F5 Labs continually tracks DDoS trends based on data from various sources. Among the most important are the F5 Security Operations Center (SOC), the front line for mitigating DDoS attacks on behalf of F5 Silverline customers, and F5’s Security Incident Response Team (SIRT), which assists F5 customers who are under attack. This article is a continuation of our previous DDoS trend article and is based on attack data from April through June 2018 from both sources.
Here are the 2018 Q2 DDoS trends we are seeing:
- Asia-Pacific (APAC) was the most attacked region in Q2 for the first time ever surpassing North America, which has been the top attacked region since the inception of DDoS attacks.
- Q2 was absent any excessively high volumetric attacks, yet the primary business verticals attacked were hosting and co-location service providers (typically large volumetric attacks are needed to impact these providers).
- UDP fragment attacks were the number one attack type in Q2 (as they were in Q1).
- Application-targeted DDoS attacks that don’t require high rates to impact service are holding at around 2% of the total attacks received by the SOC. However, application-targeted DDoS attacks were 30% all of F5 SIRT cases requesting assistance with DDoS attacks. So, even though the percentages might seem small, customers are clearly challenged with mitigating application targeted DDoS attacks, and this problem will only increase as businesses make the move towards virtualized, application-centric services.
Introduction
Analysts estimate there are over 8 billion IoT devices currently deployed around the world and growing to 30 billion by 2020. These additional 22 billion devices will likely be vulnerable to the same kinds of attacks that are infecting IoT devices today. Most devices are attacked because they have weak access control measures, for example, they’re accessible from anywhere on the Internet, are “protected” by vendor default credentials, and allow for brute force attacks.
The global attack surface is rising exponentially with the growth in IoT, and these “things” are now the cyber weapon of choice for attackers because they are easy to compromise, they are plentiful, and they often reside in unmanaged networks where there is little chance of malware detection and remediation. Attackers know this and are building botnets at an alarming rate out of things like IP cameras, SOHO routers, DVRs, and CCTV. Seventy-four percent of thingbots we know about today were discovered just in the last two years. That list includes Mirai, the most infamous DDoS botnet, which was forked into at least 10 other Mirai spin-off botnets that also have DDoS capabilities; Reaper, which has the capability of launching a 12 Tbps attack; and JenX, which offers 300 Gbps attacks for a mere $20. The average weekly allowance of a child in the US is $17.1 That means a child in the US could afford to take almost any business offline with a DDoS attack (excluding service providers and major banks, which have the capacity to withstand a 300 Gbps attack).
Speaking of children, in June, ProtonMail was under attack by a “youth” group that goes by the name of Apophis Squad. The group of young adults claimed they learned from YouTube videos how to build the botnet they used for the attack.
Figure 1: Apophis Squad claiming ProtonMail attack
Figure 2: Apophis Squad claiming to have learned how to build bots from YouTube videos
After days of enduring a steady barrage of attacks, ProtonMail came to F5 Silverline for DDoS protection assistance. After F5 Silverline mitigated the ongoing attacks, another more sophisticated threat actor that goes by the name of NullingOVH stepped in and began launching well-crafted, application-targeted attacks that took down ProtonMail. Application-targeted attacks don’t need to be high rate to cause an impact. A lot of organizations are struggling to mitigate application-target DDoS attacks because they require both DDoS and application expertise to mitigate.
This story highlights the severity of the state we are in globally. Unsophisticated attackers can learn from YouTube videos how to create botnets and launch attacks that interrupt service. And they don’t have to be large, volumetric attacks; they can be small, multi-vector attacks that cause sustained application performance impact. (It’s also worth mentioning that the ProtonMail attacks played out on Twitter for every script kiddie hacktivist and criminal to see and learn from. This part is perhaps the most concerning of all, given we know they learn from each other and adapt faster than defenders do!) According to respondents we surveyed for the F5 Labs 2018 Application Protection Report, a “service-interrupting DDoS attack” will cost 76% of respondents between $500,000 and $50 million.
