First detected in May 2018,1 DanaBot is a banking trojan that has since shifted its targets from banks in Australia to banks in Europe, as well as global email providers such as Google, Microsoft and Yahoo for the holiday phishing season (/content/f5-labs-v2/en/labs/articles/threat-intelligence/2018-phishing-and-fraud-report--attacks-peak-during-the-holidays.html). Eighty-eight percent of DanaBot’s targets between November 7 and December 4, 2018 were banking customers, primarily in Italy, followed by Poland and Germany, according to an F5 SOC Research project for Websafe that analyzed active campaigns between November 7 and December 4, 2018.
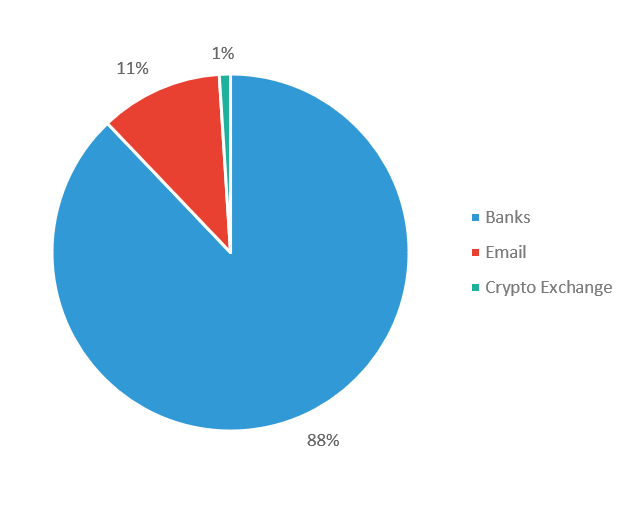
Figure 1: DanaBot industry targets November 7 - December 4, 2018
DanaBot authors have been running four primary campaigns that target the following:
The main campaign targeted multiple countries and industries, including banks, email providers, and a bitcoin exchange, primarily in Italy, followed by Poland, Germany, Austria, Switzerland, and the Netherlands.
The second most active campaign targeted German banks.
The third most active campaign targeted Polish banks.
The fourth most active campaign targeted one Australian bank.
The main multi-industry and country-targeted campaign appeared consistently during the month of November. The other dedicated campaigns were found in parallel but only on specific days rather than day after day. November 21, 2018 was the only day we saw all four campaigns active.
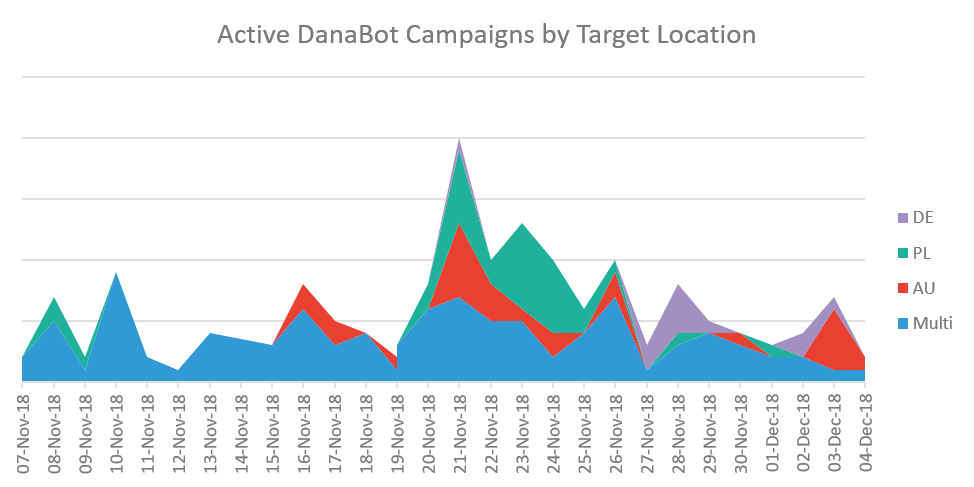
Figure 2: DanaBot campaign activity by day and targets
When looking at all targets by country across all campaigns, it’s clear that DanaBot authors are focused on Italian targets, followed by targets in Poland and Germany. The targets attributed to the US are large email service providers that are used globally.
