HTTPS, the protocol that secures the web, is broken. Okay, maybe not entirely broken. But it is constantly teetering on a knife edge. The Internet, although developed to be entirely open, now depends on Transport Layer Security (TLS) to securely deliver websites and other web-based services. However, as we recently highlighted in our 2019 TLS Telemetry Report, a surprising number of the world’s most popular sites have HTTPS configuration issues that can lead to passive and active attacks against unsuspecting victims. Thousands of websites still offer vulnerable cryptographic ciphers, such as RC4, and almost 4 percent of sites in the Alexa top 1 million still offer the broken SSLv3 protocol. Many more fail to take advantage of updates to TLS and other supporting protocols that can help close the security gaps that TLS leaves open.
To get started with Cryptonice visit the Github repository at https://github.com/F5-Labs/cryptonice.
Why Do We Need to Monitor HTTPS?
Well, the TLS protocol is relatively complex and not well understood. A simple TLS connection is composed of three core components:
- Handshake: in which a client and server must agree on the cryptographic algorithms and keys to use
- Certificates: digitally signed documents that provide authenticity and trust ensure each party is communicating with the entity they believe they are
- Record protocol: responsible for encrypting the actual communications between each system
Each of these components has its own set of protocols, ciphers, standards, key sizes, and nuances— and yet this is still a hugely simplified view that doesn’t consider the numerous other factors that make up a successful TLS connection. It’s not surprising, therefore, that many organizations seeking to deploy a secure HTTPS site simply install a certificate, quickly check that an HTTPS connection can be made, and then walk away. Job well done.
However, the TLS protocol is constantly evolving and additional protocols have emerged that help to close the door on some potential threat vectors, particularly when a client and server first connect and perform the handshake. Since many organizations do not regularly review their TLS deployments, these improvements and additional tools are never used.
Almost 4 percent of sites in the Alexa top 1 million still offer the broken SSLv3 protocol
Introducing Cryptonice

F5 Labs believes that everyone should have strong and well configured HTTPS connections to their sites, whether on the web or deployed internally within an organization. We also believe that Crypto should be, well, nice, not harmful or intimidating.
To help developers, application owners and infrastructure engineers to accomplish this F5 Labs is releasing its new publicly available tool, Cryptonice.
Cryptonice is a command-line tool and Python library that allows a user to examine the TLS configuration, certificate information, web application headers and DNS records for one or more supplied domain names.
Using default arguments Cryptonice will scan the target site on port 443, check for port 80 to 443 redirects, look for DNS CAA records, test the TLS connection and certificate and check for the availability of HTTP/2.
Cryptonice scans TLS configurations, certificates, web application headers and DNS records.
Why Use Cryptonice?
There are many tools available for scanning and analysing the results of TLS and HTTPS configurations. In fact, many of them are web based and do not need to be downloaded. So why use Cryptonice over these services? Cryptonice is aimed at solving these sorts of problems:
- A security team wants to view scans of multiple websites without having to submit and wait for individual requests to web-based services.
- A developer wants to scan an internal test site that is not publicly accessible.
- An internal auditor wants a complete picture of HTTPS deployment, not just TLS and certification details.
- A developer team lead wants to produce detailed analysis with recommended practices for improving the TLS configuration.
- DevOps engineers want to integrate HTTPS checking into a development pipeline so that APIs can test HTTPS configurations, with results automatically fed back into the loop.
How Do I Use Cryptonice?
Cryptonice is provided as a standalone Windows executable, a pre-built Python command-line tool, and even a Python library. This rest of this article briefly covers basic use of the command line tool. For information on how to build your own scripts using the Cryptonice library, keep an eye out for a soon to be released Cryptonice developer guide on the DevCentral site.
Installing Cryptonice
If you have Python 3 installed, then the easiest way to use the tool is to install using pip install as shown in Figure 1.