DDoS Attacks by Region
In Q2, total attacks declined, and that trend played out in each region, as well. In Q2, APAC was the most targeted region, surpassing North America for the first time ever. This trend began for F5 Silverline in late Q1 and stayed consistent throughout Q2. Other DDoS mitigation vendors have reported similar spikes in APAC, as well.2
Following APAC was North America, which received the lowest number of attacks in a quarter over the past two and a half years. In Q1, we speculated that DDoS attack targets would start leveling out globally versus North America always receiving the lion’s share, and we are starting to see that now.
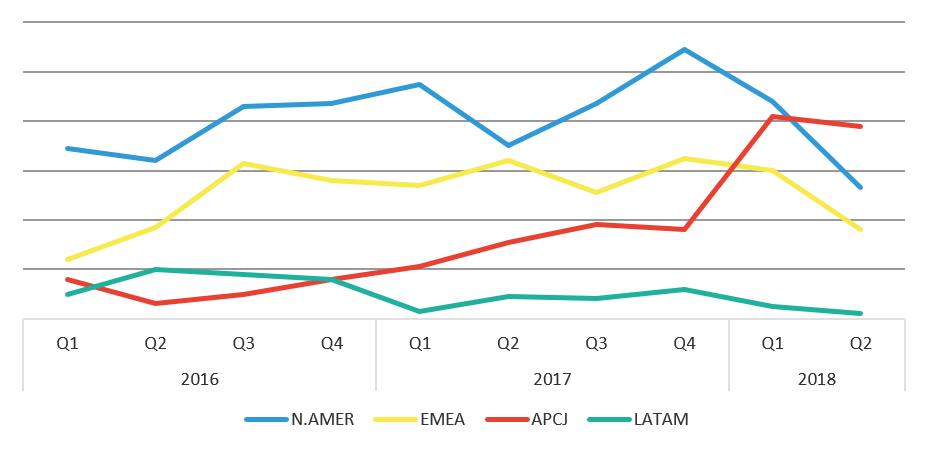
Figure 3: DDoS attacks mitigated by F5 SOC by count by region
DDoS Attack Count by Target Industry
The number of different industries targeted in Q2 was significantly less than in Q1. Hosting/co-location services were the number one target, followed by financial services in the number two position, and online gaming at number three. Tech companies fell from the number one spot in Q1 to number 5 in Q2. The flux in geo targets but not industries suggest attackers have their motives set but need to branch out attacks to other parts of the world that may not have the same robust DDoS defenses as businesses in the US, simply because they hadn’t been an attack target in the past.
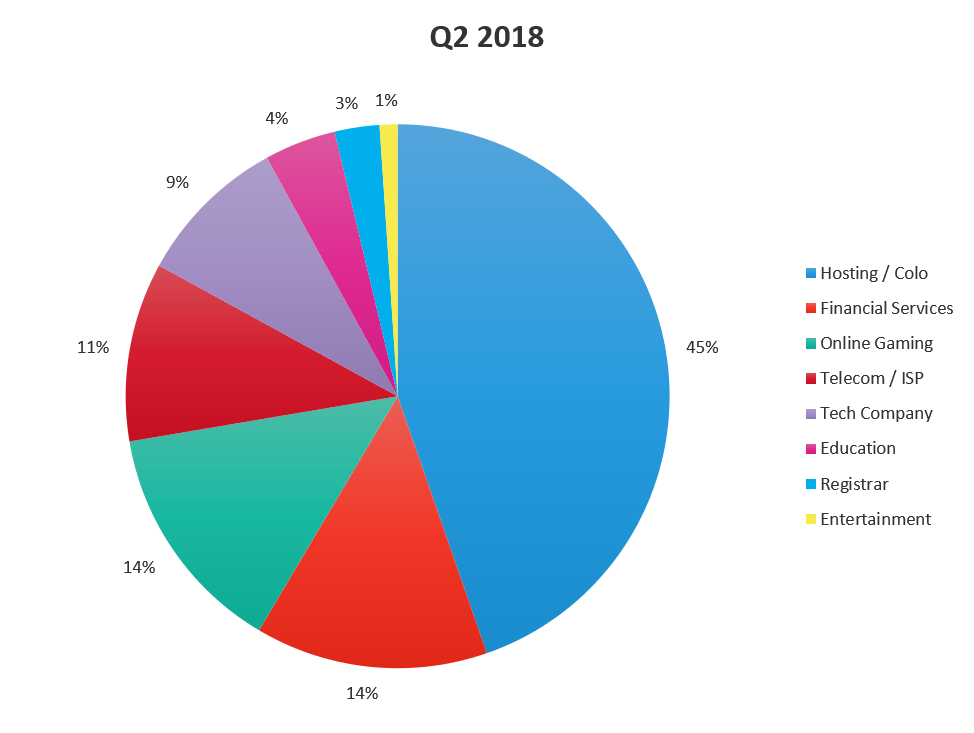
Figure 4: DDoS attacks mitigated by F5 SOC by industry, Q2 2018
DDoS Attack Count by Type
The number one DDoS attack type in 2018 has been UDP fragmentation attacks, followed by UDP flood, which was the number one attack type for the prior two years. As noted in our Q1 trend report, we expect to continue seeing UDP fragmentation attacks (a type of UDP flood that consumes more network bandwidth with fewer packets that a pure UDP flood) in the number one position as DDoS attackers favor multi-vector attacks that “fill up the pipe” by maximizing the packets and fragments being sent.