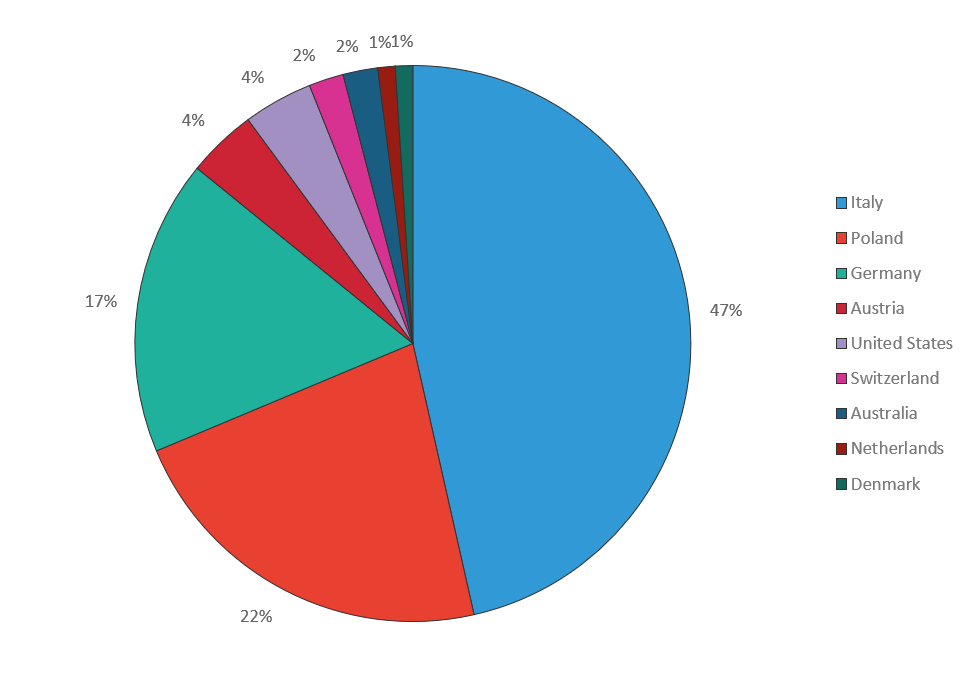
Figure 3: DanaBot Targets by Country
Multiple Campaign Targets
The following banks were targeted in this campaign, organized by country (note some banks have a presence in many countries, however, attackers reveal their intended targets when specifying a country-specific banking URL):
| URL | Country | Business |
| https://geb.bankaustria.at/*" | Austria | Bank Austria |
| https://banking.raiffeisen.at/*" | Austria | Raiffeisen Bank |
| https://mein.elba.raiffeisen.at/*" | Austria | Raiffeisen Bank |
| https://*.at/banking/*" | Austria | Unknown |
| https://ibanking.wsk-bank.at/*" | Austria | WSK Bank |
| https://www.bv-activebanking.de/*" | Germany | BV-Active Banking |
| https://kunden.commerzbank.de/banking/*" | Germany | Commerz Bank |
| https://meine.deutsche-bank.de/trxm/*" | Germany | Deutsche Bank |
| https://banking.fidor.de/*" | Germany | Fidor Bank |
| https://banking.spard*de/spm/*" | Germany | Sparda Bank |
| https://banking.bancaeuro.it/newvir/*" | Italy | Banca Euro |
| https://bancoposta.poste.it/*" | Italy | Banco Posta |
| https://bancopostaimpresaonline.poste.it/*" | Italy | Banco Posta |
| https://www.banking4you.it/*" | Italy | Banking4You |
| https://www.banking4you.it/*htm*" | Italy | Banking4You |
| https://banking.bnl.it/*" | Italy | BNL Bank |
| https://business.bnl.it/bway*" | Italy | BNL Bank |
| https://business.bnl.it/bway*=*" | Italy | BNL Bank |
| https://ibk.icbpi.it/*" | Italy | BPER Bank |
| https://ibk.icbpi.it/ibk/*/movimenti*" | Italy | BPER Bank |
| https://ibk.icbpi.it/ibk/*=*" | Italy | BPER Bank |
| https://ibk.icbpi.it/ibk/*id=internationalbeneficiary_WAR*" | Italy | BPER Bank |
| https://ibk.icbpi.it/ibk/*id=pagamenti_WAR_webcontocutilitiesportlet*" | Italy | BPER Bank |
| https://youweb.bancobpm.it/WEBHT/*" | Italy | BPM Bank |
| https://youwebcard.bancopopolare.it/WEBHT/*" | Italy | BPM Bank |
| https://www.chebanca.it/portalserver/*" | Italy | CHE Bank |
| https://www.chebanca.it/portalserver/homebanking/*" | Italy | CHE Bank |
| https://banking.credem.it/newvir/*" | Italy | Credem Bank |
| https://banking-imprese.credem.it/*" | Italy | Credem Bank |
| https://www.credem.it/*" | Italy | Credem Bank |
| https://nowbanking.credit-agricole.it/*" | Italy | Credit Agricole Bank |
| https://nowbankingprivati.cariparma.it/*" | Italy | Credit Agricole Bank |
| https://www2.csebo.it/webcontoc/css/*/stile.cs*" | Italy | CSE Bank |
| https://www2.csebo.it/webcontoc/js/varMultiLingua*.j*" | Italy | CSE Bank |
