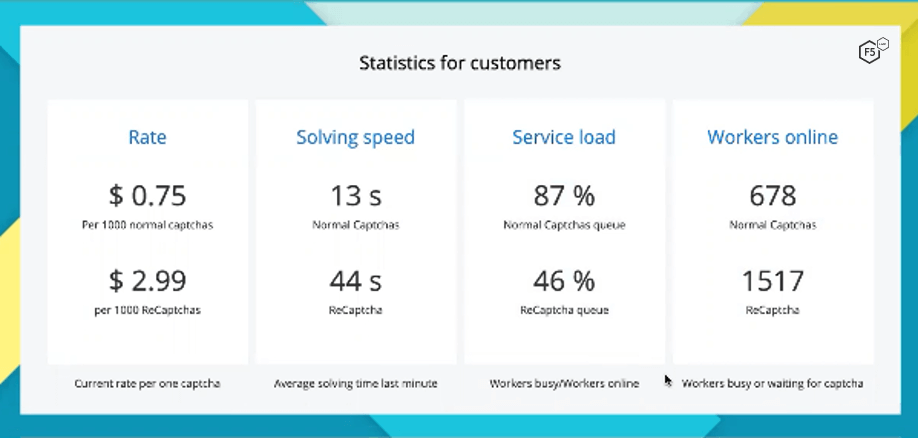
Figure 7. “Customers” (attackers) pay almost 4 times as much for solved reCAPTCHAs as traditional CAPTCHAs.
Notice the additional stats shown in Figure 7: solving speed, service load, and workers online. This is valuable data for the customers paying these rates and making purchasing decisions, and it is updated in near real time.
I Became a Human CAPTCHA Solver
Getting started as human CAPTCHA solver is one of the easiest things I’ve ever done. I set up an account as a solver (and a customer) simply by providing an email alias. The website has a very user-friendly, intuitive interface with step-by-step instructions, tutorials, and tips for solving CAPTCHAs. After exploring the site a bit, I began the training.
My Training as a Solver
Figure 8 shows an example of the training for solving traditional CAPTCHAs. Sample CAPTCHAs are shown on the left, the correct answers in the middle, and descriptions on the right. It’s evident that the support pages are not written by a native English speaker, but the instructions and execution were simple enough and I quickly improved my solve rates and speed. What’s also interesting is what is written at the top of Figure 8. It appears 2Captcha recruits human CAPTCHA solvers by claiming that solving CAPTCHAs is “helping them to quickly introduce and teach English.” It’s not exactly clear what that means, but it appears to claim that solving CAPTCHAs all day long will help a non-English speaker learn English.
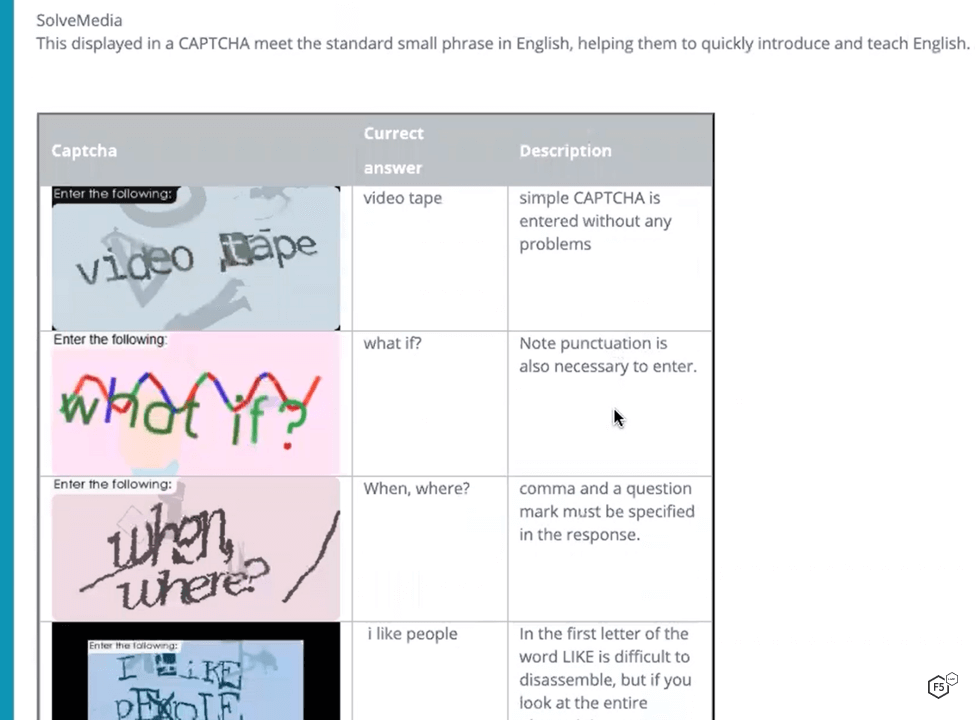
Figure 8. Detailed training for solvers provides examples and tips for solving traditional CAPTCHAs.
