Introduction
Last month’s Sensor Intel Series for March 2024 uncovered the explosion in traffic hunting for systems affected by CVE-2023-1389. The flaw which related to TP-Link Archer AX21 Wi-Fi routers has quickly become the new darling of threat actors looking to build out their DDoS botnets.
No new signatures have been introduced this month. Instead, we worked with F5 Threat Campaigns to dig for vulnerabilities without associated CVEs.1
- Threat attackers continue their explosive build out of botnets by exploiting CVE-2023-1389
- This TP-Link router vulnerability continues to grow rapidly, accounting for 40% of all scanning activity in April 2024
- Just seven CVE’s, including the TP-Link vuln, are responsible for almost 80% of all malicious traffic hitting Efflux sensors
- CVE-2020-11625, which afflicts the JetBrains YouTrack application, continues its decline. Once in the top spot only a few months ago, this now sits at number five in our Top CVE list.
- A remote code execution (RCE) vulnerability with an unassigned CVE is affecting Netgear DGN1000 devices. Whilst unspotted in sensor traffic this is currently the top exploited vulnerability being observed on the F5 Threat Campaigns map.
Malicious Internet Scanning in April 2024
While total scanning traffic is down by almost a third compared with this time last year, it is clear that the traffic which remains is highly focused on seeking out vulnerable IoT devices to subsume into a botnet.
Building DDoS Botnets with TP-Link and Netgear Routers
As we reported in March 2024, CVE-2023-1389 has seen rapid growth in related scanning activity, and that trend only continued in April 2024. This command injection vulnerability in the firmware for the TP-Link Archer AX21 Wi-Fi router accounts for 40% of all traffic hitting our sensors. Exploit code for this CVE indicates that attackers are taking over weak IoT devices to include in Mozi botnets.2
The Mozi DDoS Botnet
Mozi has been linked to a wide number of vulnerable IoT devices, including routers from Netgear, Huawei, D-Link, GPON, and TP-Link.3 The Mozi botnet uses a peer to peer (P2P) method of communication similar to that found in the popular Torrent protocol. The use of P2P networking and encrypted communication using ECDSA384 allows the botnet to hide the payload of malicious traffic and protect the integrity of the bot’s network.
The Mozi botnet is believed to focus its efforts almost exclusively on distributed denial of service (DDoS) floods, and is able to launch HTTP, TCP, UDP, and other attacks.
CVE-2023-1389 and TP-Link devices are not entirely to blame for the rapid growth of this botnet, however. Netgear devices have also been found to be widely exploited and while CVEs have been issued for some devices, such as CVE-2016-6277, some have not.4 The F5 Threat Campaigns Map shows heavy exploitation of the Netgear DGN1000 WiFi router, showing activity from 15 unique locations over the world.5 Along with active botnet activity targeting Netgear devices, Threat Campaigns is also tracking other active exploitation of GPON routers, also linked to the Mozi botnet. GPON vulnerability CVE-2020-8958 is, as you can tell from the CVE identifier, not especially new, but despite its age it remains in high demand by threat actors, and is still number 7 in our top attacked CVE list (Figure 1).
That the top vulnerability tracked by the Threat Campaign team does not have an assigned CVE (and does not appear in our list) is a good reminder that multiple intelligence sources should be combined to build an accurate view of the threat landscape.
Top Attacked CVEs for April 2024
The TP-Link vulnerability CVE-2023-1389 remains in the top spot for April (Figure 1) and clearly shows the extent to which this CVE overshadows all other traffic. For April 2024, the vast majority of all scanning traffic for the month, 79%, can be attributed to just seven vulnerabilities (see Table 1 for a full breakdown).
The Sankey diagram in Figure 2 is a more insightful look at the same data. It shows top attacked CVEs over time and is a useful way to quickly identify trends such as the explosion in traffic searching for CVE-2023-1389. The ramp up began in December 2023 when the vulnerability was announced and has been gaining in rank (and total traffic volume) ever since.
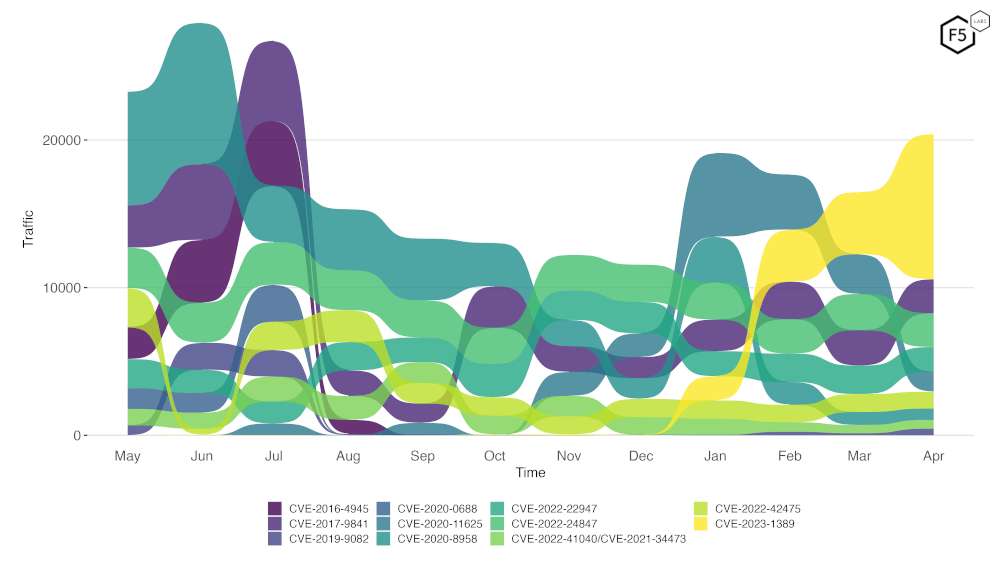
Figure 2. Top CVE scanning trends for the past 12 months.