| https://dbonline.italy.db.com/portalserver/*" | Italy | Deutsche Bank |
| https://www.bancagenerali.it/*" | Italy | Generali Bank |
| https://www.bancagenerali.it/*htm*" | Italy | Generali Bank |
| https://carigeonline.gruppocarige.it/wps8ib/myportal/*" | Italy | Gruppo Carige Bank |
| https://www.gruppocarige.it/vbank/*" | Italy | Gruppo Carige Bank |
| https://www.gruppocarige.it/wps/myportal/*" | Italy | Gruppo Carige Bank |
| https://banking.hellobank.it/*" | Italy | Hello Bank |
| https://www.inbank.it/*" | Italy | Inbank |
| https://securecca.ing.it/*" | Italy | ING Bank |
| https://www.intesasanpaolo.com/ib/content/static/*" | Italy | Intesa San Paolo Bank |
| https://www.intesasanpaoloprivatebanking.com/script/*" | Italy | Intesa San Paolo Bank |
| https://icb.mps.it/av1/cbl/exec/*" | Italy | MPS Bank |
| https://www.bancaprossima.com/script/*" | Italy | Prossima Bank |
| https://www.relaxbanking.it/newrelax1/*" | Italy | Relax Bank |
| https://scrigno.popso.it/ihb/run*" | Italy | Scrigno Bank |
| https://www.ubibanca.com/logou*" | Italy | UBI Bank |
| https://www.ubibanca.com/qu*" | Italy | UBI Bank |
| https://www.ubibanca.com/qui/nav/bonifico/*" | Italy | UBI Bank |
| https://e-bank.*agricole.p*" | Poland | Agricole Bank |
| https://system.aliorbank.*" | Poland | Alior Bank |
| https://login.bgzbnpparibas.pl/*" | Poland | Bank BGZ BNP Paribas |
| https://bosbank24.pl/corpo_web/auth/login*" | Poland | BOS Bank |
| https://ebo.*.pl/*" | Poland | EBO Bank |
| https://korporacja.gb24.pl/*" | Poland | GB24 Bank |
| https://ibiznes24.pl/*" | Poland | IBiznes24 Bank |
| https://www.ipko.pl*" | Poland | iPKO Bank |
| https://login.nestbank.pl/log*" | Poland | Nest Bank |
| https://online.nestbank.pl/bim-webapp/nest/log*" | Poland | Nest Bank |
| https://plusbank24.pl/web-client/logi*" | Poland | Plus 24 Bank |
| https://moj.raiffeisenpolbank.co*" | Poland | Raiffeisen Bank |
| https://sgbonline.sgb.p*" | Poland | SGB Bank |
| https://system.t-mobilebankowe.pl/web/logi*" | Poland | T-MOBILE Bankowe |
| https://biznes.toyotabank.pl/*" | Poland | Toyota Bank |
| https://ebanking.raiffeisen.ch/entry*" | Switzerland | Raiffeisen Bank |
| https://login.portal.citidirect.com/portalservices/forms/*" | US | Citi Bank |
The authors also targeted the following email services and platforms of major technology and entertainment providers across Europe and the US:
| URL | Country | Business |
| https://*.gmx.net/mail/*" | Germany | GMX |
| https://home.navigator.gmx.net/home/show*" | Germany | GMX |