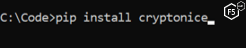
Figure 1. Installing Cryptonice using the Python installer pip
At this point pip installs Cryptonice along with all necessary third-party libraries. If all goes well, you should see something similar to Figure 2:
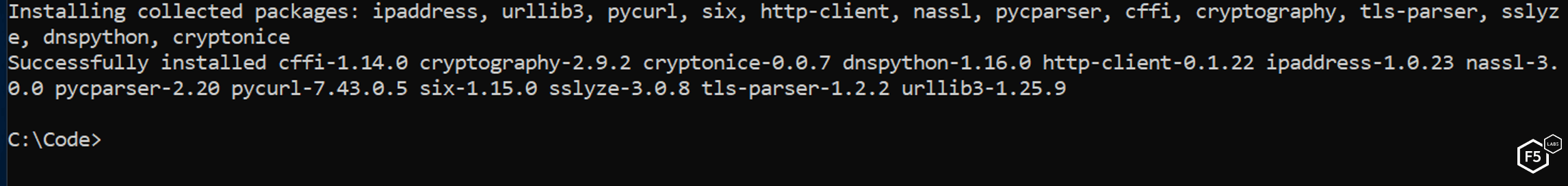
Figure 2. A successfully completed installation of Cryptonice via pip
Should you wish to grab the standalone executable file then visit the releases section of the Cryptonice tool on Github.
Going forward, use of the standalone executable and the pip installed version is the same.
Using Cryptonice
If you run Cryptonice without any arguments, you will be able to see the list of all possible parameters, as shown in Figure 3.
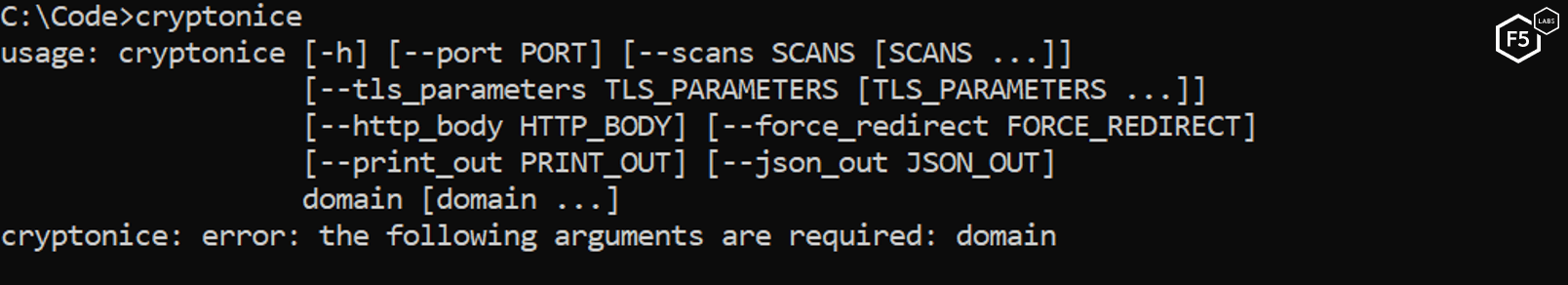
Figure 3. Running Cryptonice with no parameters displays the available options
Basic use of Cryptonice couldn’t be easier. Simply type the command and then a destination website that you wish to scan, as show in Figure 4:
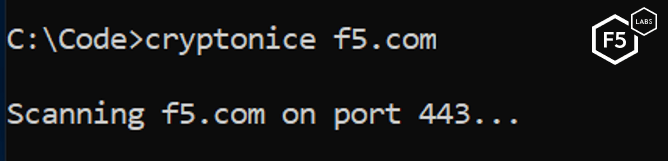
