We are excited to introduce a new threat intelligence series from F5 Labs. Effluxio,1 one of our longstanding partners, maintains a globally distributed network of sensors. Because these sensors are hosted at IP addresses with no associated domain names, traffic logged on the sensors consists of two types: automated but non-malicious scans from organizations like Shodan and Google, or traffic from malicious sources that represents attempts to identify or exploit vulnerabilities. This data gives us a view into attacker behaviors and priorities that we might not get from a single host and can be a useful complement to other sources with regard to the evolution of the threat landscape.
The goal of this new series is to identify trends in attacker targeting. For this inaugural edition we are publishing a six month retrospective focused on attempts to identify or exploit known web vulnerabilities (CVEs), limited to ports 80 and 443. In the following months, we’ll publish updates documenting how attackers’ preferred target vulnerabilities change over time, as well as the occasional one-off piece exploring particularly interesting requests or newly prevalent attacks.
Basic Findings
Let’s start with some basic facts and observations from this six-month dataset, for context:
- 2,666,226 total events logged on ports 80 and 443 from January 1 to June 30, 2022.
- Those 2.67 million events contained 61,749 unique request URIs. 41,902 of those URIs occurred exactly once in the data, meaning that the frequency distribution of targets has a very long tail.
- 33.4% of total connections requested the web root (that is, the top directory of the web server). For most of these requests we lack the information necessary to distinguish malicious scans from routine, non-malicious scans by crawlers.
- The traffic also featured some non-CVE targets that showed up with high frequency:
- 101, 482 requests (3.8% of total connections) for AWS credentials or config files (e.g. “/.aws/credentials” or “/aws/.credentials”.
- 95,605 requests (3.6% of total connections) for common PHPMyAdmin paths (e.g. “/phpMyAdmin/”, “/PMA2011/” or similar).
- 80,165 requests (3% of total connections) for common Wordpress paths (e.g. “/wp-admin/”)
- 39,579 (1.5% of total connections) were for favicons, some of which we speculate are attempts to fingerprint the software running on the server.