| https://mail.vianova.it*" | Italy | Vianova |
| *.webmail.libero.it*Main* | Italy | Libero |
| https://mail.tecnocasa.it*" | Italy | Tecnocasa |
| https://qweb.quercia.com/*.as*" | Italy | Quercia |
| https://*.bluewin.ch/*/main_swissco*" | Switzerland | Bluewin |
| https://mail.one.com/*" | Unknown | One |
| https://mail.google.*" | US | |
| https://outlook.live.com/*" | US | Microsoft |
| https://mail.yahoo.*" | US | Yahoo |
The following crypto-exchange out of the Netherlands was also targeted:
| URL | Country | Business |
| https://bitbay.ne*" | Netherlands | BitBay |
Germany Campaign Targets
The following businesses were targeted in the Germany campaign:
| URL | Location | Business |
| https://*banking.berliner-bank.de/trxm*" | Germany | Berlin Bank |
| https://*banking.sparda-*" | Germany | Sparda Bank |
| https://*banking.sparda.de*" | Germany | Sparda Bank |
| https://*banking.sparda.de/wps/loggedout.jsp", | Germany | Sparda Bank |
| https://*comdirect.de/lp/wt/login*" | Germany | Com Direct Bank |
| https://*commerzbank.de*" | Germany | Commerz Bank |
| https://*kunde.comdirect.de*" | Germany | Comdirect bank |
| https://*meine.deutsche-bank.de/trxm/db*" | Germany | Deutsche Bank |
| https://*meine.norisbank.de/trxm/noris*" | Germany | Noris Bank |
| https://*targobank.de*" | Germany | Targo Bank |
Poland Campaign Targets
All of the identifiable targets in this campaign are banks.
| URL | Location | Business |
| https://system.aliorbank.*", | Poland | Alior Bank |
| https://login.nestbank.pl/log*", | Poland | Nest Bank |
| https://online.nestbank.pl/bim-webapp/nest/log*", | Poland | Nest Bank |
| https://plusbank24.pl/web-client/logi*", | Poland | Plus Bank 24 |
| https://moj.raiffeisenpolbank.co*", | Poland | Raiffeisen Bank |
| https://www.centrum24.pl/centrum24-web/*", | Poland | Santander Bank |
| https://system.t-mobilebankowe.pl/web/logi*", | Poland | T-Mobile Bank |
Australian Campaign Targets
The Australian campaign targeted one bank over two URLs:
| URL | Location | Business |
| https://*my.commbank.com.au/netbank*" | Australia | Comm Bank |
| https://*my.commbiz.commbank.com.au*" | Australia | Comm Bank |
DanaBot is using the same webinject pattern used in the past by Tinba and Gozi, as we reported in May 2016. This same webinjection infrastructure behavior by DanaBot, Tinba, and Gozi strongly supports our claim in our previous article that a great deal of fraud business logic is now implemented in JavaScript and contained in the webinjects.