Figure 4. Performing a basic Cryptonice scan against f5.com using default parameters
Viewing the Results
Using the tool at the command line displays an overview of the results in the console. This output shows basic protocol and cipher support, information about HTTP redirects and some information about the DNS records and certificate information, as shown in Figure 5:
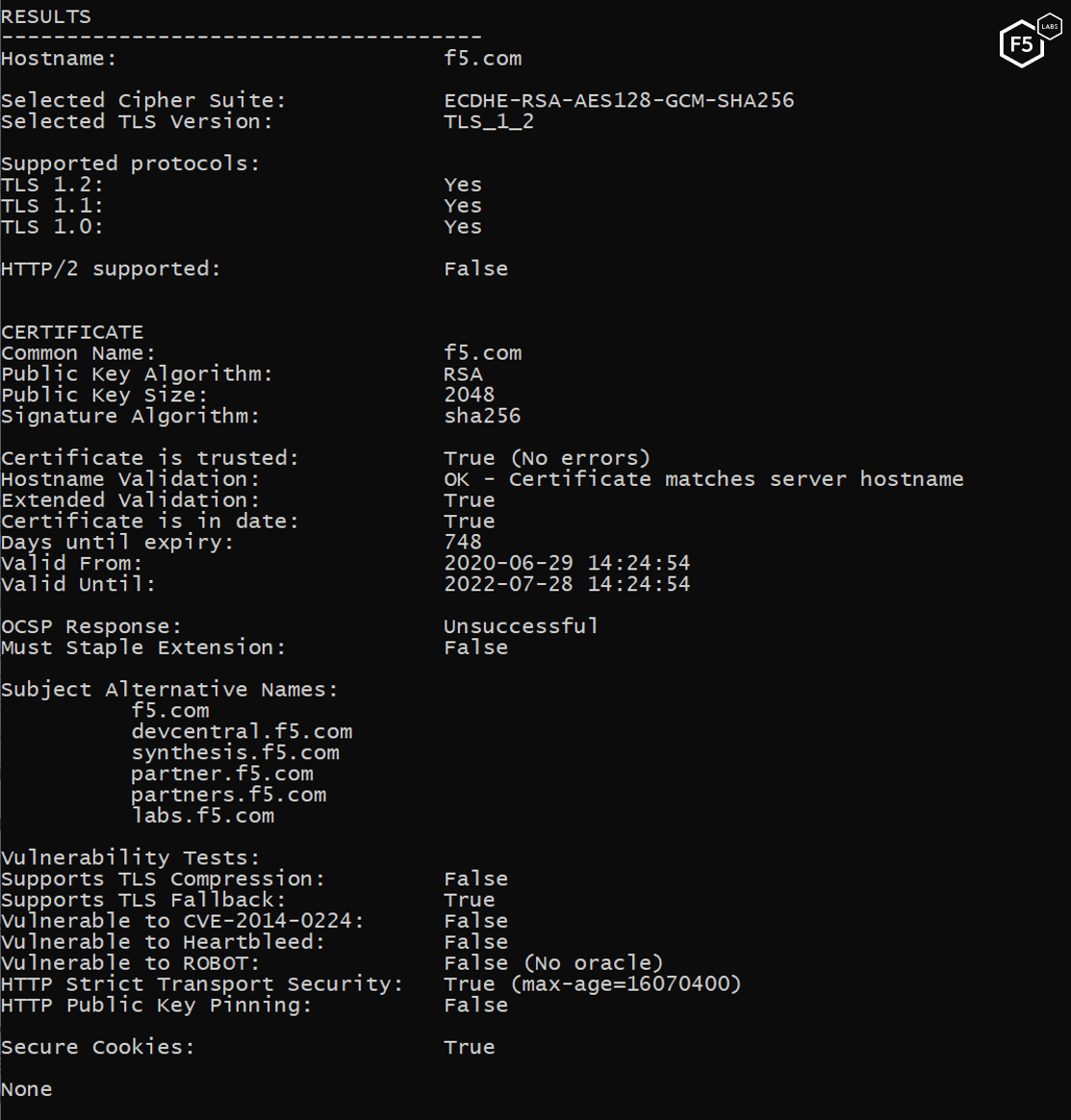
Figure 5. Viewing the Cryptonice scan results for f5.com
In addition to the console output, the full report is saved to a JSON file. This JSON output, as shown in Figure 6, is far more detailed than the command-line results so it is useful to examine it carefully. The JSON file is compliant with RFCs 8259, 7159 and 4627 as well as the ECMA-404 standard. Output is single-line and optimised for further scripting or automation so human readability is difficult.
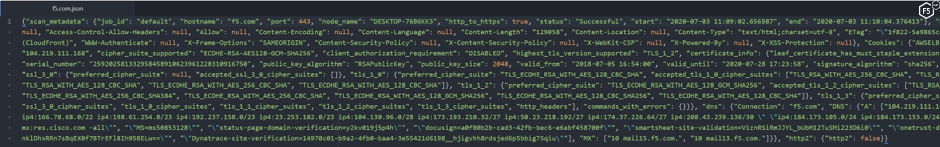
Figure 6. Viewing the JSON output of a Cryptonice scan
For human readability we recommend the use of a JSON formatter which displays indented JSON over multiple lines, as shown in Figure 7.