We identified 29 known vulnerabilities in the remaining traffic.
- 97% of the remaining traffic were related to just 6 CVEs.
- Of these 6 high-frequency CVEs, five are remote code execution (RCE) vulnerabilities, 2 are IoT vulnerabilities, and one is an administrator password disclosure.
- While this target is not actually a CVE, we observed 13,213 events of scanning for a misconfigured PHP debugger, which if present would allow arbitrary PHP code to be run on the target.
Six-month Overview
In the future we will be publishing monthly summaries of CVE targeting to give defenders a sense of which patches to prioritize. However, six monthly summaries in a row can be hard to parse, so Figure 1 shows how CVE targeting in our data fared over the entire six-month period. Below this overview is a list of all of the CVEs we identified in the logs with a short description and a link to more information.
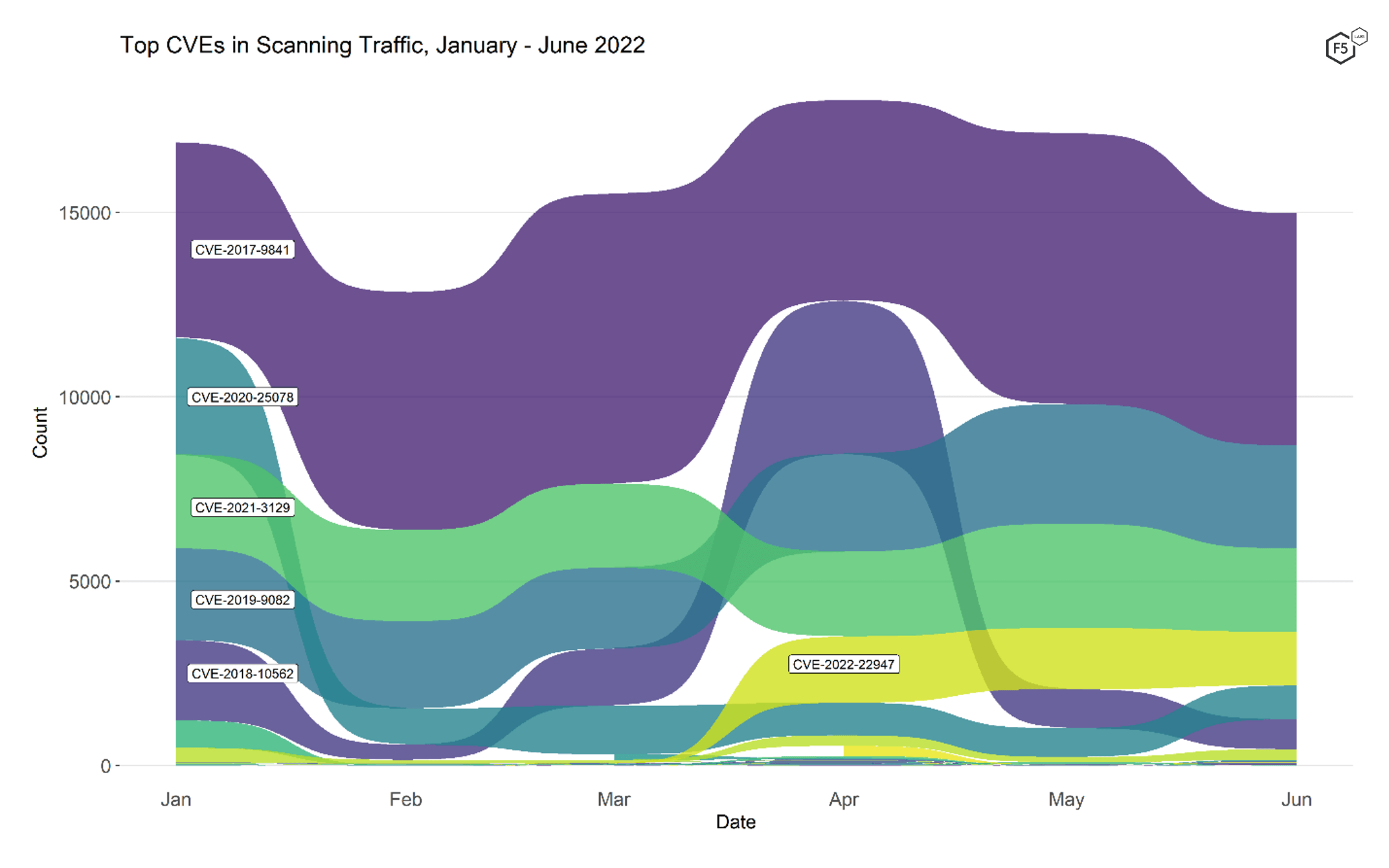
Figure 1. CVE targeting volume for 30 CVEs, January 2022 - June 2022. The top five vulnerabilities in January make up five of the top six in June, in volume over the six-month period.
As you can see in Figure 1, six out of the 29 identified CVEs constituted the vast majority (96.7%) of the traffic, so much of our analysis is focused on them. CVE-2017-9841 was the most frequently targeted for the entire six-month period, fluctuating slightly but never enough to fall from the top spot. Below that, the other top five vulnerabilities traded positions a few times due to notable changes in traffic:
- CVE-2020-25078 dropped from second spot in January to fourth in February and varied between fourth and sixth position afterwards. In January it made up 19% of CVE-focused traffic, but it dropped to 7.7% in February and hovered between 4.4% and 8.5% for the rest of the period.
- Traffic targeting CVE-2018-10562 grew tenfold between February and April, approaching that of CVE-2017-9841, before it subsided back to its baseline levels in May.
- CVE-2022-22947 grew dramatically between March and April, despite (or perhaps because) only being published in March. Its traffic grew from one single connection attempt in February to 19 events in March and 1799 events in April, putting this vulnerability on the map almost overnight.
