This month’s installment in F5 Labs’ monthly Sensor Intel Series focuses on vulnerability targeting trends for the month of August. As in previous editions in this series, the source for this intelligence is Efflux’s globally distributed network of sensors.
Most of the vulnerabilities that attackers scanned for in August are the same bunch that have shown up in previous months. However, last month one vulnerability showed up third in traffic rank that had not previously shown significant targeting. This is an authentication bypass vulnerability in the JAWS/1.0 web server as it exists on several digital video recorders (DVRs).1 It had previously escaped our attention, mostly because it is a vulnerability with no NVD entry or assigned CVE number, but now that we are looking for it, we see that it also took fifth place back in April 2022.
Normally we restrict this analysis to vulnerabilities with CVE numbers, but this is a particularly interesting vulnerability for two reasons: it is quite severe, and it is an IoT vulnerability with the classic IoT root cause: weak authentication. Given that last month we noted an increase in attacker scans for IoT vulnerabilities, and that the last year has seen several notable DDoS attacks, we felt that traffic targeting this vulnerability merited inclusion despite its somewhat unofficial status.
Other than this JAWS DVR vulnerability, August featured many of the same prominent vulnerabilities we’ve watched over the course of 2022: CVE-2020-8958 (another IoT vuln), CVE-2017-9841, CVE-2018-10561, and CVE-2021-28481 make up the rest of the top five for August. Figure 1 shows the volume of traffic targeting the top 10 CVEs in August.
Table 1 contains traffic counts for August and changes from July for all traffic targeting known CVEs.
| CVE Number | Count | Change (July - August) |
| CVE-2020-8958 | 5208 | -3038 |
| CVE-2017-9841 | 4486 | -1505 |
| 2018 JAWS Web Server Vuln | 2983 | 1951 |
| CVE-2018-10561 | 2248 | -2113 |
| CVE-2021-28481 | 1748 | -91 |
| CVE-2018-10562 | 1618 | -2110 |
| CVE-2019-9082 | 1453 | -1055 |
| CVE-2022-22947 | 1349 | 19 |
| CVE-2021-3129 | 1284 | -773 |
| CVE-2017-18368 | 717 | -2548 |
| CVE-2020-25078 | 545 | -3194 |
| CVE-2021-26086 | 354 | 75 |
| CVE-2021-44228 | 334 | 136 |
| CVE-2021-22986 | 128 | -319 |
| CVE-2021-41277 | 152 | -74 |
| CVE-2020-3452 | 143 | 138 |
| CVE-2022-22965 | 28 | 9 |
| CVE-2022-1388 | 27 | -20 |
| CVE-2020-9757 | 20 | 6 |
| CVE-2021-29203 | 19 | 15 |
| CVE-2022-25369 | 13 | 4 |
| CVE-2021-21315 | 12 | 10 |
| CVE-2008-6668 | 11 | 3 |
| CVE-2018-7600 | 11 | -2 |
| CVE-2021-32172 | 11 | 8 |
| CVE-2021-3577 | 11 | 3 |
| CVE-2018-7700 | 9 | 2 |
| CVE-2020-28188 | 9 | 0 |
| CVE-2019-2767 | 8 | 4 |
| CVE-2020-7796 | 8 | 2 |
| CVE-2021-33357 | 8 | 2 |
| CVE-2020-13167 | 7 | 2 |
| CVE-2018-1000600 | 6 | 4 |
Table 1. CVE targeting traffic for August, along with changes in traffic volume from July.
To compare with previous months, Figure 2 shows a bump plot of CVE traffic and rankings from January through August 2022. Note that Figure 2 is subtly different from the similar bump plots in earlier SIS articles. As the number of CVEs grew, the plot was becoming harder to read and individual vulnerabilities were becoming harder to differentiate. For this month, instead we filtered for the top five vulnerabilities per month. Because several vulnerabilities were in the top five for several months, this produced a group of nine vulnerabilities, which we then plotted across the whole duration. While this does mean that a handful of somewhat interesting CVEs aren’t being plotted (such as vulnerabilities with dramatic changes in traffic but still overall small volumes), this is much easier to read.