Figure 9 shows a similar example of the training for reCAPTCHA. Again, the instructions are a bit cryptic, but plenty of examples are provided for workers to become proficient.
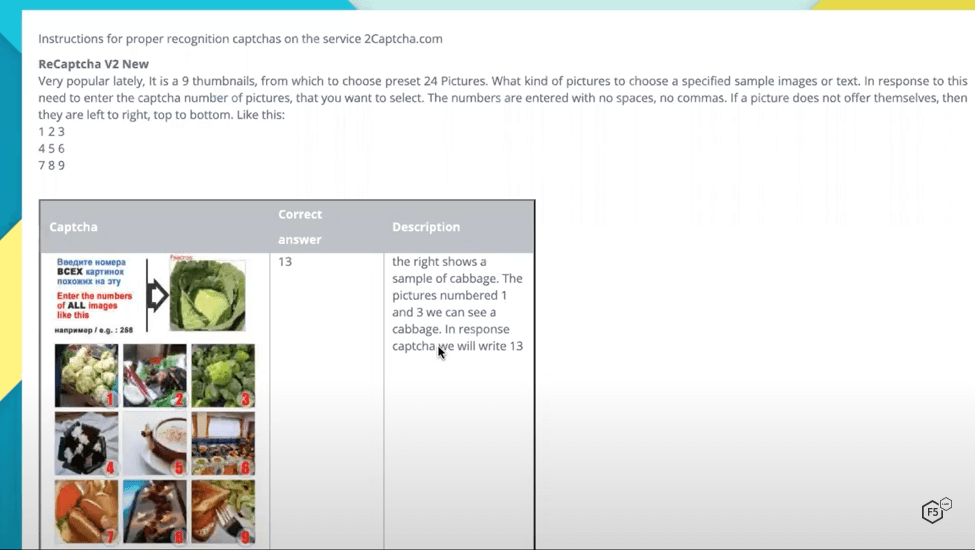
Figure 9. Detailed training for solvers provides examples and tips for solving reCAPTCHAs.
The Work of CAPTCHA Solving
The actual work of solving CAPTCHAs is pretty tedious, as you might expect. In Figure 10, I’m solving a traditional CAPTCHA. Notice in this session, I had solved 22 CAPTCHAs and had earned only $US 0.00665.
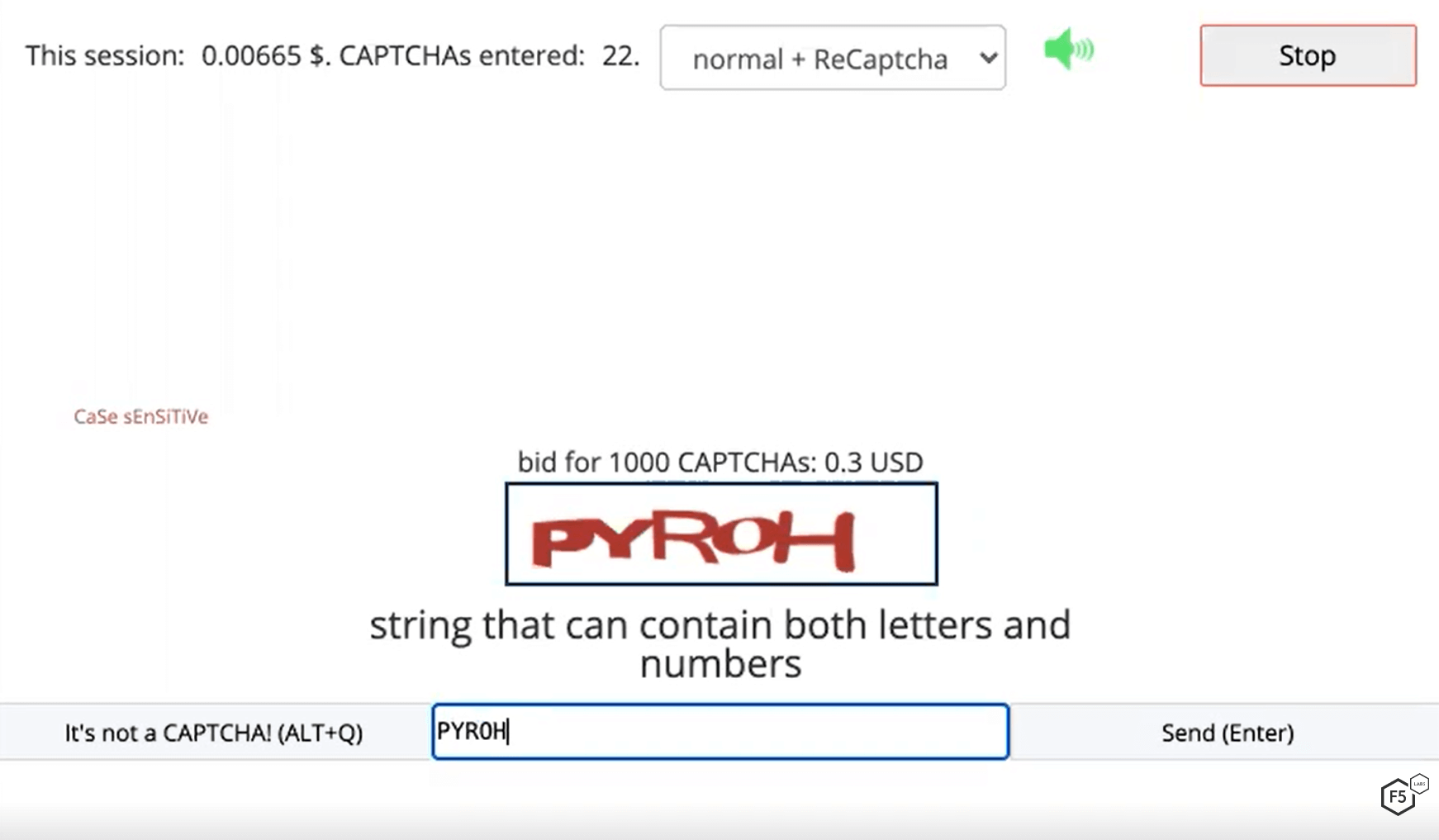
Figure 10. While solving a traditional CAPTCHA, the screen displays my current earnings and the number of CAPTCHAs solved.