Because these top six constituted so much of the traffic, the other 24 vulnerabilities became so hard to trace through that plot that we didn’t even bother to include a legend. Table 1 shows traffic counts and proportions over the entire period for all identified vulnerabilities:
| CVE Number | Count | Proportion of CVE Traffic (%) |
| CVE-2017-9841 | 38658 | 40.5 |
| CVE-2019-9082 | 15736 | 16.5 |
| CVE-2021-3129 | 14691 | 15.4 |
| CVE-2018-10562 | 10167 | 10.7 |
| CVE-2020-25078 | 8067 | 8.5 |
| CVE-2022-22947 | 4934 | 5.2 |
| CVE-2021-44228 | 1295 | 1.4 |
| CVE-2021-26855 | 815 | 0.9 |
| CVE-2022-22965 | 308 | 0.3 |
| CVE-2020-3452 | 204 | 0.2 |
| CVE-2018-7600 | 80 | 0.1 |
| CVE-2021-29203 | 61 | 0.1 |
| CVE-2018-7700 | 46 | <0.1 |
| CVE-2020-9757 | 42 | <0.1 |
| CVE-2021-3577 | 32 | <0.1 |
| CVE-2017-0929 | 29 | <0.1 |
| CVE-2021-32172 | 26 | <0.1 |
| CVE-2021-21315 | 24 | <0.1 |
| CVE-2020-7796 | 22 | <0.1 |
| CVE-2021-33357 | 20 | <0.1 |
| CVE-2020-13167 | 19 | <0.1 |
| CVE-2020-28188 | 19 | <0.1 |
| CVE-2019-8982 | 16 | <0.1 |
| CVE-2017-9506 | 15 | <0.1 |
| CVE-2018-1000600 | 13 | <0.1 |
| CVE-2021-31589 | 13 | <0.1 |
| CVE-2022-25369 | 13 | <0.1 |
| CVE-2008-6668 | 12 | <0.1 |
| CVE-2019-2767 | 12 | <0.1 |
Table 1. Volume of traffic targeting CVEs in the first six months of 2022, with raw traffic counts and proportions of total traffic targeting CVEs.
CVE/Target Writeups
CVE-2017-9841
A remote code execution (RCE) vulnerability in PHPUnit (4.x before 4.8.28 and 5.x before 5.6.3) that allows attackers to execute arbitrary PHP code on the target. The vast majority of the payloads observed in our data appeared to be checks for a vulnerable target, such as “<? md5(“phpunit”) ?>” or calls to run “uname”; however, in some cases we saw an attempt to download and install a PHP based webshell. NVD
CVE-2019-9082
An RCE vulnerability in ThinkPHP before 5.0.24. Allows attackers to execute operating system commands on the target. Similar to CVE-2017-9841, the majority of the commands run were simple checks used to validate that the target was vulnerable, but we did see a few instances where a script or executable would be downloaded from an attacker-controlled server and run, using “wget”, “curl”, or “powershell”. NVD
CVE-2021-3129
An RCE vulnerability in Ignition before 2.5.2 (as used in Laravel and other products). Allows attackers to execute Ignition “solutions” which can, through quite a complex chain of actions, lead to remote code execution. If you want a lot of details, we recommend you check out this writeup (https://www.ambionics.io/blog/laravel-debug-rce). In our data, we again primarily saw payloads which appear to be for a simple validation of vulnerability, with a few (malformed) attempts to run code. NVD
CVE-2018-10562
An RCE vulnerability on some models of Dasan GPON home routers. The majority of the payloads we observed are associated with the Mozi botnet, a variant of Mirai. NVD
CVE-2020-25078
A vulnerability in the D-Link DCS-2530L (before 1.06.01) and DCS-2670L (before 2.03) router software, which allows the attacker to obtain the remote administrator password for the device. As a disclosure vulnerability, there wasn’t any evidence of what an attacker would do with the remote administrator password, but one assumes that, having obtained it, full control over the device would be the next step. NVD
CVE-2022-22947
An RCE vulnerability in Spring Cloud Gateway prior to version 3.1.1+ and 3.0.7+. Allows attackers to perform a code injection on the target. Once again, the majority of the events showed simple testing for the presence of the vulnerability, and a handful attempted to exploit it, generally downloading a python script and attempting to run it. NVD
CVE-2021-44228
This is the infamous “Log4Shell” vulnerability, which we probably don’t need to summarize for anyone reading this, but we have a basic explanation of Log4Shell as well as a reflection on its implications. NVD
CVE-2021-26855
A vulnerability that allows an attacker to bypass authentication and impersonate an admin on Microsoft Exchange Server, in practice this is usually chained CVE-2021-27065, which allows arbitrary file writing, to achieve RCE on the target. It affects many different versions of Exchange. This vulnerability was one of four zero-day vulnerabilities that were extensively exploited in a coordinated campaign by a state-sponsored group in early January 2021. The bulk of our observations feature sets of pairs of requests from the same IP address, first with a GET to confirm the presence of a host, then a POST with an XML schema autodiscover request. NVD
CVE-2022-22965
This is one of the (also) infamous Spring4Shell vulnerabilities, so named for their superficial similarity to the then-recent Log4Shell event. 2022-22965 is an RCE in Spring Framework versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19, as well as older unsupported versions. Most of the logs we have targeting this vulnerability are exploratory, looking for likely endpoints such as “/register?class.module...” and “login?class.module...”. NVD