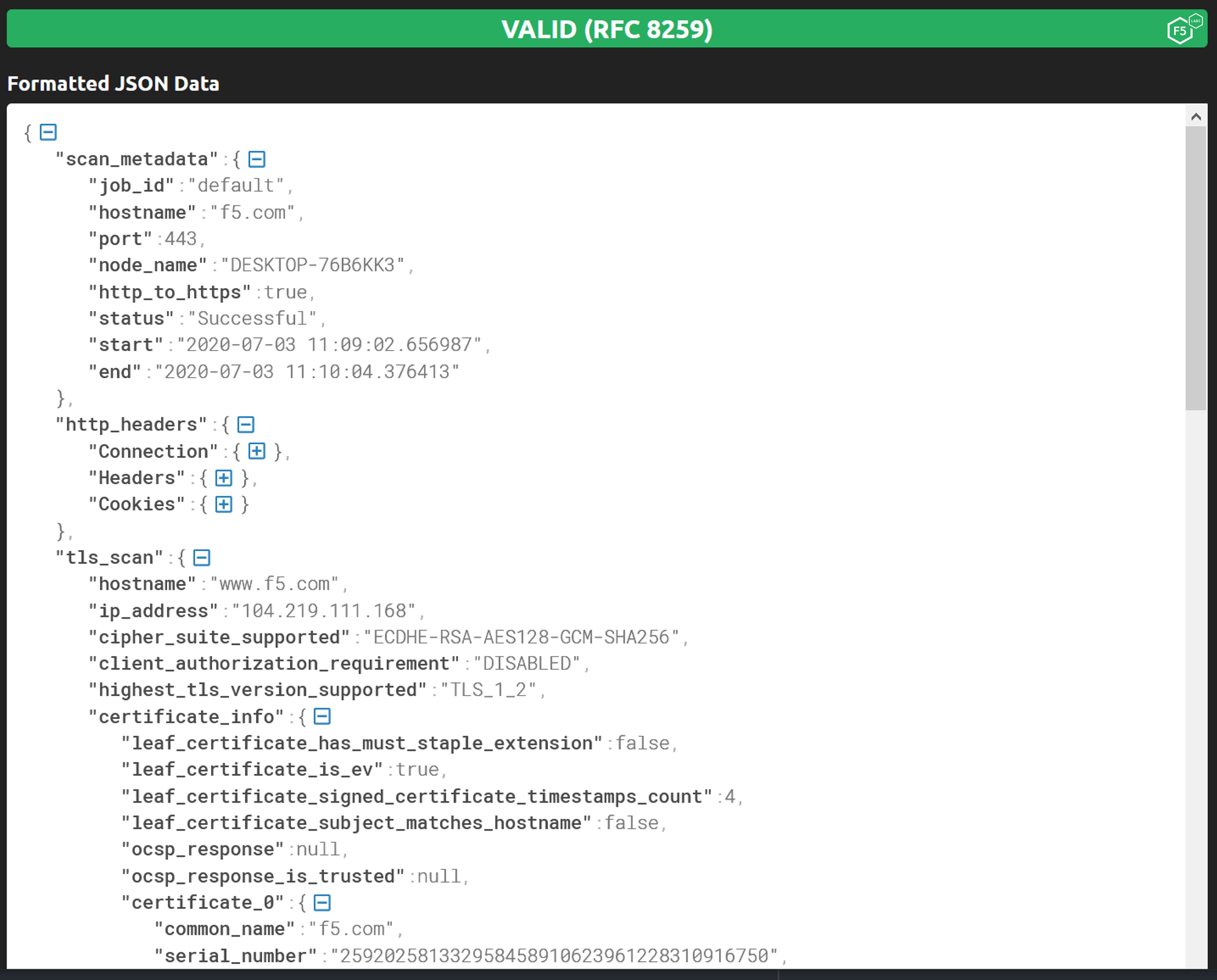
Figure 7. Viewing same output as seen in Figure 6 using a JSON formatter (Source: https://jsonformatter.curiousconcept.com)
Using Cryptonice to Find Configuration Problems
Let’s look at a few examples of how to use Cryptonice to spot real-world problems with TLS configurations.