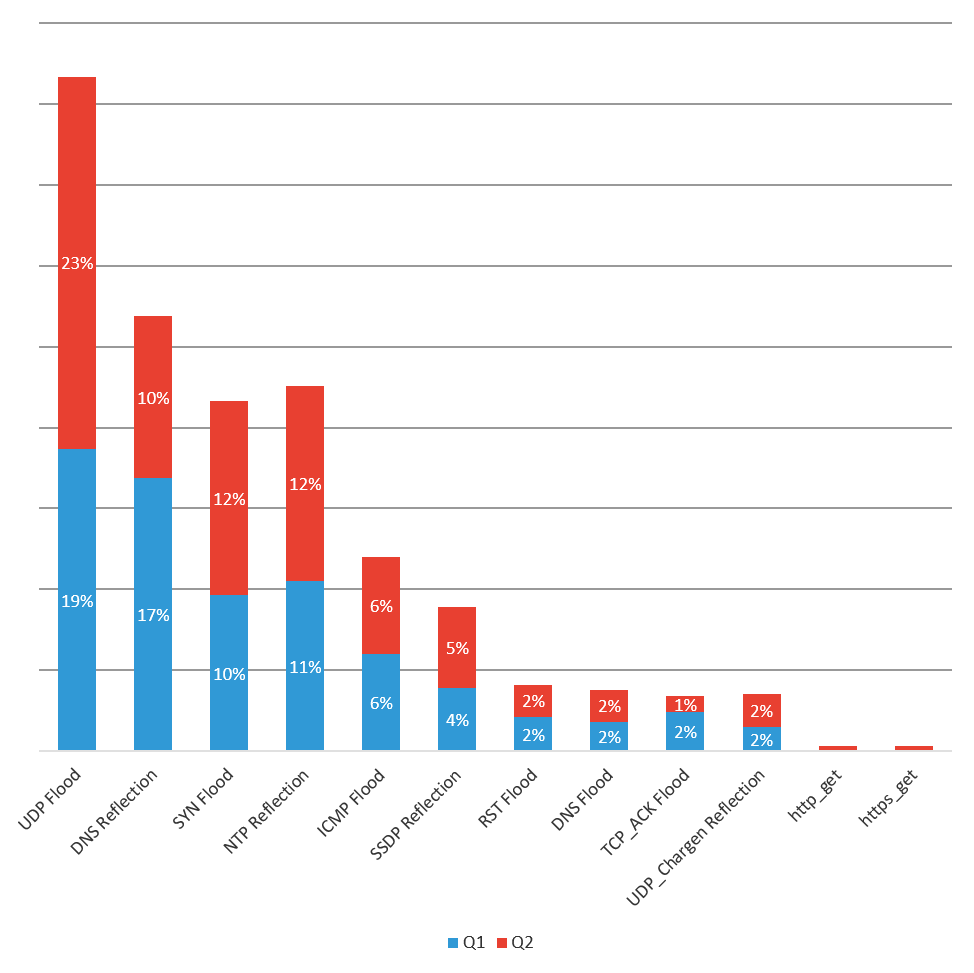
Figure 5: 2018 DDoS attacks mitigated by F5 SOC by type, Q1 and Q2 2018
DDoS Attack Count by Category
Volumetric attacks are still the most popular category of DDoS attack, followed by reflection and then fragmented attacks. Application-targeted attacks stayed flat at 2% of all DDoS attacks mitigated by the F5 SOC in Q2 2018. Even though application targeted attacks are only 2% of the total, their impact is being felt just as much as the other attack categories.