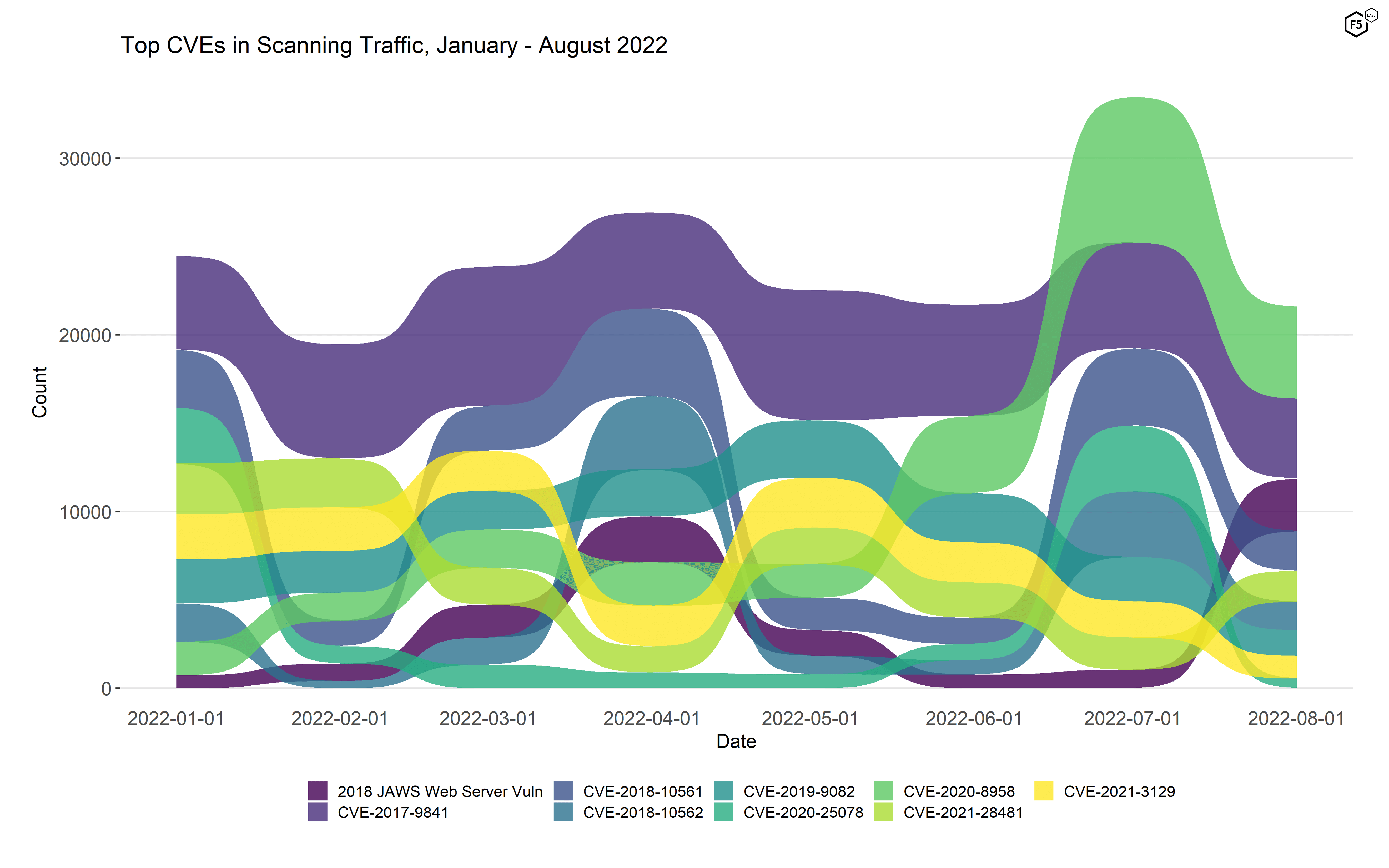
Figure 2. Top targeted CVEs, January - August 2022. These nine vulnerabilities represent the top five for each individual month, aggregated together. As in July, CVE-2020-8958 was the most frequently targeted vulnerability in August according to our sensors.
August Port Scan Data
F5 Labs also analyzes data for TCP ports other than 80 and 443 from the Efflux network. The top 10 ports for August 2022 follow patterns we’ve been seeing for years, with port 5900 (VNC) topping the list, followed by a collection of ports used mainly for remote access (ssh, telnet, ftp, RDP) and some database and mail related ports as well. This month, SMB dropped out of the top ten (but was still at #13) and POP3 made an appearance, up from #16 the month prior.
| Port | % of total connections | Typical Application |
| 5900 | 26.1% | VNC |
| 3306 | 15.1% | Mysql/MariaDB |
| 23 | 13.2% | Telnet |
| 80 | 10.3% | HTTP |
| 21 | 10.0% | FTP |
| 22 | 6.9% | SSH |
| 443 | 4.3% | HTTPS/TLS |
| 110 | 3.1% | POP3 |
| 1080 | 2.0% | SOCKS Proxy |
| 3389 | 1.0% | RDP |
Table 2. Port targeting data for August 2022.
Conclusions
Many of the trends that this scanning traffic represents are unsurprising. Attackers’ emphasis on remote code execution vulnerabilities, for instance, is predictable given the options that a successful exploit provides them. The continuing interest in IoT vulnerabilities means that we should echo the prediction we made about July attacker trends, which is that attackers are building up infrastructure for future DDoS attacks.
Finally, an examination of Figure 2 makes it clear that attacker interest is dynamic and unpredictable. There are too many variables at play, many of them hidden from view, for us to be able to predict with any confidence that a given vulnerability will become popular.2 The surge in scanning for CVE-2020-8958 is a great example: both in terms of rank and traffic volume, it was insignificant until it spiked in July. In the absence of any way to make specific predictions, timely reporting of observed events is probably as good as we are going to get. And with that slightly self-serving observation, we’ll sign off until next month.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