CVE-2020-3452
A directory traversal vulnerability in Cisco Adaptive Security Appliance (ASA) and Cisco Firepower Threat Defense (FTD) which allows for directory traversal and remote file disclosure. Nearly all of our logs of requests targeting this vulnerability are targeting one of two paths, “/+CSCOT+/translation-table” or “/+CSCOT+/oem-customization” followed by various query strings, which is consistent with exploit proofs of concept for this vulnerability. NVD
CVE-2018-7600
A highly critical RCE nicknamed Drupalgeddon 2 which affected Drupal versions 6.x – 8.x. This vulnerability was caused by insufficient input sanitization on AJAX requests related to form submissions. Most of our records targeting this vulnerability were merely confirming its presence, though we did note a few requests that attempted to download a webshell. NVD
CVE-2021-29203
A remote authentication bypass vulnerability in HPE Edgeline Infrastructure Manager < 1.23. (Note that HPE issued a patch in v1.22 with an insufficient mitigation, and 1.23 is the definitive mitigated version.) For the most part we noted pairs of requests from each IP address, first a PATCH request to a password reset function, then a POST to log in at a separate URI. However, we did not note any traffic looking for the third stage of this attack which changes the password of the OS root account, so it is possible this activity was all reconnaissance and not an active attempt to exploit. NVD
CVE-2018-7700
A cross-site request forgery (CSRF) vulnerability in DedeCMS 5.7 that results in arbitrary code execution. All of the requests we received were testing for remote code execution using a simple PHP function such as generating an MD5 hash. NVD
CVE-2020-9757
A server-side template injection vulnerability affecting the SEOmatic plugin v < 3.3.0 for Craft CMS. The template injection results in RCE. The sensor traffic matching this vulnerability invariably was testing for remote code execution by trying to evaluate a mathematical expression. NVD
CVE-2021-3577
An RCE in some Motorola-branded Binatone Hubble cameras resulting in unauthorized access to the device from the same network. Most of the traffic we observed was attempting to abuse a function for setting the time zone for the camera to download a shell. Patch version depends on the camera model.2 NVD
CVE-2017-0929
A server-side request forgery (SSRF) in DotNetNuke (DNN) < 9.2.0, resulting in disclosure of internal network resources. Our logs noted several attempts to connect to attacker-controlled resources or to download a webshell. NVD
CVE-2021-32172
An RCE in the Maian Cart ecommerce shopping cart system ultimately caused by an unsecured internal API in the Elfinder plugin. The lack of access control allows the attacker to use the API write a webshell using Maian Cart’s file manager plugin, resulting in RCE. All of the related logs were attempts to use the API to create a local file to write a webshell. NVD
CVE-2021-21315
A command injection vulnerability in the System Information Library for Node.JS (npm package "systeminformation") in versions before 5.3.1. By passing in an array instead of a string, it’s possible to inject commands that will be executed by the host OS. In our samples, all of the requests appeared to be attempting to upload the /etc/password file via the wget command to an Interactsh server.3 Interactsh is a service that allows for the detection of out-of-band interactions, so this appears to be simple testing for the presence of this vulnerability. NVD
CVE-2020-7796
A Server-Side Request Forgery vulnerability in Zimbra Collaboration Suite before version 8.8.15 Patch 7. This allows an attacker to cause the server to make a web request on their behalf. As with CVE-2021-21315, above, all of the requests were tests attempting to connect to an Interactsh server, and so appear to be simple testing for the presence of this vulnerability. NVD
CVE-2021-33357
A command injection vulnerability in the RaspAP 2.6 to 2.6.5 web GUI which allows an unauthenticated attacker to run arbitrary OS commands. RaspAP is a software package for wireless routing that runs on Debian devices, including the Raspberry Pi platform. Once again, 100% of the traffic we observed targeting this vulnerability was simple testing involving using the vulnerability to send a request to an Interactsh server. NVD
CVE-2020-13167
An unauthenticated remote code execution (RCE) vulnerability in Netsweeper versions through 6.4.3. An attacker can supply a specific query string and run a command. In our data, all attempts to exploit this vulnerability simply echoed the word “nonexistent” into a file which can be read with another request. This is consistent with checking for a vulnerable server, rather than attempting to deliver a specific payload. NVD
CVE-2020-28188
An unauthenticated remote code execution (RCE) vulnerability in TerraMaster TOS through version 4.2.06, which allows attackers to run OS commands. 100% of our observed events were basic tests for this vulnerability, either using it to make a request to an Interactsh server, or by creating a uniquely named file with known content on the webserver which would be able to be viewed on a subsequent request. NVD