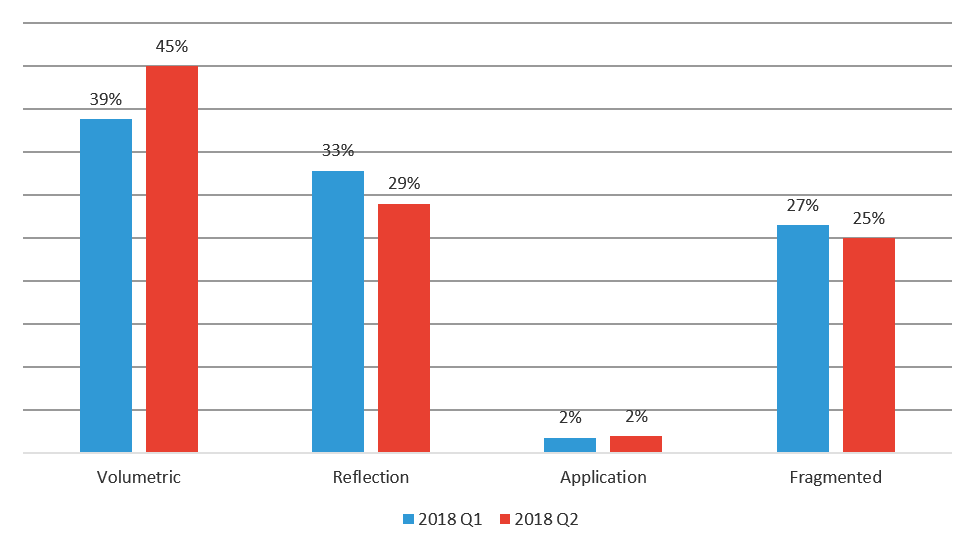
Figure 6: DDoS attacks mitigated by F5 SOC by category, Q1 and Q2 2018
Special attention should be paid towards the emergence of application-targeted DDoS attacks. Application attacks are more precise and require traffic scrubbing versus the typical blocking of unwanted port traffic at the network layer. Although DDoS attacks against applications are still rare, this new and evolving attack method is introducing additional complexity for customers who are struggling to mitigate DDoS attacks.
F5’s SIRT assists any F5 customer with a valid support contract who is under cyber attack. In an emergency, the SIRT routinely assists customers whether they have F5 DDoS products in place or not. Almost 50% of the DDoS attacks they helped customers with in 2017 were application-targeted attacks compared to 3% of the total DDoS attacks the SOC mitigated. In 2018, application-targeted attacks were 30% of the total DDoS attacks the SIRT helped F5 customers with, compared to 2% of the total DDoS attacks observed by the SOC. Although application-targeted DDoS attacks are a small percentage of total attacks launched, customers are clearly struggling to mitigate these attacks on their own because they account for nearly a third of all DDoS calls to F5’s SIRT.