As soon as I press Enter for this CAPTCHA, another CAPTCHA appears for me to solve, shown in Figure 11. Now I’ve solved 23 CAPTCHAs in this session, and I’ve earned $US 0.00695.
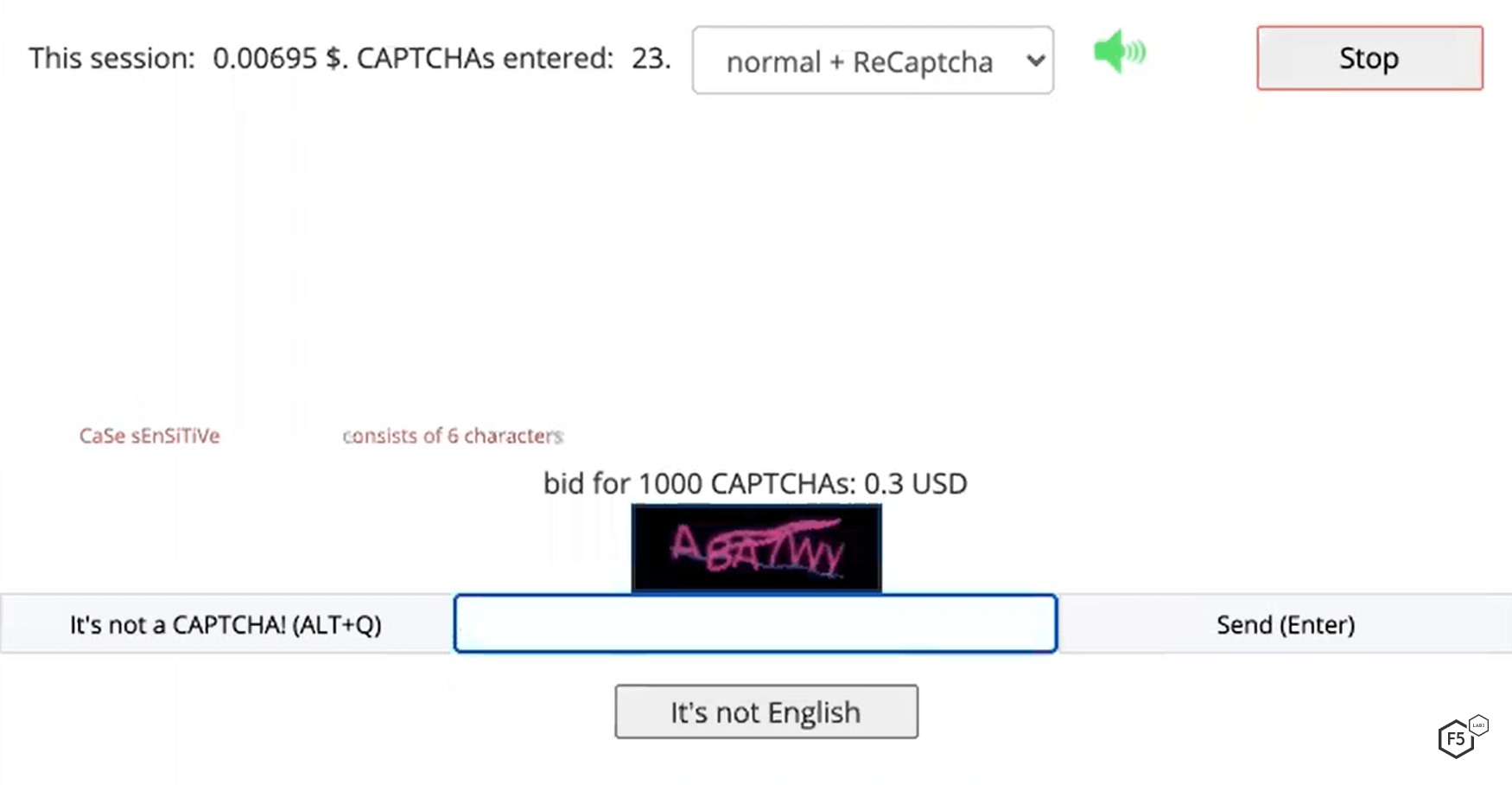
Figure 11. My earnings for solving one additional CAPTCHA have increased by only $US 0.00030.
As workers solve more CAPTCHAs and become more proficient, they receive tiny incremental pay raises. “Proficient” here is a reflection of shorter lag time between keystrokes; pay rate is not based solely on the total number of CAPTCHAs solved. Workers who are too slow or provide too many incorrect answers run the risk of being booted out of the system—even a shady clientele expects reliable service.
Getting Paid as a Solver
2Captcha’s going rate for solvers (as of April 2021) was $US 0.30 per 1,000 traditional CAPTCHAs and $US 1.01 for 1,000 Re-CAPTCHAs (see Figure 12). This is a mere fraction (4% for traditional CAPTCHAs and 3.4% for reCAPTCHAs) of what I saw customers getting charged. At these rates, solvers working 11 hours per day non-stop—which is entirely unrealistic—would make only $1.20/day for traditional CAPTCHAs. For reCAPTCHAs, which take roughly twice as long to solve, solvers would still make only $2.02 working an 11-hour day.