The full list of CVEs along with traffic counts, and associated CVSS v3 and Exploit Prediction Scoring System (EPSS) scores can be found in Table 1 (Appendix). EPSS scores provide a way to predict how likely it is a given vulnerability will be seen. For those that need a refresher, check our explainer article F5 Labs Joins the Exploit Prediction Scoring System as a Data Partner.
Of the 119 vulnerabilities we tracked across April 2024, 107 had EPSS scores of 0.87 or higher, indicating high likelihood of exploitation. Of the top 10 CVEs ( Figure 1) only two had low EPSS scores. The GeoServer (JT-Jiffle) deserialization RCE (CVE-2022-24847) had a score of just 0.40609 while the JetBrains YouTrack vulnerability (CVE-2020-11625) scored only 0.46926. The low EPSS scores imply that the likelihood of encountering these exploits attempts is relatively low. This certainly corroborates our findings of the decline in traffic targeting CVE-2020-11625. However, while total volume aiming for CVE-2022-24847 is low compared with some other vulnerabilities, it is remaining consistent and shows no sign of significant decline over time.
The plots for the top attacked CVEs, shown in Figure 3, is a great way to easily identify the big changes in individual CVE exploitation. In it we can see the steady decline of CVE-2020-11625 which began in January of 2024 after its explosive growth back in November 2023.
The decline in traffic targeting CVE-2020-11625, and the drop in relative top-10 position for CVE-2022-24847 (see Figure 2, above), are likely reasons for their current low EPSS scores.
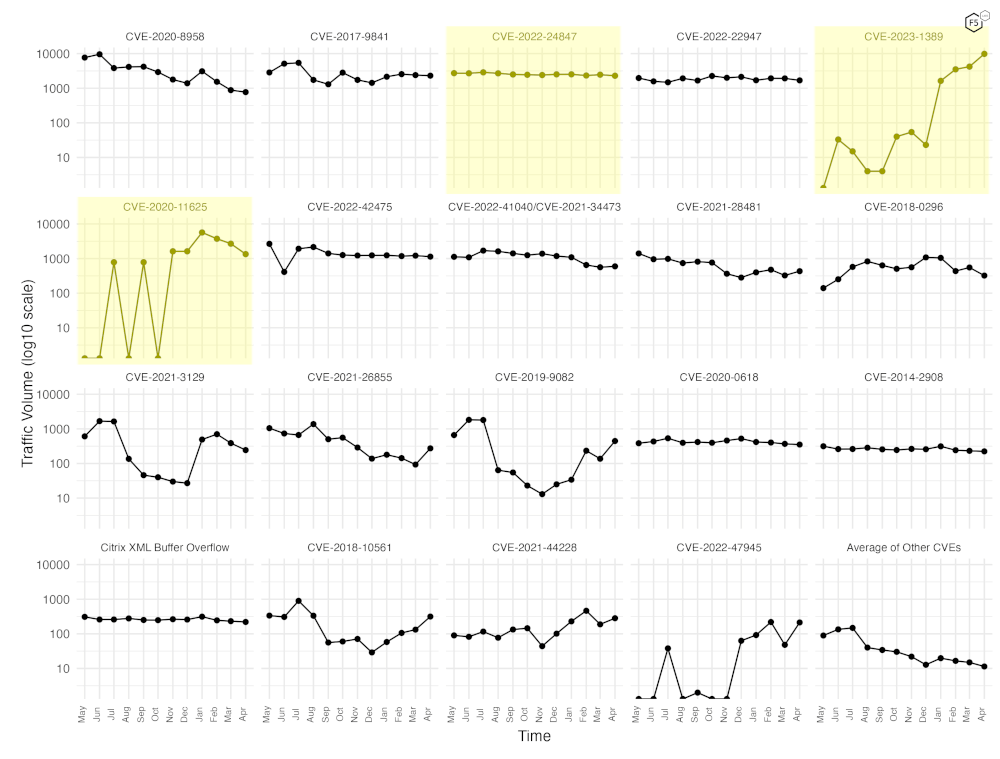
Figure 3. Individual plots per top attacked CVE in April 2024.
Table 1 contains the full count of malicious traffic volumes as well as the CVSS v3 and EPSS scores for each CVE. It’s not until we visualize the data, however, that we see the obvious pattern hiding in plain sight (Figure 4). The overwhelming majority of scanned CVEs can be attributed to high (CVSSv3 >7.0) and critical (CVSSv3 >9.0) vulnerabilities.
This seems logical. A high/critical CVSS score is typically awarded to a CVE when it is remotely accessible, and exploitable with relative ease: just the kinds of vulnerabilities that attackers love to scan for. Minimal effort, maximum reward. It is no wonder, then, that much of the scanning activity we see is targeting home routers. They are deployed en masse by ISPs, have high bandwidth connections, and commonly feature remote configuration web apps or APIs which are ripe for abuse.
Conclusion
Subsuming vulnerable IoT devices into global botnets continues to be the top activity for malicious internet wide scans. Patching against known CVEs is essential for anyone owning a vulnerable device. It is important for everyone to be aware of why these botnets continue to be built out: increasing denial of service (DoS) capabilities. Consider what DDoS defences you have and what their strengths and weaknesses are.
Appendix
This data is now also available in CSV format in the F5 Labs Github repo TopCVEs.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


