Distributed Denial of Service (DDoS) is a common attack method used by hacker groups and individuals to severely hamper or shut down an organization’s online services, causing both monetary and reputation losses. While DDoS attacks have been common since the late 2000s, attack sizes have increased significantly in the past few years. Our new normal is 100+ Gbps attacks, with larger scale attacks peaking at upwards of 450 Gbps, which far outweighs the capacity of most enterprise networks outside of the service provider industry. What are you doing to prepare?
New protocol exploits and amplification attacks have become too large for most organizations to combat without the support of a cloud-based DDoS scrubbing service. In 2013, it was reported that SpamHaus services were brought down due to a 300 Gbps attack. Then in 2014, an attack peaking at 400 Gbps was recorded. However, the world’s largest recorded DDoS attack in history was reported in 2015 with a peak of 500 Gbps.
An interesting story was published1 in multiple media channels in January this year when a group calling itself New World Hacking said it initiated a successful 602 Gbps DDoS attack, targeting BBC websites. However, even while the group was marketing itself and its supposed largest DDoS attack in history, there was no real evidence of such attack. The group claimed it used Amazon’s cloud service to conduct the attack and it “programmed a bypass linked to proxies” so monitoring firms “wouldn’t detect it, anyway.” A source with direct technical knowledge of Amazon’s systems and internal processes, who did not want to be named as he or she was not authorized to speak on the record, dismissed the allegation, saying that it “doesn’t line up” with how Amazon’s cloud services work.
Around the same time that New World Hacking went public with its story, the F5 Security Operations Center (SOC) started seeing an increase in volumetric DDoS attacks. The F5 SOC has already mitigated ten ongoing attacks that peaked north of 100 Gbps in 2016, four over 200 Gbps, and two over 400 Gbps.
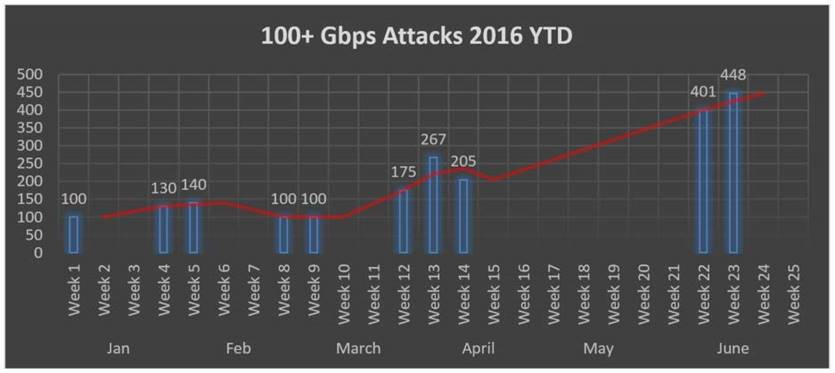
Figure 1: Peak attack bandwidth in Gbps, 2016 YTD
Figure 1: Peak attack bandwidth in Gbps, 2016 YTD
While the quantity of large volumetric attacks in Q1 was higher, the size of attacks grew exponentially in Q2, peaking at 448 Gbps in June. As expected, we are seeing flux in attack types quarter over quarter. UPD remains the most popular protocol for exploit whereas DNS and NTP exploits have been ramping up in Q2.
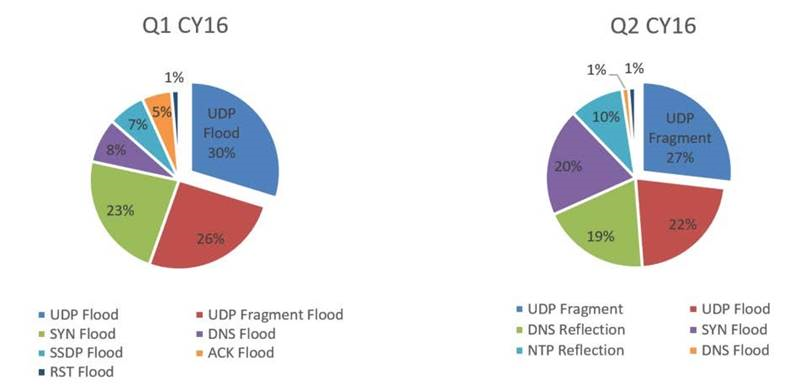
Figure 2: Q1 and Q2 attack types as detected by F5
Figure 2: Q1 and Q2 attack types as detected by F5
Below is the breakdown of attack traffic per data center, peaking at a total of 447.7 Gbps.
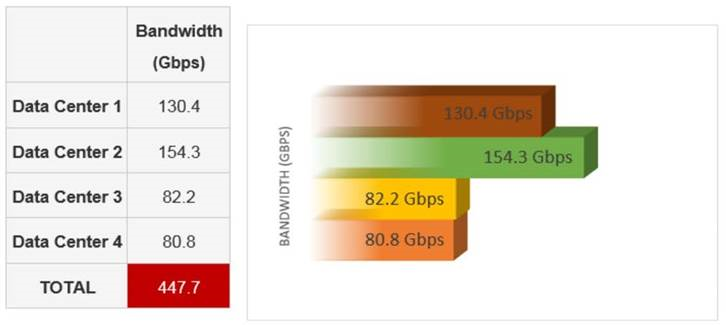
Figure 3: Pre-mitigated traffic summary by F5 (in Gbps)
Figure 3: Pre-mitigated traffic summary by F5 (in Gbps)
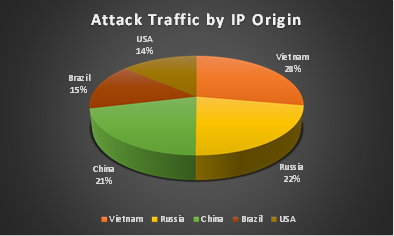
Figure 4: Botnets segmentation by source country
Figure 4: Botnets segmentation by source country
During the latest 448 Gbps attack, the F5 SOC revealed that the source countries and ASNs used for this attack spread worldwide, a common method used to decrease the likelihood of authorities catching the perpetrators.
No one has claimed responsibility for this attack as of yet, and mitigation efforts are ongoing. What we can say is the attack destination is a U.S.-based financial institution that is routinely targeted. A quick Google search can lead to some assumptions regarding current campaigns that target financial institutions by a well-known hacker collective.
DDoS, like all other Internet-based attacks, show no signs of slowing down, only increasing in sophistication, attack volume, and frequency.