The first example in Figure 8 shows a number of security concerns with this website. The site is using a long 4096-bit RSA key with their certificate (1), which is great! However, the list of protocols also shows that SSL v3 is supported which presents a serious weakness to this site (2). In the Recommendations section Cryptonice shows a CRITICAL warning for SSLv3 and shows additional High warnings for the use of weak ciphers (3). The full list of ciphers this site supports is visible in the JSON output for this scan.
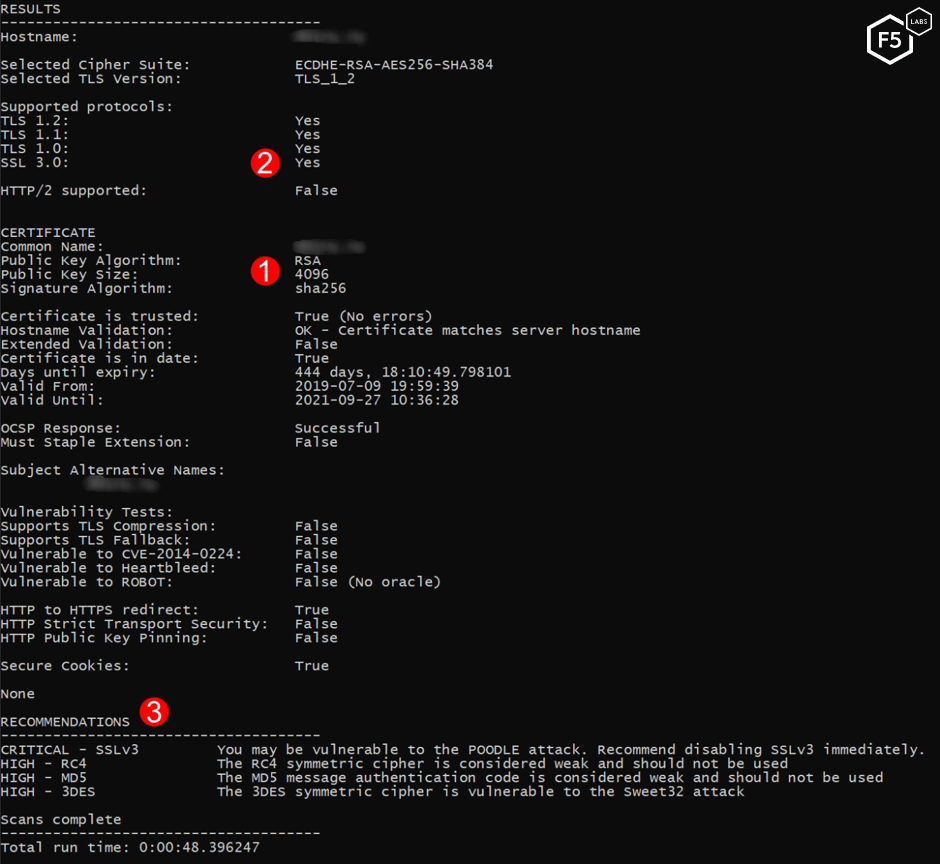
Figure 8. Using Cryptonice to find weak protocols and ciphers
Figure 9 shows the results of a scan against a site with an expired certificate. This is represented in a number of places in the Results and Recommendations sections. The entire certificate chain is tested for errors and, in this case, shows False (1). We can also see a negative number of days left for this certificate, indicating that the certificate ‘Valid Until’ date has passed (2). Finally, we see a CRITICAL warning, making it clear to us that this certificate has expired (3).