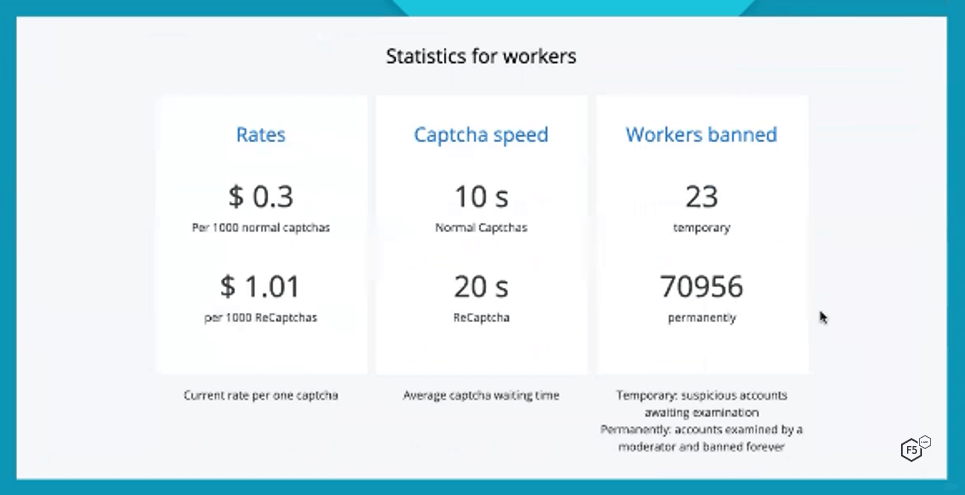
Figure 12. Workers solving CAPTCHAs make a small fraction (4% for traditional; 3.4% for reCAPTCHAs) of what 2Captcha charges its customers.
Solvers have a wide range of choices for receiving payment from 2Captcha (see Figure 13). Notice the minimum withdrawal amounts vary by payment service.
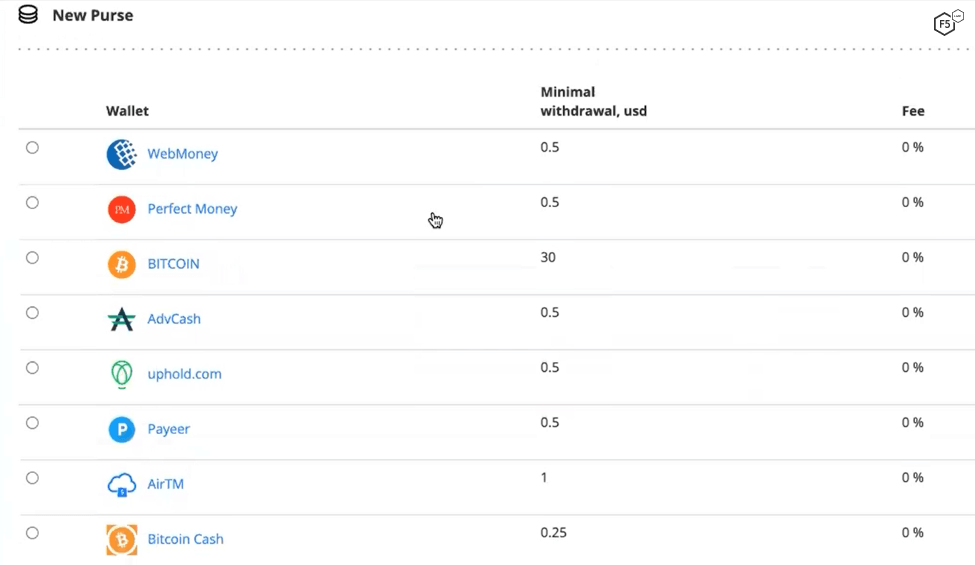
Figure 13. CAPTCHA solvers can receive payment through a variety of online payment service.
2Captcha Doesn’t Skimp on Support
Perhaps surprisingly, shady services of many kinds are often known for providing excellent customer support. 2Captcha is no exception. In addition to the user-friendly interface and the abundance of training materials, 2Captcha provides extensive support pages and FAQs (see Figure 14) for both workers and customers. Some solver companies even provide telephone support.
Figure 14. Example of 2Captcha’s FAQ page for workers. A similar page is available for “customers.”
2Captcha customers get their own set of instructions and FAQ pages. The example shown in Figure 15 provides a detailed description of Google’s most recent version of CAPTCHA, reCAPTCHA Enterprise, and instructions for how to use 2captcha to beat it.
Figure 15. A support page with detailed description of Google’s latest version of CAPTCHA, reCAPTCHA Enterprise
Conclusion
So, that is what the job of a CAPTCHA solver is like—and sadly, it’s a real source of income for many people around the world. Solver services like this one are convenient and widely used by attackers. As a result, CAPTCHAs are only a speed bump for motivated attackers while introducing considerable friction for legitimate customers. Despite this, many companies still rely on them, and some subject their customers to a CAPTCHA for every significant interaction. Cybercriminals and the parallel economies which cater to them are always innovating and evolving past defenses, and versions of CAPTCHA have been with us now for nearly two decades, frustrating legitimate users without providing meaningful barriers to the bots that have adapted to overcome them.