Note this example of a script used in both Tinba and Gozi in 2016. Both use the same element names and injection routine:
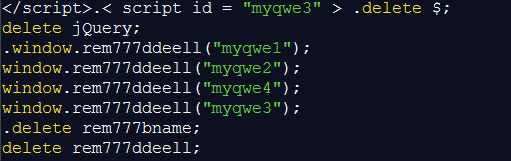
Figure 4: Tinba and Gozi injection routine, 2016
In Gozi 2016, the malware is using a placeholder @ID@, probably for the BOT-ID, in script id valued as myjs3. DanaBot is using the actual BOT-ID in script id valued as myjs3.
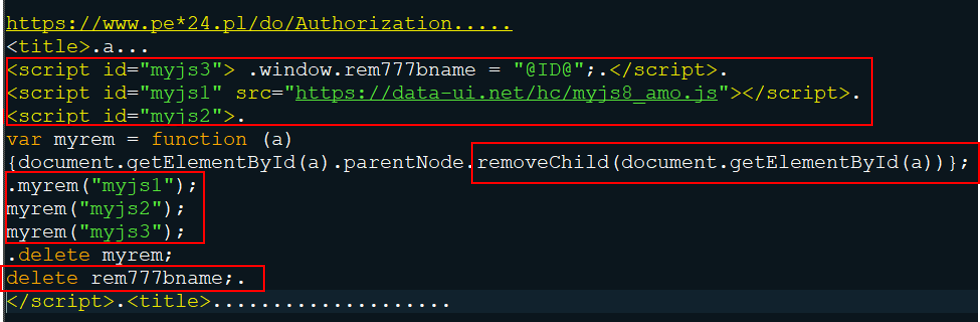
Figure 5: Webinject used in Gozi, 2016
Now, compare that to this example used recently in DanaBot. In Gozi 2016, the malware is injecting a JavaScript named myjs8_amo.js onto the injected user page. DanaBot malware is using an injected script named myjs28_frr_w1.js. In order to mask its activity on the injected page, the malware removes suspicious scripts immediately after execution by using removeChild and getElementById.
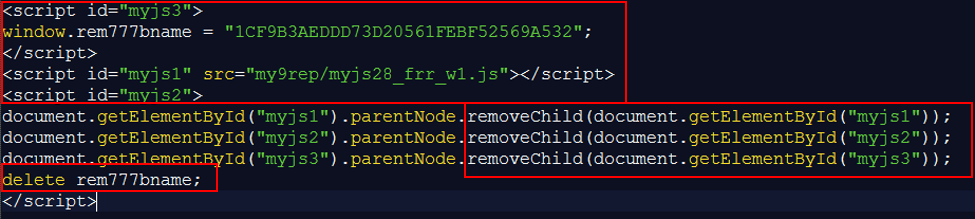
Figure 6: Webinject used in DanaBot, November 2018
Conclusion
As with all banking trojans, DanaBot actively updates its campaign targets to both avoid detection and maintain continual operations to optimize the attacker’s financial reward. We are not surprised to see a geographically diverse range of targets during the peak holiday phishing and fraud season. However, what is notable is the focus on European banks, most specifically the Italian banks.
While we do not know who is maintaining this malware, the threat actors are using the same injection patterns as those used by older, successful banking trojans like Gozi and Tinba. Given this progression, we wouldn’t be surprised if this malware continued its increased activity in 2019.
All organizations, especially the known targets identified in this article, should make their customers aware that they are being targeted through phishing and spam campaigns. The main purpose of these campaigns is to plant malware on their machines that is designed to steal money from their bank accounts and gain access to their email.
To combat the impact of fraudulent transactions occurring as the result of malware-infected customer machines, organizations should implement fraud detections within their web platforms that can detect banking trojans and block resulting fraudulent transactions. For more details on how to combat phishing attacks that lead to fraud, see F5 Labs’ 2018 Phishing and Fraud Report (/content/f5-labs-v2/en/labs/articles/threat-intelligence/2018-phishing-and-fraud-report--attacks-peak-during-the-holidays.html).