CVE-2019-8982
A vulnerability in WaveMaker Studio 6.6 which allows reading files on the server as well as Server-Side Request Forgery (SSRF). In our dataset, we see attempts to read the /etc/passwd file, which is a common means of testing a local file disclosure vulnerability. NVD
CVE-2017-9506
A Server-side Request Forgery (SSRF) vulnerability in the Atlassian OAuth plugin in versions 1.3.0 to before 1.9.12, and versions 2.0.0 to before 2.0.4. In our dataset, the majority of requests were to test via an Interactsh server, or to fetch what amounts to a test file with a unique string. NVD
CVE-2018-1000600
A sensitive information disclosure vulnerability in the Jenkins GitHub Plugin 1.29.1 and earlier allowed for a user with Overall/Read access to Jenkins to capture credentials stored in Jenkins (and also allowed CSRF). In all cases in our dataset, we observed validation of this vulnerability by causing a request to an Interactsh server. NVD
CVE-2021-31589
An unauthenticated cross-site scripting (XSS) vulnerability in BeyondTrust Secure Remote Access Base <6.0.1 that allows attackers to create a new administrator account. Half of the traffic we observed targeting paths associated with BeyondTrust Secure Remote Access were testing for the vulnerability, and half of them were only looking for the application itself. NVD
CVE-2022-25369
A vulnerability in Dynamicweb 9.5.0-9.12.7 that allows unauthenticated attackers to create administrator user accounts. Our logs show attempts to test for the vulnerability. (Note that this CVE has been allocated but has not been published on NVD yet.)
CVE-2008-6668
A set of directory traversal vulnerabilities in the web-based fax tool nweb2fax <= 0.2.7. The vulnerability allows attackers to read arbitrary files. All of the connections we logged were traversing directories looking for “/etc/passwd.” NVD
CVE-2019-2767
An XML External Entity (XXE) injection vulnerability in Oracle Fusion Middleware’s BI Publisher component v11.1.1.6.0, 11.1.1.7.0, 11.1.1.9.0, and 12.2.1.0.0. Exploiting this vulnerability can allow attackers to read, write, or delete data within BI Publisher. Sensor traffic targeting this vulnerability was uniformly testing for the presence of the vulnerability using an XML file named “xxe.xml.” NVD
Conclusions
The majority of the vulnerabilities that were targeted in our sensor traffic are remote code execution vulnerabilities. This is unsurprising, given other research that indicates that code execution vulnerabilities have a higher likelihood of exploitation than other kinds of vulnerabilities.4
Further, those vulnerabilities that allow for remote code execution with a single request are typically used to automate further steps, such as installing a web-shell, to download and run an executable on the target, or to use such techniques to immediately load bot-net related malware. Conversely, with vulnerabilities that require more than one step, we observed that testing for the presence of the vulnerability was more common, rather than a direct attempt at the first stage of exploitation. In other words, understanding the nature of a vulnerability is helpful in terms of interpreting or triaging the traffic targeting it.
A significant amount of the traffic observed used services such as Interactsh to determine vulnerability status. Since these services are anonymous, there is no way for us to determine if the probing that used these services was done for malicious or research purposes. It is likely a mix of both. This seems to be a place where outbound filtering and inspection could yield some benefit.
More broadly speaking, the persistently high volume of scans looking for misconfigurations (exposed AWS credentials, remote PHP debuggers, and the like) indicates that attackers will discover and take advantage of misconfigurations very quickly.
Likewise, the scanning for various IoT/network gear vulnerabilities indicates that these too represent an attack surface that needs greater attention in the environments that have these devices. Whether IoT devices are deployed intentionally by the organization, or accidentally by individual staff, attackers are clearly aware of the opportunities they can offer.
In general terms, what we have observed so far should come as no surprise. The practical considerations of securing environments have remained the same:
- Pay attention to the software installed in the environment and the prioritization of patching software and systems at the network edge (especially for RCE vulns).
- Maintain awareness of what devices and software are really running in the environment.
- Focus on detecting unusual activity, both in terms of what is coming into your network, but also in terms of what is leaving it.
As we move forward into our monthly cadence, we’ll call out what changes, and dig deeper into interesting specifics as we find them. We’re excited to start this new series, and we hope you’ll enjoy it.