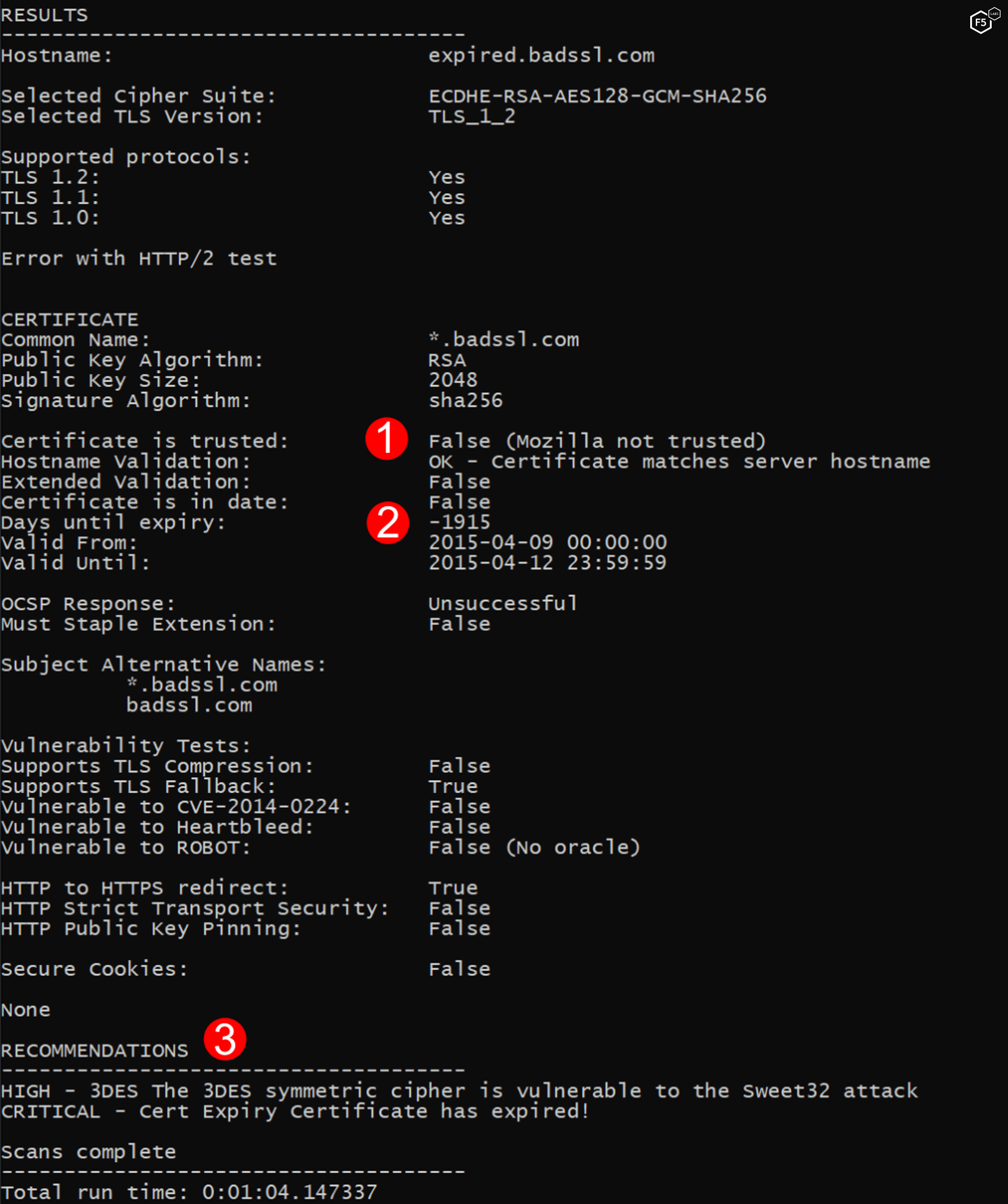
Figure 9. Using Cryptonice to detect expiring certificates
Cryptonice can be used to identify and alert to many different configuration problems, including:
- Legacy protocols and ciphers
- Short key lengths
- Invalid, expired, or untrusted certificates
- HTTP/2 and HTTP/3 support
- Some TLS vulnerabilities
- TLS related HTTP headers
- DNA CAA records
Should you wish to customize the content of your scan, specific options can be provided to select scan types (TLS, HTTP, HTTP2, DNS), parameters for a TLS scan (certificate information, accepted cipher suites, vulnerability tests), protocol redirection tests and output generation. These options are documented on the F5 Labs Github page:
https://github.com/F5-Labs/cryptonice
The Future of Cryptonice
We’re excited about the first version of our tool but we’re even more excited about its future. We plan to add additional modules to query Certificate Transparency logs, test for protocols such as HTTP/3, and produce detailed output with clear guidance on how to improve your cryptographic posture on the web.
However, this is version 1.0 and in the true spirit of open-source software, we encourage users to submit bugs on our GitHub page, and we encourage everyone to fork and submit pull requests for fixes and new features so that everyone can benefit from them.
We’re excited about the first version of our tool but we’re even more excited about its future.