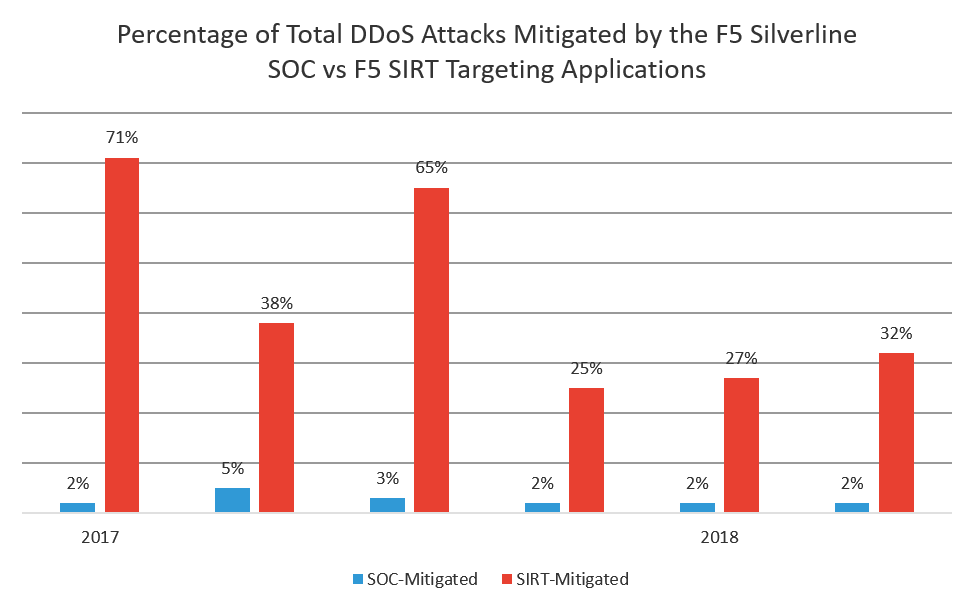
Figure 7: Percentage of total application-targeted DDoS attacks mitigated by the F5 SOC and F5 SIRT
Mitigating DDoS Attacks
Given that kids in basements can create devastating thingbots that can take down email service providers like ProtonMail (and challenge the DDoS mitigation services that protect them), everyone should be planning now for DDoS attacks to come at frequencies and rates yet unseen, and with possibly devastating financial impacts.
To limit the number of systems available to compromise that then turn around and launch DDoS attacks:
Limit remote administration to a management network, not the entire Internet.
Ensure secure remote access methods are implemented. Always change vendor default credentials and make use of VPN tunnels and SSH keys.
To fight brute force attacks, implement rate limiting and account lockout policies.
Manage vulnerabilities on Internet-facing systems and secure all applications with a web application firewall.
All organizations need a DDoS strategy. To help determine the right DDoS solution for your organization, use the following decision-making criteria:
Determine the frequency with which you get hit (or might get hit) with DDoS attacks.
- If you have not yet experienced a DDoS attack, measure your chance of attack against your industry peers.
- If your industry is not listed in our industry target charts, use the $550,000 – $50 million attack impact to determine whether your business can survive the cost of one attack.
Evaluate your skillsets and ability to defend against a DDoS attack.
- Beyond high-rate, volumetric attacks, low-rate, multi-vector attacks cause problems with application latency and can be troublesome to mitigate without expert DDoS defenders. Do you have an in-house team of expert DDoS defenders?
- Application-targeted attacks are on the rise and often need DDoS and application experts to mitigate. Although they account for less than 10% of the attacks we see, almost 50% of Security Incident Response Team (SIRT) support calls are for DDoS assistance.
Know your network limits.
- What size of pipes do you have coming into your network or networks? Your DDoS attack capacity peaks at your network capacity.
Based on these three factors, choose the right DDoS solution for your business, and consider the fact that any solution you choose must have proactive botnet defense. Without it, no network or systems stand a chance against a devastating thingbot attack.
On-premises solution
- Attack frequency: For organizations that get attacked a lot and is therefore more cost effective to mitigate internally vs paying a scrubbing service
- Ability to defend: For organizations that have in-house DDoS mitigation expertise
- Network Capacity: For organizations with large network circuits capable of sustaining high-rate attacks
Hybrid solution (combination of on-premises and automation to cloud scrubbing)
- Attack frequency: For organizations that get attacked enough at rates within their network capacity to warrant an on-premises solution, but also want the additional capacity and expertise of a scrubbing service on hand.
- Ability to defend: For organizations that have expertise on hand but might need assistance with application-targeted attacks or various other low-rate, complex, multi-vector attacks.
- Network Capacity: For organizations that can handle less than 10 Gbps but need assistance thereafter.
Outsourced scrubbing service
- Attack frequency: For organizations that don’t anticipate being attacked enough to warrant on-premises or hybrid solutions.
- Ability to defend: For organizations that do not have expertise in-house.
- Network Capacity: For any organization (except those that choose a hybrid solution) that cannot withstand a multi-Tbps attack.


